Introduction@Delivery:~$
| Column | Details |
|---|---|
| Name | Delivery |
| IP | 10.10.10.222 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | ippsec |
| Out On | 09 Jan 2021 |
Pwned
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌─[root@d3dsec]─[~/Desktop/HTB/Time]
└──╼ #cat nmap/result.nmap
# Nmap 7.80 scan initiated Sun Sep 27 08:19:05 2020 as: nmap -sC -sV -oA /result 10.10.10.222
Nmap scan report for 10.10.10.222
Host is up (0.16s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
So basically Two ports are opened 22:ssh
80:http
Port-80
There is a simple Web Page.
Let's click on Contact Us.
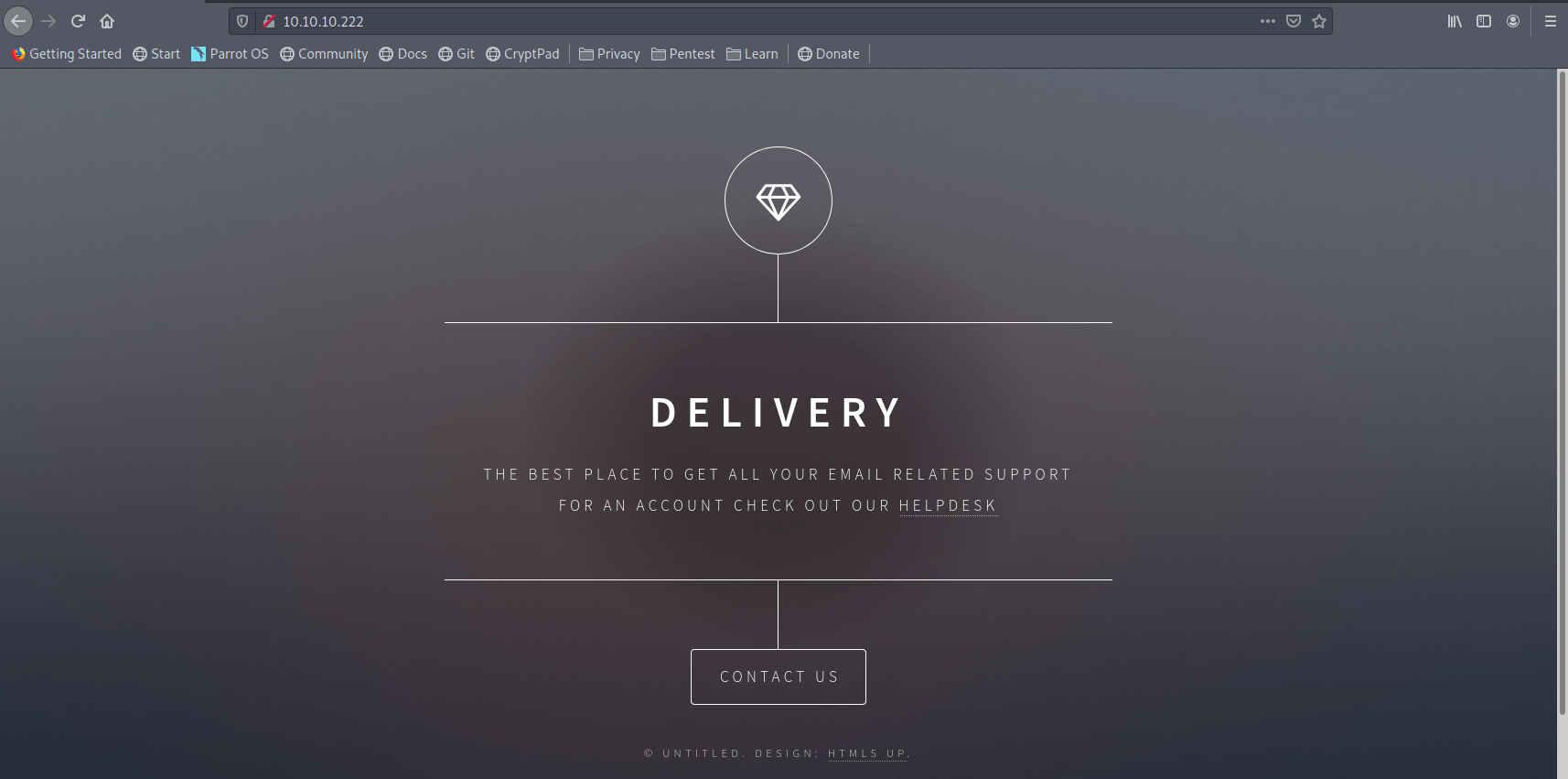
This give us Two links.
Let's click on both.
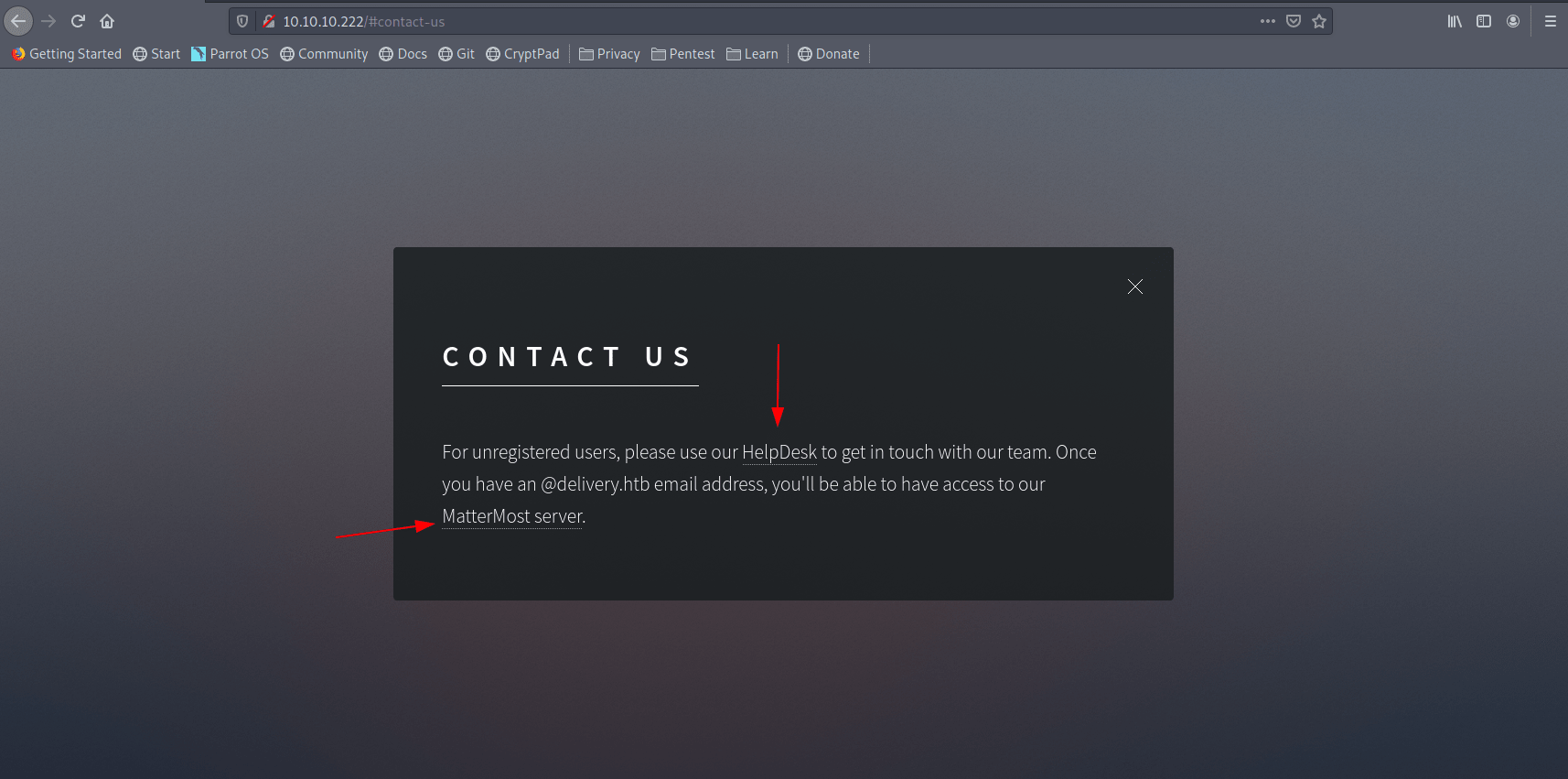
Now we find two domain name with this two links.
helpdesk.delivery.htb
delivery.htb:8065
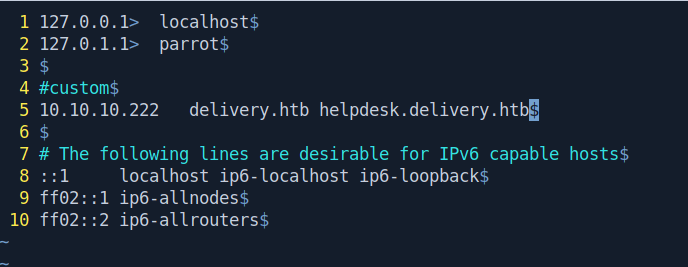
Let's add both in our /etc/hosts file.
Now let's first go to delivery.htb:8065.
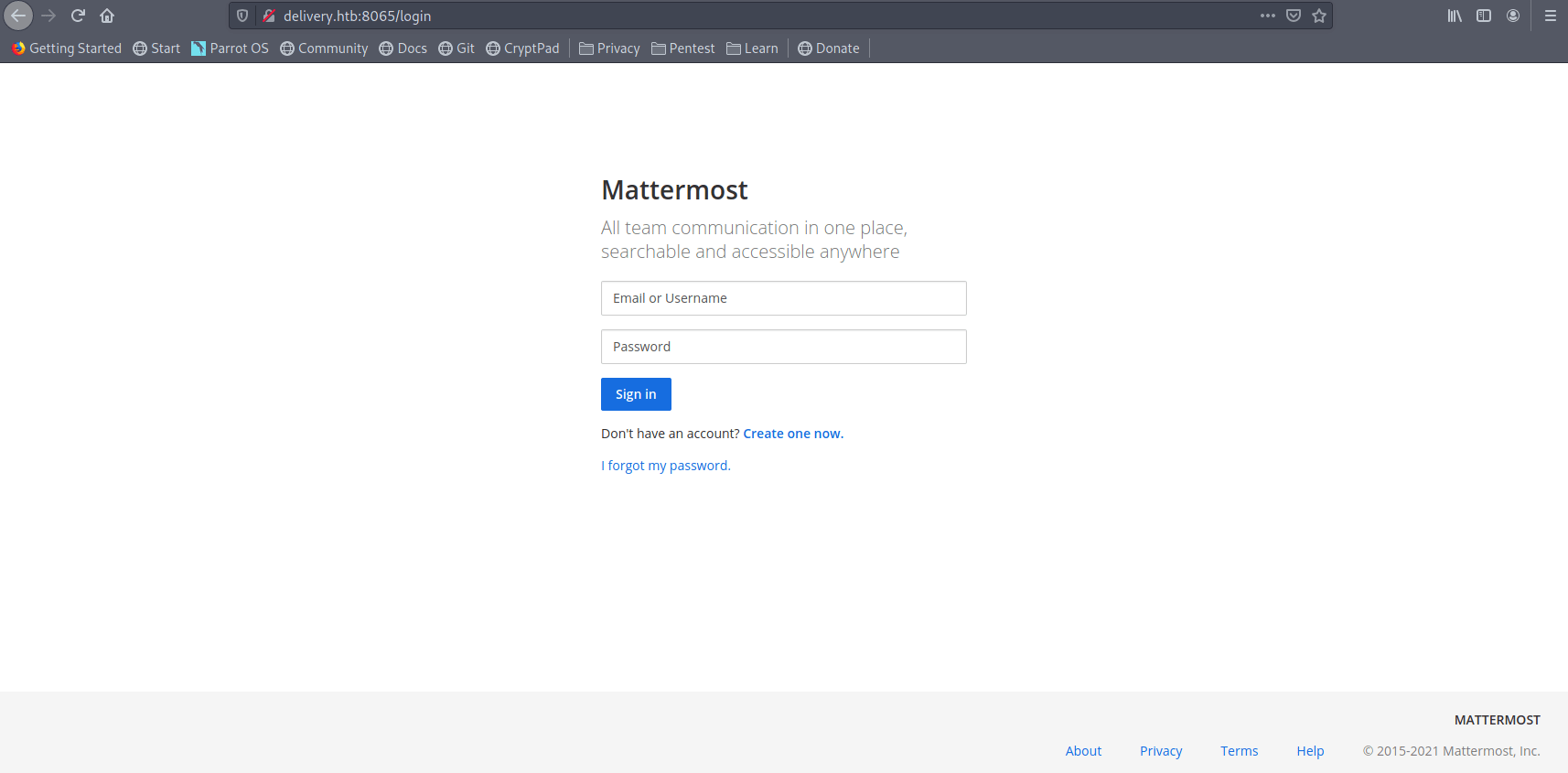
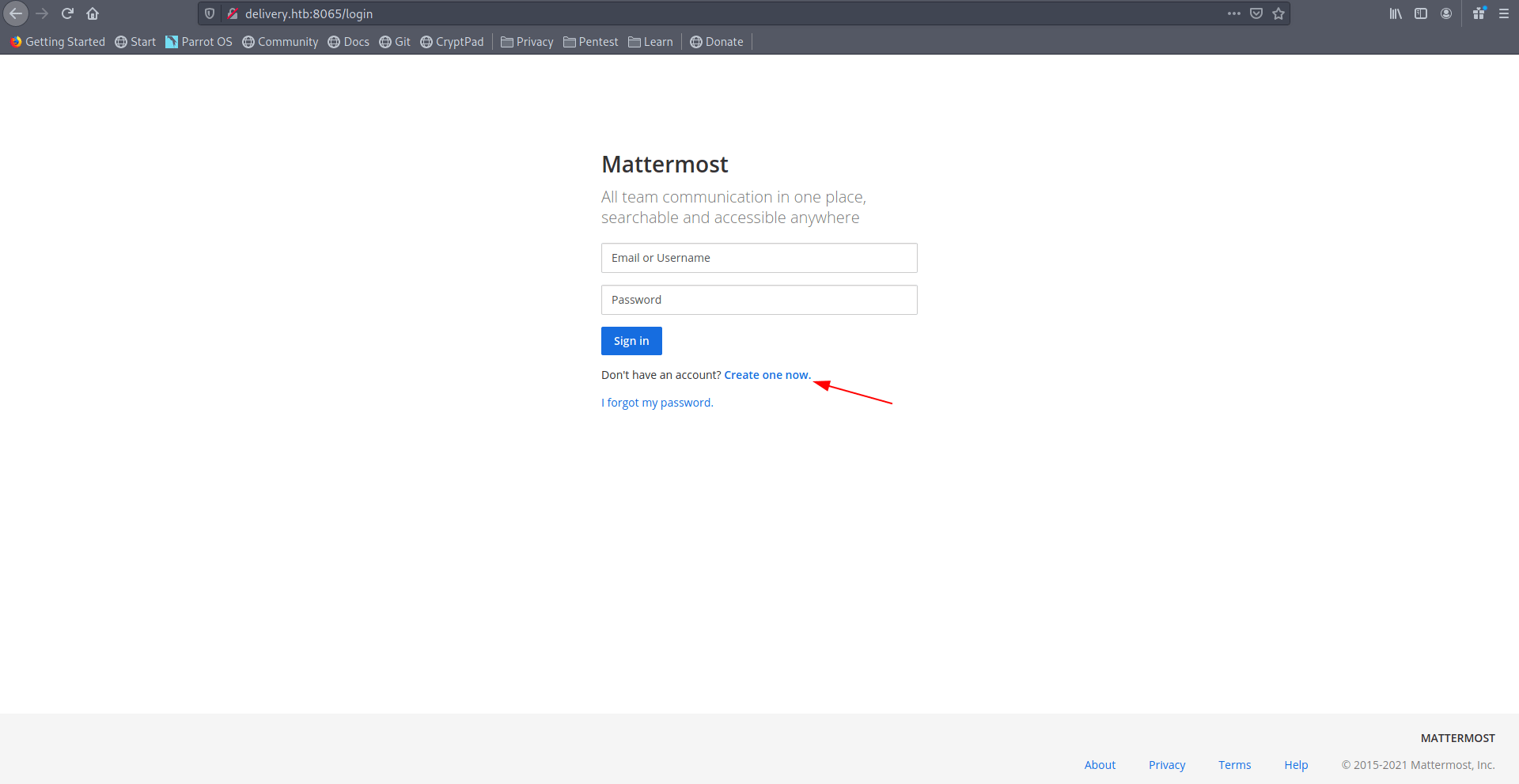
There is a login page and create-one-now option let's click on that real quick.
Give the details and click on Create Account.
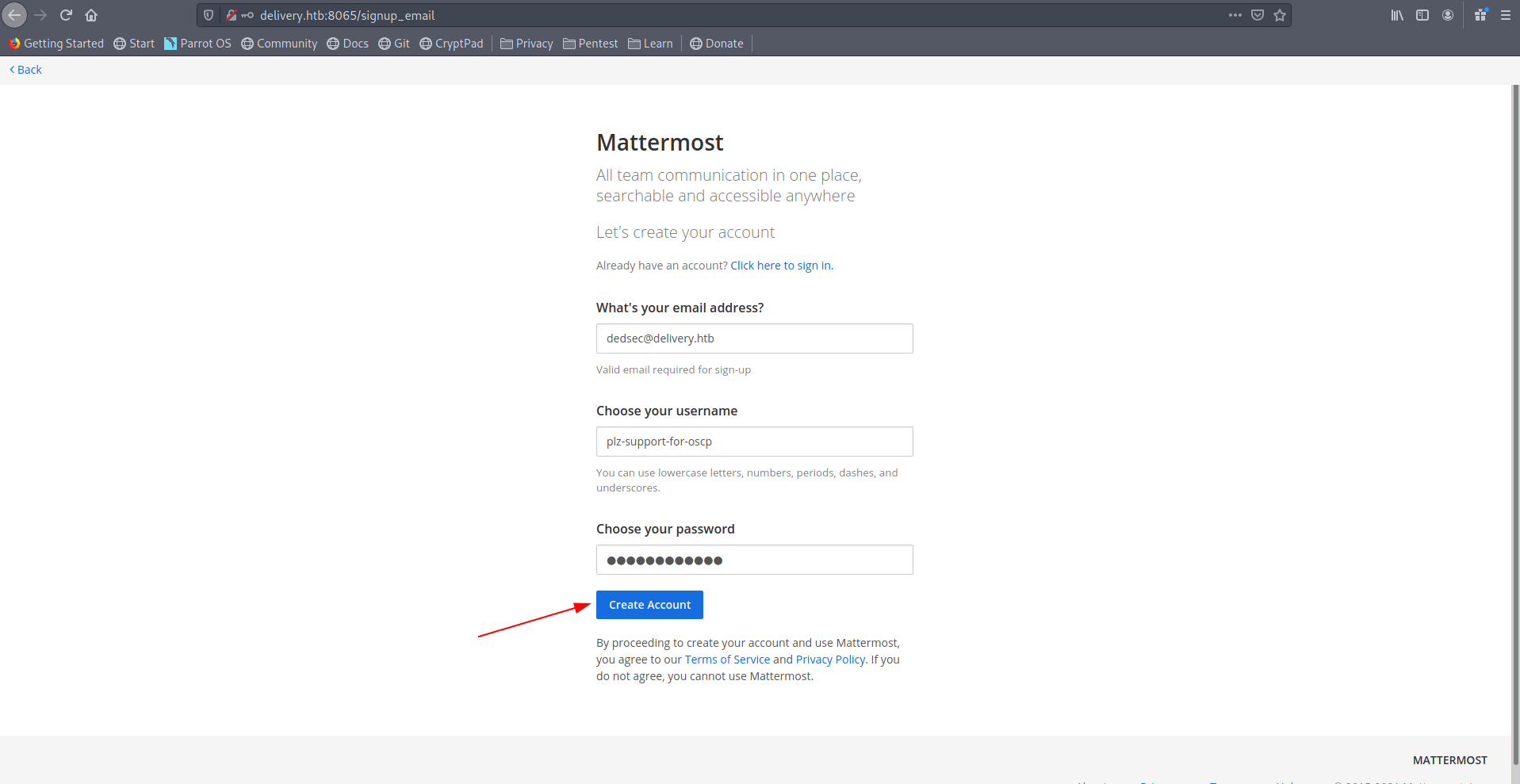
It's asking us for verify our email address. but we don't have that email id.
So we can't do anything here let's go to another domain called helpdesk.delivery.htb
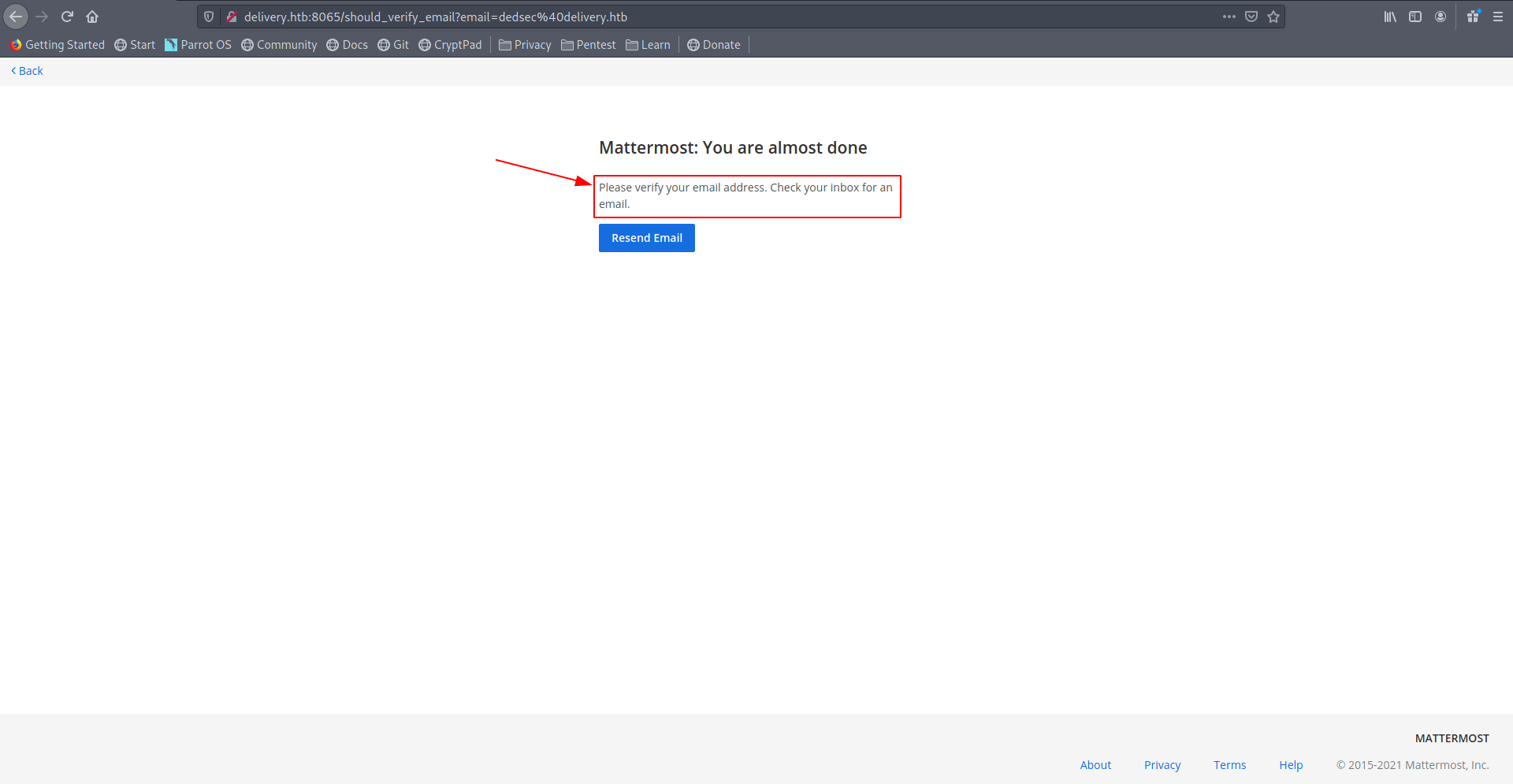
It's a support center page.
Let's click on open a new ticket.
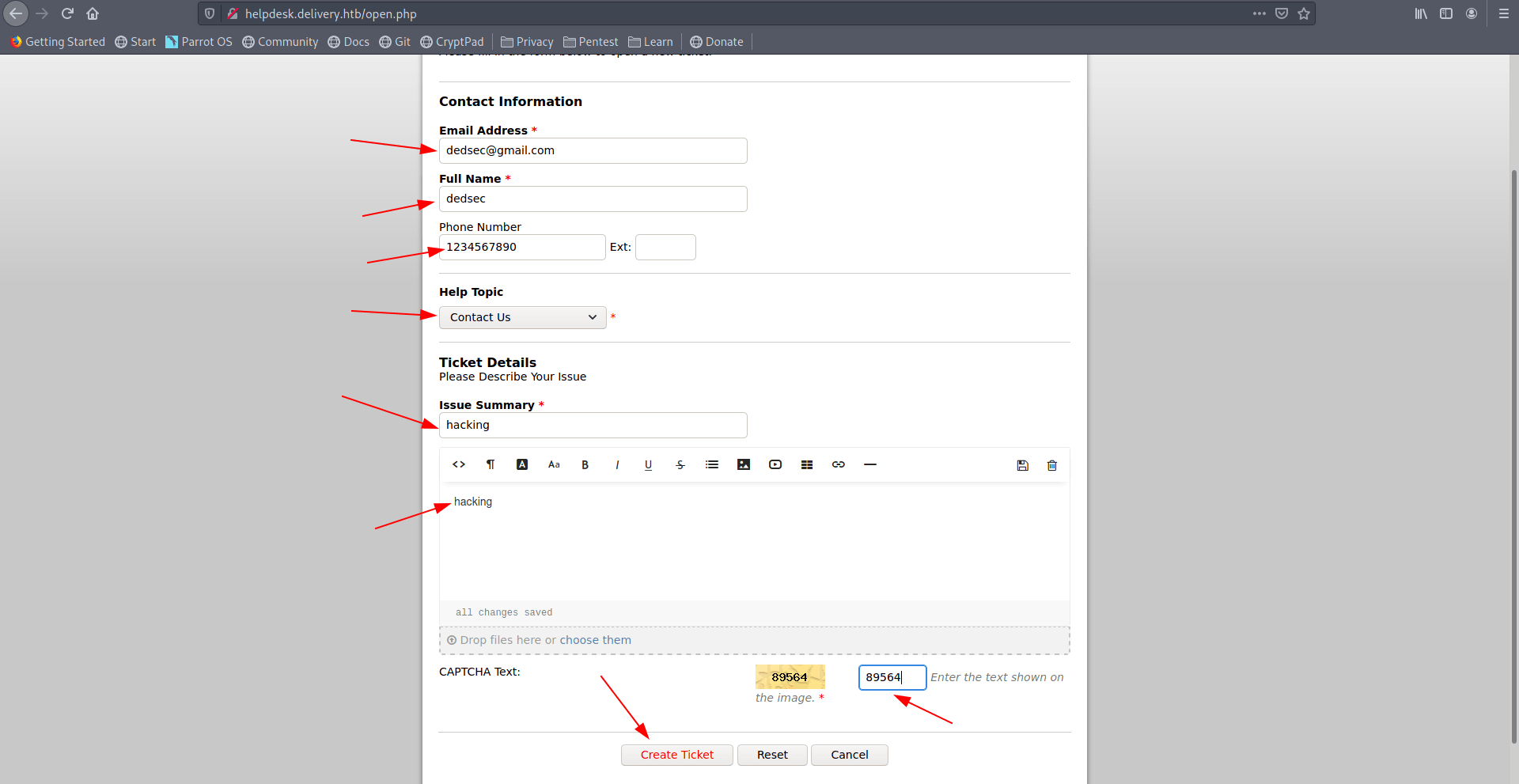
I fill all information and then click on Create-Ticket.
Important : Write down your email-address on mousepad or anything you want because it will use after that.
Now you also got another email and ticket number save this also in your notes.
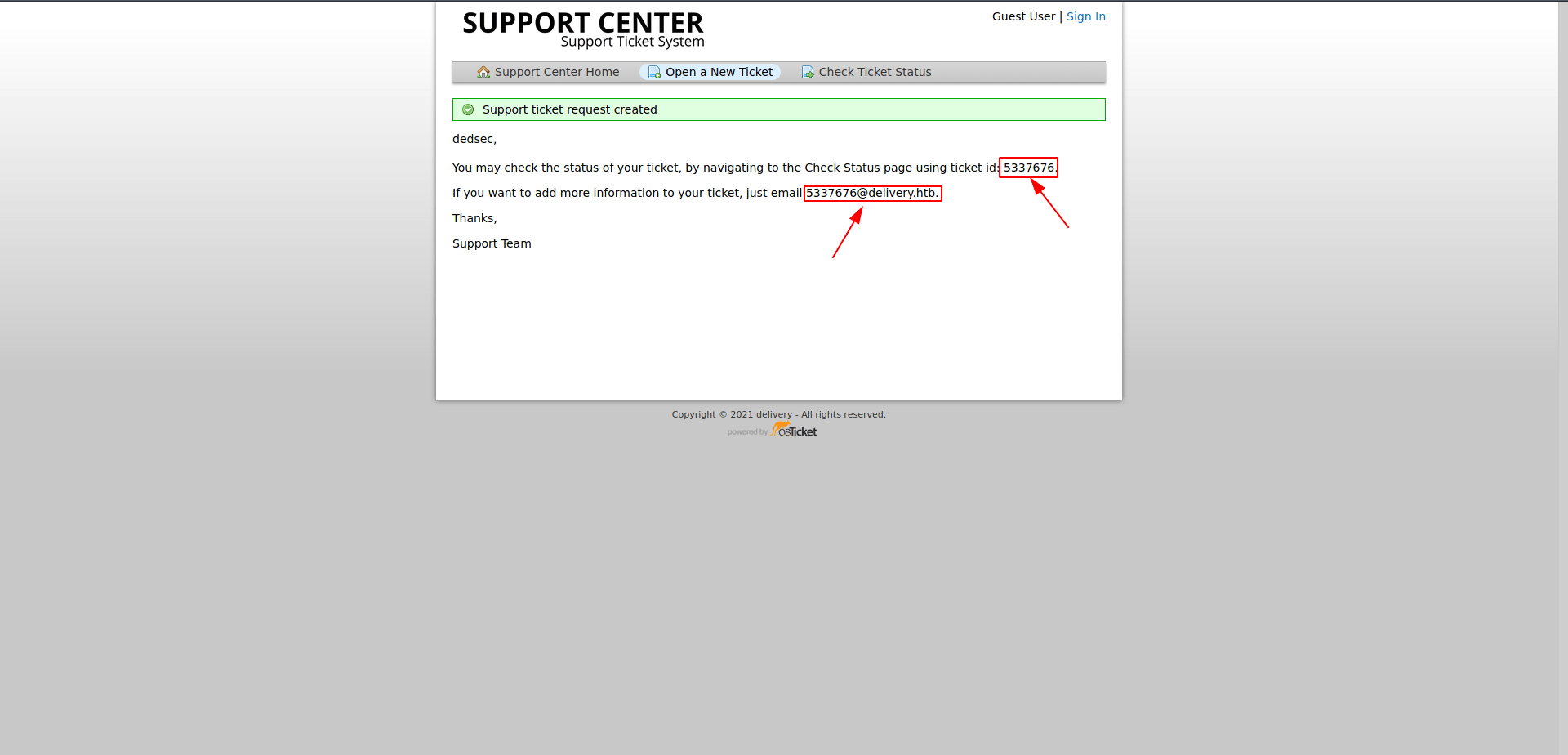
Now click on Check-Ticket-Status.
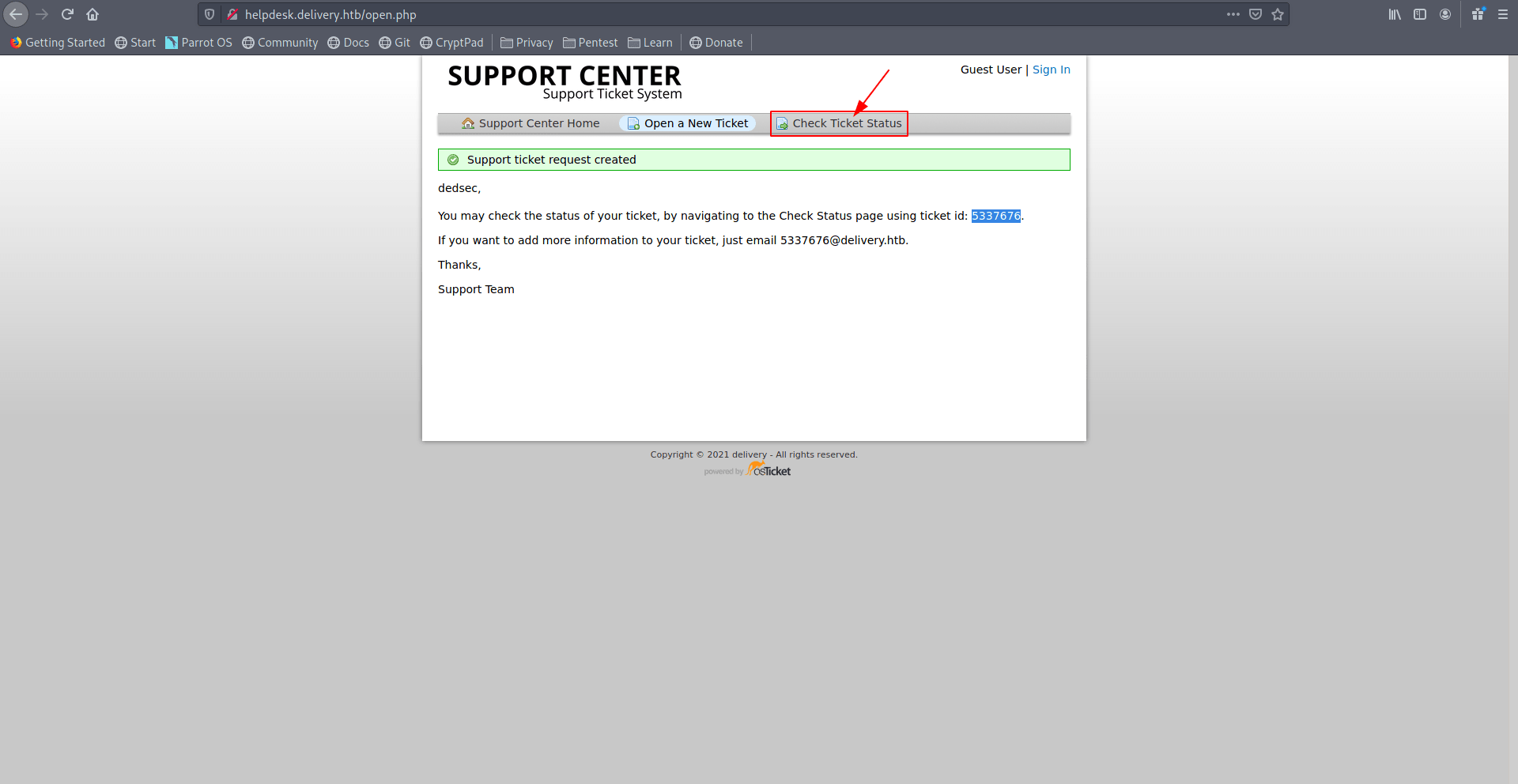
Now enter your email id which you use in your create ticket form and enter ticket number which you store in you notes.
After that click on View-Ticket.
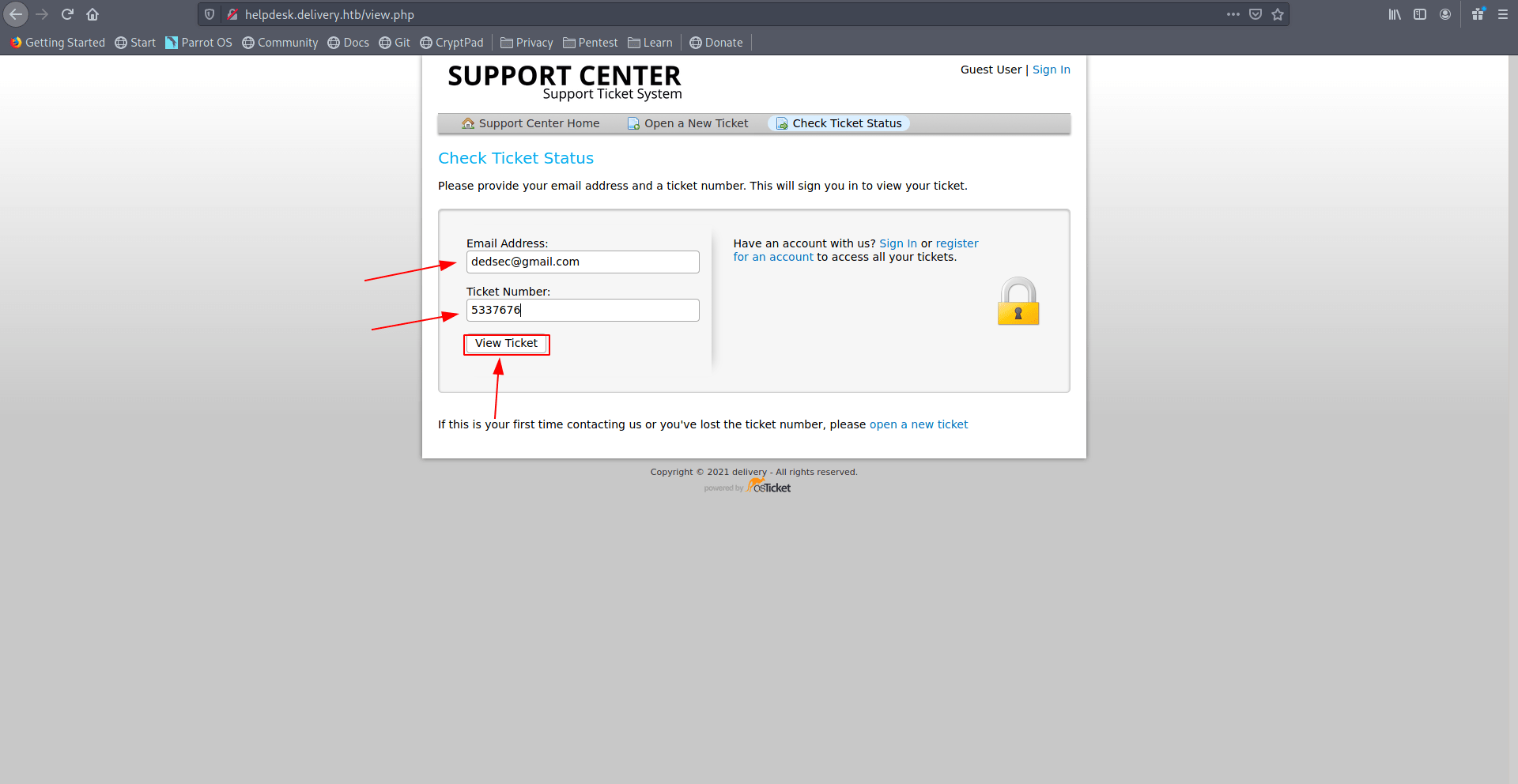
Now you got the inbox of your email-address which will be use when we register on delivery.htb:8065.
Now open delivery.htb:8065 in new tab.
Important : Don't close this tab.
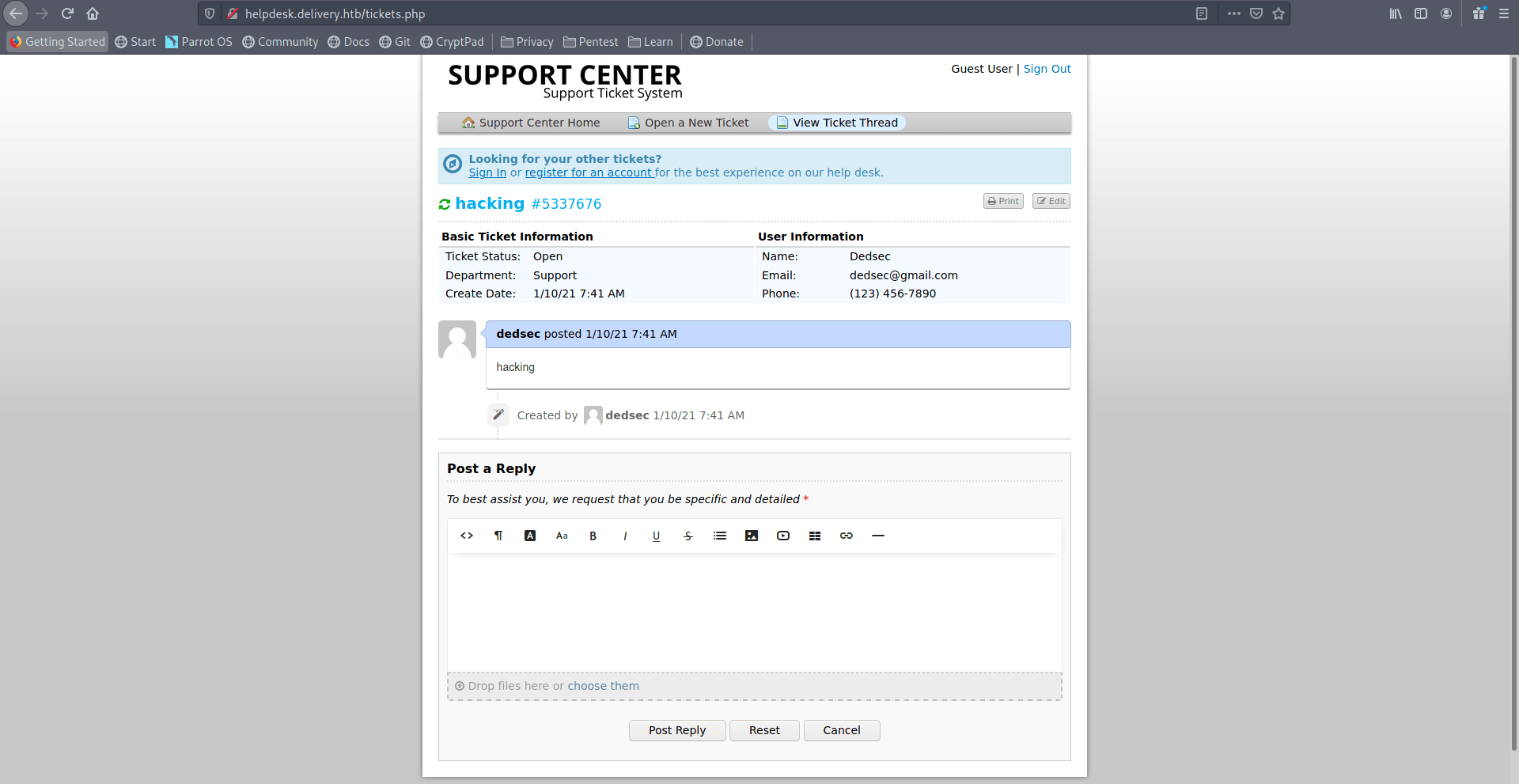
Now again click on Create account.
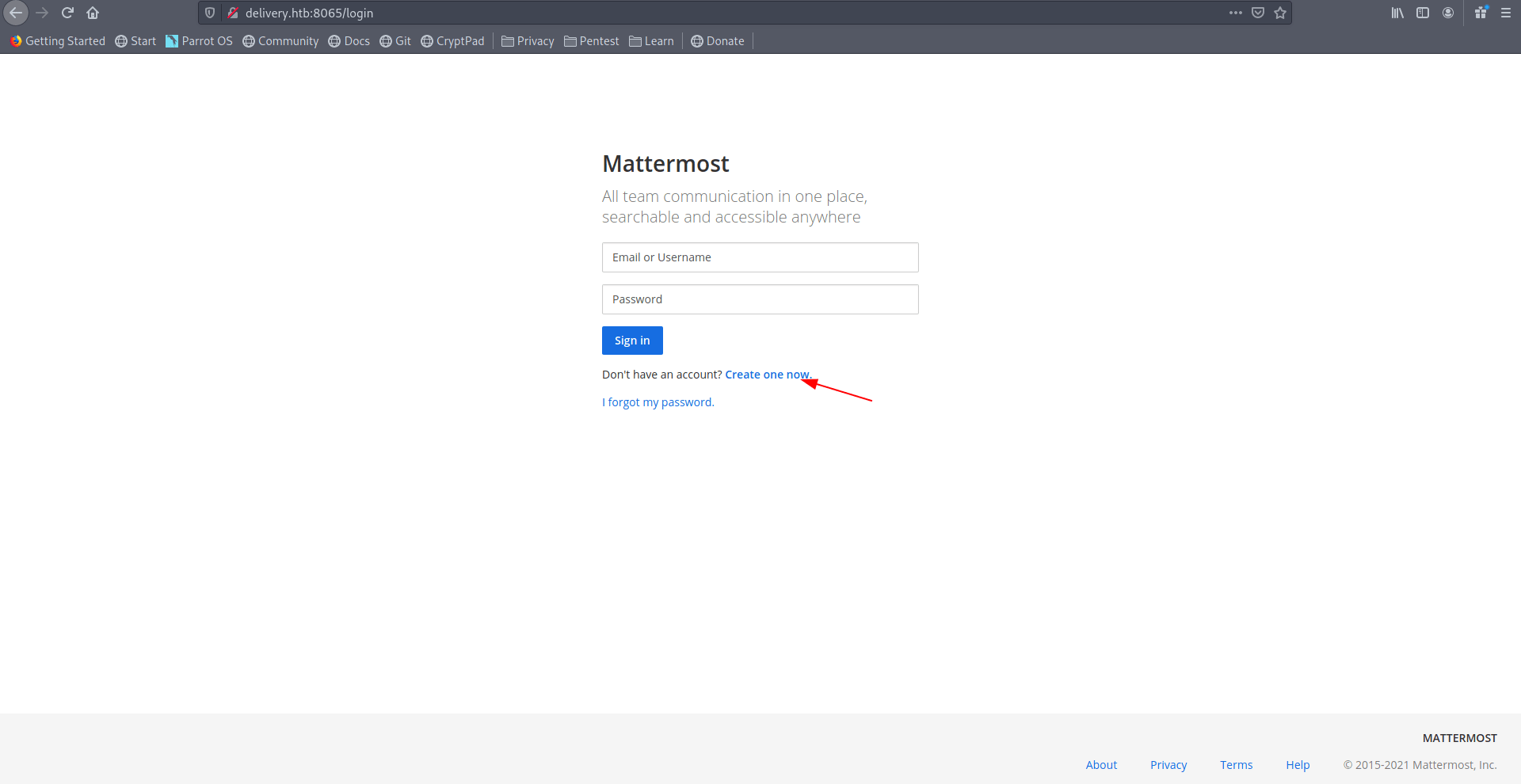
Add that email-address which you got after creating ticket.
Now click on create-account.
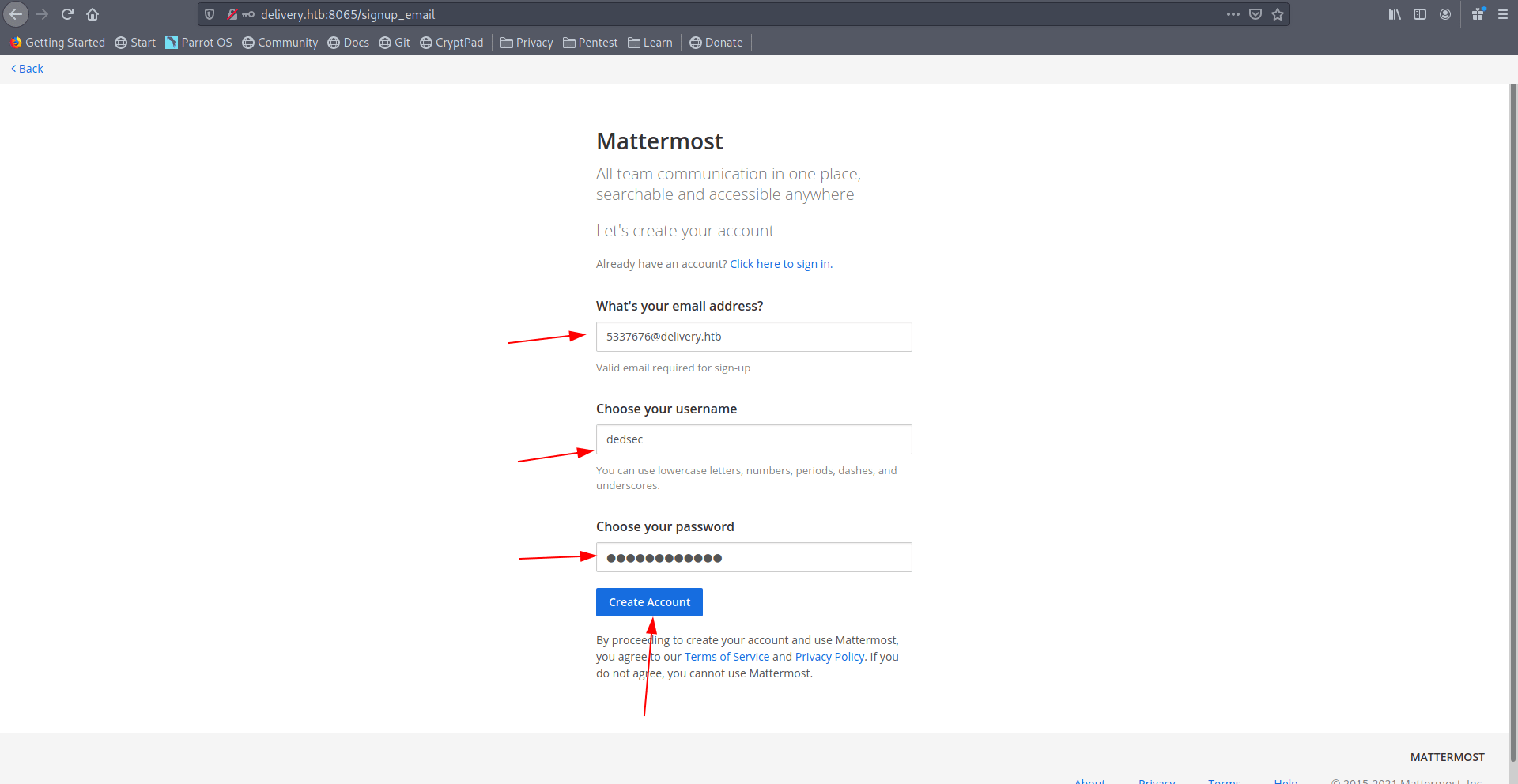
Now he send the verify link in our previous tab. Let's go on previous tab.
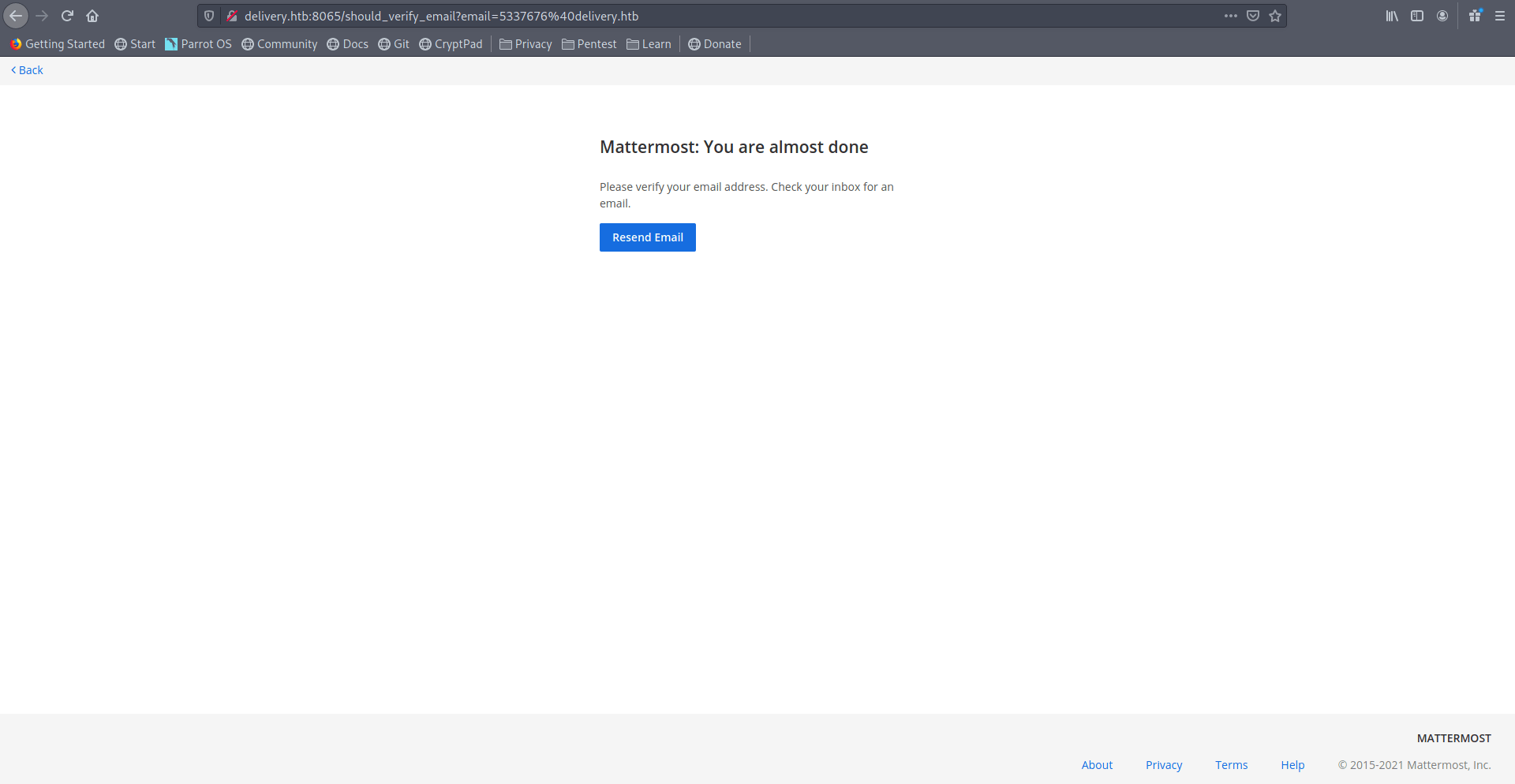
Now click on View Ticket Thread for refresh the page.
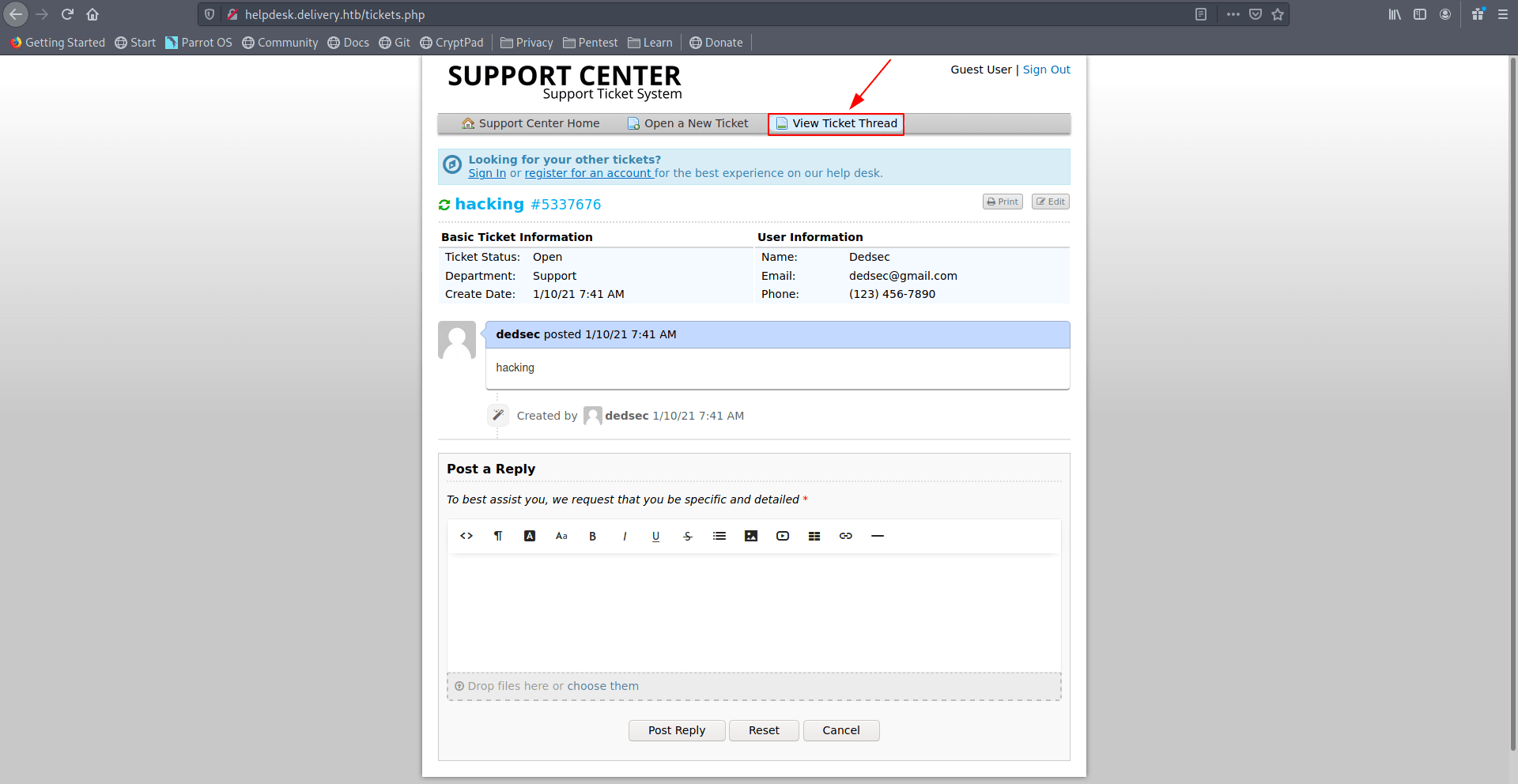
And you got the email with verfication link. copy that link and open in new tab.
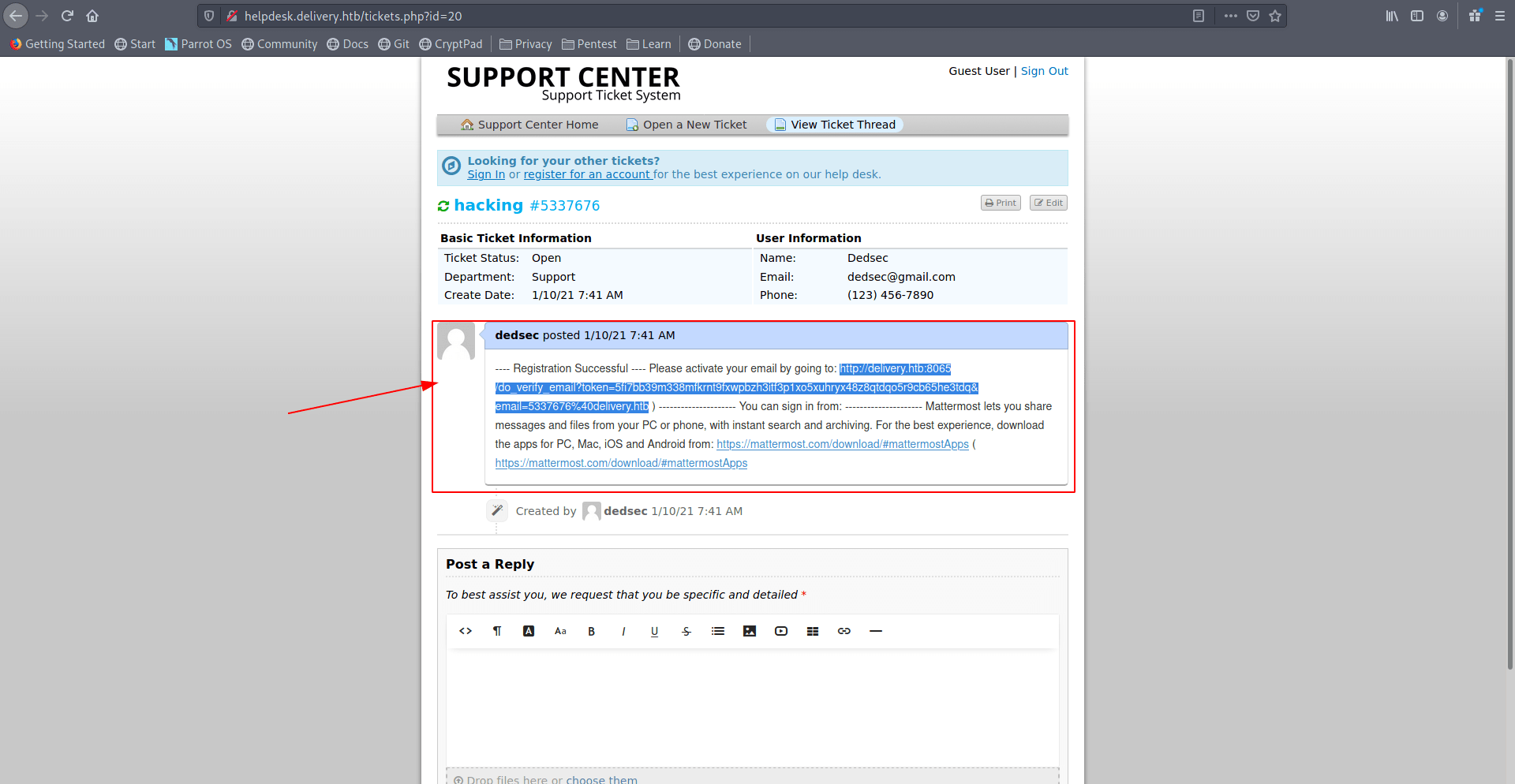
Now it's said Email verified.
Now enter the password and Sign in.
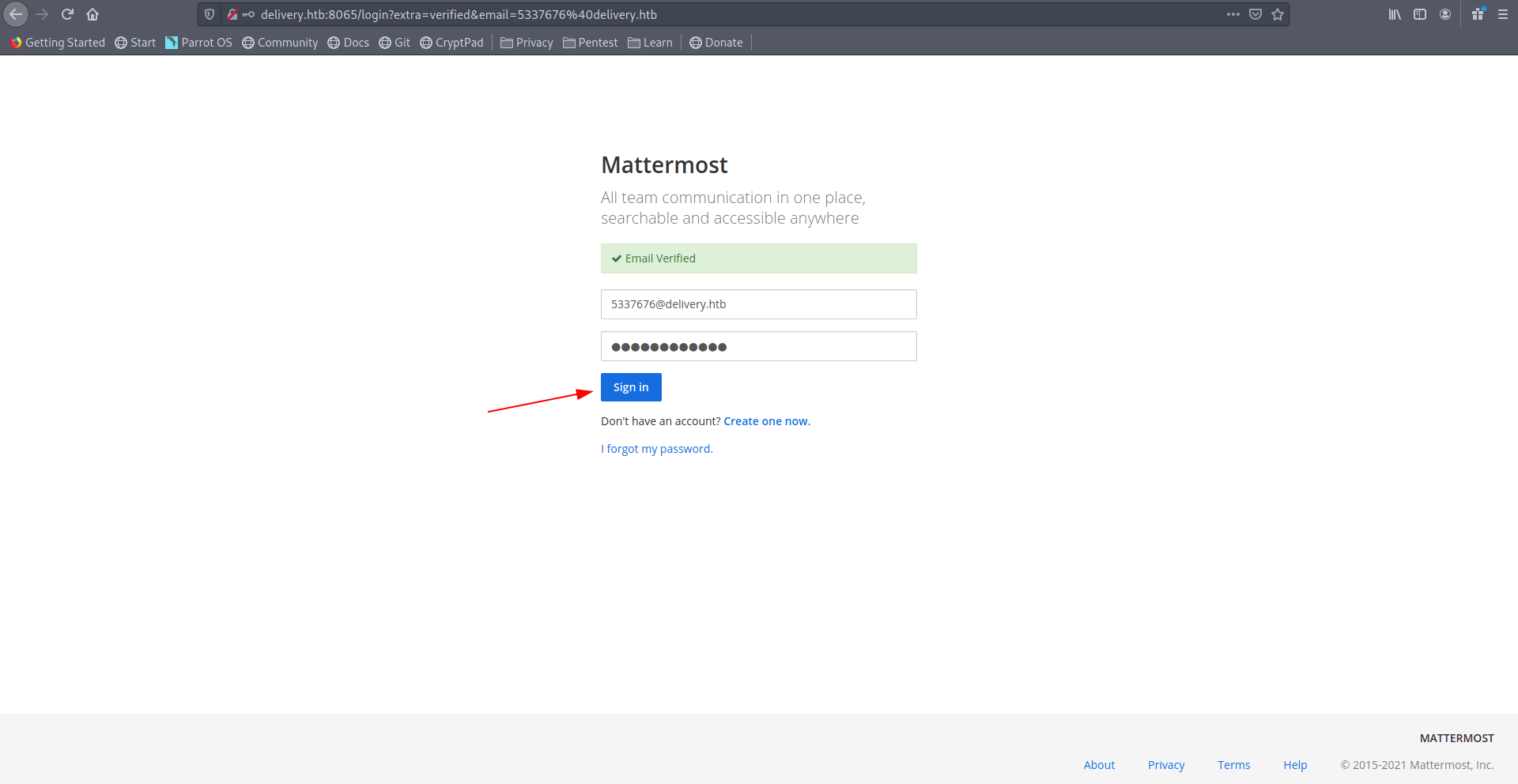
Click on Internal to Continue.
Click on Skip Tutorial.
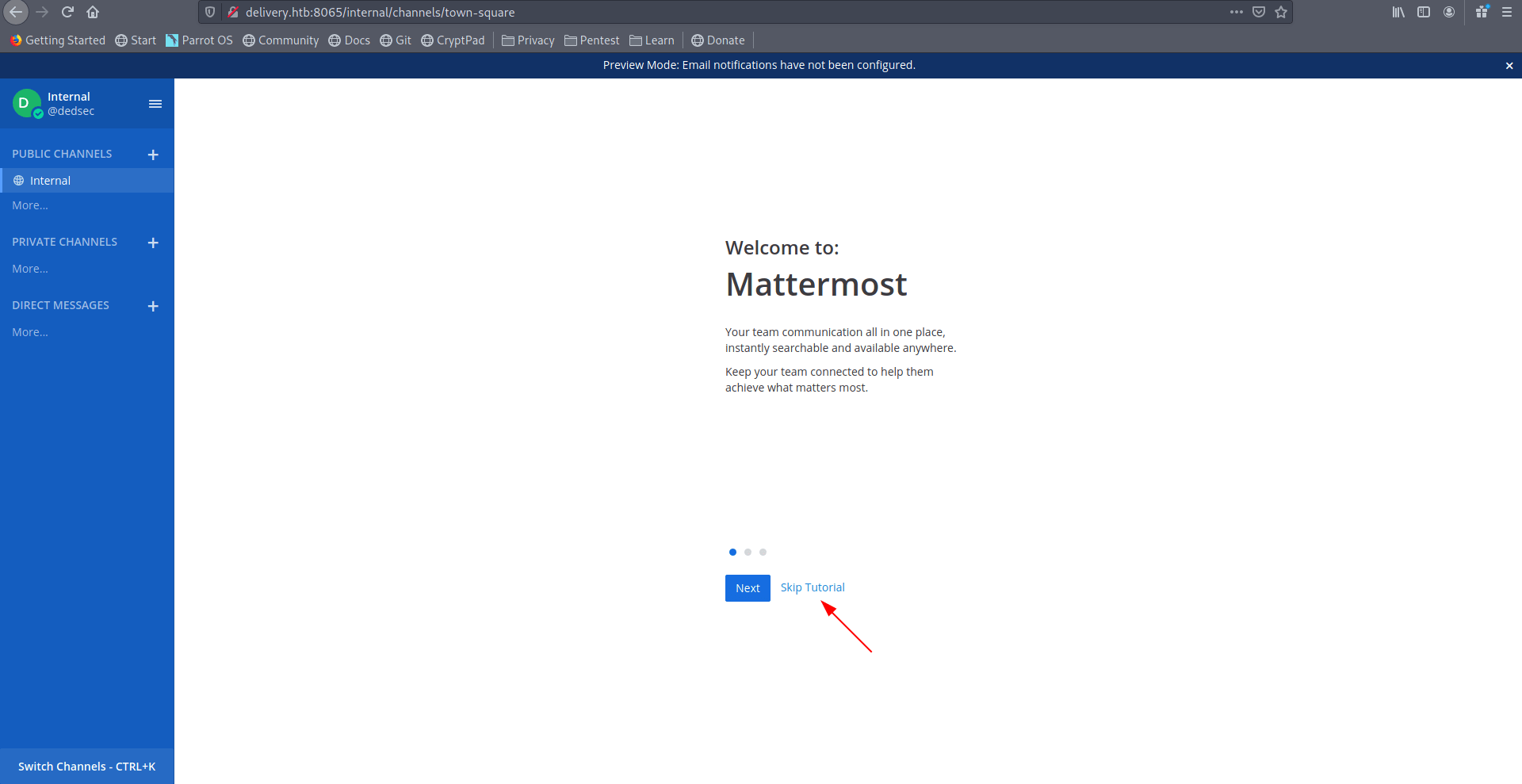
Now if you see a closer look you find username and passowrd for ssh.
maildeliverer:Youve_G0t_Mail!
Let's ssh in and got our user.txt.
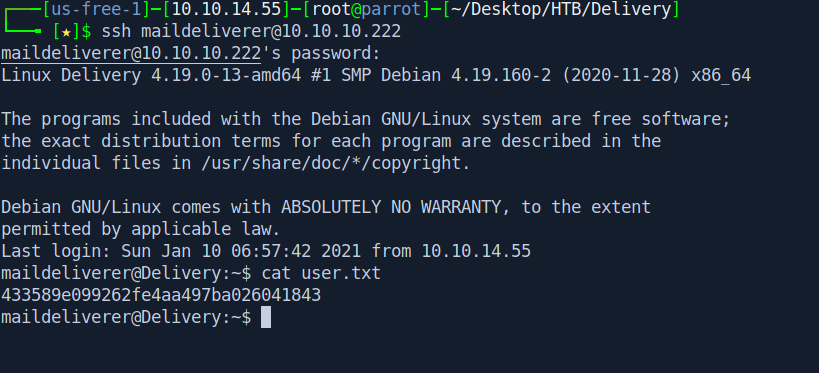
After some manual Enumeration I found an interesting file called config.json inside /opt/mattermost/config/ directory.
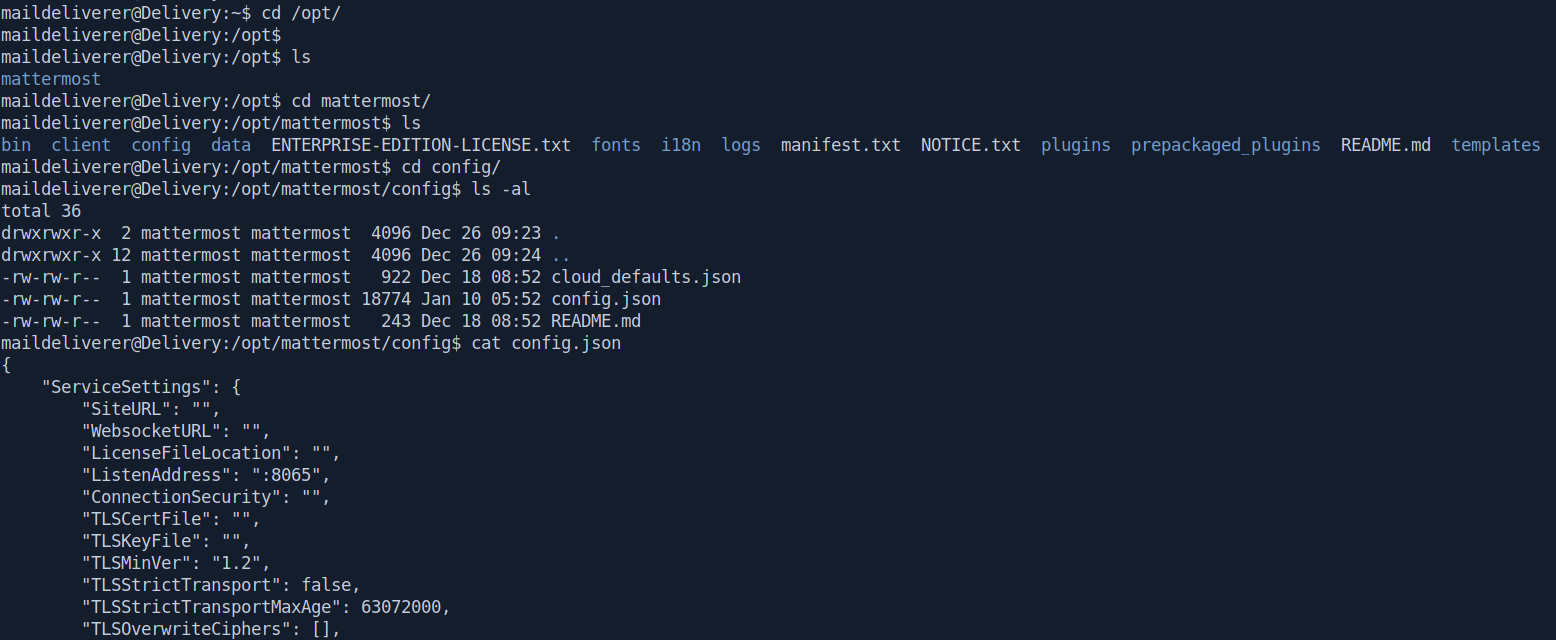
After Enumerating the file we find the mysql creads with database name.
mmuser:Crack_The_MM_Admin_PW
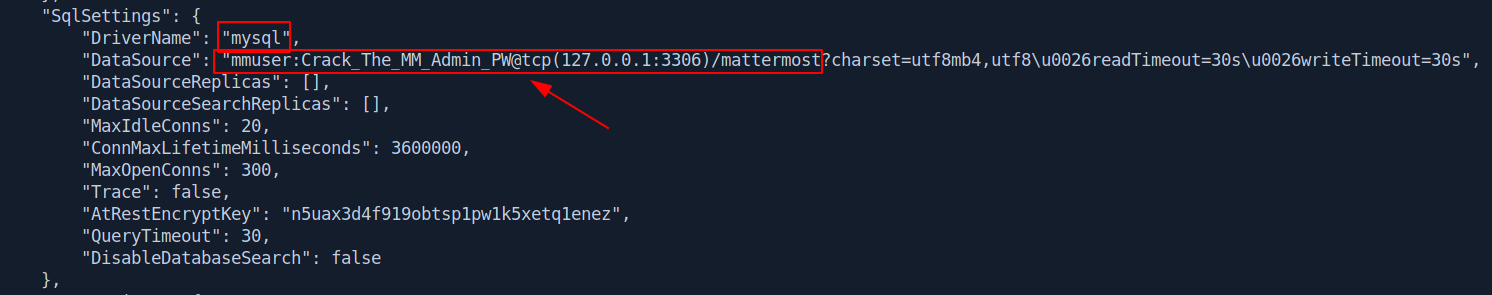
Let's login in mysql real quick.
1
mysql -u mmuser -p'Crack_The_MM_Admin_PW' mattermost
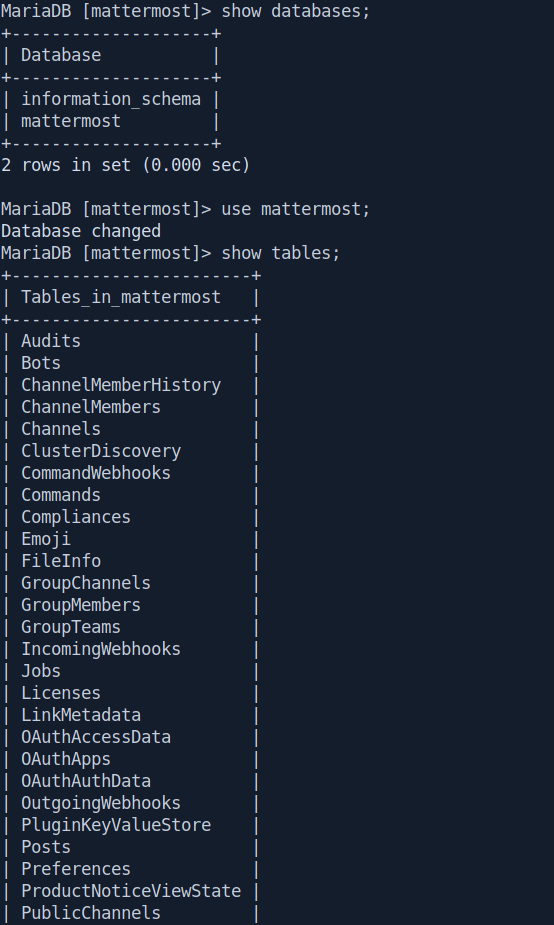
We find the user table let's check what's inside that.
1
2
3
show databases;
use mattermost;
show tables;
It's really messed up.
1
select * from Users;
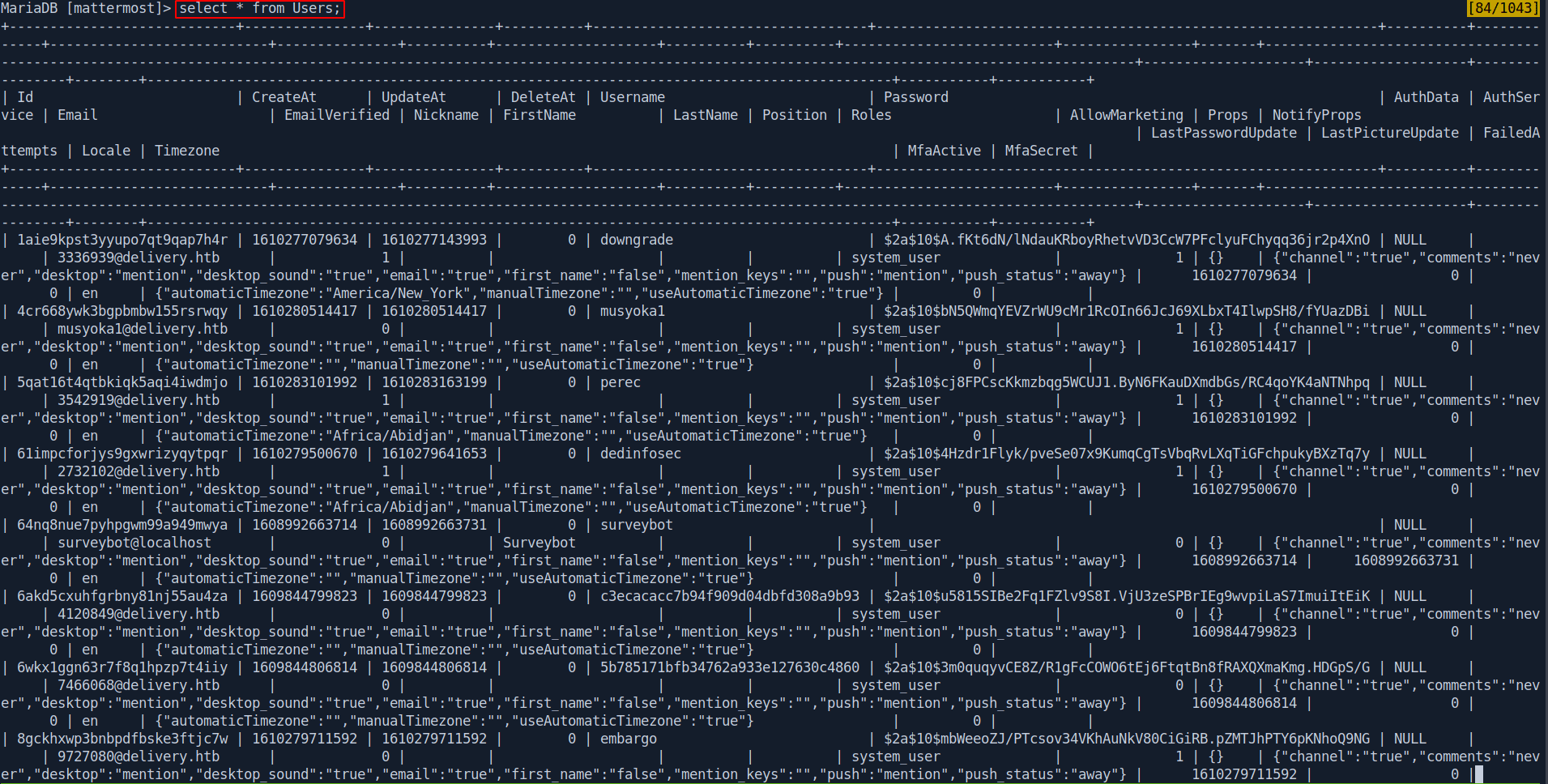
So now we only grep root passoword.
And we got the hash.
1
select Password from Users where Username = 'root';
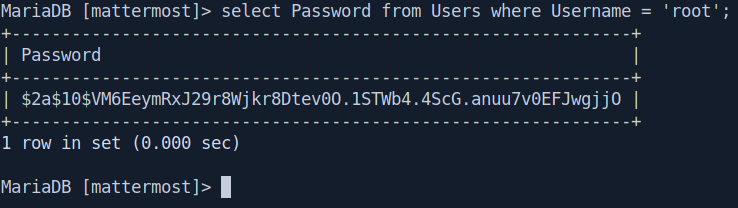
i use john to crack the hash with rockyou.txt but it doesn't work.
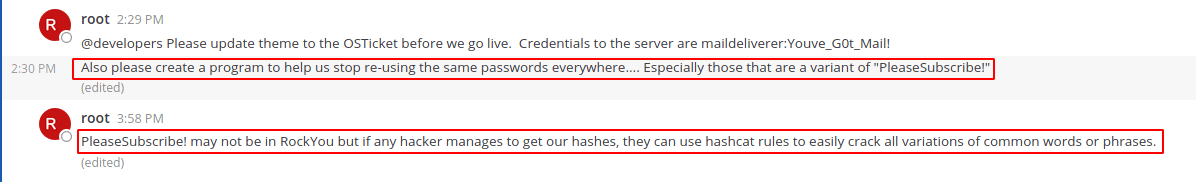
After that i think i miss something then i realized that i don't read the chat carefully.
I go back and read the chat of root then i realized that we want to create a wordlist with hashcat rules with this hint "PleaseSubscribe!"
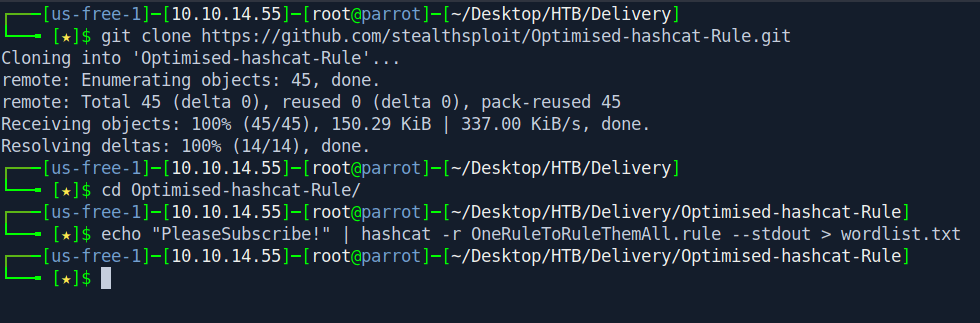
So i download OneRuleToRuleThemAll from github for making a wordlist.
1
2
3
git clone https://github.com/stealthsploit/Optimised-hashcat-Rule.git
cd Optimised-hashcat-Rule/
echo "PleaseSubscribe!" | hashcat -r OneRuleToRuleThemAll.rule --stdout > wordlist.txt
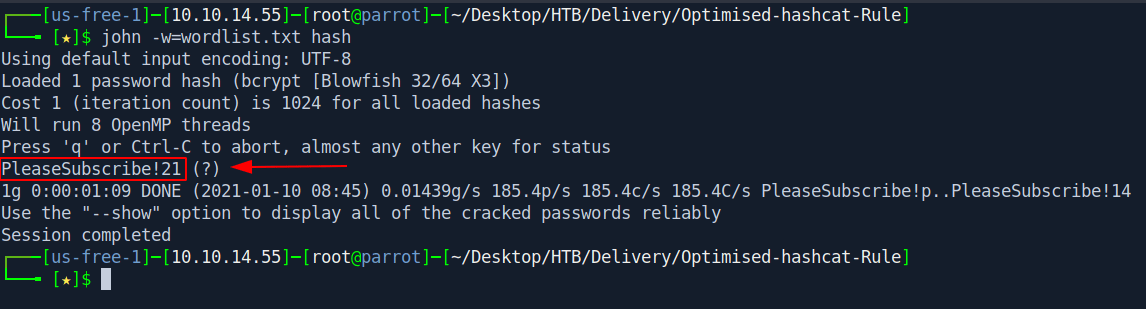
Now we got the wordlist let's crack the hash real quick.
And we got the password "PleaseSubscribe!21"
Let's change the user to root and got our favourate root.txt.
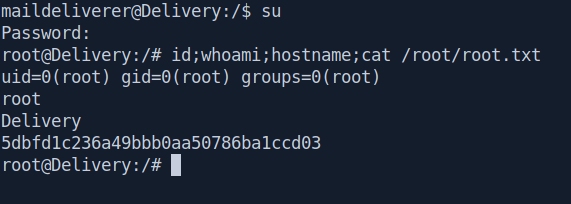
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| OneRuleToRuleThemAll | https://github.com/stealthsploit/Optimised-hashcat-Rule |
